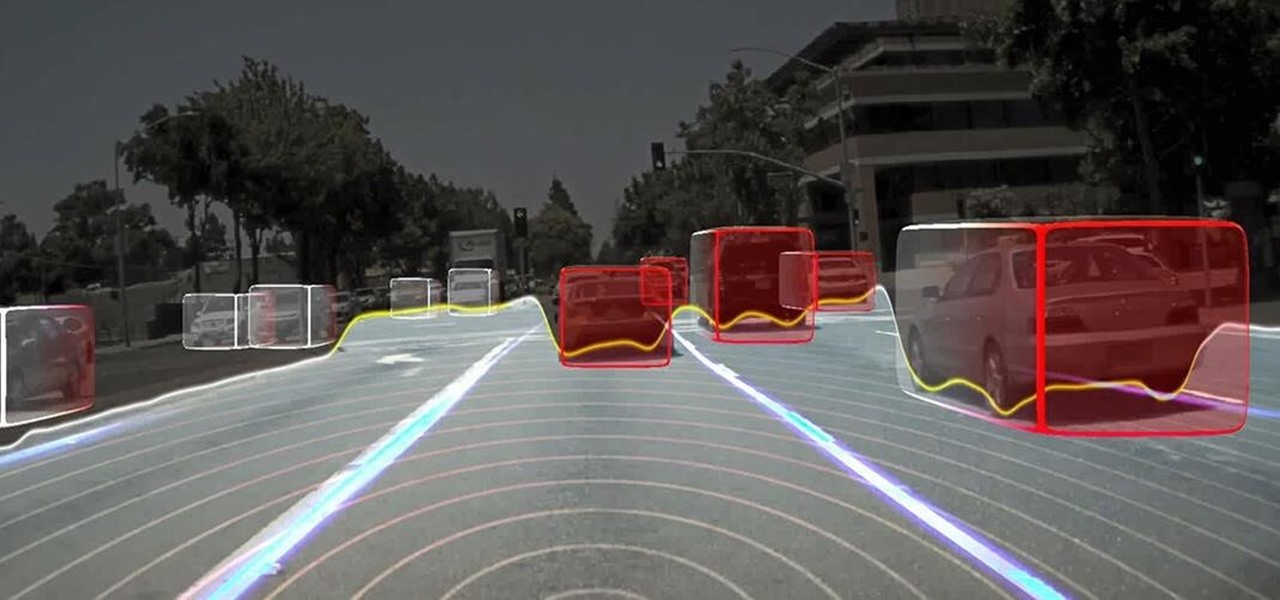
Blue has defined Facebook's color scheme since its inception. Both Facebook's main app and Messenger theme are blue, which means your chat bubbles, like emoji, and menu bar items are also. While certainly a satisfying color for chat, you may get sick of it after a while, especially when it's in every thread. Luckily, Facebook lets you customize the color of individual Messenger chats.

Magic Leap continues to launch new AR apps on its fledging app store before the door closes on 2018, and this time the app is a sequel from a veteran VR developer and early Magic Leap development partner.

A report by PwC highlights that immersive experiences in augmented and virtual reality represent the fastest growing segment of the entertainment and media industry over the next six years. News from two companies working in the industry, Fox and NetDragon, underscore the growth forecast.

