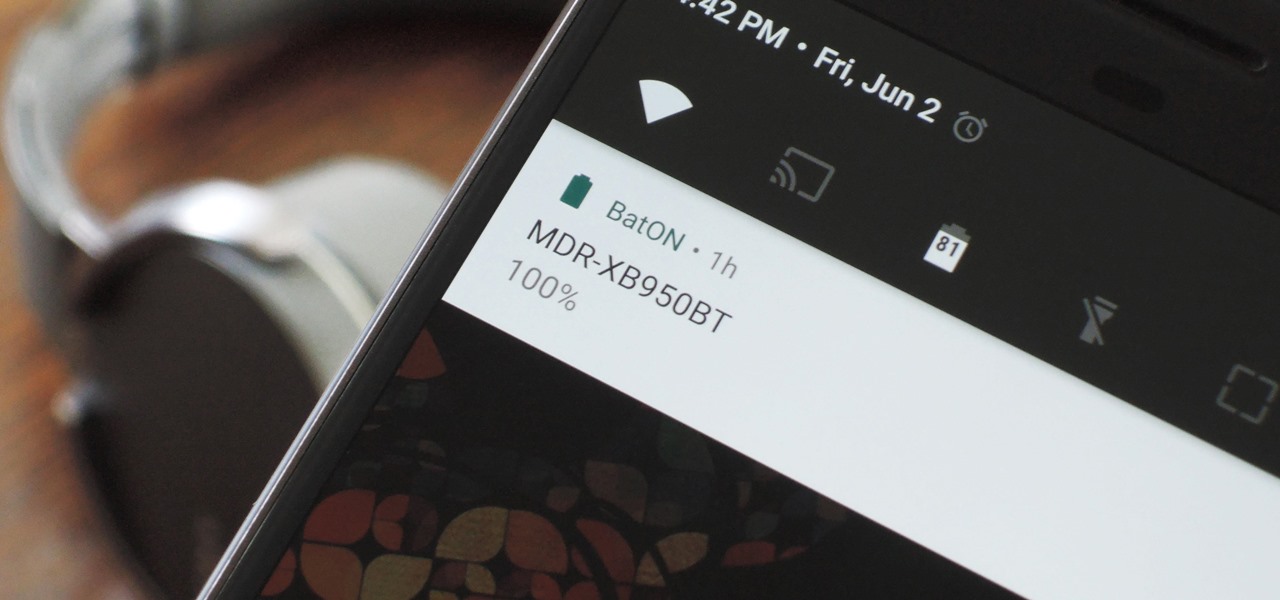
The iPhone has a feature that lets you see how much juice is left in your Bluetooth headphones, but most Android phones are lacking this ability. Thankfully, there's a simple app that'll close this gap in functionality.

Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your browsing history, hides passwords, and deletes cookies. This essentially means ads won't be able to follow you around, in the sense that you won't see ads related to your last ten searches on Google.

After about six months of testing, Facebook has decided to start rolling out a new feature on mobile that automatically plays sound for videos in your News Feed, thanks to "positive feedback" from test users. As far as I'm concerned, they have been testing with the wrong users, because auto-playing sound is by far worse than auto-playing videos ever could be.
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

