Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

I consider myself a master of emoji, crafting complete sentences and paragraphs using strictly ideograms and smileys. However, everyone seems to have their own interpretation for each little image, so my elaborately clever emoji-only sentences can get lost in translation. But there's an easy way to translate emoji into their exact meaning, as well as decode everyone's mystifying emoji talk.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

This is a simple pattern, designed to produce a well-fitting mitten. Both the right and left mittens worked the same up to the shaping for the top of the mitten. A slight adjustment for making one right and one left, then they are worked the same. The gusset for the thumb constructed with the increases made in the center of the gusset, rather than on each side. This makes it easy with a minimal amount of counting stitches as you go. I have been crocheting for 56 years. In doing research for w...

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

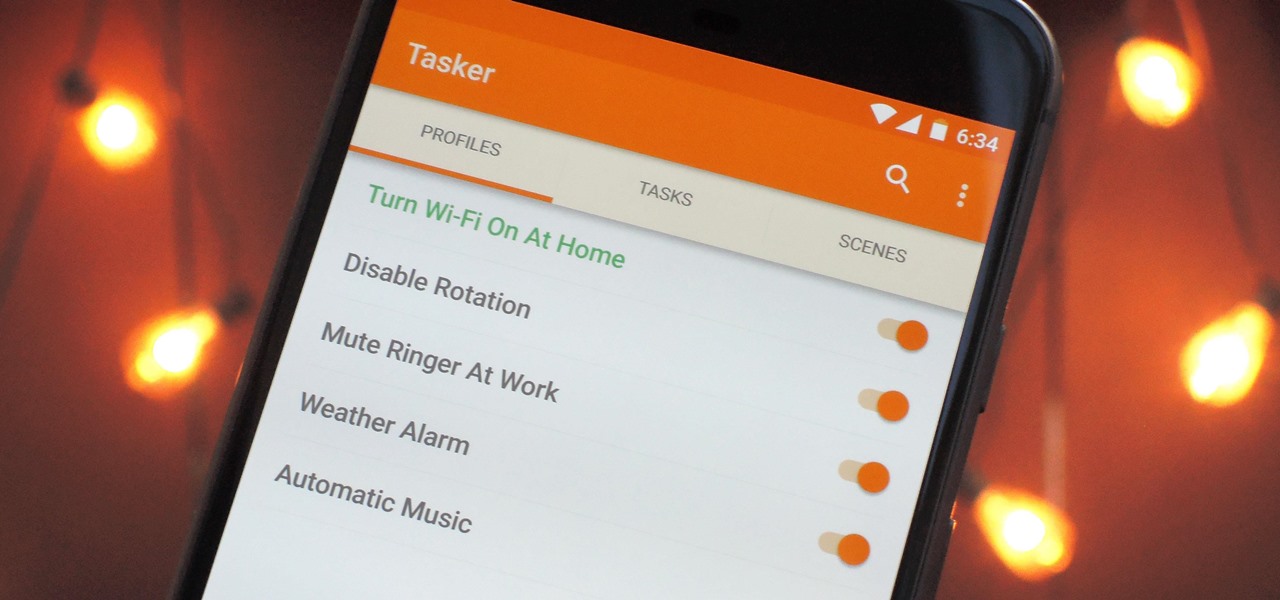
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

There's three types of animal lovers in the world. The first are your basic pet owners. The ones with a

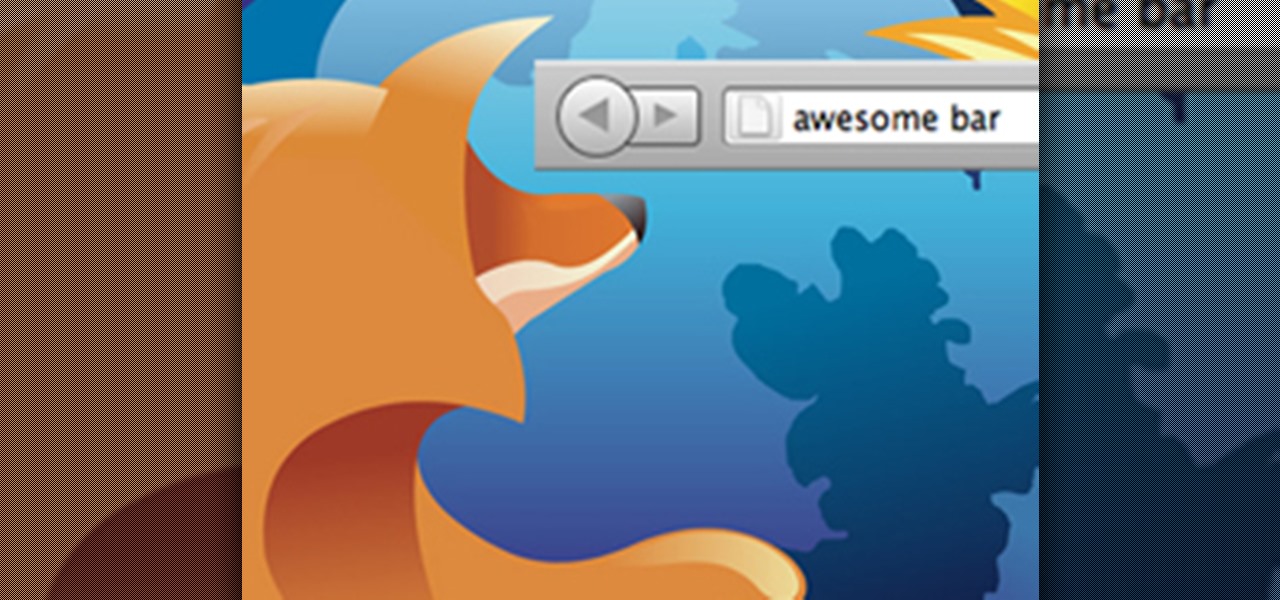
Getting used to your new Firefox 4 web browser? If so, you might have seen some improvements in the Location Bar. The updated features make browsing the web a cinch, so it's no wonder why more and more Internet junkies are calling it the Awesome Bar. It's faster and easier to use, and there's even some optional tweaks that you can employ to make your Internet experience smooth and effortless.

