This is how to do the Manu Ginobili step back jumper! NBA hot shot show's us how to pull the step back jumpshot, one of his Signature Moves on Nike's series. First the long step and catch your balance. Then setup for the rim. Go behind the back and then see what you have in front of you.

In this video tutorial, Wess does some research and builds a steady-cam for under fourteen bucks. Hooray for no more motion sickness!

Work out and getting in shape with dips. Learn how dip exercises can increase your strength and fitness in this training video. Take action: do not lock elbows, upper arms stay parallel to floor, and no partial reps, use full range of motion! Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she en...

Work out your arms with dumbbell concentration curls. Learn how to exercises with curls in this fitness video. Take action: stay tight without rocking, get full range of motion, squeeze at the top of the movement, and plant your elbow. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys tr...

Have you tried working out with reverse curls? If so you know that they are an essential part of lifting weights and strength training. This fitness how-to video demonstrates work out the bicep muscle with reverse curls. Learn about curls and weightlifting exercises in this workout video.

Learn to make your own super effective bass traps and acoustic panels with materials from your local hardware store, just by watching this home audio video tutorial.

Learn how to do cable rope power overhead skull crushers. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do prisoner squats. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do floor leg raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do triceps bench dips with your feet on the floor and sculpt your body without weights. Presented by Real Jock Gay Fitness Health & Life.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

As you already know, the Galaxy Note 10 and 10+ have gotten rid of the beloved audio jack (RIP). Fortunately, it has never been a better time to switch to wireless. There are Bluetooth headphones and earbuds for every budget and every need.

While some widely praised immersive computing initiatives at Google are shutting down, over at Epic Games things are just ramping up, and it involves quite a bit of cash available to indie augmented reality developers and startups alike.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Hollywood has already proven that it's on board with augmented reality, with examples ranging from Avengers: Infinity War to Ralph Breaks the Internet. But one startup wants to make the augmented reality content that's being used to promote TV and film entertainment smarter.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

There's always been a clear divide between flagship and midrange phones. Flagships will run you at least $700, while midrange typically falls between $250 and $550. The main difference is the processor, with midrange phones sporting a 600-series Snapdragon and flagships rocking the 800-series. Now, Qualcomm may have just created another smartphone tier with their newly-unveiled 700-series chip.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

Many Samsung fans were excited when the Galaxy S9 kept the 3.5 mm headphone jack. While this is a rare delight in 2018, you also have the option for high quality audio playback over Bluetooth. When used with compatible headphones, the S9's new Bluetooth audio codecs can greatly improve audio quality.

Huawei has been on a roll recently. They just became the second largest smartphone manufacturer in September, passing Apple and trailing only Samsung. Shortly after, they announced their new Kirin 970 flagship SoC to rival the Snapdragon 835, then followed that up by announcing the Mate 10 and 10 Pro. Well apparently, Huawei isn't done with announcements just yet.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

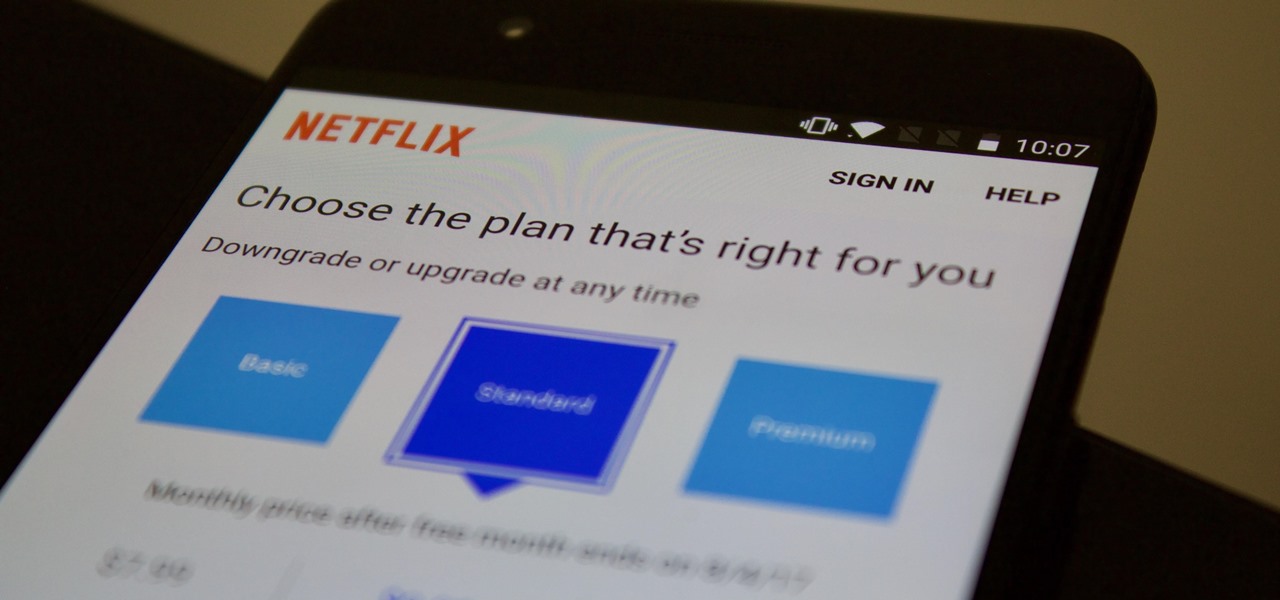
Netflix offers three different tiers of service. The good news is that no matter which subscription plan you choose, the available content is the same. Whether you choose the cheapest plan or the most expensive, you'll be able to watch any TV show or movie in Netflix's library. But there are other things to consider when choosing the plan that's right for you and your smartphone.

