Interested in pen spinning? Want to pick up a few moves? Pen spinning is the skilled movement of a writing instrument or pen with one's hands. It is used as a source of self entertainment (often for students), but there is a great deal of pen spinning culture (competitions, websites, etc.). Watch this pen spinning tutorial video and learn how to perform the "Double Charge" move.

ICELED UFO is a complete automotive underbody lighting kit consisting of four ICELED tubes, an advanced Electronic Control Unit and a wireless Infrared handset that allows the entire system to be remote controlled from inside or outside the car. The ECU can independently address all the pixels in the tubes allowing them to project patterns ranging from complex all the way down to a single color on the ground. The ECU also provides ICELED data for synchronous control of additional ICELED light...
It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

Google's Pixel smartphones have earned a reputation for taking great photos without relying on top-of-the-line camera sensors. Instead, Google leans on the software side to squeeze super images out of its camera. This also enables them to roll out new features out to previous-generation devices.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

Software issues occur more frequently on jailbroken iPhones, though, they're usually minor bugs that can be fixed easily with a respring. But if your device freezes up, restarting is the only way to get back to normal, which also means having to re-enable your jailbreak. There is one way, however, to respring without interacting with the touchscreen and having to re-jailbreak.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

The "Albums" tab in Photos is great for sorting through the images and videos on your iPhone since you can narrow things down by your recent pics and recordings, apps used, media types, people, places, and so on. If you never look at all of those folders, however, it could feel like an overwhelming cluttered mess. Plus, there may be some collections you don't want others to see.

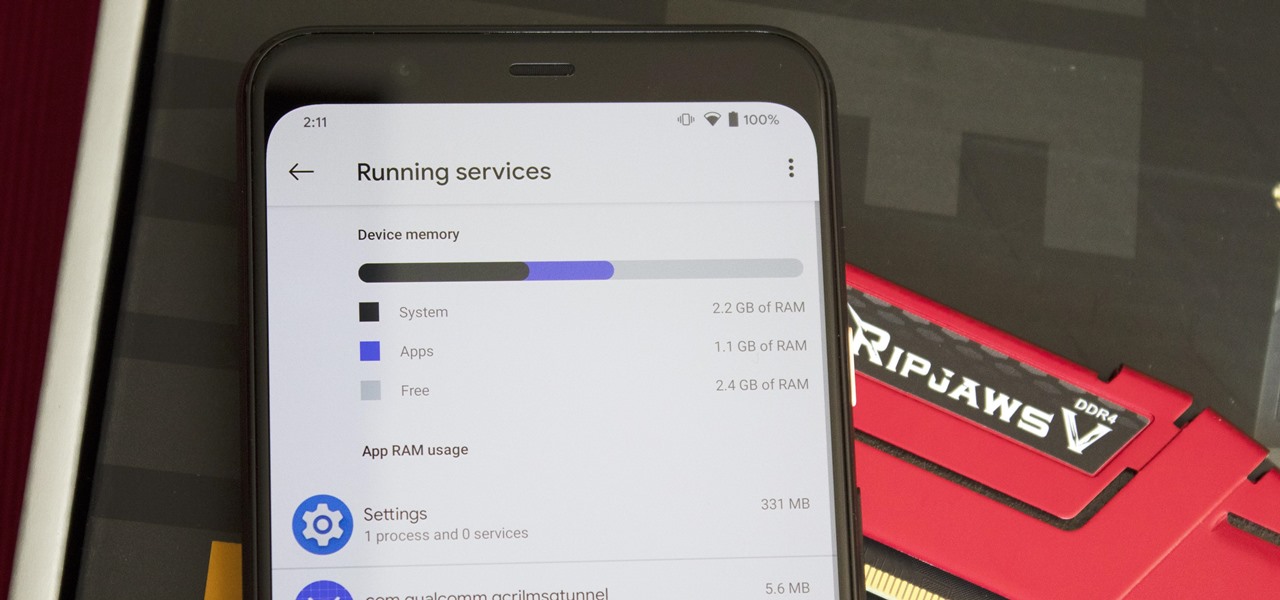
Not every app is designed well. With nearly 3 million apps on the Play Store and countless more that you can sideload from other sources, there are bound to be a few stinkers. And many of them do a terrible job using RAM.

