The battery on your iPhone can go from 10% to completely dead in a matter of minutes, or at least it can feel that way. Apple does prepare you with an alert when you hit the 20% and 10% mark, but it's easy to forget to charge your iPhone before it dies even with those notifications. That's why you should also be notified when your battery's down to 5% remaining.

Google released the first build of Android 12 almost exactly one year after dropping Android 11, which is remarkable in the midst of a global pandemic. But you can tell the Android engineers have been hard at work while quarantining, because the latest OS version is absolutely packed with new features.

TikTok has grown to be one of the most popular social media platforms in the world. The video-sharing app is a driving force for viral content, spurring various popular movements in dance, pranks, comedy, and more. And as one might assume, videos on TikTok don't stay on TikTok — they're shared on Instagram, Twitter, and other services where millions of people get the chance to also view them.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

Apple released the first public beta for iOS 14.5 on Thursday, Feb. 4. This update is proving to be the most significant in some time, offering new features and changes like support for PS5 DualSense and Xbox Series X controllers, the ability to unlock your iPhone using your Apple Watch, AirPlay 2 support for Fitness+, Reminders sorting and printing options, 5G support when using dual-SIM, and more.

Apple released iOS 14.5 developer beta 1, and the update sports a list of interesting features and changes. Some of those include support for the Xbox Series X and PS5 DualSense controllers, the ability to unlock your iPhone with Apple Watch, AirPlay 2 support for Fitness+, 5G support for dual-SIM setups, and a refreshed Software Update page in Settings.

If you'd rather be gently relaxed out of bed instead of stressed out at loud alarm sounds, there are a few things you can do on your iPhone. One of your best options is to use carefully selected songs that start out calm and soothing and gradually increase in intensity and volume. But you could also use a more intense track you know will wake you up, only set to ascend in volume to ease you out of slumber.

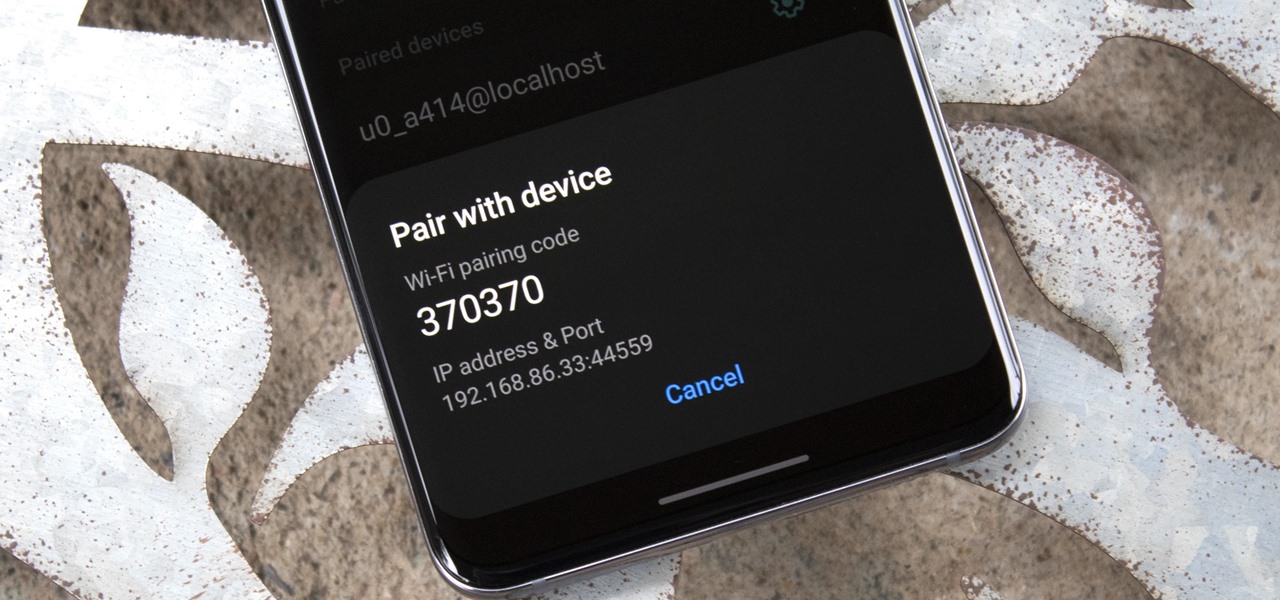
Samsung's One UI 3.0 skin is built on top of Google's Android 11 open source code base, which means you get all of the standard features, plus some cool bonus stuff from Samsung. However, it's one of those standard AOSP features that you might find most useful if you send a lot of ADB commands.

