
How To: Lower off the top while climbing
A great percentage of sport climbing accidents happen after the climber reachs the anchor. Next to belayer miscommunication not having a system is the next killer.


A great percentage of sport climbing accidents happen after the climber reachs the anchor. Next to belayer miscommunication not having a system is the next killer.
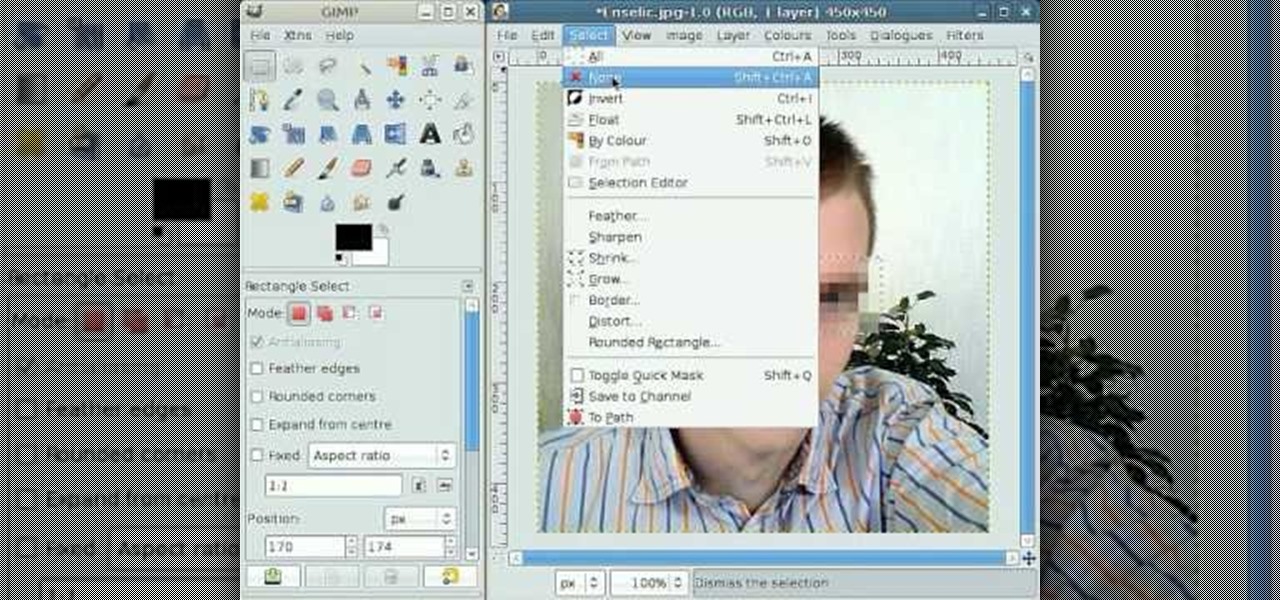
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.
Hey everyone. Only found the site a few days ago but really loving it. Been

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Learn one of the world's most popular games. It's actually good exercise, too! Step 1: Decide who goes first

