
How To: Do the russian stops
Check out this demonstrational video and learn how to perform a depth jump static landing with a bunny jump to a hurdle rebound. This combination is very demanding and all the elements need to be learned properly first.


Check out this demonstrational video and learn how to perform a depth jump static landing with a bunny jump to a hurdle rebound. This combination is very demanding and all the elements need to be learned properly first.

Sasuke is one of Naruto's most popular characters in the series for both the manga and the anime cartoon. Sasuke was always demanding his parents attention, for which they gave it too his older brother Itachi. All the training and stress his endured for his parents was all washed away when his brother came home and slaughtered the whole Uchiha clan, including his parents. If you want to learn how to draw this dismal Sasuke anime/manga character, it's really quite simple. DragoArt has this vid...

The cinematic photos feature in Google Photos can create impressive three-dimensional views of normally flat images, turning ordinary pictures into life-like representations of the moment captured. Google Photos would automatically pick images from your library to apply the effect to. Now, you can choose images on demand from your library — it's just not super obvious that you can.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.
Dreaming up the next big business is easy. Running day-to-day administrative tasks is not. The tedious nature of entrepreneurship is the barrier that holds many people back from realizing their full potential.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

The LG G6 was officially announced by LG at Mobile World Congress 2017 in Barcelona and released in the US on April 7, 2017. The device is almost exactly what we've been expecting from all of the rumors and leaks building up to its release. The modular design we saw in the G5 is gone, taking the removable battery with it. However, we do gain waterproofing, an improved dual-camera setup, a larger screen with smaller bezels, and Google Assistant.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...
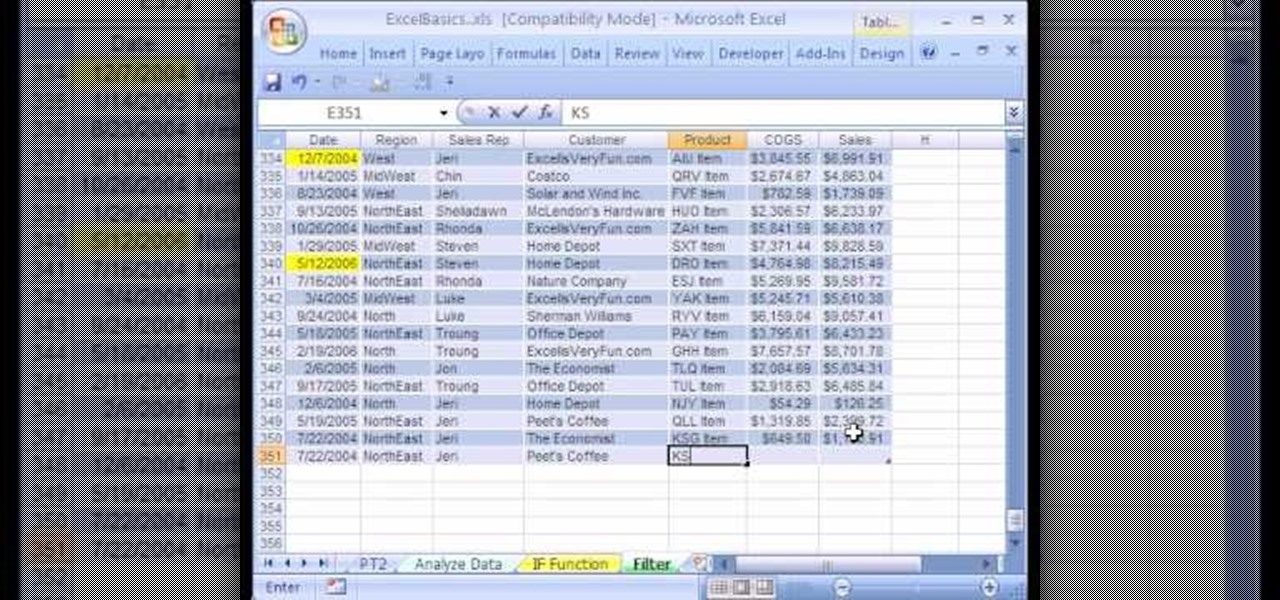
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

Google Chrome is finally here, and everyone can benefit from a faster, streamlined web browser. This video will cover all the basic functions and features of the new Chrome we browser, so if you're thinking about switching, this is a must-see.

This video tutorial is going to show you how to use Skype over the 3G network on your iPhone. For this purpose you will need a jailbroken iPhone. Go to Cydia and launch it. This will take a bit of time. Make sure you have the latest Mobile Substrate & Skype. If not, follow the video and download and install it. Then press home button and come back to springboard and click on Skype. It takes sometime to load. Press on the free phone and press call. If you want you can select speaker and there ...

