Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

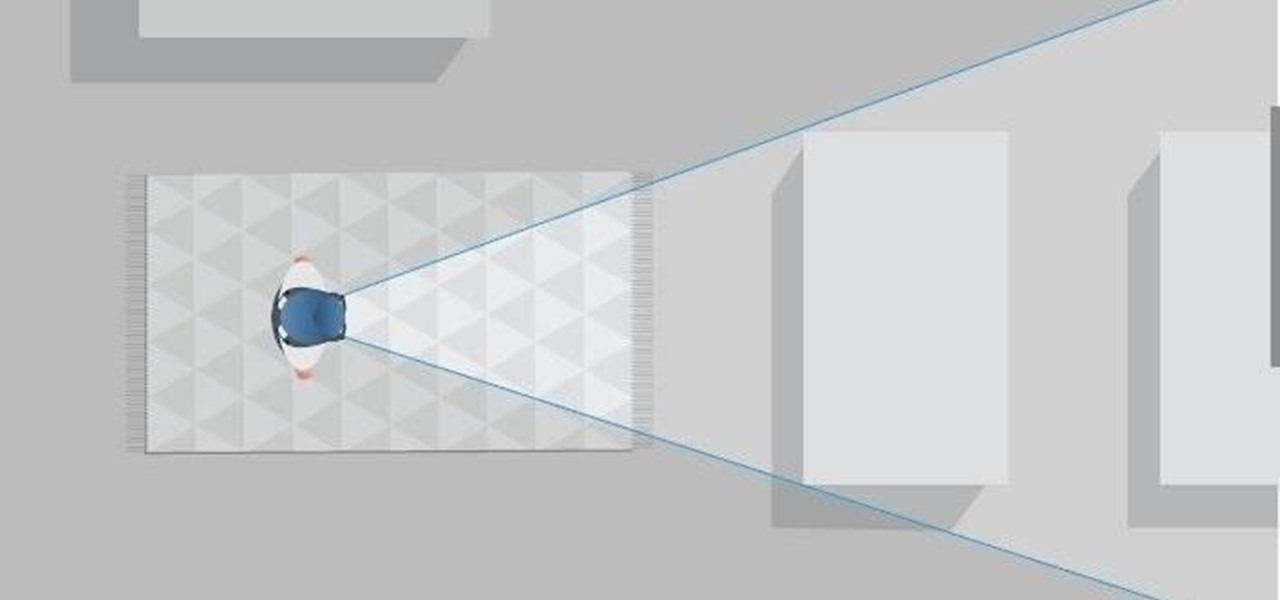
A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

While the three new iPhones won't even be announced until Sept. 12 during Apple's fall event, case makers are already primed for the launch of the devices. Some case designs are already live on manufacturer websites, and you can even buy or preorder cases for the iPhone XR, iPhone XS, and iPhone XS Plus to have right now or on launch day.

Any little bit of new light shed on Apple's rumored augmented reality plans is irresistible, and the latest comes from a fairly powerful source — a former Apple engineer who worked on the iPhone.

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

The arrival of Magic Leap One is tantalizingly close and, although the company has been saving the last details for launch day, a few of the more important details were found this week hiding deep in the code on Magic Leap's website.

The shifting sands of immersive computing, currently fluctuating between augmented reality and virtual reality, can be hard to navigate if you're only versed in one of the platforms. But a new series of videos from Leap Motion paints a picture of a near future world in which AR and VR will seamlessly merge together, forcing us to change the way we see both.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.

This week's crop of Snapchat lenses is jam packed with pop culture, and spot-on examples at that. Post Malone and Famous Dex are super hot right now, and there's a ton of buzz surrounding Arrested Development's latest season.

The next big event Apple is holding is WWDC 2018, its Worldwide Developers Conference, is about to happen. If you want to see the first glimpse of iOS 12 for yourself, as well ARKit improvements, Apple Watch news, and maybe even some macOS announcements, here's how you can tune into the event right at home from your computer or mobile device.

The premise of Jurassic World revolves around splicing genes to create new dinosaurs, so it is fitting that the location-based AR game is a clone of Pokémon GO merged with the DNA of the Jurassic Park franchise.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

The price tag for the Microsoft HoloLens might be out of range for the average consumer's budget, but for enterprises, like BAE Systems, adopting the AR headset is yielding a return on the investment. And for those with even slimmer wallets, Best Buy just made the Lenovo Mirage, part of the Star Wars: Jedi Challenges package, more affordable.