In a departure from Apple's newer iPhone models with Face ID technology, the 2020 iPhone SE goes back to the old days where the Home button ruled, and Touch ID was the biometrics method. But if you've never owned an older iPhone with a Home button, something as simple as shutting down and restarting the iPhone SE could elude you.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

In older Android versions, you could flood your status bar with a wall of notification icons. But starting with Android 9, Google made it to where you can only see four icons by default, and it was mostly done to accommodate phones with notches. But Google's only notched phone is the Pixel 3 XL, so what if you have literally any other Pixel?

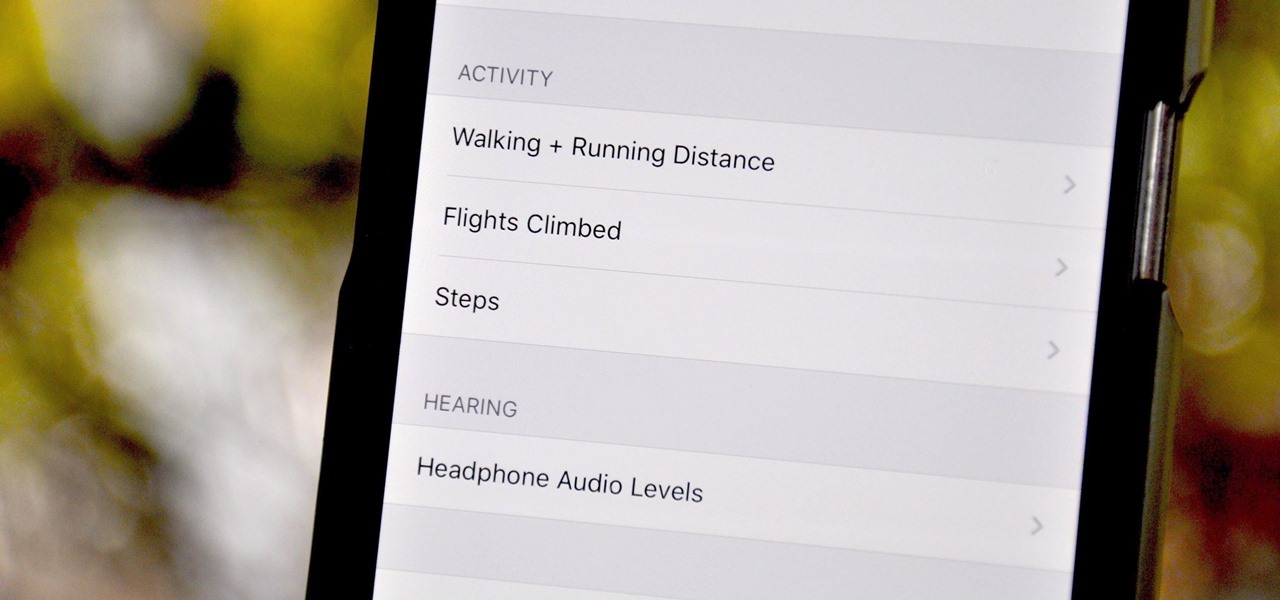
Your iPhone tracks how many steps you take, how far you walk, and how many stairs you climb each day. That may seem a bit frightening, but it's all for a good reason: the Health app stores this data so you can view your progress in one place. But interestingly, opening the Health app isn't the easiest way to view this info.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

The long wait is over — the best augmented reality device on the planet is finally available.

If reaching up to access Camera controls like the flash, HDR, and timer wasn't bad enough, it's gotten a lot more tedious on recent iPhones like the X, XS, and 11 series thanks to their tall displays. If you have a jailbroken iPhone, however, you can easily fix this issue using a free tweak.

