Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It looks like the dust is finally starting to settle on Google's POLED PR nightmare. The Pixel 2 XL — one of the most hotly-anticipated phones of the year — has been plagued by screen issues and worries. While it is certainly not without its faults, Google has created several software fixes and is offering a 2-year warranty for screen burn-in, so we can rest a bit easier about purchasing Google's latest Pixel.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

We've got Google Maps to help us out when we need to navigate outdoors, but Google can only map out so many indoor locations without getting creepy. And that's where Stimulant comes in. This "innovation studio" built a HoloLens app that lets you map out an area, define locations, and use the headset to get instant directions to any defined location.

Welcome back my friends !! Today we'll go through the second part of this C# series

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Mascara application for me is not only for the eye lashes, but also for the water line and eye lids. Through the different techniques I tried, I can certainly and undoubtedly say that it works like a charm and is truly two-in-one.

Eyebrows are made to frame your eyes. See how well-shaped and defined eyebrows creates a huge difference to one's face? Yeah, but most of the time, girls experience a hard time creating the perfect outline that would complement their eye shape and defining while making it look even is another story. This tutorial will help you (if you are experiencing eyebrow hurrahs as well) :

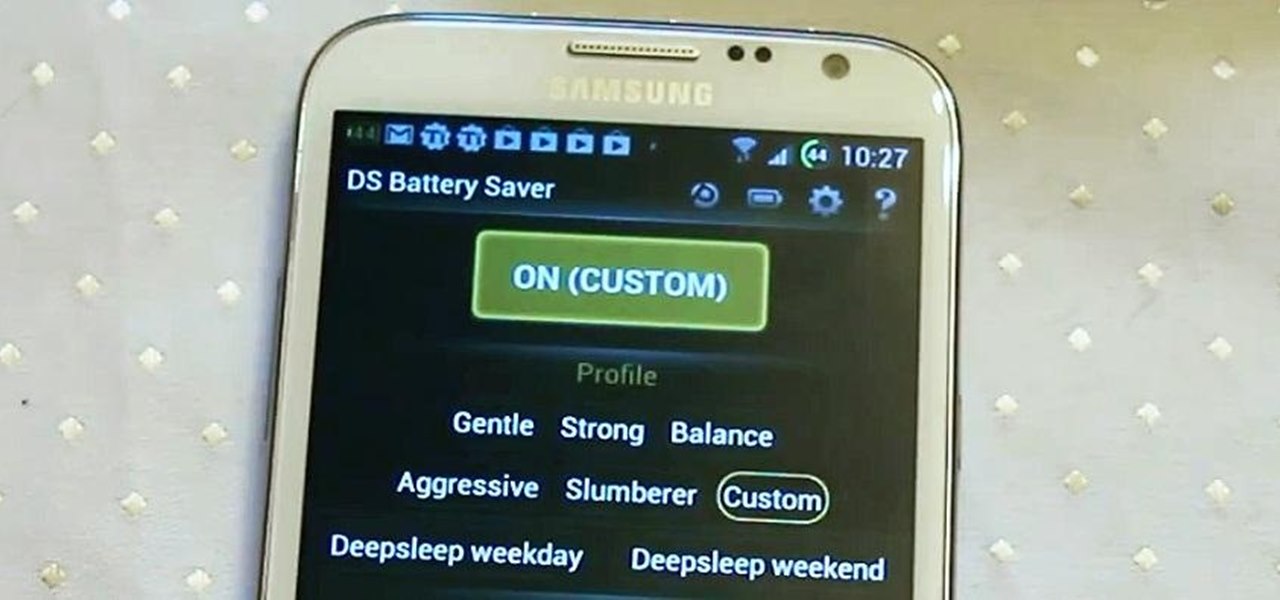
Newer smartphones are more power hungry than ever before, and the Samsung Galaxy Note 2 has a mighty appetite for amps that only Jenny Craig could possibly curb. On average, your Note 2 (or other Android device) lasts for what, a day, maybe two days before dying. Mine barely lasts 8 hours! This is thanks to all of the apps running in the background of your phone, even when you're not using them, eating through all of your CPU, leaving nothing but crumbs.

Cheetos fingers is defined as the unpleasant (but mostly pleasant), oddly-colored residue left on the thumb, index finger, and middle finger after ravenously eating through a bag of—you guessed it—Cheetos. It can usually be cleaned up by licking your fingers (my favorite) or washing your hands (boooooo). For the folks who enjoy the latter, Cheetos fingers are an annoyance. As someone who enjoys this idiosyncrasy, I've never quite understood the disgust in getting your fingers all cheesed up.

Ever since the mid-2000s, there's been a lot of bandying back and forth on the Internet over what exactly Steampunk is. Some people think it's one thing, others another thing, and some think that it shouldn't be defined at all.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

Researchers at Disney have demonstrated the ability to render virtual characters in augmented reality that are able interact autonomously with its surrounding physical environment.

Based on newly surfaced information, transparent smartphones like those teased in Iron Man 2 and those hand-tracking monitors made famous in Minority Report may eventually end up being "designed by Apple in California."

The laws and regulations in place in the US for driverless vehicles are a mess, but Republican congressional members say they can fix it.

Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

Unity released the Beta 5.6 on December 13 with a bunch of new upgrades in the works, including support for Vulkan, better instancing options, and more improvements to particles—to name just a few that are potentially relevant to the mixed reality community. And today, December 15, Unity has just released the EditorVR that we reported on a few weeks ago as a part of their "Experimental" builds.

When it comes time to buy a new smartphone, the sheer amount of options on the market can make you feel overwhelmed. There are Android devices of all shapes and sizes with different functionalities and price points, and now, even Apple has three unique iPhone models to fit various budgets.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

What's up guys! It's time to discuss strings in more detail. Review

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

Magic Leap is making it easier for developers to share their spatial computing experiments with other Magic Leap One users.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.