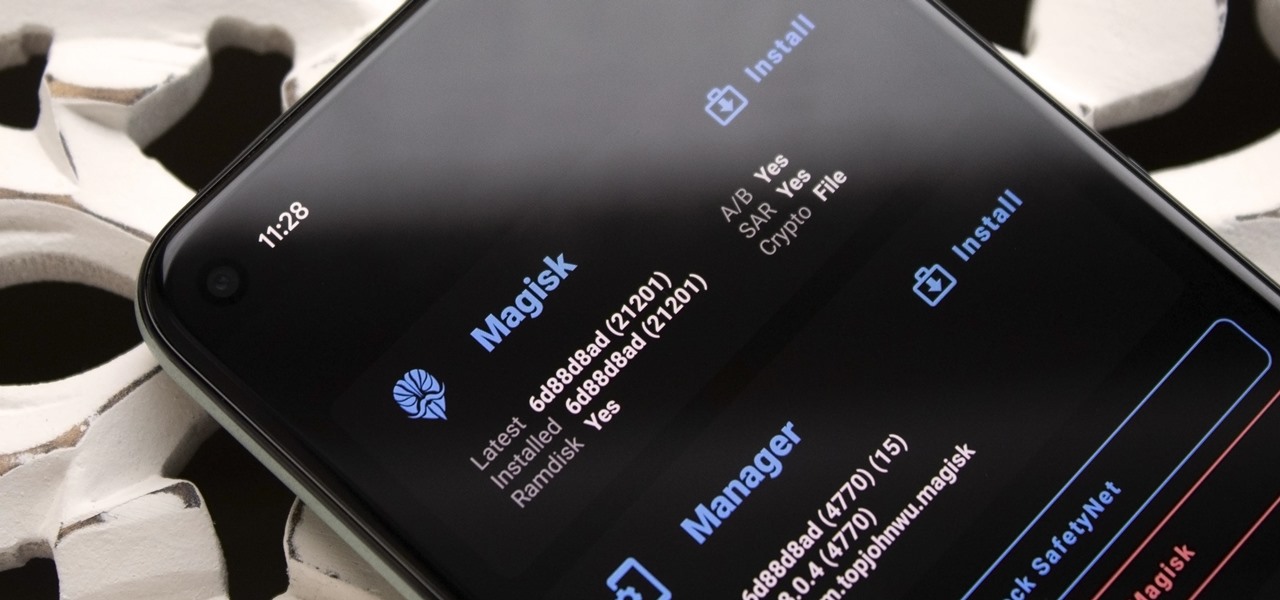
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

The iPhone has a setting that will obfuscate the content of notifications on its lock screen until you're recognized by Face ID. Google implemented this same feature in its Pixel phones, but many Android devices have no such option. At least, not by default.

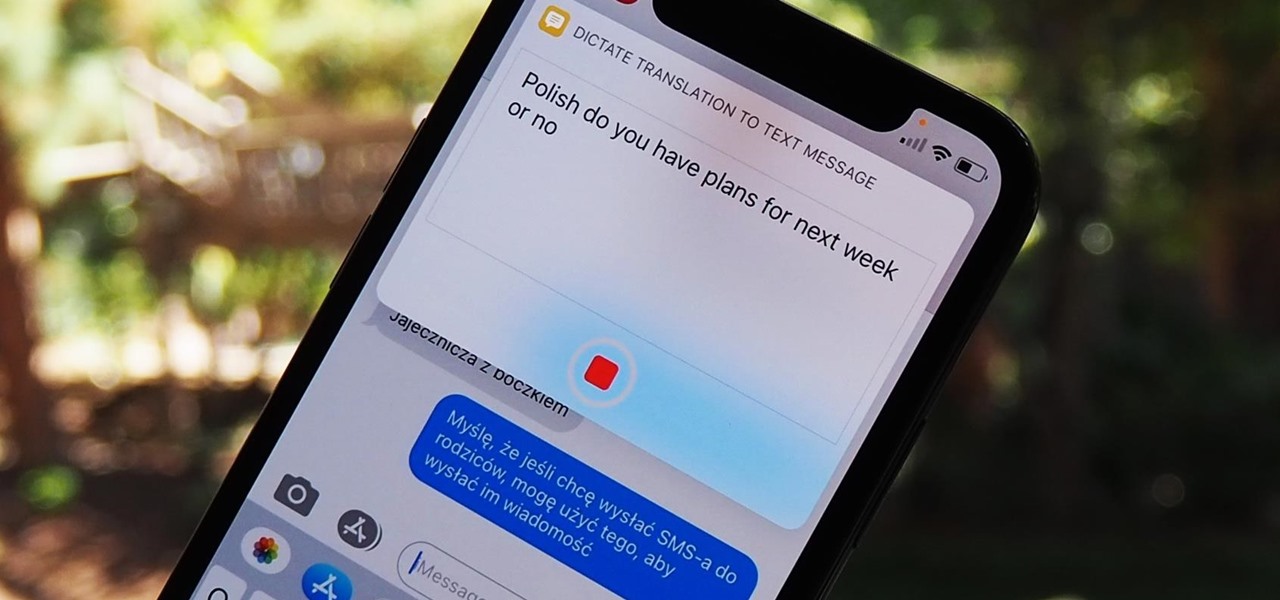
When iOS 14 came out, Apple released Translate, an app for translating voice and text between several languages (even within Safari). Unfortunately, it's not as comprehensive as some third-party apps or even Siri. That's why Apple uses Microsoft's translation services within Shortcuts. It may sound surprising, but we're not complaining since you can do some pretty awesome things with it.