John Legere seems to operate under the philosophy of, "If you're going to be late to the party, throw a better one." On Tuesday, Legere announced T-Mobile's intention to build the nation's first true 5G network, following AT&T's rollout of its "5G Evolution" network. A network which many said was, to put it in polite words, nonsense.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.
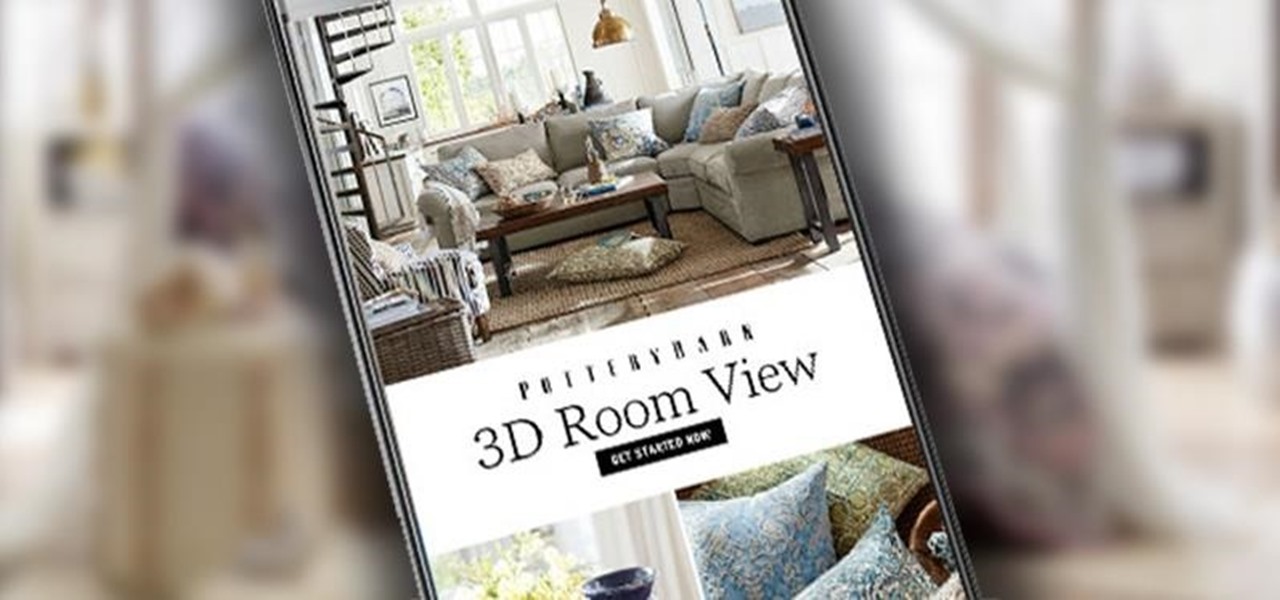
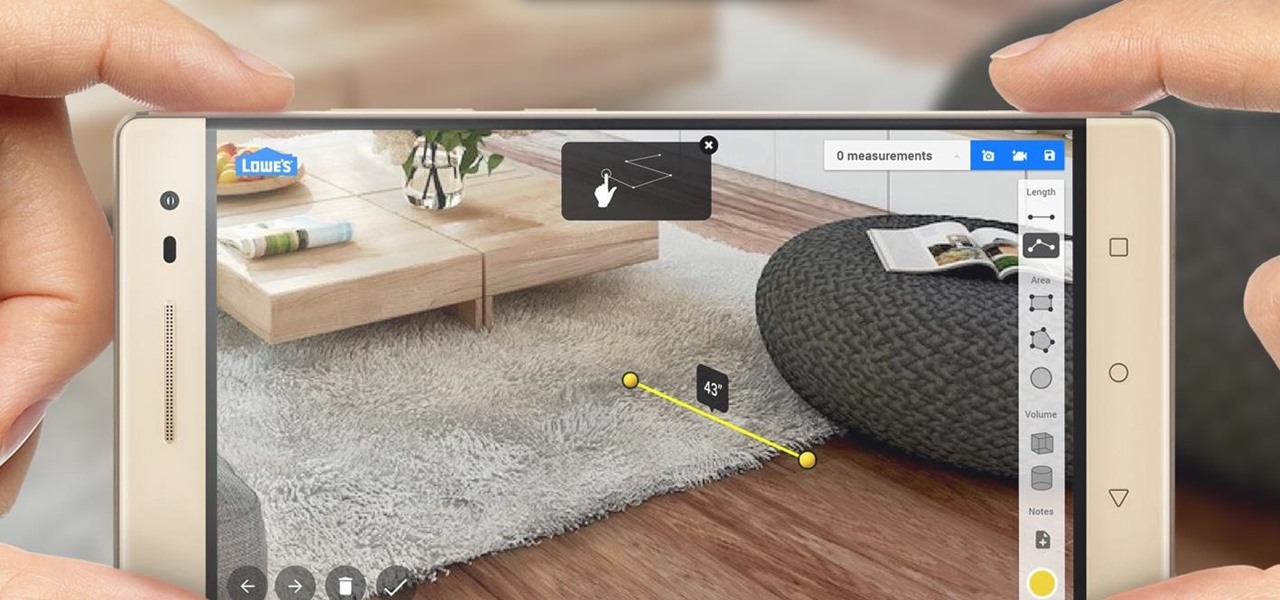
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.