Your brain actually needs to be refueled throughout the day, and our brains function best on carbohydrates. Brain foods like fruits and fish are important for fueling your brain all throughout the day. Learn some tips on eating brain foods and keeping your mind active in this nutrition how-to video.

Understand the way accordions function in this free video series that will help you play your accordion with ease and comfort.

Sometimes is gets rather difficult to see certain things on the palm sized iPhone. Take a look at this tutorial and learn how to zoom in on the iPhone's screen.

Your iPod can function as more than just an mp3 player, it also works as an alarm clock. Take a look at this tutorial and learn how to set an alarm on your iPod and wake up to your favorite playlist.

In this blessing, we express our gratitude to HaShem for the fact that our bodies continue to function properly. The Asher Yatzar prayer is over two thousand years old. This video explains how to say this Jewish bathroom prayer.
If you just got done watching the video tutorials on the "human skeleton structure," then this is your next step. Check out this educational science video series on the neuroanatomy of the human body.
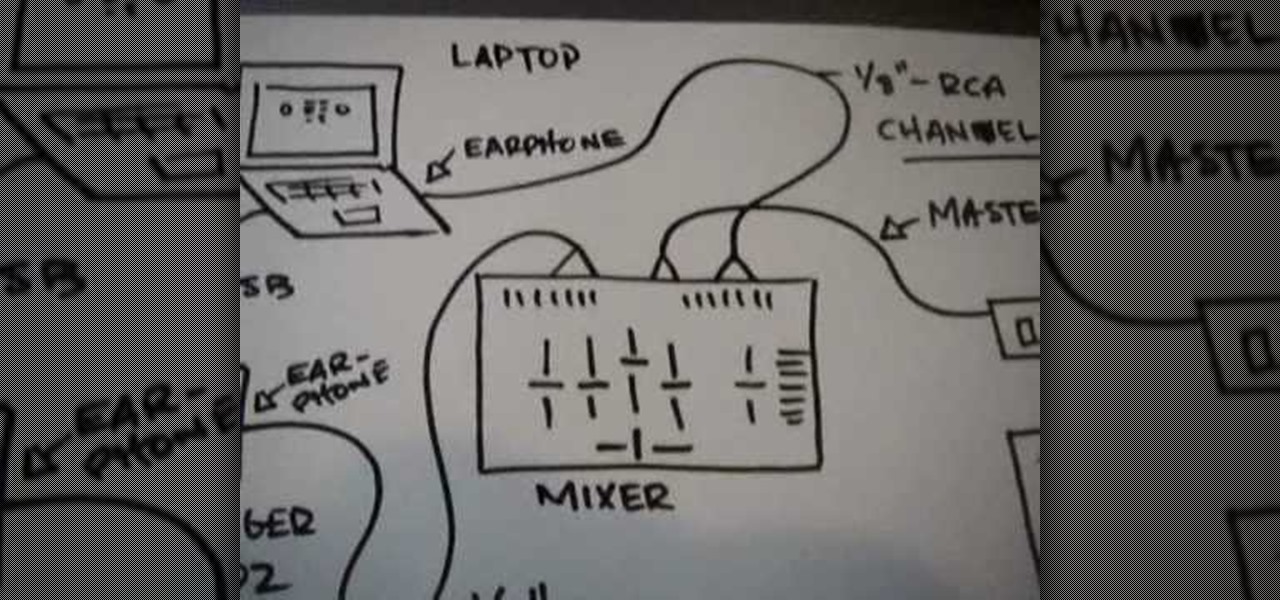
This video shows you how to connect your laptop to your mixer. First you will need two different sound sources from your laptop to your mixer. This is so that you can use all of your mixer functions on two different channels. The way to do this is to run a 1/8" RCA cable channel 7 from your normal earphone jack to the mixer. Also use a behringer uca202 audio interface to connect to the laptop via USB cord. This provides another earphone jack. Then use a master out cable to connect it to an am...

This video shows you how to enable cookies in Google Chrome browser.Enter Google Chrome. First of all, select the last icon in the upper right corner of the window (the one that looks like a wrench) and click on options. Then choose the "Under the hood" tab and scroll down until you reach the cookies section. All you have to do is make sure that the "Allow all cookies" option is selected and click OK.Once this is done, you will be able to use sites that require cookies, which otherwise would ...