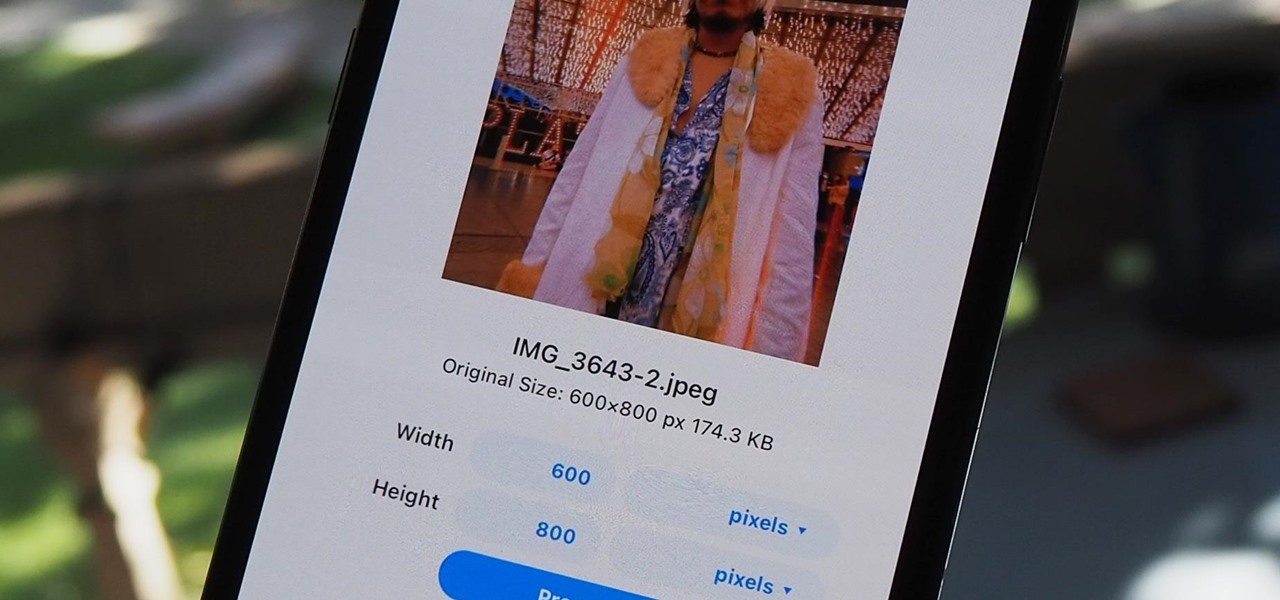
The rear cameras on iPhones have remained at 12 megapixels since the iPhone 6s, but with each new iPhone model, more data is going into photos. That means larger file sizes. If you're running into issues with your pictures being too large, whether you're sharing or uploading them, there's an easy way to resize an image or group of images using a shortcut.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.

Google doesn't get enough credit for it, but they definitely make some of the best phones for rooting and modding. Heck, if you want to replace the entire operating system on a Pixel, you can do it pretty easily. It all starts with the bootloader.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Aside from home screen widgets, one of the most exciting updates to the iPhone with iOS 14 is Picture in Picture mode. With it, you can watch minimized versions of videos on top of other apps so you can multitask like a pro. However, not every service is on board with Apple's new features. YouTube is the primary culprit, but there is a workaround.