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.
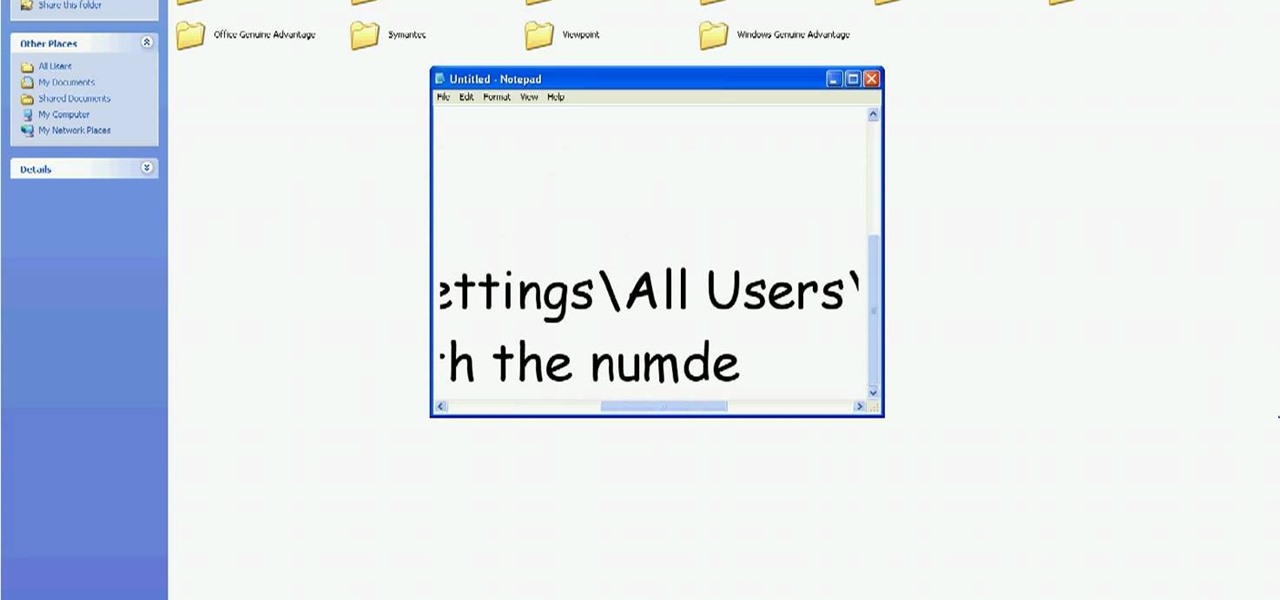
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

Have you noticed some issues with your Apple iPod Touch, like performance issues (speed) or errors (frozen screens)? The first thing you always want to try to resolve these types of issues (especially freezing) is a simple little reset feature on the iPod Touch, available by pressing and holding the Home and Sleep/Wake buttons. If you this doesn't work, you can try restoring the software via iTunes. If that doesn't fix the frozen iPod, then you'll need to contact Apple or a repair technician.
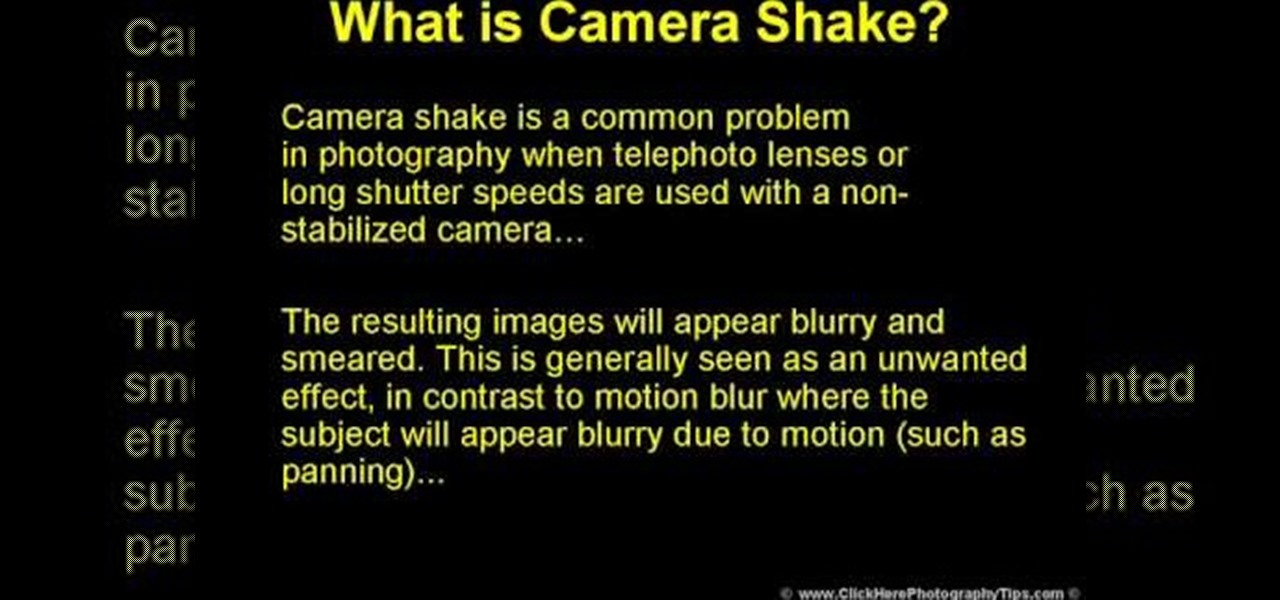
Camera shake is often an unwanted effect in photography, when a telephoto lens or long shutter speed has been used for a camera that hasn't been stabilized. The images subject to camera shake appear blurry and smeared, which is often considered an error - though some photographers find artistic value in camera shake and purposefully try to cause the effect in their art.

JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. Again, far left Pepsi, near left Pepsi, near right Mountain Dew and far right Mountain Dew. This hack will allow you to see the stats, set the price and see error logs.
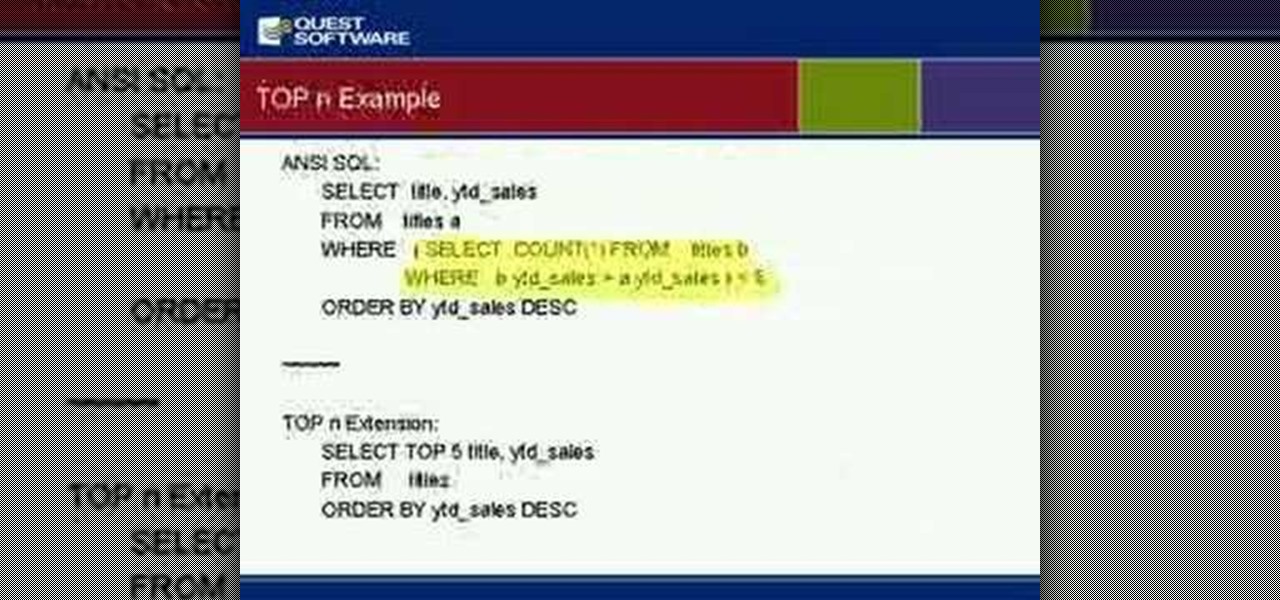
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.
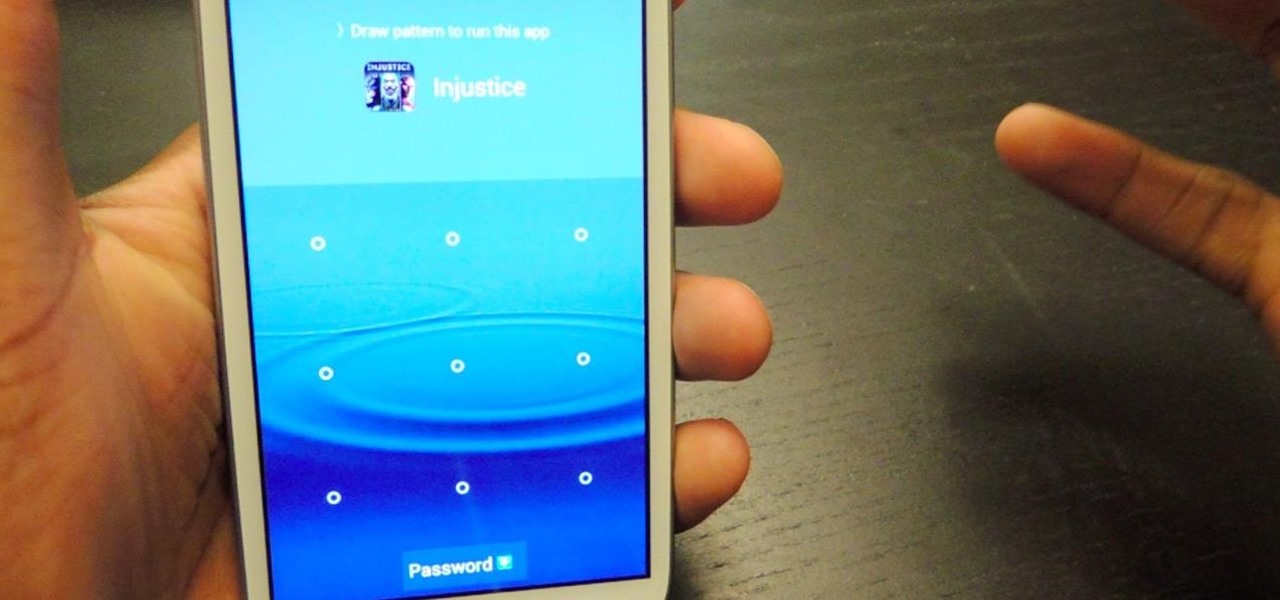
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.
This how to will show you how to program a fairly simple Hacking bat file. First open notepad.