If you've seen, heard, or even tried the latest virtual reality headsets, you've probably heard about something called "room scale." It's why the HTC Vive suddenly usurped the reign of the Oculus Rift while no one was looking, and it's exactly where Oculus hopes to catch up. Here's what it is and why it matters.

Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

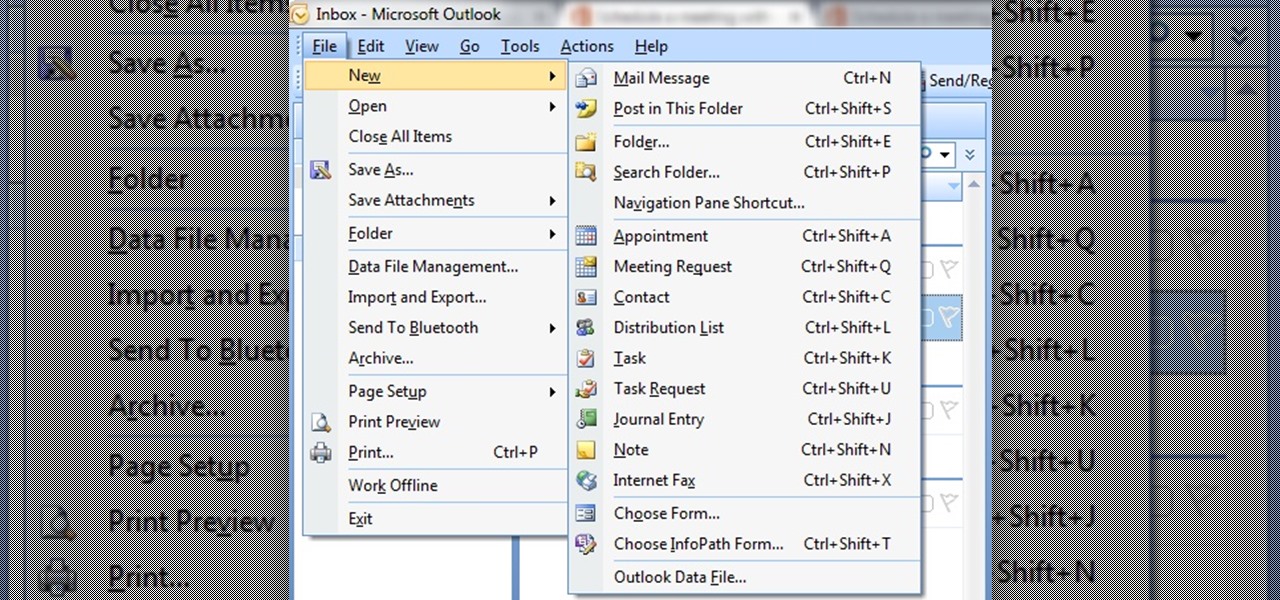
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Brought to you by Purdy Paints The art of painting requires excellent tools. And with so many options on the market, it can be hard to find a brand that works for you and your DIY project. That's where Purdy comes in.

