Last year, Razer kicked off a new trend by building a smartphone from the ground up with mobile gamers in mind. At the time, many thought the Razer Phone solved a problem that no one really had — but a year later, we're starting to see that gaming phones are perfect for more than just Fortnite players.
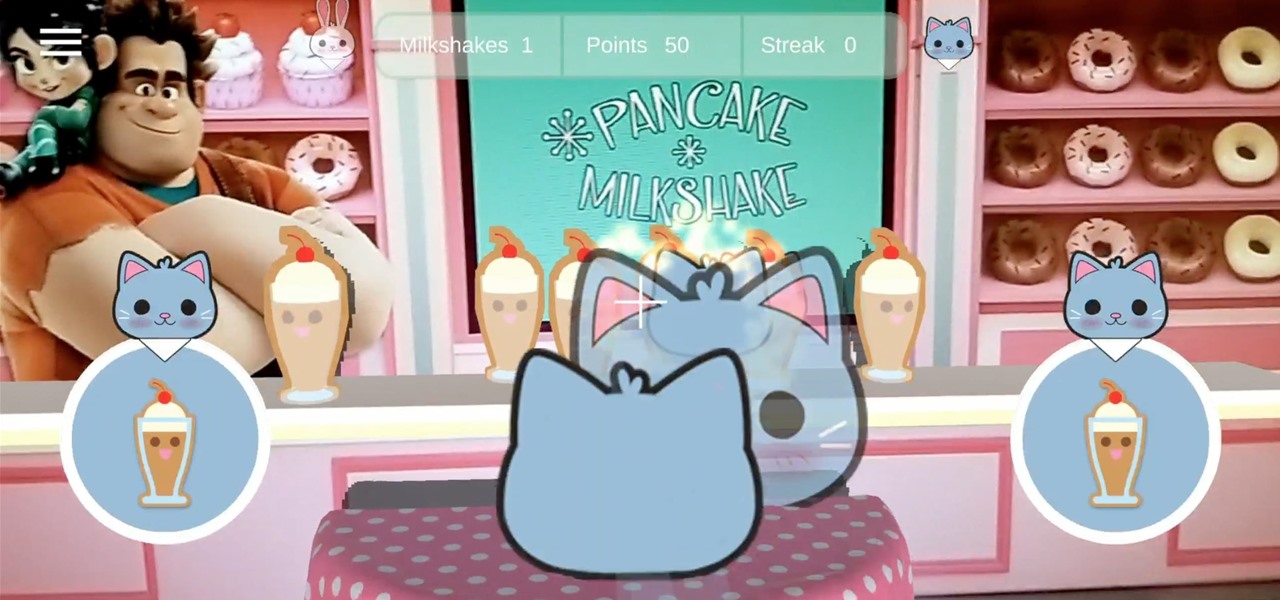
One of the funniest scenes from the teaser trailer for the Wreck-It Ralph sequel is the basis for the new pre-show augmented reality experience via the Noovie ARCade app.

Augmented reality experiences for consumers, for the most part, are relegated to mobile devices at present, but creation and development of those experiences is still a province of desktop computers.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Whether you're new to Android or you just haven't kept up on the app scene lately, we hand-picked over one hundred essential apps that are all designed to improve your experience. From custom launchers and icon packs to weather apps and file explorers, there's something for everyone in this list.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

