The Android App Market is flooded with tons of new mobile applications each day. But there can't be that many developers out there familiar with the Android OS, so where are all of these apps coming from?

Inception may not be the lead contender for the 68th Golden Globe Awards, honoring the best movies and television from 2010, but Christopher Nolan's film still collected four nominations— Best Motion Picture, Best Director, Best Screenplay and Best Original Score.

The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them.

How to use the text tool in GIMP (GNU Image Manipulation Program) the free, open source image editor, to add text to your images. Use the text tool in GIMP.

How to work with layers in GIMP (GNU Image Manipulation Program) the free, open source image editor. Layers in GIMP function in exactly the same way as Photoshop. Work with layers in GIMP.

Fullscreen isn't always fullscreen, especially on your smartphone. As screens get taller and bezels get slimmer, more phones end up with an aspect ratio that doesn't match most YouTube videos. Luckily the video-sharing app has a nifty workaround to fill your screen.
Recently, I decided to install Kali 2016 as dual boot on my laptop. Everything install perfectly up until the installer gave me the option to set up the package distribution mirror. No matter what setting I provided, no mirror would set up correctly. I was forced to continue the install without setting up the mirror. If you do not know what this means, I will explain it. Basically, you will not be able to update or install any tools onto your Kali distribution.

Windows users have looked on with envy at Mac owners wrangling torrents with ease for years. Now, finally, a new Windows torrent client is making downloads easier, safer, and more customizable.
Hey its August. I dont know why I post so often but I wanted to add up on a post by Cameron Glass here What we are going to do today is turn that backdoor into a .app file so that we dont even need to touch the victims computer! also thanks to someone who helped me with this. (You know who you are)
In this tutorial we will be go over how we can make use of conditionals. In Perl the main conditional is the if statement. The if statement in
Back in Backtrack5 there was a nice GUI addon for the aircrack suite called feedingbottle. I liked it because it simplified easy tasks like fake auth with a click of a button. I was hunting for sources and it seems that all I could find was an ubuntu deb package from 2013. It was a little tricky installing it on a 64-bit system so I thought I would write a quick how to. Feedingbottle is an x86 package so you must install the corresponding libraries. If they are missing you will get a "bash:.....

Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me.

Amazon's Appstore has come a long way since it launched in 2011, with over 250,000 apps to its name. That being said, their app numbers pale in comparison to Google's Play Store, which currently boosts over 1.3 million apps.

Google is set to release an update to their Hangouts messaging service starting this week. The update to version 2.1.075 brings new features, with the biggest ones being merged chat and SMS messages and a home screen widget. Here's a complete breakdown of the new features you can expect.

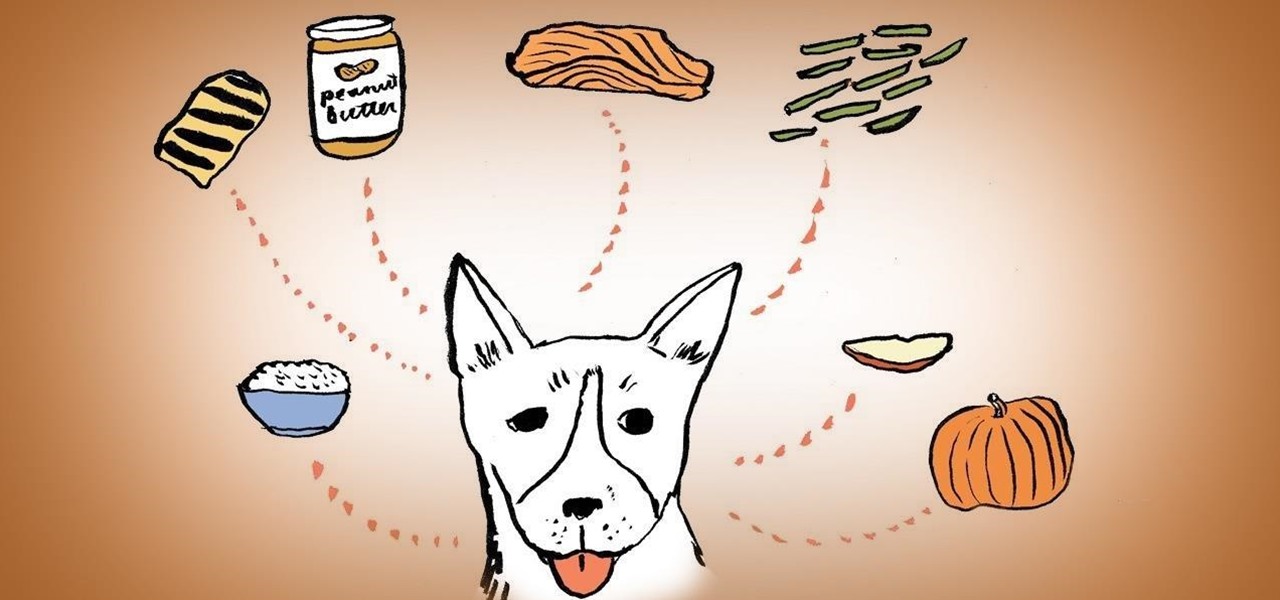
Want to boost your dog's immune system and skin health? Add some extra flavor to your dog's food bowl with a few pieces of cooked salmon, deboned and unseasoned, which is an excellent source of fatty omega-3 acids.