Access your computer's BIOS settings

1. The following Steps shows how to open a URL in a Web Browser, using a Button Click from a Flash Application. 2. Open a new Flash Application and place a Rectangle Shape from Tools and inside place a Text Box and Enter a Text named "URL". 3. Then convert it to Symbol by Right Click->Convert to Symbol and selecting type as Button. 4. Goto Button Properties and Name the button instance as "btnurl" 5. Then in the Action Screen Create a OnRelease() Event function for Button "btnurl" 6. use a me...
This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

With the LG KU990 Viewty, you can take and view a crystal clear photo. Packed with high-quality camera features, this camera phone enables you to capture a high-definition image using a 5 MP camera lens certified by Schneider-Kreuznach and edit your photo on a large, clear, 3-inch display just like a professional photographer.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus.

Now that you know the power of the music, in this video series, learn how to use a Korg Triton Studio synthesizer to create songs and melodies of your own. Our synth expert, RT Ouk, will explain many of the basic functions in detail, including how to use the different modes on the Triton keyboard, such as the Combination Mode, the Program Mode, the Sequencer, the S. Play Mode, the Sampling Mode, and the Global Mode. Also get tips on often used buttons like Disk, Compare and Menu, which allow ...

The augmented reality passthrough abilities of Facebook's Oculus Quest were only fully opened to independent developers recently.

Snapchat parent company Snap may finally be taking the big step into the fully-functioning augmented reality wearables realm with the next iteration of its Spectacles devices.
It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

Android 11 is available as a simple beta install for Pixel devices right now. Just visit Google's beta signup page, make sure you're signed in with the same account used on your Pixel, then opt into the program. You'll get an OTA update that will put you on Android 11 in no time. But is it ready to be a daily driver?

Python is commonly touted as one of the best programming languages for beginners to learn, and its straightforward syntax and functionality makes that hard to argue with. But a lot of tutorials still use Python 2, which is outdated now. Python 3 introduces many new features, and it's important to be aware of them going forward, as well as the key differences between Python 3 and its predecessor.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Over the past few months, Google has prioritized the development of its video communications products as the demand for social distancing solutions continues to increase in response to the COVID-19 pandemic.

For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the keynote and developer sessions?

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.
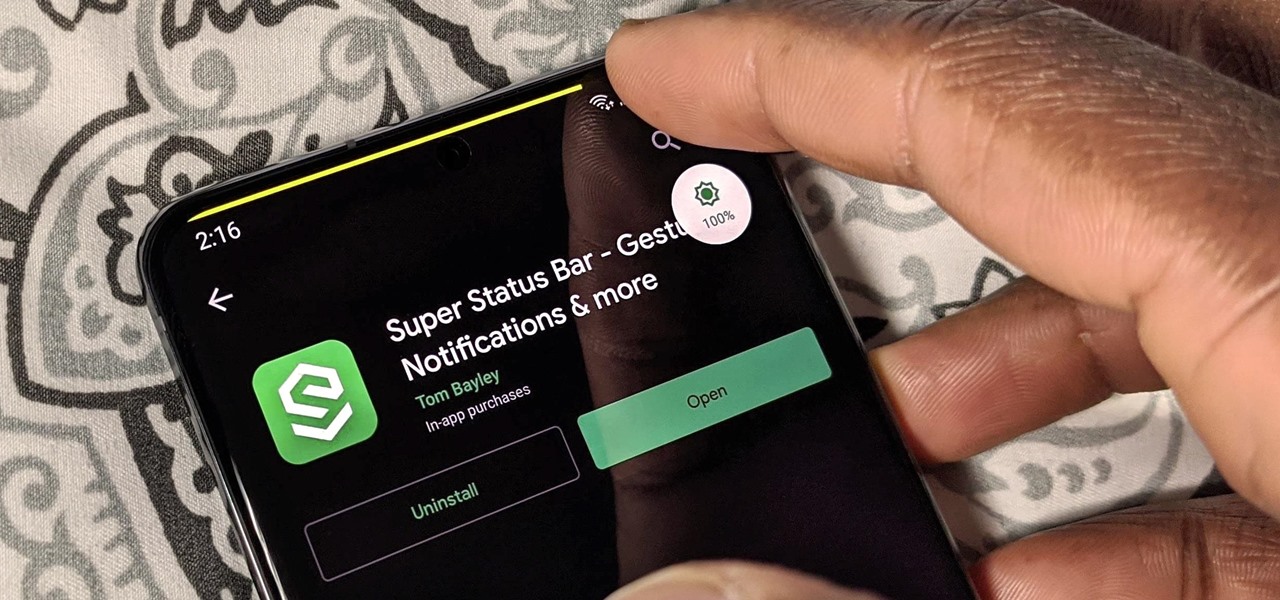
LineageOS is great and all, but custom ROMs were at their peak when CyanogenMod reigned supreme. It had all sorts of innovative features that have since been copied by Google and Samsung and the like. But one thing that still hasn't been adopted into stock Android or One UI is CM13's easy way to adjust screen brightness.