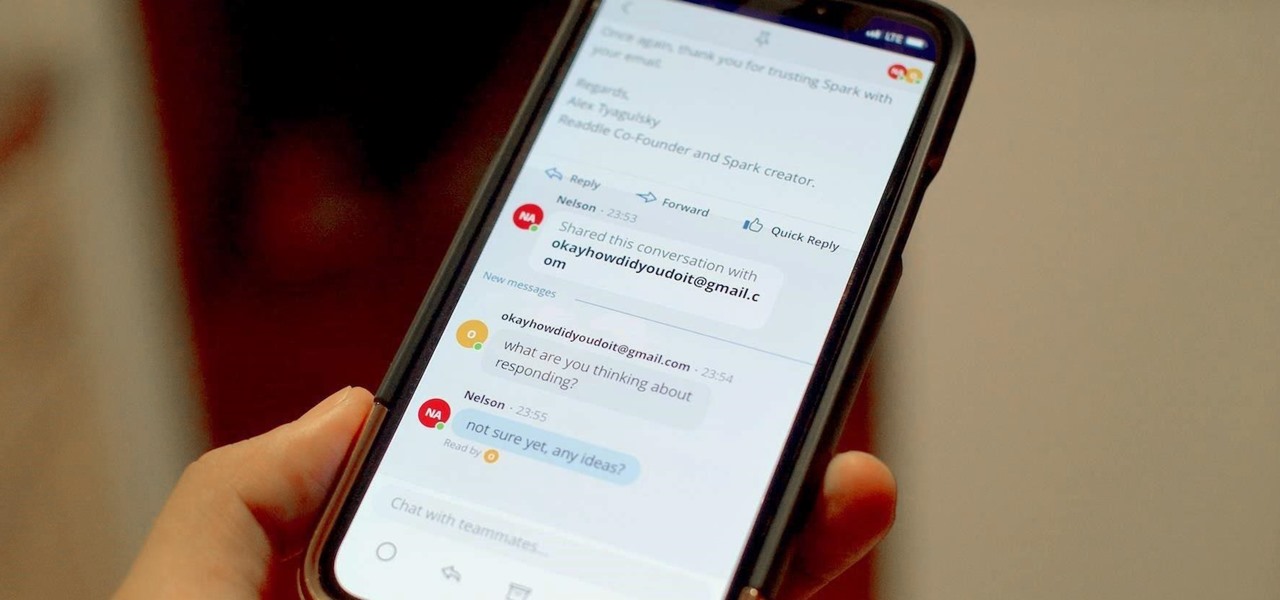
You usually reply to emails on your own ... unless it's related to your work. You may want input from coworkers or higher-ups, and while forwarding works, Spark offers an easier way to discuss important emails with others. Using Spark for Teams, you can easily share an email with your team and discuss it privately.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

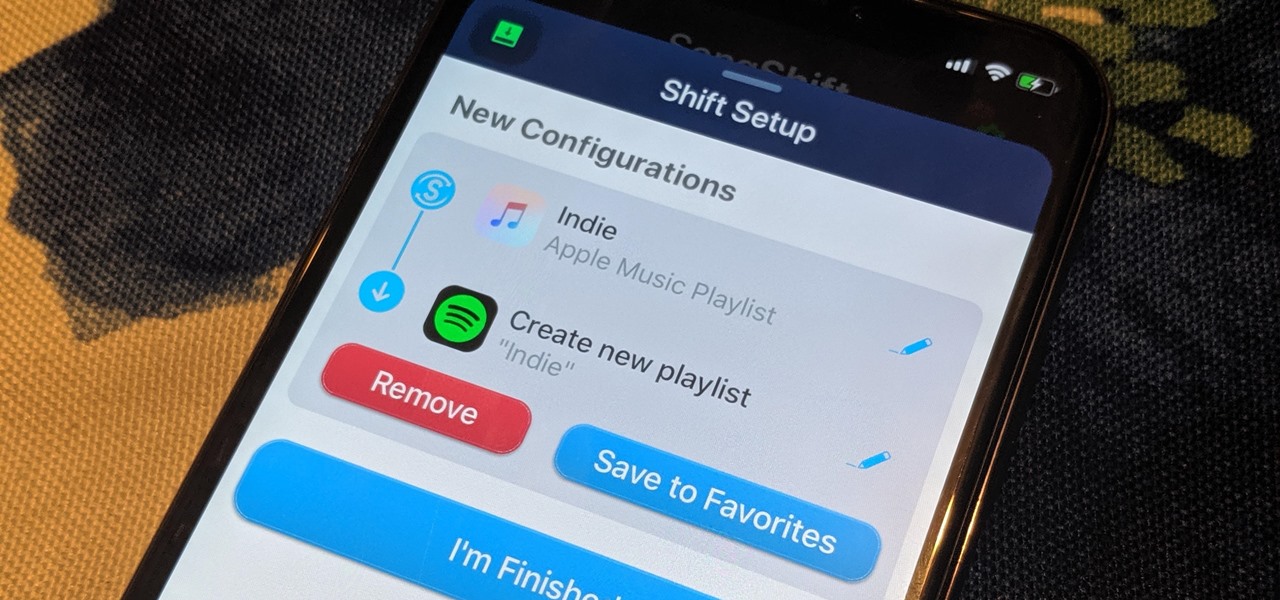
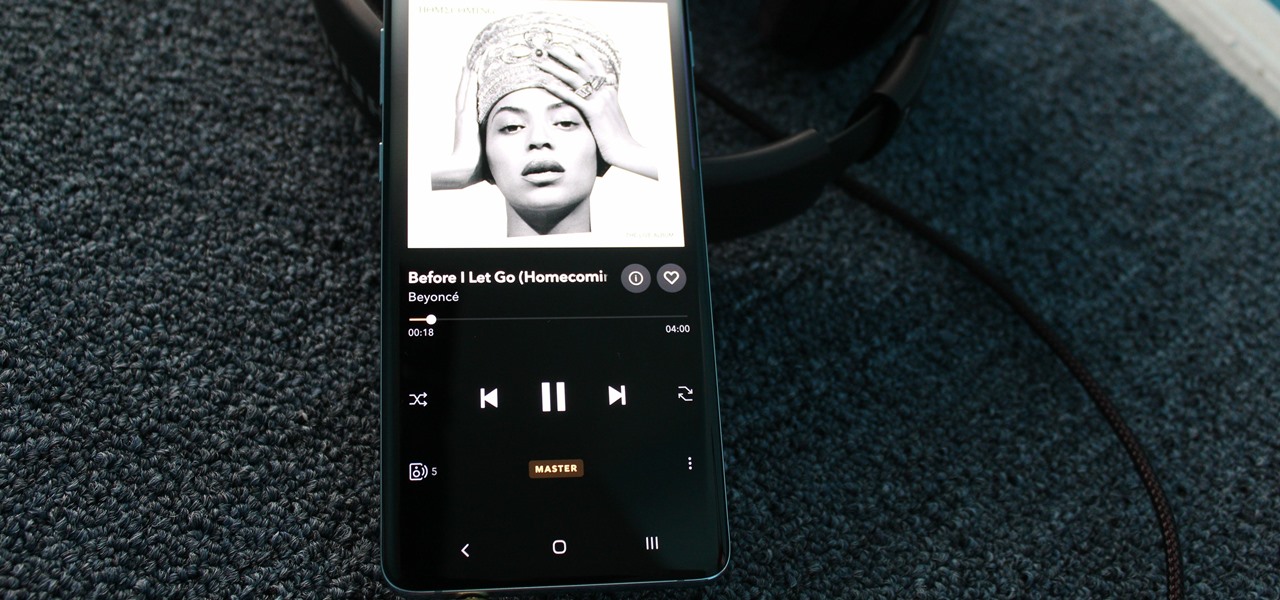
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

