
How To: Green your business
Preserving the environment is not only the right thing to do—it can result in significant cost savings for your business.


Preserving the environment is not only the right thing to do—it can result in significant cost savings for your business.

New windshield wiper blades can be tough to install, but maintaining them is critical for safe driving in bad weather.

Make a splash at your next masquerade party with this purr-fect black cat costume. You Will Need

Make your eyes look bigger and brighter by lengthening your lashes. You Will Need

A perfect, green lawn and colorful flower garden are worth your time and effort. Don't let weeds ruin your hard work.

Find out how to patch up your radiator hose long enough to drive to the auto parts store or your local mechanic and replace it with a new one.

A little planning is all it takes to decorate your dorm with style! You Will Need

Labor is probably the most feared of pregnancy’s "unknowns." Here's how to manage it. You Will Need

Why justify the cost of buying a corsage from your local florist? Make an affordable corsage yourself that reflects your personal style.

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A daily, brisk 30-minute walk boosts brain power, helps control weight, and improves your overall health. And if you commit to doing it with friends, you're more likely to stick with it.

Broken or missing skateboard wheels aren't the end of the world. In just a few minutes, you can replace them.
Don't let fate decide the makeup of your fantasy football team. Participate in a live draft with these tips.

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.

Doing the laundry uses a lot of water and energy. Here’s how to wash your clothes with a clean conscience. This video will show you how to conserve energy when doing laundry.

Learn how to cope when a pet dies. Few will ever love you as unconditionally as your pet does. So when you lose them, it's can be hard to move on. Here is some help.

Learn how to decorate your graduation cap. Customizing your graduation cap is a way to stand out among the sea of identical, ill-fitting graduation robes.

Renting is only half the battle – setting up an artist’s studio demands patience and preparation. Learn how to set up an artist's studio with this how to video.

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Don’t know your LCD from your A-S-S? We’re going to fix that. Learn how to choose the right flat screen for you with this Howcast guide. Flat screens are pricey, so make sure you know what you're doing.

Is your child a gimme monster? Put a lid on demands and tantrums with these tips. You Will Need

Go thrifty! Go vintage! Go second hand. With the right approach and an open mind, a trip to your local thrift store can yield some fashionable bargains. Buying used is a smart solution to this economy, and gives you a smart sense of fashion.

Learn how to play "Take Back The City" by Snow Patrol, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Wearing vintage clothing is one of the best ways to reduce the environmental impact of your fashion choices—short of walking around naked.
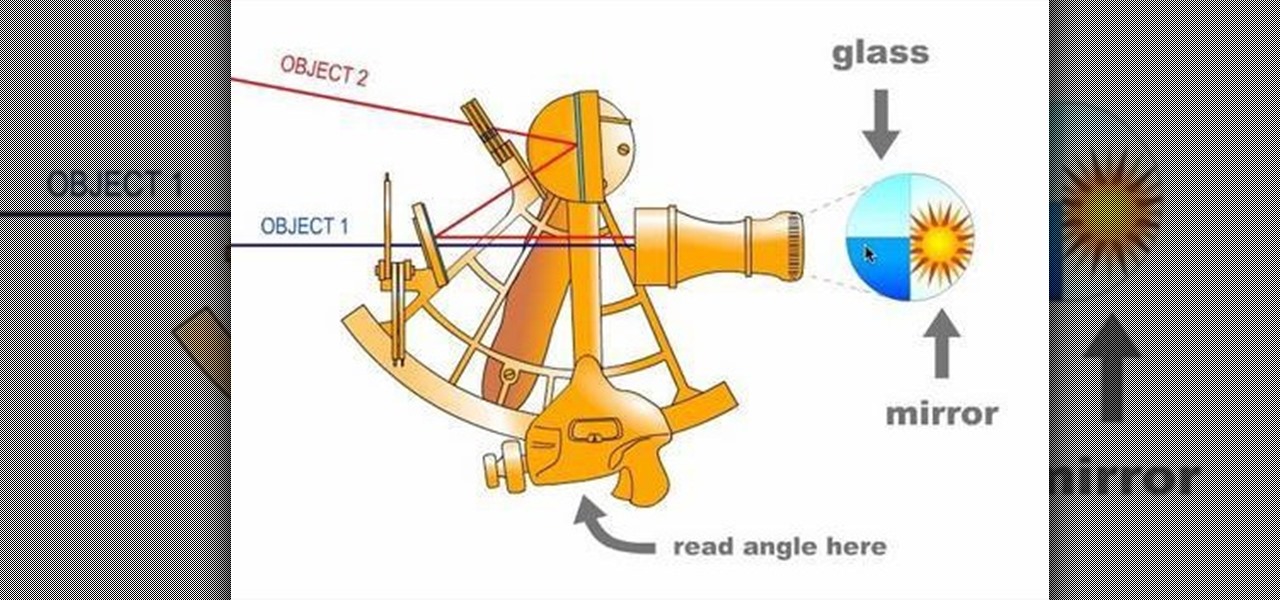
Learn how to find south, your latitude, and your longitude with only a few household items and some know-how, just by watching this science video tutorial. However, if using the homemade quadrant cited, the precision of your findings will be rather low. Don't worry, you'll be within a few hundred miles though.

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Luke Bryan song. Not just any Luke Bryan song, but one of his greatest: "Country Man." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Gymnastics is one of the most physically demanding and difficult sports in the world. Here are a few intermediate tips for anyone wanting to take their skills to the next level.

Making a PCB is very simple; it does not consume a lot of time and the results look professional. After watching this step-by-step how-to video, you will be able to make your own PCB in your workshop using just a few inexpensive materials.

The Hyco cold vaporizer. This is a cold vapor unit which can give 50-80 % fuel mileage plus, if done to the instructions on the video.

Learn how to do heavy medicine ball alternate 2-1 arm snatches. Presented by Real Jock Gay Fitness Health & Life.

Tim Carter shows a clever method that prevents tree roots from entering an underground sewer or septic line. Check for underground utilities before attempting this project.

Adams Holland and his design assistant Debra now decorate a cake. They start with an angel food cake that has already been baked and cooled. They next add an apricot glaze between the layers. It doesn't have to be perfect, it can be messy, that just makes it feel more homemade. They have stiffened some whipped cream, then fill the middle and apply it around the edges. Adams starts low and moves up, that way the whipped cream has something to rest on. Once covered, you might think what a mess ...

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there are plenty of alternatives to get your TV news fix, free of any payment, account, or commitment.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.