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.
Dimensional analysis is the process of analyzing units to decide which conversion factors to use. You can use this in real life if you want to figure your gas mileage. Here is a link to a website to help you Dimensional Analysis definitions | Quizlet.

No matter what word game you're playing, whether it's Scrabble or one of its near-homogeneous counterparts like Lexulous, Wordfeud or Words with Friends, one of the easiest ways to stay on top of your opponent is knowing all of the legal two-letter words you can play. You're not going to win by only playing two-letter words, but there are definitely occasions when the game could slip from your hands by not playing them.

This video demonstrates how to use Spotlight or Finder to find files & folders in Mac OSX. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to find files & folders in Mac OSX, For Dummies.

Interested in creating your own dynamic, web-based applications using Microsoft Visual Web Developer? In this installment from the Absolute Beginner's Series of video SQL tutorials, SQL Server beginners will learn about tables and definitions of data types, properties, keys, etc. in this second video. Find out how table rows, columns, and fields interrelate and whether columns can be empty. For more information, as well as tips for being a more effective user of Microsoft Visual Web Developer...

As touched upon in the past, knowing all of the possible words you can play is key to being a better Scrabble player. If you don't have the vocabulary, then you can't compete against the best of the best, and you'll never even get the chance to spar against professionals such as Nigel Richards, Joe Edley, Andrew Fisher, and Wayne Kelly.

Here are some charts I made to help you master crafting recipe levels. Don't forget to note the rewards at the bottom of each chart!

I first heard the term molecular gastronomy while watching an episode of Bravo's Top Chef a few seasons back. Intrigued by the concept, I sought to find out more about this modern, deconstructed type of cookery. If you happen to be around foodies and the topic of molecular gastronomy comes up (which very likely will at some point) you'll want to have a few points to contribute and maybe even give them a run for their money.

The Funny Thing About Dying - A Story of Coping With Loss

The provenance of this Sci Fi Airshow is unquestionable. With decades of experience interpreting science fiction from a written to a visual medium, Bill George is the perfect tour guide for this fantastical, photoshopped exhibit. Assembling the collective imagination of multiple authors into one Airshow is a rare treat.

OSPD1 In 1978, the first SCRABBLE Dictionary was conceived and published by Merriam-Webster, with the help of the National Scrabble Association (NSA). The idea was to include any word that was found in one of the five major dictionaries at the time:

So I have been wondering this for a while now. What exactly is steampunk? I know a little bit about it but I feel as thought the internet definitions can only give so much information. What do you guys think? Is steampunk a lifestyle? A fiction base? A for of a art? I think that steampunk has way more potential than people think. Share your ideas on what you think steampunk is and what you would like to see be done with it!

Via WonderHowTo World, SCRABBLE: Dirty SCRABBLE. Everybody likes to play dirty, but we're not talking bluffing with fake words or closing up the board—we're talking actual "dirty" and offensive words.

Dirty SCRABBLE. Everybody likes to play dirty, but we're not talking bluffing with fake words or closing up the board—we're talking actual "dirty" and offensive words.

I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:
1.) If you do not know something, keep our mouth shut.* No-one, I repeat no-one, is interested in your uneducated guesses about why something is the way it is, or why someone did something a certain way. At best, you will trick them into temporarily thinking you know what you’re talking about. At worst, you will convince them that you are speaking the truth and they will perpetuate your bullsh*t to others. Do not contribute to making the world a more foolish place just because you had to say ...

MIMESIS n pl. -MESISES or -MESES mimicry MIMETIC adj 61 points (11 points without the bingo)

FEAZING 70 points (20 points without the bingo) Definition: fazing; disturbing the composure of [present participle of feaze]

When you look up the word free in the dictionary, you'll find a lot of definitions, but in the days of digital dependency and a falling economy, free only means one thing—expensive stuff for nothing. And if you own a Windows computer, one of the best sites to get free software from is Giveaway of the Day.

The only thing better than successfully pulling off a new experiment is doing it with household materials. You get to laugh in conceit as professional scientists everywhere spend all their grant money on the same project you just accomplished with some under-the-sink chemicals! However, there are times when DIY gets dangerous. Some household chemicals are not pure enough to use and some are just pure dangerous. Let's take a look at two problems I have encountered in the course of mad sciencing.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.

COXSWAIN v -ED, -ING, -S to direct (a crew) as coxwain 70 points (20 points without the bingo)