As you might know, Tidal differentiates itself from the competition with its audio quality. Unlike Spotify and Apple Music, it aims to give its subscribers studio quality audio from any device. However, before you sign up for Tidal, be aware there are few steps you need to take in order to stream such high-quality music.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

After announcing at Google I/O 2019 that augmented reality content would come to Search, Google revealed how it would make that happen with the latest round of updates to ARCore.

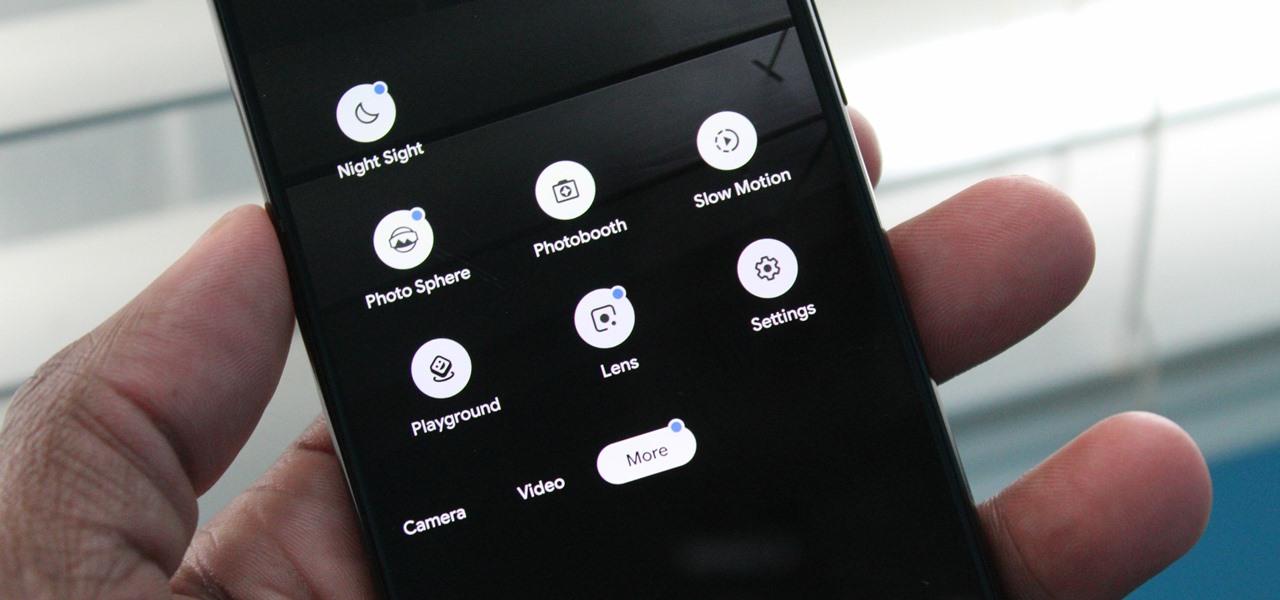
Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

