
How To: Use a 2-3 zone defense in basketball
Learn how to design a defense to stop dribbling penetration or passes to the middle. If you're a basketball coach, you'll definitely want to utilize this two-three zone defense.


Learn how to design a defense to stop dribbling penetration or passes to the middle. If you're a basketball coach, you'll definitely want to utilize this two-three zone defense.

If you think that card counting is only a thing in the movies then think again. You too can try a couple of methods to help you count cards. Like anything, the more you work on it the better you will be.

When Penguins Attack - TD hacks, cheats, glitches. How to hack the flash game When Penguins Attack - TD. Defend the human race against the onslaught of evil penguins. Watch this video tutorial to learn how to hack When Penguins Attack - TD with Cheat Engine (09/27/09).

Everyone gets an upset stomach from time to time. The first line of defense in this high-tech age is still old-time remedies! Watch this video to learn how to sooth an upset stomach.

Sword fighting, or saber fencing, is a recreational sport that tests quick action and solid defense. Learn more about saber fencing from our fencing expert in this free video series.

Would you like to improve your passing ability and start to rack up assists on the court? Are you needing to work on your defense? Learn these helpful basketball passing and defensive drills in this free sports video series.

Learn sabre parry and defense moves in sabre fencing, including beat touch, missed attack, and more with expert fencing tips in this free sabre fencing video series.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

To commemorate the rollout of the AR+ update for Pokémon Go, Apple CEO Tim Cook took to Twitter to promote and celebrate the moment his company's ARKit platform made possible.

Now that it has buried the legal hatchet with Meta Company, augmented reality startup Dreamworld has announced plans to open up pre-orders for its Dream Glass AR headset.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.
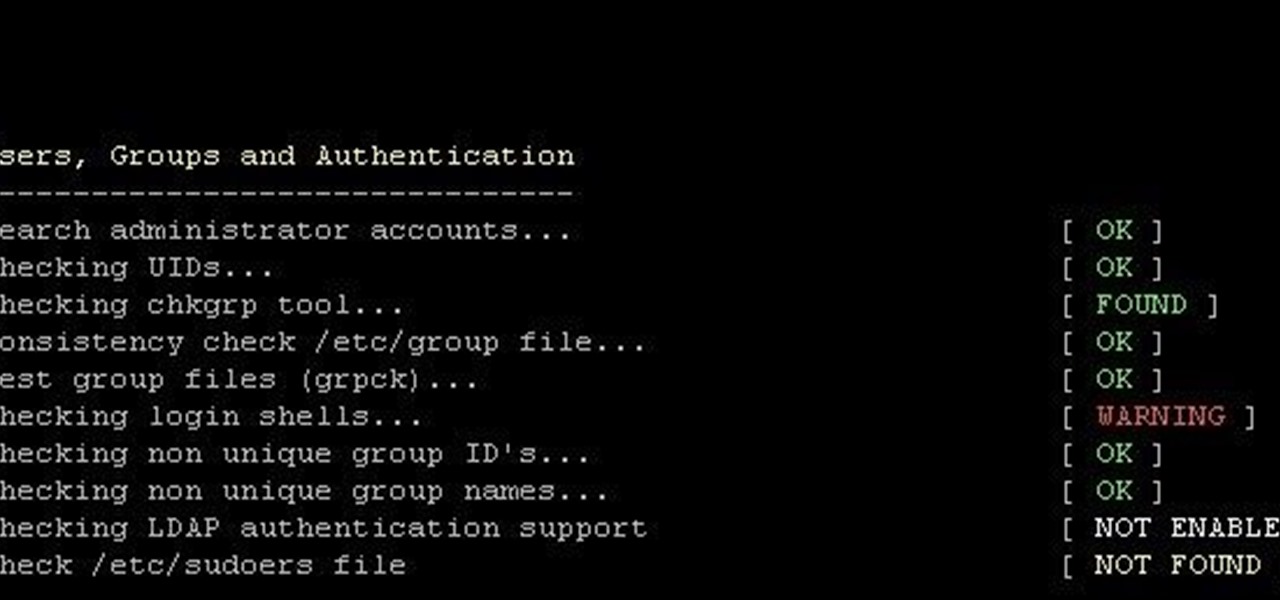
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

A field hockey midfielder is the quarterback of the team, and must advance the ball from the defense to the offense. Learn how to play midfielder in field hockey in this video tutorial.