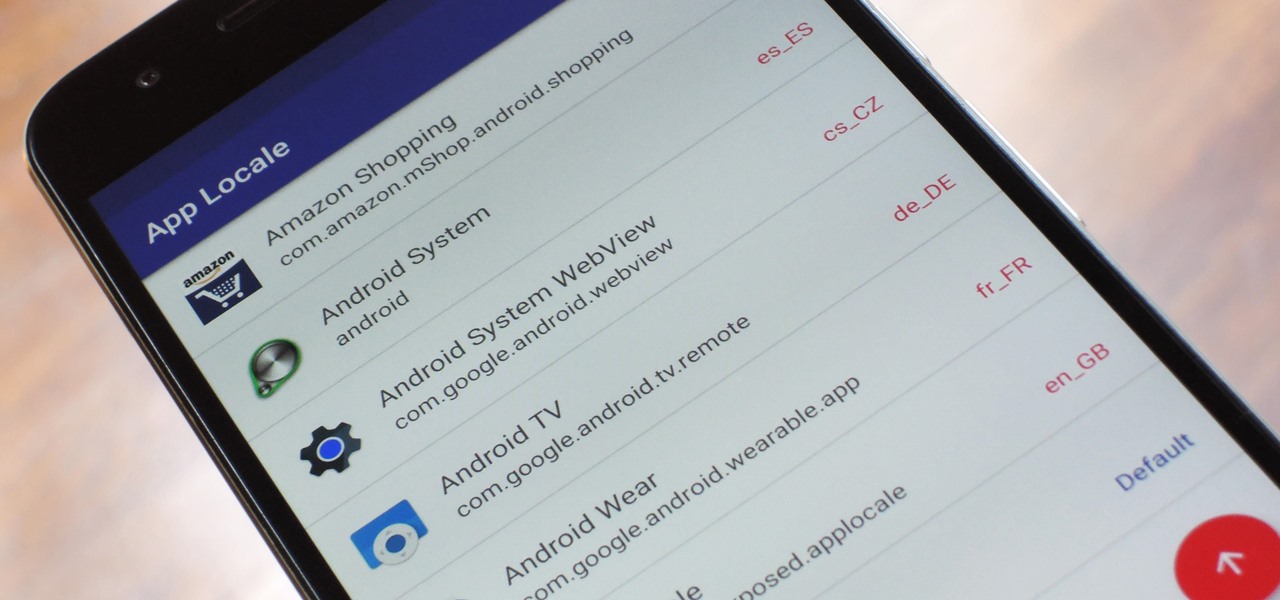
Android clearly wasn't made with bilingual users in mind. When you set a default system locale, every app on your phone uses that region's language—and there's no granular control here. This really becomes an issue if you use social media or news apps that are primarily in a different language, because apps are generally written in the developer's native tongue, then poorly translated to all other languages.

The default screen timeout on most Android devices is 30 seconds. This usually offers a good balance of usability and battery savings, but sometimes, you need the screen to stay on longer. For instance, practically every time I try to show something on my phone to someone else, the screen locks before they get a chance to see it. But increasing the system-wide screen timeout isn't a great solution either, because this can lead to unnecessary battery drain and even screen burn-in.

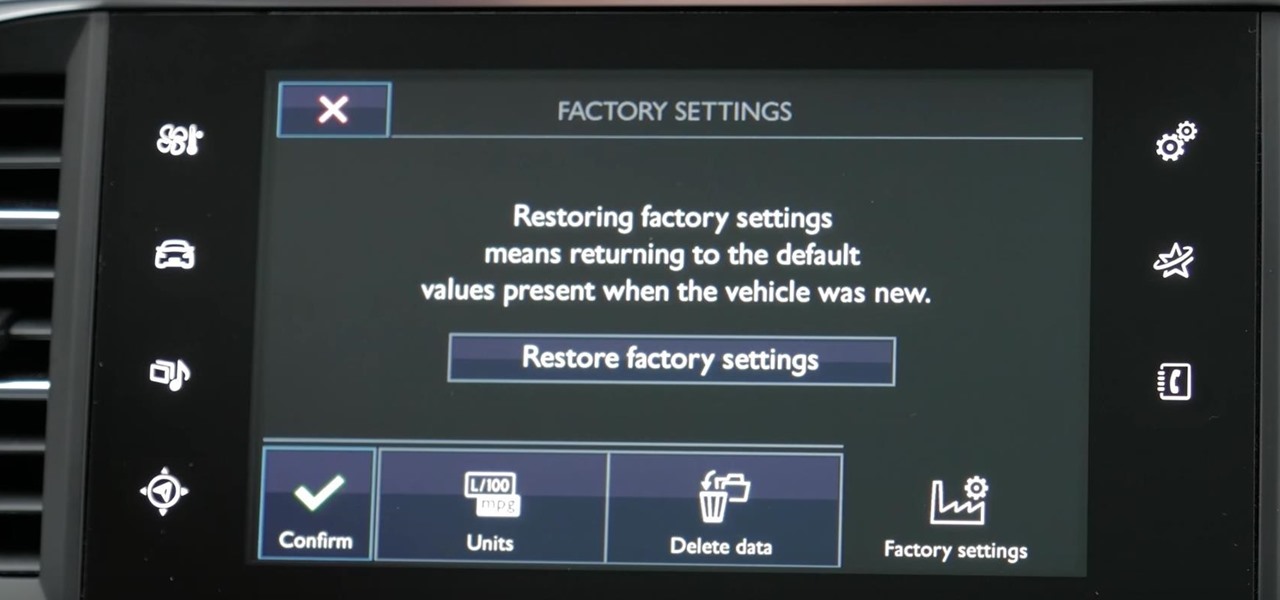
My Next Car how to video series - how to restore factory settings in Peugeot 308 iCockpit (2015, 2016 and 2017 Europe model). You use this if you want to return to the default values present when the vehicle was new.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

