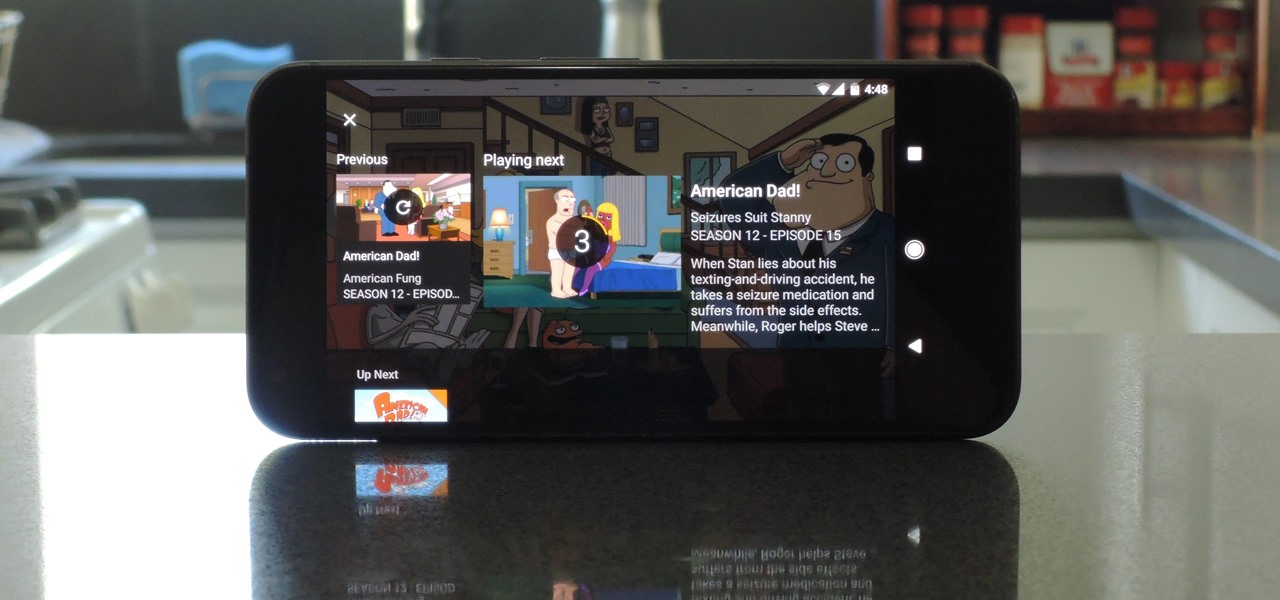
Just because Developer Options is hidden by default doesn't mean you shouldn't unlock it. While for rooters its benefit are obvious, even for the average user it opens the door for tools which enhance your experience. From animation speed to improving gaming graphics, Developer Options has something for everyone.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Samsung Experience (better known as TouchWiz) can take some time to get used to when you switch to a Galaxy from another Android device. It's a bit heavy-handed with the features, and many consider the UI theme to be a little over the top. Thankfully, there are several stock settings that can dial this back.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

While Android 9.0 Pie introduced some significant changes to the core operating system, the feature most people will be talking about is the native gesture controls. By default, these gestures are disabled — but for those of us wanting to try to the future of Android, here's how to enable the new controls.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

The Galaxy S9 and S9+ have terrific cameras that are packed with awesome features. But if you've grown tired of taking and viewing photos on only a part of your screen, Samsung has built in settings to let you take full advantage of their flagships' Infinity Display.

Google just dropped the new Android 9.0 Pie update for Pixel devices, and it's packed with cool new features. There's notch support, a new screenshot button, and even a way to edit screenshots after you've taken them, just to name a few. But one feature that's easy to overlook is the new transition animations, which have been completely revamped.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

