
News: Gut May Hold Key to Infectious Brain Diseases
Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.


Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

As we slowly approach its January 3 start date, CES 2017 seems to be shaping up to be an exciting year for smart glasses as well as augmented and mixed reality.

Creating a dress, or any other clothes for that matter, takes quite a bit of design, planning, and manufacturing to get it just right. Fashion designer Jim Reichert put on a HoloLens and saved himself a bunch of time designing a dress through the use of a life-sized holographic woman.

While flying isn't easy, once an airplane gets into the clouds there isn't a whole lot to worry about—most of the work happens during takeoff and landing. Helicopter pilots, on the other hand, have a lot of dangerous obstacles (like power lines and buildings) to contend with. But, once again, augmented reality can save the day.

One thing you have to love about Google is their sense of humor. From their annual April Fool's Day pranks to the hidden Flappy Bird mini-game in Android to tons of hidden commands in Hangouts, you can just tell that those smart guys in Mountain View still like to have a little bit of fun with their work.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

With the DOJ attempting to rip Apple a new one and an Apple attorney firing back, the President offered his opinion on the recent encryption debacle between the FBI and Apple at SXSW, amidst some talk about the direction of today's tech industry.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

Smartphones and TVs aside, most of the electronics industry is focused on making everything smaller. From cars to cameras to computers to memory, we want power and convenience to go hand-in-hand. Professor John Rogers at the University of Illinois is ready for the next wave of medical tech with his smart electronic biosensors.
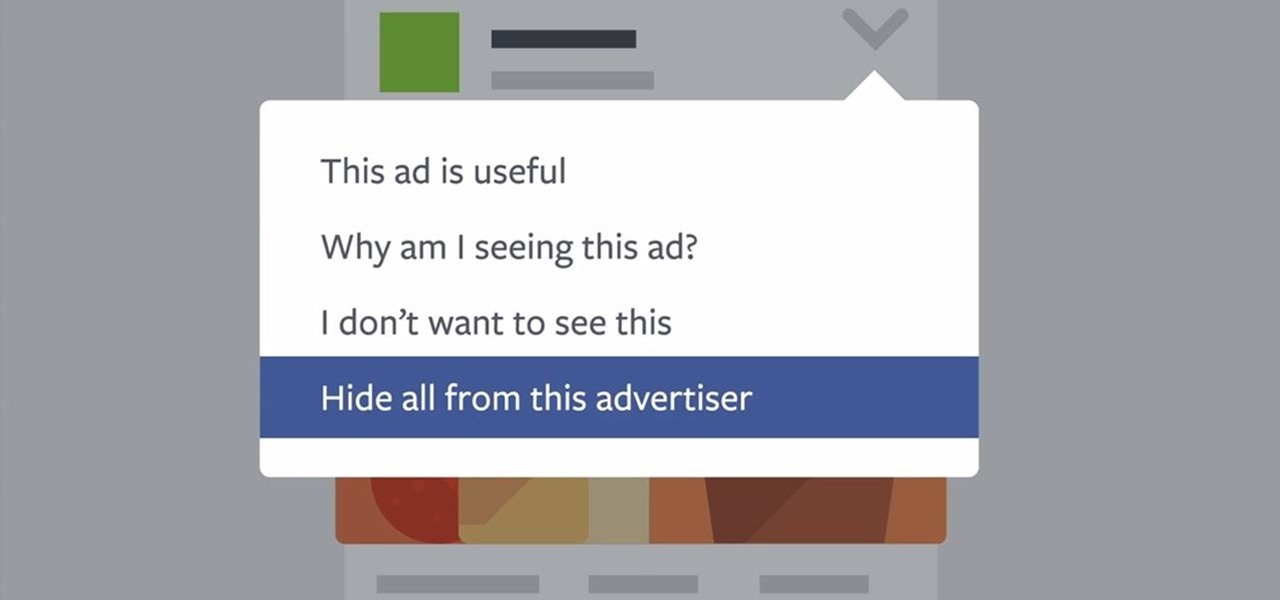
Facebook wants to take your browsing history and sell it to advertisers. Video: .

You already know that 3D-printing technology is swiftly evolving—it's been used to print balloon animals, bikinis, and house keys, and there's even an affordable home version of the printer, as well as one you can 3D print.

E3, or the Electronic Entertainment Expo, is the 20th annual trade show for video games and gaming tech. The event takes place on Tuesday, June 10th at the Los Angeles Convention Center, and you can watch a live stream of the event on Twitch.

Even if your business is mostly online and computer related you will need paper, which in other hand will need classifier to be sorted out and easily accessed. The paperless office is as much of a myth as the paperless toilet, so accept it, if you are serious about business, you need paper. Important contracts between customers signed on papers, leaflets, reminders, advert previews, drafts for preview at the table. The paper is always used even in today highly computerized epoch.

If new leaked images are to be trusted, an iPhone with a display around 5 inches will be released later this year. From Italian site Macitynet, images show a device that's stated to be the new iPhone 6 side-by-side with the new Samsung Galaxy S5. A couple of weeks ago, I showed you leaked internal emails and memos that suggested Apple was concerned with not only Samsung's marketing strategy, but about the industry trend towards larger devices.

When you come home from the grocery store, you probably put away every single fruit and vegetable in the bins and drawers in your refrigerator. Any fifth grader knows that fridges work to preserve food, thus everything should go in there, right? Nope!

Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android devices. Quite the opposite really, as we saw from leaks of its new Magazine UX. The new user interface was shown during Samsung's presentation of it's latest Galaxy tablet at this years CES, and as reported to Re/code,...

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.
In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

When most people think of stained glass, the first thing that comes to mind is a church, but it's become more popular in home decor as well. The biggest downside is that high quality stained glass pieces can be insanely expensive—and it's not an easy project to take on yourself.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

In the mid-80s, the Nintendo Entertainment System was released, and it not only revitalized, but also revolutionized the video game industry. With games such as Super Mario Bros., Legend of Zelda, and Metroid, the NES went on to become the best-selling gaming console of its time. Even though the console is several decades old, it is immortalized in the world of gaming and will forever be known as the standard for gaming consoles. As if that isn't enough, Instructables user fungus amungus has ...

In this episode of Steampunk Research and Development, our guest is Matt Silva, the co-founder and art director of Penny Dreadful Productions. While his current love is producing, Silva is also responsible for bringing to life some amazing creations in PDP's Remnant line, which we talk about on the show. Silva, who supports himself entirely from his work as an artist and a producer, talks about how he got to where he is today and offers advice for anyone interested in following in his steel-p...

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

The streets of Tokyo are about to get a lot scarier (or more awesome), after Suidobashi Heavy Industries unveiled their latest project: a 13-foot tall, customizable, piloted robot. It's armed to the teeth with a water bottle rocket launcher and a BB Gatling gun capable of firing 6,000 rounds a minute; all for the very reasonable price tag of around 1.35 million dollars.

Magnetic ink is generally used by the banking industry to allow computers to read information off of a check, but that doesn't mean you can't have some fun with it. The guys over at openMaterials have figured out a great recipe for a DIY magnetic ink that you can use for an interesting art project—or just to mess around.

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.