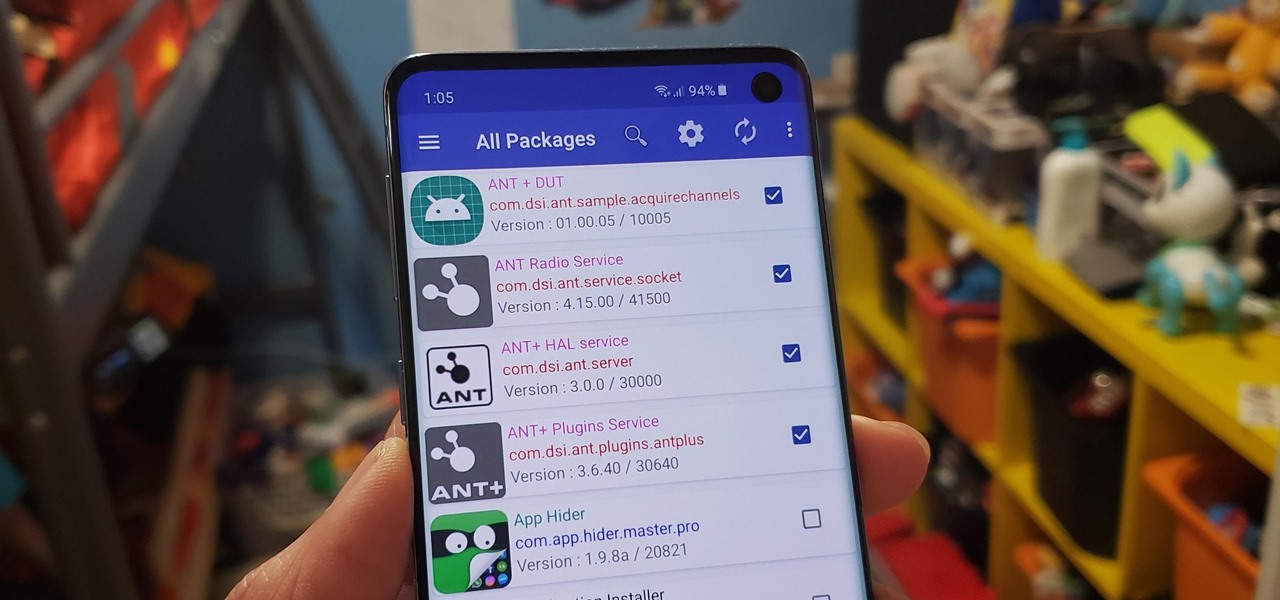
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