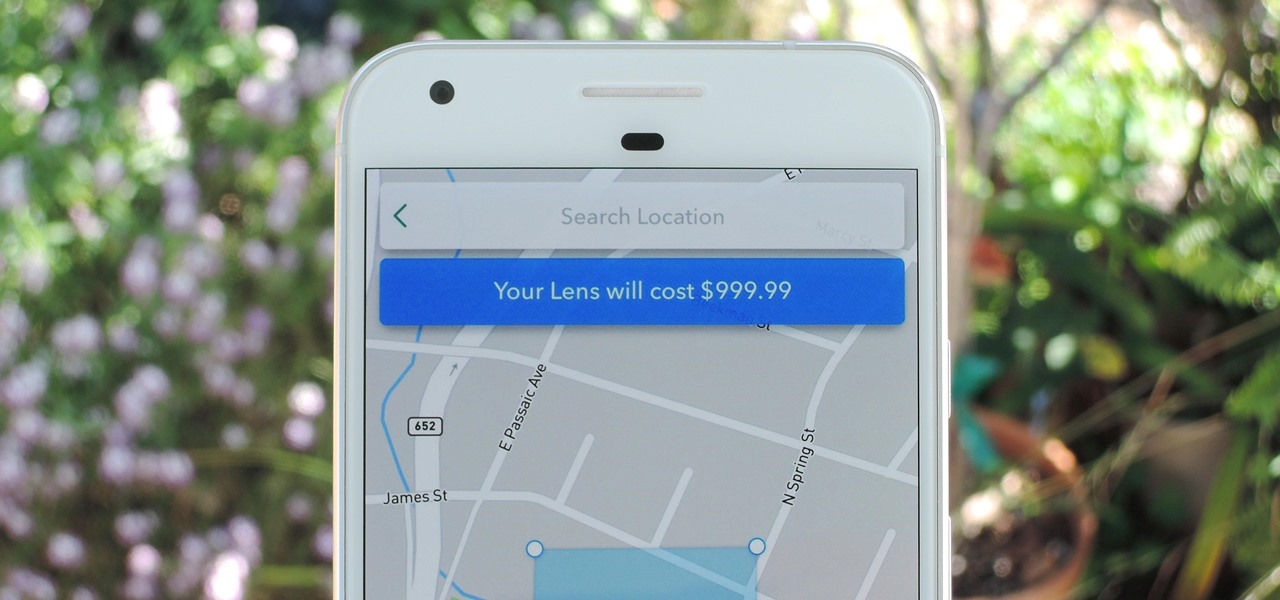
Snapchat just rolled out a feature that lets you create custom Filters and Lenses. While the average Geofilter won't run you more than a few bucks, it's not that hard to exponentially jack up the price. Amazingly enough, Snapchat's latest attempt to monetize their platform can ultimately cost you as much as $999.99. Ignore the penny, let's call that a cool grand.

Earlier this week, Snapchat announced a partnership with NBCUniversal regarding the 2018 Winter Olympic Games in South Korea. Starting on February 10, Snapchat will be streaming a feed of NBC's live broadcast of the Olympics in Pyeongchang.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The greatest pain in owning a high-powered gaming PC is the simple fact that you can't play it all the time. Sometimes you have work or school, and other times, you may just want to go mobile. When something like this impedes your ability to play PC games, you may end up settling for mobile games. What if, instead of doing that, you were able to play your PC games from your iPhone?

While the Twitch app for iOS came out way back in 2011, livestreaming iPhone games was a rarity until Apple recently updated its ReplayKit in iOS 11. However, Twitch hasn't jumped on the bandwagon yet, but that doesn't mean you can't livestream your iPhone games to Twitch right now.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

Apple's codec for photos and videos in iOS 11, HEVC (High-Efficiency Video Coding), as well as the container, HEIF (High-Efficiency Image File Format), result in a reduction in size for pictures and movies without sacrificing quality. Seems like a win-win situation, but Windows-users can't open the .heic extension that these files use. In order to open HEIC files on a Microsoft Windows PC, you'll have to turn to third-party apps and tools. One of these tools, CopyTrans HEIC for Windows, essen...

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Razer just released their first flagship Android smartphone, appropriately named the Razer Phone. While mobile gaming fans are sure to enjoy the Razer Phone, the buttery-smooth 120 Hz display makes this an appealing option for anyone in the market for a new phone. If you've just picked up the Razer Phone or it's piqued your interest, here are ten awesome tips to hit the ground running.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