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

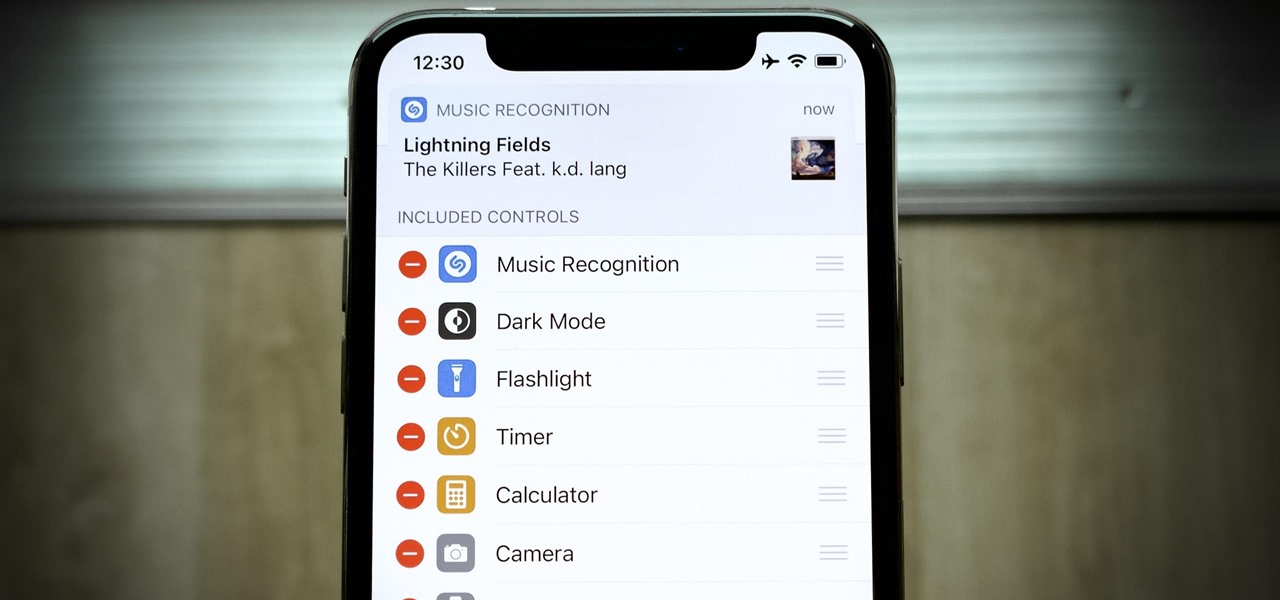
Apple just released the first beta for iOS 14.2 to iPhone software testers today, Monday, Sept. 21. This update brings a new Control Center tile for Shazam music recognition, a redesigned Now Playing Control Center tile, and a new "People Detection" feature in Magnifier.

Apple just released the eighth public beta for iOS 14 today, Wednesday, Sept. 9. At this time, beta 8 (18A5373a) seems to be a minor update to iOS 14, introducing bug fixes to improve the software's overall stability.

Apple just released the eighth developer beta for iOS 14 today, Wednesday, Sept. 9. Beta 8 (18A5373a) appears to be a minor update offering bug fixes to improve overall stability.

Millions of people use YouTube every day, whether it's for trailers, new music, or gameplay walkthroughs. But according to Pew Research Center, over half of U.S. adults use YouTube to figure out how to do things. If you fall into that crowd, adult or not, sometimes it's good to have written instructions to follow along with the video or in lieu of it completely.

While Google Play Music fans mourn its demise, its replacement, YouTube Music, is gaining some neat features that its predecessor never had.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.

Apple just released public beta 2 for iOS 14 today, Thursday, July 9. The good news comes two days after Apple released the second iOS 14 developer beta, and 17 days after the release of the first developer beta. While this is the first public beta for iOS 14, it's called "public beta 2" to keep in line with developer beta numbering.

Apple just released the second developer beta for iOS 14 today, Tuesday, July 7. The update comes 15 days after Apple seeded developers the first iOS 14 beta, which introduced home screen widgets, picture-in-picture, and 4K YouTube support, among more than 200 other features.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

One of the coolest aesthetic features of iMessage is its animated message effects. If you're like many users, you might even have discovered them by accident, where wishing your friend a "Happy Birthday!" or congratulating them on a promotion unexpectedly flooded your screen with balloons or confetti.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.