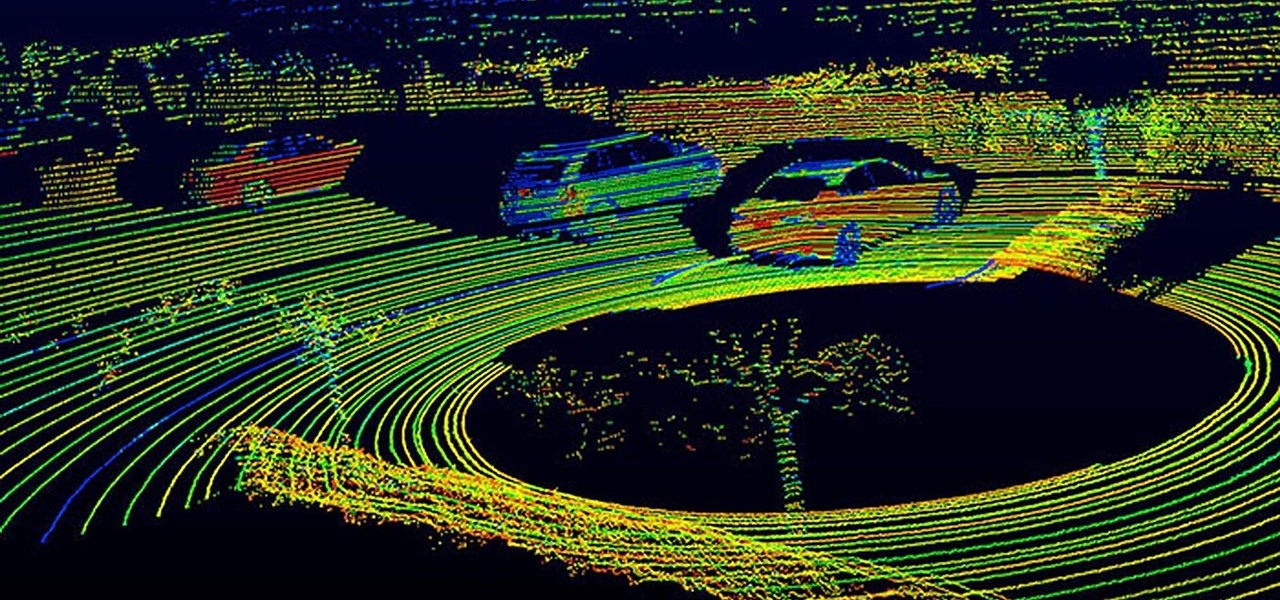
Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Velodyne wants to set the standard for the driverless industry when it comes to LiDAR. To do that, the Silicon Valley-based team just announced its next step — create a low-cost, fixed-laser sensor that can be embedded into a wide range of automotive and autonomous vehicles. That next step is named the Velarray. A sturdy, compact, and affordable LiDAR laser.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

Rabbits have been a persistent problem in Australia for over 150 years. Now the Peel Harvey Catchment Council (PHCC) and Peel-Harvey Biosecurity Group have released a strain of the rabbit haemorrhagic disease virus (RHDV), called RHDV1 K5, to reduce the number of pests in the Murray region of New South Wales.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

Step aside, Heinz: there's a new ketchup in town. Beetroot ketchup is the rising star of condiments. It's a vibrant, earthy, and sweet topping for summer BBQ burgers and grilled hot dogs, as well as a pretty un-beet-able dip for French fries. There's no corn syrup, it's paleo-friendly, and the beets give it a bright, bold flavor like no other sauce you have ever tasted.

Mochi seems to be everywhere these days: as a topping at your local frozen yogurt shop, in ice cream balls (the green tea ones are heaven), and as colorful treats all over Instagram. It seems like mocha mania is in full force!

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Cooking on a budget isn't always easy, but there's a silver lining: it can be really fun. Ever since I started supporting myself I've enjoyed going shopping, finding the most affordable items, and learning how to make the most of them. Sure, sometimes I wish I could afford to buy a filet mignon and some morel mushrooms every night, but there's a different kind of enjoyment that comes from being able to turn a few dollars into a gourmet meal. For me, that means starting with cheap meat, and af...

Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

Depending on who you ask, the OnePlus One smartphone has so far been either a bit of a letdown or a rousing success.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

The mother of all games is almost here. Super Bowl XLVIII pits the Seattle Seahawks (or Seachickens, if you're from the Bay Area) against the Denver Broncos and regent exemplar of neck surgeries, Peyton Manning.

It's no surprise that Costco has great deals, and that's why millions pay annual fees for the privilege to shop in their wholesale outlets. Just take their hotdog and soda combo for $1.50—it's the same price now as it was 27 years ago.