Augmented reality could come in very handy for those of us prone to losing things—namely, our wallets. Pixie Technology, a company from Los Altos, California, has developed a way to locate your lost wallet and keys using AR technology and tracking chips, a platform they call the "Location of Things."

The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and '90s.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Food labeling is a tricky beast. For instance, when I read the words "cage-free" on an egg carton, I think it means that happy chickens frolic in a sunlit meadow all the livelong day until they're gently herded into a clean, sweet-smelling coop to lay a few dozen eggs—which I can purchase for a reasonable price, of course.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

If you've recently joined the ever-growing ranks of the cable cutters, you're far from alone. More and more people (myself included) are getting fed up with service providers' outdated subscription models and absurd pricing—and canceling their service.

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

This video tutorial is in the Business & Money category which will show you how to negotiate a salary right out of school. Of all the questions you can get asked in an interview, probably the toughest one to answer is "what are your salary expectations?" if you quote too low, you might leave some money on the table. And if you go too high, you may price yourself out of the job. So, what does a college student do? If they asked you the question in an interview, be clear that it's a negotiation...

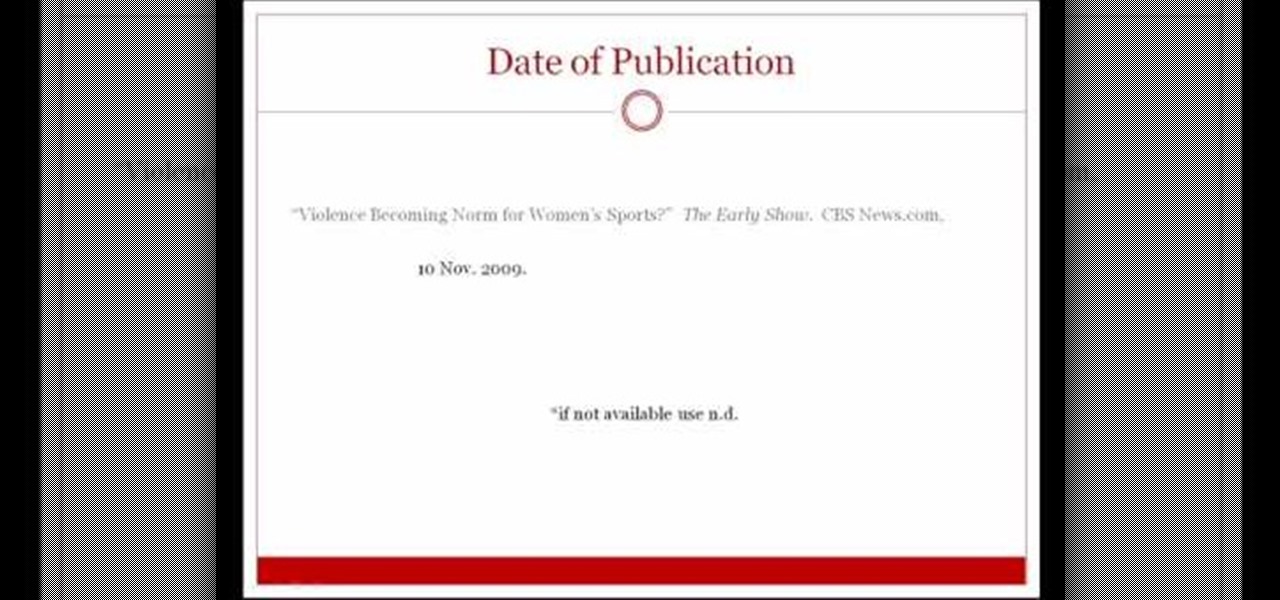
If you're writing a college essay or report, your bibliography is a painful, yet necessary part. And thanks to all of the information available on the World Wide Web, most colleges and universities accept websites as resources in your bibliography. But citing websites can be confusing when using the MLA citation format. This video will breakdown the process.

In this tutorial, Chef Jason Hill teaches us how to cook tilapia. Tilapia recipes can range depending on what kind of food you want. Tilapia is a fresh water fish with firm white and flaky appearance. To begin, toast 1 c of cornmeal for 2-3 minutes over medium heat. After this, put the mixture into a casserole dish and then make your pepper topping. Set your pan on medium-high and place 2 tbsp olive oil along with bell peppers, pasilla, and red peppers that are chopped. Then, stir in 1/2 c wa...

Ezreal is a champion you can bring onto the Fields of Justice. This video demonstrates what Ezreal, a strong ranged fighter, can do and the best ways to use him in combat. Here are a few good strategy tips when it comes to scaling his abilities, and a few ideas on how to fight certain opponents.