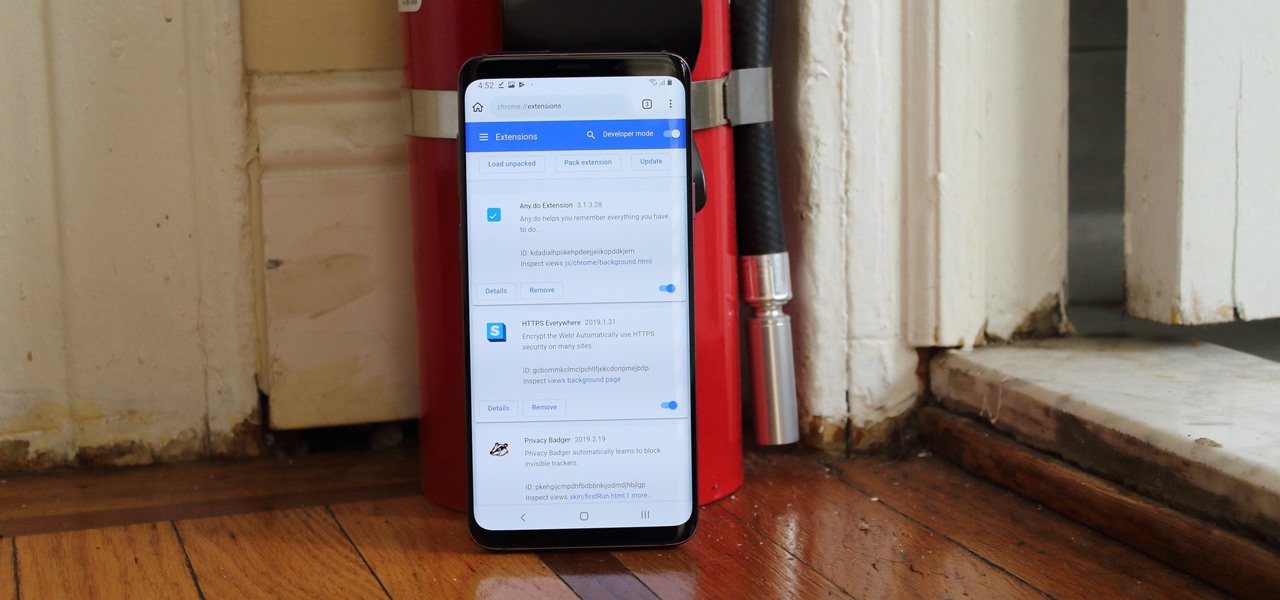
For years, there has been a disconnect between the Chrome app on your smartphone and the Chrome browser on your computer. The latter was a powerfully fast browser which could be enhanced with extensions to add new features and functionality, while the former was just a fast browser. Well, that all changes now.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.

Sileo is an ideal marketplace for developers to showcase apps, tweaks, and themes that Apple would never allow in the App Store. While a majority of these packages are free to try out, there are jailbreak apps that cost money for your iPhone. But actually paying for mods can be a bit tricky.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

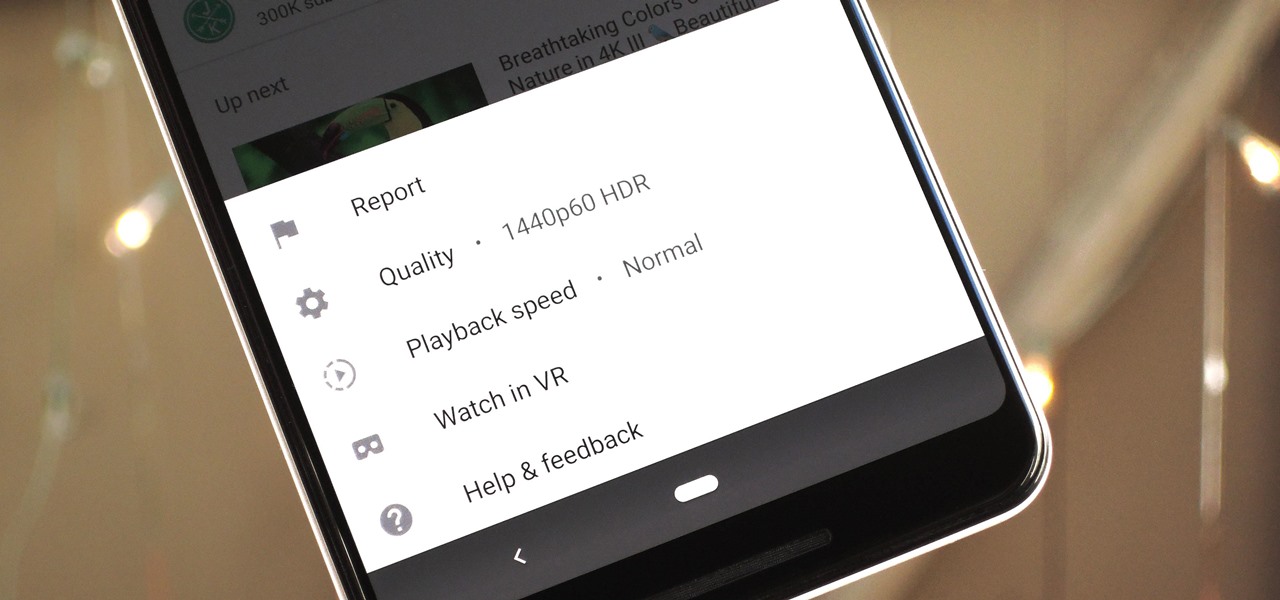
The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.