Apple's iTunes Match service is a great feature for people who have large libraries or want to sync their music across a lot of different devices. It lets you store any song in your library that exists in the iTunes Store on the cloud, even songs you imported from CDs, and even improves the quality of some of them. But, like any new service, it's not without its problems, and the fact that it costs $25 a year makes those problems seem even worse. Among the issues that users reported, unmatche...

As with any new releases, full updates that completely revamp the look and feel of your iPhone's operating system will have teething problems that eventually get ironed out with incremental updates. iOS 11, with its issue of not being able to connect to the App Store on some iPhones and iPads, is no exception.

GE Aviation and their software partner Upskill are seeing success by giving their mechanics smart tools and smart glasses, the latter in the form of Google Glass.

Augmented reality developer Blippar has created a new visual positioning service based on computer vision that is two times more accurate than GPS in urban locales.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

The Chromecast may be slowly weaving its way into the smartphone ecosystem, but the amount of supported Android apps that are available for the streaming media player are still severely limited.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

We've all seen the blue screen of death at least one time in our lives. I grew up using a Windows PC about the size of a small refrigerator and that damn screen popped up at least once a day. Thankfully, errors like these happen much less often, but now that our smartphones have basically become pocket PCs, these type of errors can and do happen.

Chlorine gas is a very useful oxidant, which was first introduced as a toxic weapon by the German Army. Even today, it's still used as a weapon, most recently in the Iraq War by insurgents. But chlorine gas has more useful (and less lethal) applications, and if you want to learn how to make some at home, NurdRage has the answers.

This video explains how the amount of shoulder rotation you get during a windshield wiper forehand can differ from a classic forehand. After you hit the tennis ball, you typically have to rotate a little bit more than you otherwise would on the windshield wiper. There are a number of reasons for this, but in this video we keep our focus relatively narrow.

Every time you hit a tennis forehand you choose how you position your feet -- what stance you will use. You can hit a forehand with an open, neutral, or closed stance, but you should stay away from the closed stance if possible. This last stance makes it difficult to rotate your upper body through contact, making it difficult for you to use correct forehand mechanics.

Watch this how to video to figure out how to solve the 4x4 Rubik's Cube Revenge. So, get out your Rubik's or Eastsheen Cube and watch this tutorial.