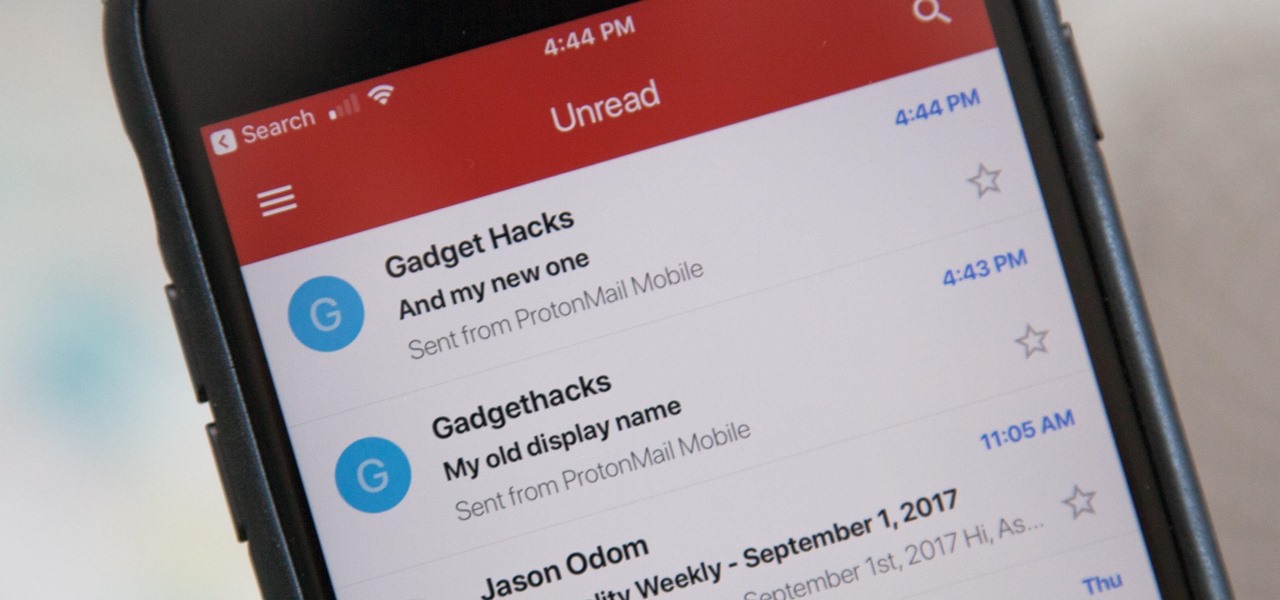
Your display name in ProtonMail is what email recipients will see when they first receive your message in ProtonMail, Gmail, or another email provider. You can choose this name when you first set up your ProtonMail account, but it can also be set up after the fact if you skipped that step.

Adding additional photos to a movie project in iMovie for iPhone is relatively simple, but incorporating more videos to your timeline is a little bit more involved, only because there's more that you can do. Unlike with photos, you can trim the length of new videos, select the audio only, and add overlay effects.

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."

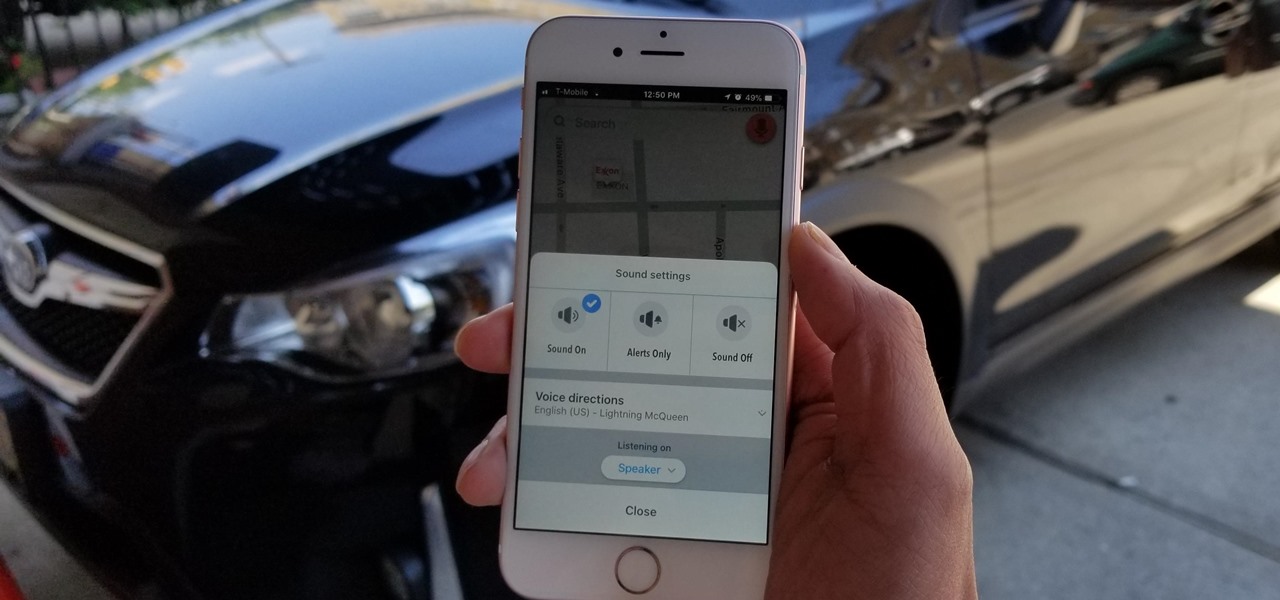
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