Stock prices be damned, HTC is ready to right the ship with it's soon-to-be-released follow up to the HTC One. The financially challenged device maker, according to inside sources, plans a March release for it's newest flagship.

Imagine if Apple sold customized, jailbroken iPhones at their retail stores. Do you know how freaking awesome that would be? Knowing Apple and their extremely tight-assed regime, it's more likely that Tony Romo will actually win a Super Bowl (Cowboys burn).

Adblock Plus is a well known add-on for Google Chrome and Firefox that eliminates all of those annoying and obtrusive advertisements on the webpages that you visit.

There's nothing wrong with driving an older car, but one problem that a lot of people run into is that as mobile devices get more advanced, it gets harder and harder to use them in vehicles made more than a few years ago. There are several ways around this, like installing a dash-mounted iPod Nano or putting a smartphone dock in your ashtray.

A common misconception is that all car batteries die. This, in fact, isn't true—the majority of "dead" car batteries just don't contain enough juice to power a car, but they can still provide enough watts to keep emergency fans and lighting running, which is great when a power outage occurs. So, instead of lugging the battery to the nearest drop-off center or just letting it collect dust in the garage, you can put that car battery to good use.

Whether you're job searching, networking, or just giving your information out to someone you just met at a bar, this circuit board business card made by Brian Carrigan will make sure no one ever forgets meeting you! Sure, you could buy a customized USB business card on some online shop, but if you're trying to emphasize your geek cred, why wouldn't you make your own PCB card from scratch? Carrigan used a USB controller and added an Atmel AT45DB series flash chip so that it could store his res...

If you've been following the Olympics at all, you've probably heard (or experienced firsthand) that people are not very happy with NBC's coverage. The online streams are inaccessible for those without a cable subscription, and the TV broadcasts of big events are being tape-delayed for prime time.

Who uses Yahoo! Image Search, you ask? Scientists apparently.

WARNING VM uses the hard disk as ram. So it repeatedly writes and reads of the hard disk. Since the iPod has flash memory usage of this tweak will lower your device lifespan to 5-7 years. So i recommend this tweak on a old device you want to speed UP!!!
Water Purification Device Prompts TSA to Close Down Minneapolis Airport In another stupendous incident of comical over-reaction, the TSA ordered the evacuation of two airport terminals in Minneapolis after a water purification device was found in a woman’s luggage.

Levers are the only toggleable way to provide a steady source of power to your redstone circuits, but they're ugly and they stick out like a sore thumb. Just look at this:
In case you haven't figured out already, our government is always on the move to figure out new ways to extend their control. The CISPA, for one, is one of the best examples, along with "re-education" programs, and racial divide (Trayvon). What I've noticed in the past few months is that their new "ideas" are coming out at an increasingly alarming rate.

There's no denying the coolness of an iPhone. But what if you pulled a homemade wooden cell phone out of your pocket instead? You'd probably be the talk of the town. If you like that idea, then make it a reality by building your own cell phone!

Your favorite device is running low on juice and needs a couple new AA batteries—and with a quickness. You run to the store and grab the first pack of AAs you see. But should you? There's tons of options available, so which make and model gives you the most power per dollar?

The exploding ashtray prank was once fairly commonplace long before the Internet was born. Using flash cotton to create a startling explosion, this prank is certainly effective at getting a reaction. Flash cotton is a staple of many magic acts; used for its ability to create a brilliant flash of fire without causing a burn to the skin.

Besides Wikipedia and teachers (in that order), textbooks are the go-to source of information during our school years. Today, we take a look at what happens when the people writing these voluminous tomes get attacked by a sudden bout of ennui.

So far, there have been some excellent entries to our WTFoto Stock Photo Challenge, but the battle is not over yet. You still have a couple days left to submit your best find to the WTFoto community corkboard for a chance to take the crown. Remember, we're looking for an absurd stock photo image that nobody's ever seen before. Entries are due Monday, February 27th, 11:59:59pm PST. One second later and, well... I'll probably just let it slide. But 2 seconds later and you're out!

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

In this article, I'll be showing you how to make a cool visual representation of sound using an old cathode ray tube (CRT) television, a stereo, and a sound source. You'll also need a pair of wire cutters, and a few screwdrivers. To properly understand this project, it's a good idea to learn a little bit about how CRT TVs work. Check out this article on how they work.

I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.

There’s a race on to see who'll be the Instagram of moving pictures. This makes sense, since many of our phones are clogged with video that, so far, no one is going to see. Wouldn’t it be great if there were a simple app that could take our video content, edit it for us, and then publish it to all of our networks?

The purpose of this article is to discuss how you can change your Windows 7 logon screen. This post will explain how to require a user to enter a username and password by default like the classic version of Windows.

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

Many users of the virtualization software VirtualBox may have noticed that the USB system has been pretty buggy for quite a long time. I've had my USB randomly duck out on me way too many times to count. This can really be difficult to deal with when you require access to the devices and files from the host system.