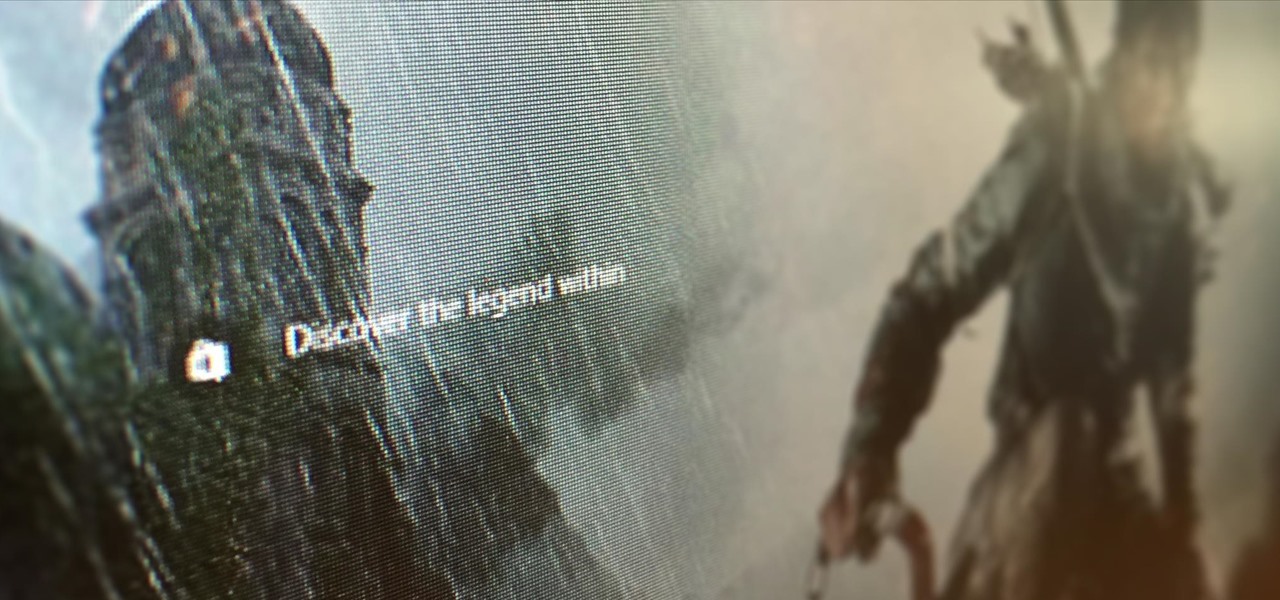
For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launching an Edge window once you log in. However, the aforementioned users have reported seeing the image below for the new Rise of the Tomb Raider game. Rather than taking you online in Edge to learn about it, you're given ...

By default, the Play Store app on Android is set to automatically update your apps in the background. This definitely makes it easy to ensure that you're always running the latest versions, but it does come with some downsides.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and novices alike.

Taste is certainly relative. When you look at Central American architecture and notice all of the bright pastel colors, then move just a thousand or so miles to the north and see that buildings in the United States are mostly painted in earth tones, this becomes abundantly clear. Imagine if you were to switch hemispheres altogether—what would you see in East Asia?