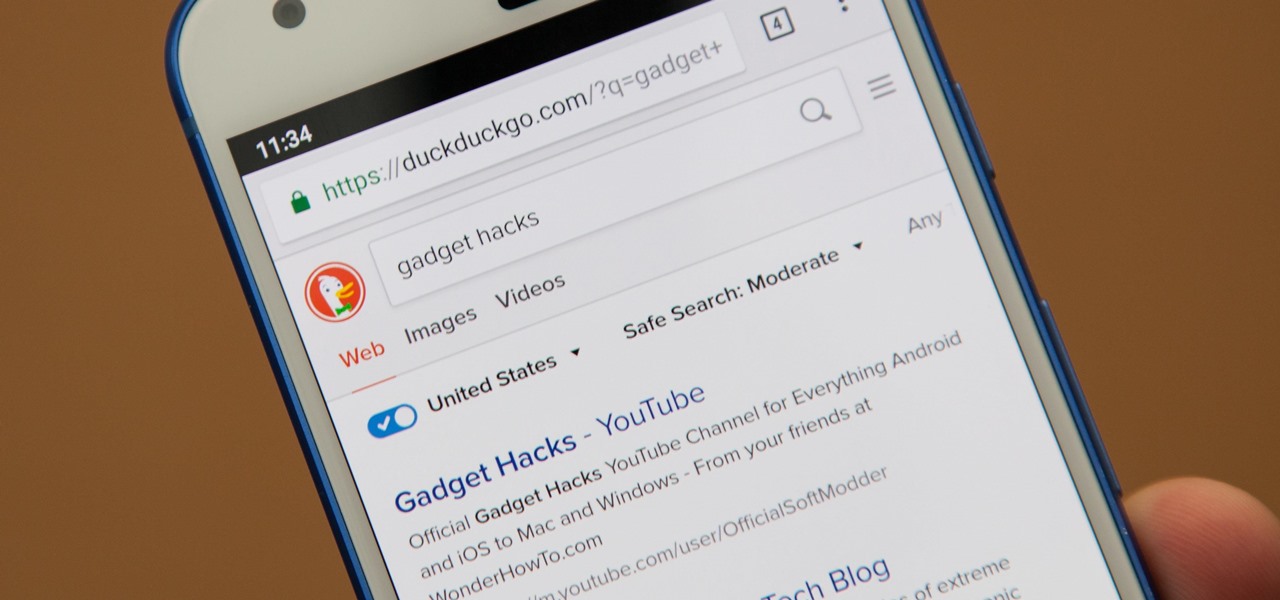
Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over everything in your life. Whatever the case, it's easy to switch from Google to another default search engine.

While you were busy browsing Instagram, composing tweets, or chasing Snapchat updates, an eight-year-old ARKit developer was hard at work on her first step toward taking over the tech world via augmented reality.

With much of the hype centered around its powerful cameras, it's easy to overlook the equally impressive audio capabilities of the Galaxy S9. After all, the S9 and S9+ are the first Samsung flagships to feature AKG-tuned stereo speakers, and that's not even mentioning all the software enhancements that help deliver rich, immersive sound in several different listening situations.

This week's Game Developers Conference came at just the right time for Magic Leap, a company that was riding a wave of bad news from legal troubles and rumors regarding Magic Leap One.

Google just released Android 9.0 Pie, but the Android community is already working its magic. Developer Quinny899 quickly ported the updated Pixel Launcher from the new build, so you can try it out on other phones right now.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

In the not so distant past, you had to actually go meet someone in person to repay money you owed them. Say they covered your half of dinner or picked up movie tickets — they wouldn't get their money back at least until the next time you saw them. Thankfully, Venmo has effectively eliminated this inconvenience.

With the Super Bowl just days away, it seems appropriate to draw parallels between football and the professional sport of technology business, or, more specifically, the augmented reality segment.

Google's Pixel lineup hangs its hat on smooth software and a polished UI. At the core of this experience is the Pixel Launcher, a home screen app that is often imitated, but never perfectly duplicated. That is, until developer AmirZ released the latest version of his Rootless Pixel Launcher port.

It's tough to keep pace with Apple lately. As expected, only one day after the public release of iOS 11.2.5, the company released iOS 11.3 to developers. A day after that, Apple pushed it out to public beta testers, too. With new Animoji, more transparent battery information, Apple Music receiving music videos, and more, this update is the one to watch out for.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The Pixel 2's camera is one of the best you'll find on an Android phone. Among its standout features is the incredible Portrait Mode, which Google accomplished with some impressive software processing. Thanks to a few clever developers, you can now enjoy the Pixel 2's Portrait Mode on your Galaxy S8 or Galaxy Note 8.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Coinbase sets itself apart from other wallet apps by making cryptocurrency transactions incredibly convenient. You can easily withdraw cash from the app and deposit it into your bank account within days — and now, if you want to cut the time from days to mere minutes, Coinbase has you covered as well.

With the big reveal of the Magic Leap One: Creator Edition in December 2017, and now the update on Feb. 13, 2018, we no longer have to speculate as to what the augmented reality headset will look like or when (in general) it will be available.

The Sony Xperia XZ Premium brought 4K HDR to a Sony flagship along with some competitive internals, while the Xz1 brought some powerful specs in a more midrange, traditional form factor. While it only makes sense to be excited about what's coming next, Sony has yet to show us the XZ2. For now, we need to stick to the rumor mill. Thankfully, the rumor mill is a fun place to be.