Most of the time, when I’m bored during math class, I play with my calculator to satisfy my boredom. Recently, I've discovered that when multiplying any number by 11, 111, or any number similar to it, that it has a pattern (though I guess everything in math has a pattern). I don't know if this technique is original, because I didn't read anything about this. It's just mere observation. If it’s a tried and true technique, let me know.
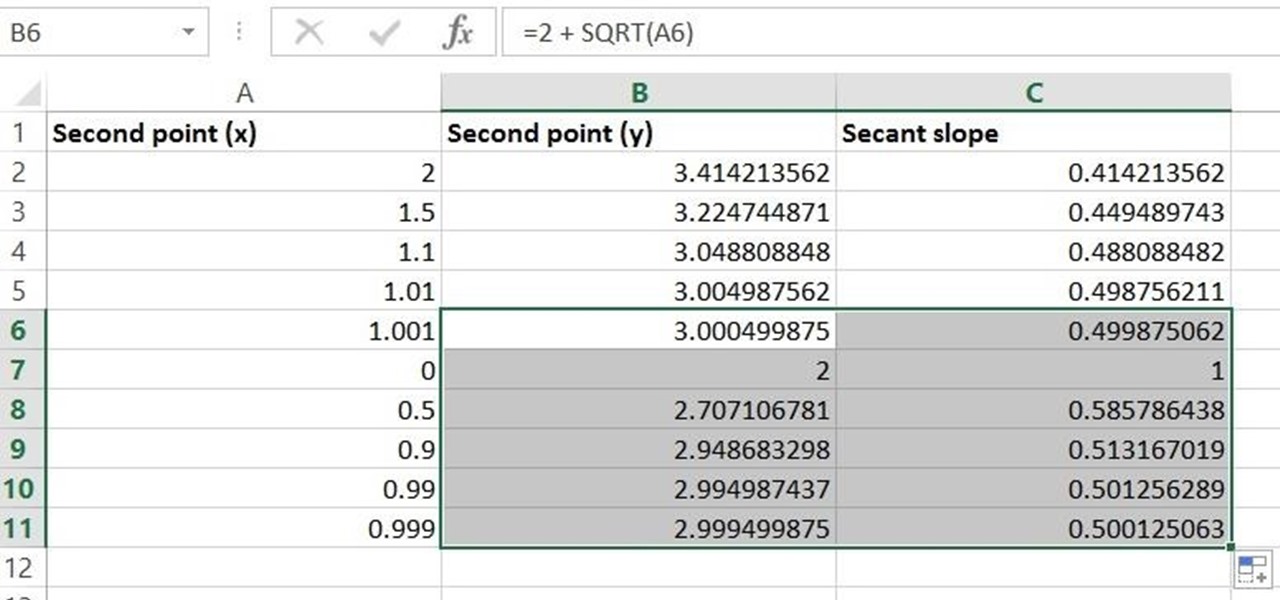
Given a function, you can easily find the slope of a tangent line using Microsoft Excel to do the dirty work. That is to say, you can input your x-value, create a couple of formulas, and have Excel calculate the secant value of the tangent slope. This is a fantastic tool for Stewart Calculus sections 2.1 and 2.2.

In this video, learn how to convert the American pound (lb.), a United States customary unit of mass, into kilograms (kg), a metric unit of mass in the International System of Units (SI).

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?
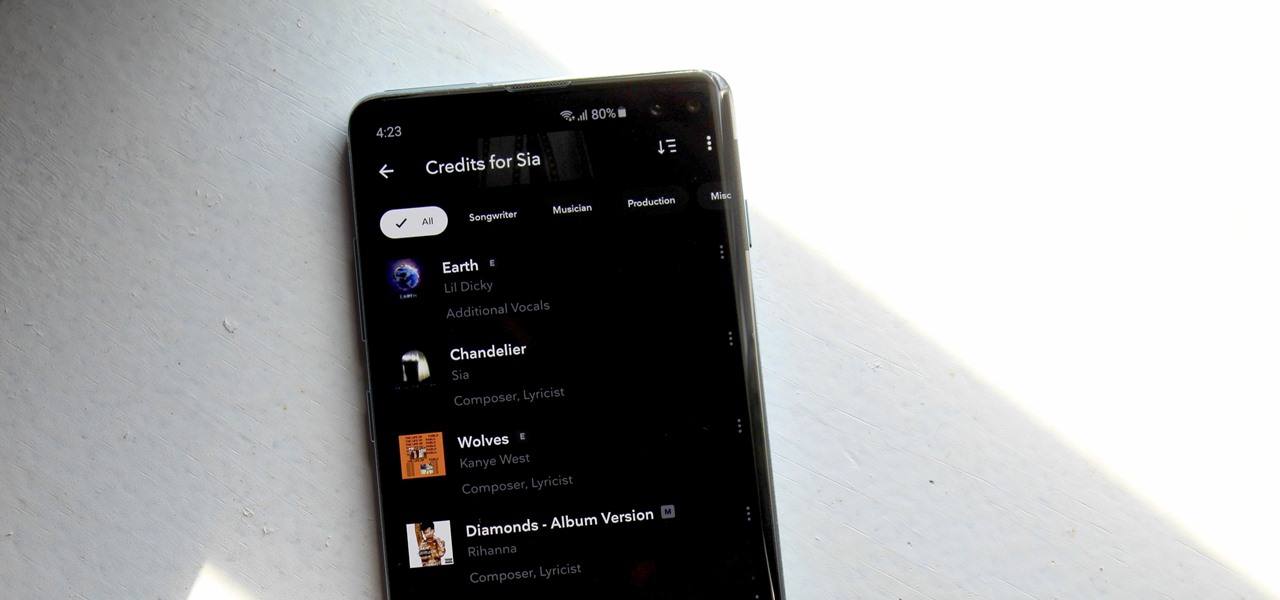
Contrary to popular belief, it takes more than just one artist to create the sound, lyrics, and vocals of a song. With most music being enjoyed digitally nowadays, it's harder to know all of a track's collaborators, as this info used to be in the CD booklet. Well with Tidal, you can now easily find this information and more.