Cast-iron cookware breeds a strange kind of obsession. When I got my first pan, I spent untold hours seasoning, cooking, researching the best non-soap methods to use for cleaning, and re-seasoning that thing. Finally, I became exhausted by the whole process and realized that you can skip seasoning a cast-iron pan as long as you use it regularly and clean and oil it properly in-between uses.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

Shark jumps Steampunk, experts unsure of the meaning. Cape Town -- In an unprecedented move today, a Shark have jumped a steampunk couple as they were attempting to work on their hobby steamboat.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Apple might not be ready to unveil its rumored-yet-unconfirmed smartglasses. But the iPhone's current depth-sensing hardware is proving to be useful for both smartglasses makers and mobile AR apps.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

As Magic Leap prepares to ship the Magic Leap One later this year, the company is putting its focus on mentoring developers and creators to build a content ecosystem for the spatial computing platform.

On Friday, audio giant Bose emerged as the latest, and perhaps the most surprising company to announce that it's planning to release augmented reality smartglasses.

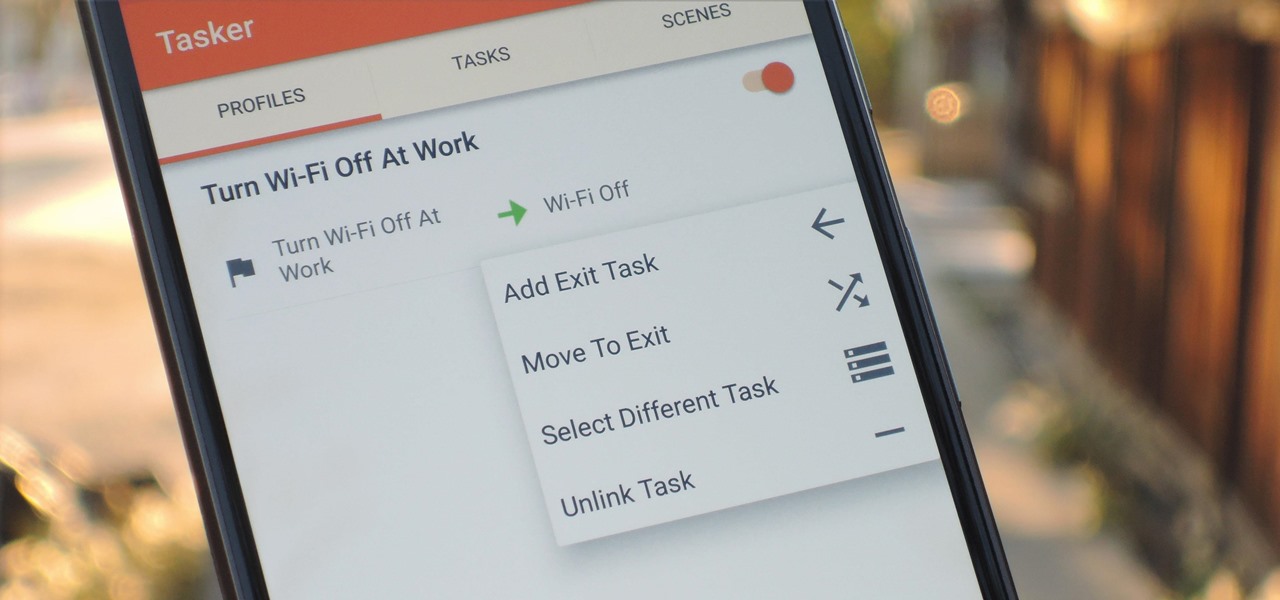
When you create a profile in Tasker, it will run a task as soon as all of the conditions in your profile are met. But what happens when the profile's conditions stop being met? By default, nothing will happen, but if you create an exit task, the automation tool will run that instead.

Zenge came to my attention as a free game on the Google Play store — it will remain free until midnight, so anyone catching this review on the 25th, download it ASAP — but I imagine it would be worth the typical $0.99.

Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.

A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Caramel is delicious, but it can be a tricky flavor to incorporate into baking. Traditionally, caramel is a liquid, and that doesn't always suit dessert preparation since adding extra liquid to baked goods can ruin them. So how do you get that buttery, toffee-like flavor?

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!