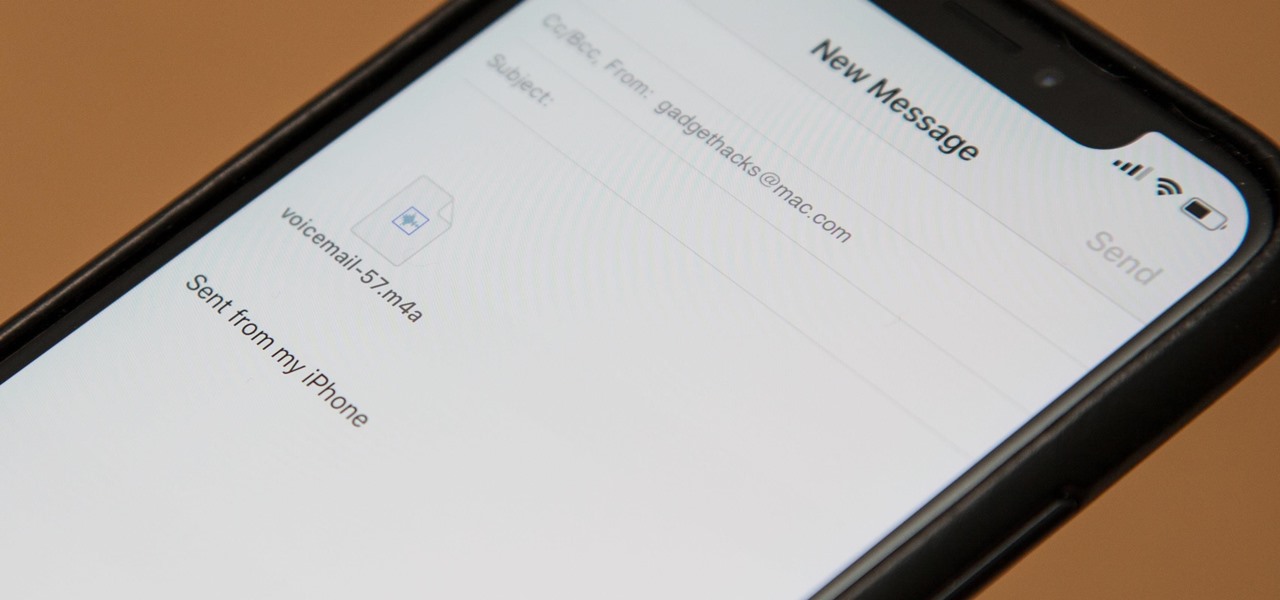
Eventually, your voicemail inbox on your iPhone will get full, and you'll have to delete some messages in order to make way for new ones. If all the voicemails you currently have are super important, you're not going to want to delete them before saving them first, of course. Luckily, this is a super simple task, and you can even forward them to someone else if needed.

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.

To use Apple Pay in iOS 8, you had hold your iPhone to the card reader first, and then you could either switch to a different card or pay with your default one. Now, in iOS 9, you can access your Wallet (which replaces Passbook) on the lock screen before you get to the reader.

While some of the additions to the emoji keyboard in iOS 8.3 have been criticized for actually doing the opposite of their intended purpose, they've been well received overall. But the biggest winner of the new emojis was one that actually wasn't even released—the "Vulcan salute" emoji.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

It's been over a year now since Google introduced a visual way to track down which tabs are playing audio in Chrome, something that was previously only available using third-party extensions. However, they still didn't give an easy option for shutting those tabs up without having to stop what you're doing.

There's no such thing as a perfect Android keyboard. Some, like Swype, have gesture typing down to a science, but lack in predictive technology. SwiftKey, on the other hand, boasts awesome next-word prediction, but less than stellar gesture typing. Many others are optimized for multiple languages, space saving, or emojis, but none are without their flaws.

Many of us were required to take a foreign language in school, but sadly, many of us are far from fluent in said language. To be a better citizen of the world, learning popular and rare languages would be dope, but in reality, that's probably never going to happen. If you ever do find yourself in a situation where you're messaging people who don't speak your language, there's an app that can help you.

Being in a band, I exposed myself to years of extremely high volumes, so I can't hear as well as I once did. I'm not concerned about going deaf or anything, but I tend to have the volume raised to the max, beyond the "high volume" warning, whenever listening to music on my OnePlus One with headphones.