For a field hockey offense to score, their attacking must be better than the defense's tackling. Speed and accuracy are essential for an effective field hockey attack. Learn how to attack in field hockey in this video tutorial.

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

This explores Fischer's opening strategies versus various openings. This video looks at one of his defenses against the King's Pawn Opening. The match was played in 1966 in Santa Monica against Wolfgang Unzicker.

Learn the correct position for playing defense on the low post as a basketball player.

Learn how to draw the defense and kick the pass on the basketball court with the help of this exercise.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

If you missed out on Black Friday this year, you've got a second chance at saving some big bucks on apps, mobile devices, HDTVs, and other tech. See below for all of the hot Cyber Monday deals from Amazon, Apple, Google, Microsoft, and other online retailers. This list will be continuously updated throughout the day, so bookmark it to stay up to date on all the of Cyber Monday discounts.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

Self-defense is essential in a violent society where anything can happen. Should you ever find yourself in a choke hold, keeping your wits about you and knowing what to do will help you escape safely. Watch this video to learn how to escape a choke hold.

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the shell four defense drill. The shell four drill is an effective way of training for basketball. Follow along with this video demonstration and improve your game with this drill.

This is a video of Peter Gade demonstrating backhand defense for going to the backhand side of the court, sorry no English translation of it.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, hosts can put an end to it.
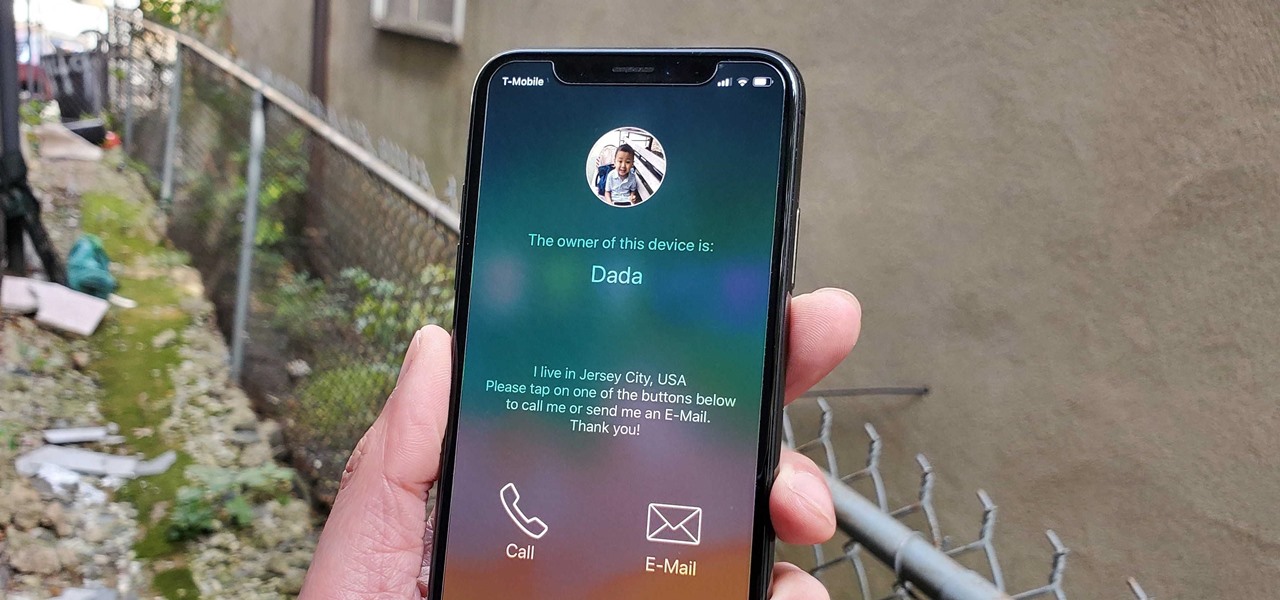
The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.