Haptic feedback is one of the iPhone's most underrated features. With Face ID, you'll feel a satisfying tap or two when buying something in the App Store or iTunes, unlocking protected notes, viewing saved passwords in Settings, and the list goes on. For the first time, Apple has added haptic feedback when unlocking your iPhone via Face ID, as well as a way to disable haptic feedback for Face ID entirely.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Venom, the latest in a long list of comic book characters to headline its own movie, is known by comic book fans by his catchphrase, "We are Venom."

In recent years, medical professionals have demonstrated how the HoloLens can assist in surgeries, ranging from collarbone repairs to spinal surgeries to cosmetic procedures. Now, the largest children's hospital in the United Kingdom is also ready to deploy the technology.

If you aren't convinced that mobile augmented reality apps need occlusion (or you don't know what the word even means), you really need to watch the latest video from AR cloud startup 6D.ai.

Online shopping giant Shopify literally cannot wait for ARKit 2.0 to arrive via iOS 12 this fall to implement its latest augmented reality feature.

When you first update to iOS 12 on your iPhone, notifications on the lock screen and in the history will be grouped automatically into stacks based on a variety of factors for each app. For example, articles from Apple News will be stacked together based on sites. But you can also change this so that all alerts from a particular app will be grouped in one bundle, not separate ones.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

As Facebook, Apple, Samsung, and others offer augmented reality selfie effects and content that challenge its platform, Snapchat has continued to innovate with its augmented reality capabilities.

Snap Inc. added stickers back in 2016 to its Snapchat app, and it has been building on that functionality ever since. Now, you can add Bitmojis and even GIFs from Giphy to your photos and videos. Even better, you can pin any of these stickers to background items or moving subjects when sharing videos. That means stickers aren't pinned to the screen itself but to a real-world location.

One of the most popular mobile games out there for kids has added an augmented reality mode that brings the titular character into the real world.

In the latest example of life imitating art, IBM has applied for a patent for a video censoring system that looks a lot like the "Arkangel" child monitoring system from the latest collection of modern sci-fi fables from Black Mirror on Netflix.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

When it comes to streaming your favorite movies and TV shows, there aren't many media players that are better than Kodi. With its fast performance and easy-to-use interface, it is definitely one of the best options. But what really sets it apart is its ability to add functionality.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

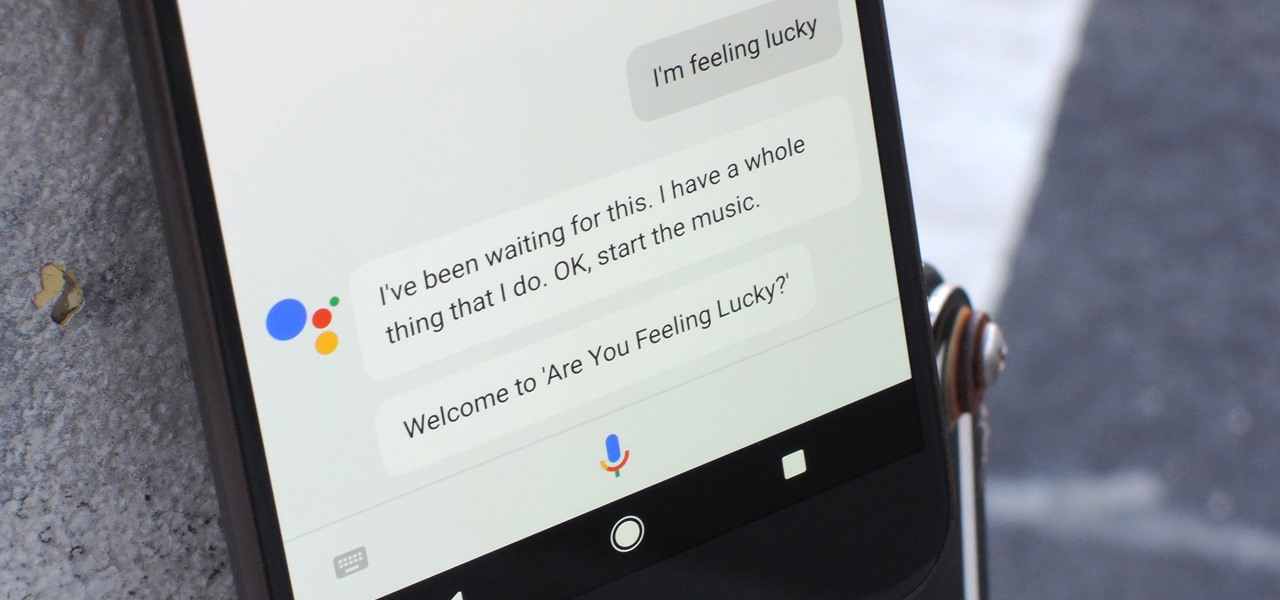
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