Your Apple TV is just that — your Apple TV, which means you probably want to personalize it a bit, to make yours stand out from everybody else's. And the easiest way to do this is by renaming it. If you live in an apartment building, this will help differentiate your Apple TV from your neighbors' when trying to use AirPlay.

If you're new to Plex, there are a couple of things you should know up front. First is how to use it — simply install the Plex server app on your computer and point it to your media library, which you can then access anywhere using the Plex app for iOS or Android. All of this is free.

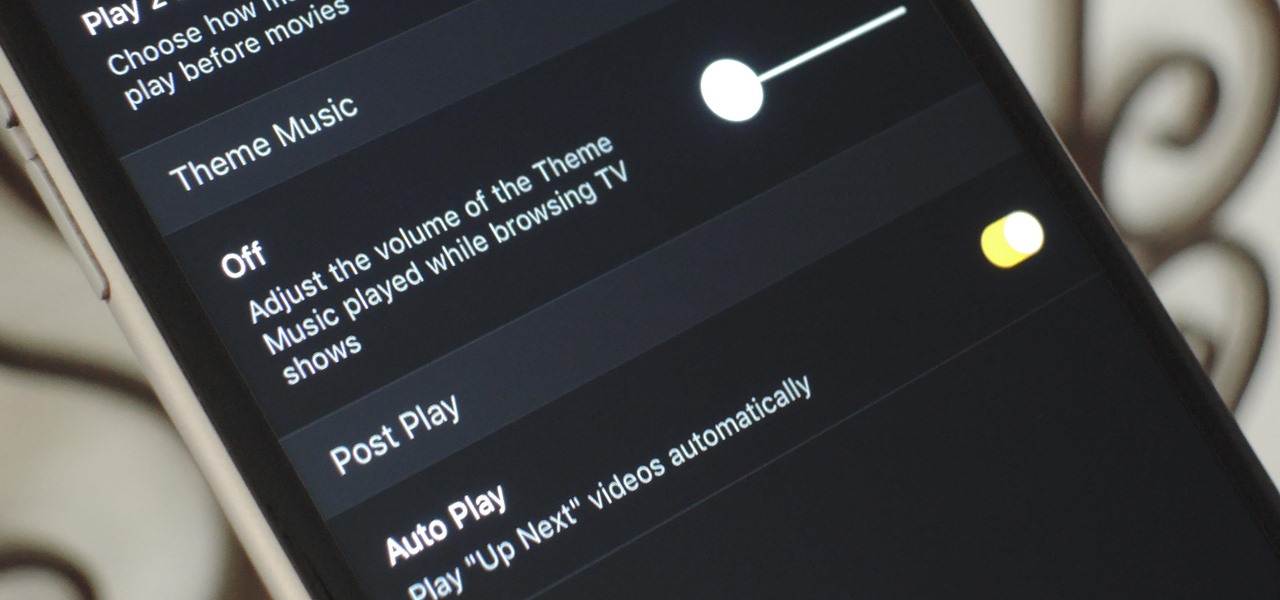
Overall, Plex is a great service. You just install the server on your computer, then you can stream your media library to wireless devices with the Plex app for iPhone or Android. But it does have one annoying feature that's enabled by default: Theme music plays automatically when you're viewing the details page for a TV show.

I couldn't live without seeing previews of certain notifications on my iPhone, but there are definitely some that I'd like to hide, either because they're annoying or because I don't want anyone else to see them. Previously, you could only disable notification previews for Apple apps such as Mail, Messages, Photos, and Wallet, but in iOS 11, you can disable previews for every single app on your iPhone.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

In a recent series of tweets, investor and entrepreneur (and NR50 member) Amitt Mahajan summarized the challenges and opportunities for iOS developers looking to leverage Apple's ARKit for augmented reality experiences.