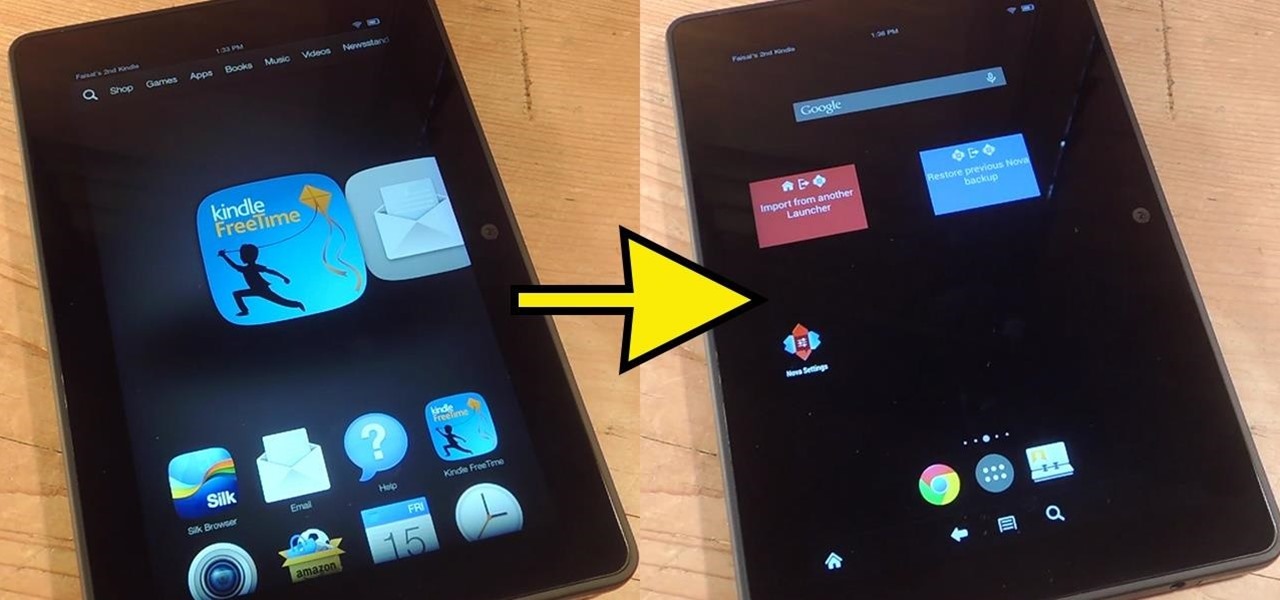
Whether if it's to play games or watch Netflix or YouTube, children love using our smartphones and tablets. As an uncle of many, I don't mind my nieces and nephews using my gear, but I do mind them opening apps they have no business being in, like my photo gallery or messaging app.

Stocked with a 7-inch LCD display and 323 PPI (pixels per inch), the Kindle Fire HDX is one of the best tablets on the market for enjoying some great literature or entertaining streaming services—and I take full advantage of what this device offers.

After a few unnecessary U-turns, I quickly realized that Apple Maps wasn't for me, which is why I hate that it opens as the default app any time I select a shared location or an address from Yelp. Copying and pasting the address to Google Maps isn't a huge deal, but it's certainly not as fluid of a process as I'd like.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

Though they share the same name, the HTC One and OnePlus One have completely different sound quality. HTC had put a lot of time and effort into fine-tuning their BoomSound technology, while OnePlus is still fairly new to the game, with brand recognition being a much greater objective than awesome speakers.

With so many keyboard options available for Android, there's no reason to limit ourselves to the default one, or to just the ones available in the Amazon Appstore. While the Appstore does provide alternatives, such as SwiftKey, it doesn't come close to the selection available in the Google Play Store.

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

This video will show you how to change downloading location from Google Chrome. If you download a special type of file often then you have to visit default downloading folder and move them to your preferred location. But you could set the downloading location to your preferred folder from chrome. Watch the video and follow all the steps carefully.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

This video will show you how to disable windows beep in your PC. If you are using windows 7 or 8 in your PC and don't want beep sound at the beginning. Watch the video and this video will help you to mute the default beep.

Amazon just signed a deal with HBO to host the cable channel's original content on its Instant Video service. For those of us with Amazon Prime accounts, this is great news—but there aren't any readily apparent options for playing it on Chromecast.