If you've ever wanted to see a selfie stick in centuries old works of art, now's your chance. The Art Gallery of Ontario is launching an exhibit called "ReBlink." The exhibit uses augmented reality to give modern updates to their paintings which visitors can see through their smartphones or tablets.

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

The list of HoloLens applications continues to grow as more companies discover ways to enhance their operations using augmented reality. Air New Zealand is the latest to show interest in the technology, demonstrating their vision for AR in a new concept video.

Intel launched their Advanced Vehicle Lab in Silicon Valley this week, and the tech giant is now on the hunt for potential partners.

Disney is gearing up fully autonomous vehicles that will shuttle you and your family from the parking lot to the amusement park, stress-free. Well, as stress-free as you can get while introducing grandma to the concept of a car with no driver. No, grandma, Satan is not "steering this contraption." At least, we don't think he is ...

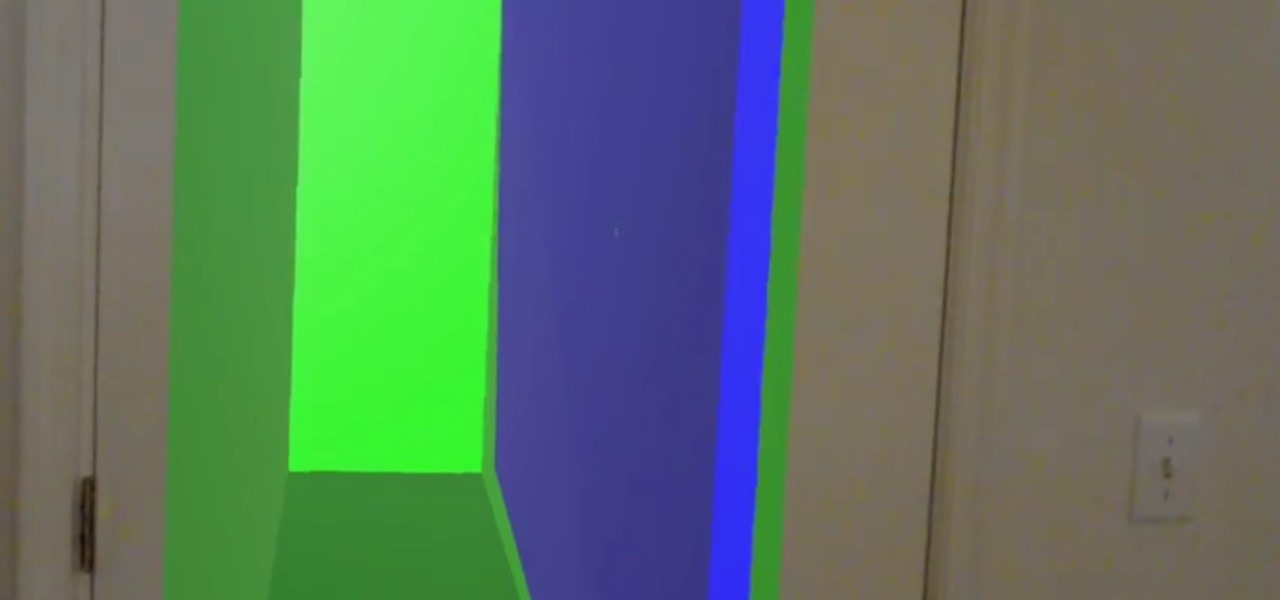
Once mixed reality technology is more widely available and realistically priced for consumers, using the tech to create the illusion of a larger space, will likely be a favorite use for mixed reality in places where real-estate is expensive, people tend to live in smaller homes and work in tighter offices.

Here at NextReality, we talk a lot about the many different ways of controlling holograms in the HoloLens and other augmented and mixed reality devices; New and creative ways are coming more and more every day. Most recently is something called the HoloSuit. In the 25-second clip below, you can see a woman moving the arm of a jacket which in turn moves a 3D model of Darth Vader on the screen. It's a simple idea with big potential.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

There are literally hundreds of granola recipes floating around the internet—but I can tell you right now that they're all completely unnecessary. You don't need a recipe to make granola; I've been making granola for years and have never once used one!

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.

Five Phases of Hacking:- The five phases of Hacking are as follow:

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)