
Tips for Cold Season: How to Spread Fewer Germs When Sneezing
What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.


What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.

To shine light on the future of the relationship between humans and viruses, a team of researchers from the University of Oxford looked into the dim and distant past.

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Bad news, guys. The shelf life for liquor leftovers does not apply to your two-buck chuck. While an opened bottle of your favorite whiskey will stay respectable for ages thanks to its high ABV (which makes it inhospitable to outside elements), an opened bottle of merlot will sour quickly. However, it turns out that red and white wines have different life spans once they're opened—for reasons which we'll cover below.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

Living in Los Angeles has taught me one thing—parking is a luxury. If you are lucky enough to find street parking anywhere near your desired location, do not pass it up thinking you will get an even closer one. It does not exist. Looking for free parking? Get real. You can't even park at a busted meter in Los Angeles, despite state law saying otherwise. Now, finding a good parking spot is not just relevant for Los Angeles, but for other large cities and any other crowded areas, be it a shoppi...

Summer is the best friend of poison ivy, oak, and sumac. When the weather is hot outside, people spend more time in the great outdoors, which means more people accidentally running face first into some poisonous shrubs, leaves, and vines. If that sounds like you, instead of suffering through the itch or spending money on expensive pharmaceutical solutions, try some of these home remedies out.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

In this free video series, our karate instructor, Madison Warner will teach you the basics of Koden Kan karate, including the starting stance, blocking, punching, kicking, and even some self-defense techniques, demonstrated with a partner.

We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly but deliberately worked to build itself into a viable competitor in the enterprise space via its wearable display technology.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.
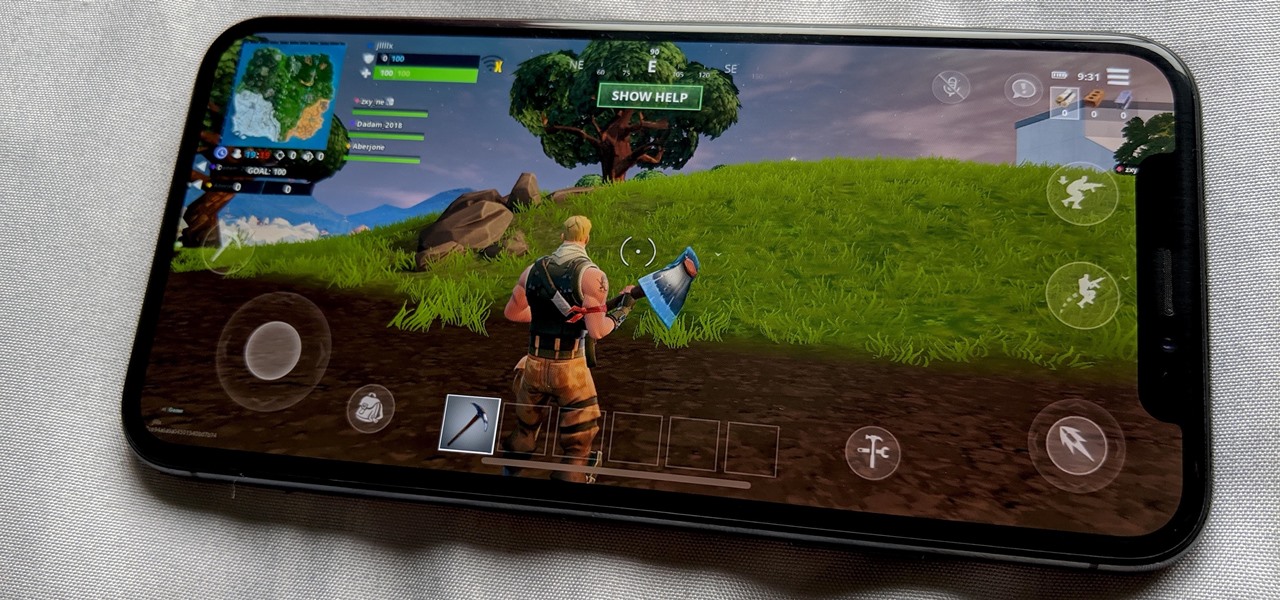
Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which multiplayer games are worth your time on Android or iOS?

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

Apple announced support for mobile driver's licenses and state identification cards in Apple Wallet back in 2021, and Arizona was the first state to jump on board in 2022. Fast forward to now, and only six states let you add a driver's license or state ID to Apple Wallet on your iPhone and Apple Watch. It has been a slow rollout, but more states are coming or are at least showing interest.