There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

The holiday season is upon us, and that means all the big-box stores are competing against each other to offer the best prices on electronics. What was once a 24-hour period of flash deals the day after Thanksgiving has now become a holiday in and of itself — Black Friday is an event you don't want to miss.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

Creating doodles on an iPhone is made easy thanks to the "Draw" tool in Notes and "Digital Touch" for iMessages, but these are limited in scope. Drawing in Notes has no animated effects, and while Digital Touch does, its drawing tools are lacking and the animations can only live within iMessages. If it's animations you want, Apple has another app that can help you create them.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

For some Android users, this guide is sacrilege — but for others, iOS is just an attractive operating system that can be admired without feeling like you've betrayed your own phone. If you're one of those Galaxy Note 9 owners that have peeked across the aisle and desired an interface as clean as the one on the iPhone XS Max, you can configure your Note 9 to look like its rival with some tinkering.

Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to both Face ID and Touch ID-enabled iPhones. Not only do we know about the bug itself, we know exactly how to exploit it.

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

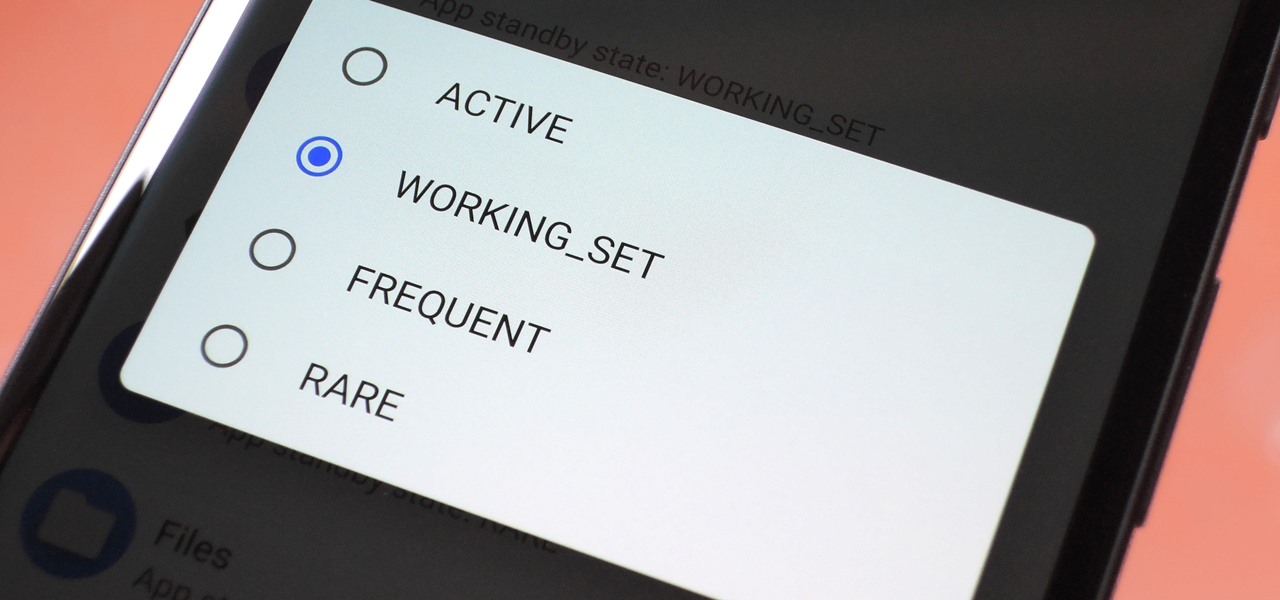
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

Apple's iOS 12 has finally landed. The big update appeared for everyone on Monday, Sept. 17, and hiding within are some pretty amazing augmented reality upgrades for iPhones, iPads, and iPod touches. We've been playing with them ever since the iOS 12 beta launched in June, and here are the things we learned that you'll want to know about.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

The world finally received its first official look at the iPhone XR, XS, and XS Max, Apple's 2018 suite of smartphones, on Wednesday, Sept. 12. If you're someone looking to get their hands on one, two, or three of these new iPhones as soon as possible, you'll need to know all of the important dates so you don't end up missing out to others ahead of the line.

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.