
Apple AR: Cambria & Markilux Match IKEA with ARKit Apps for Home Makeovers
IKEA won't be alone among ARKit apps for visualizing home décor and improvements when iOS 11 arrives next week.


IKEA won't be alone among ARKit apps for visualizing home décor and improvements when iOS 11 arrives next week.

With Apple ready to unleash ARKit to millions of iPhones and iPads and ARCore on its way to supporting millions of Android devices, is there room in the world for a cross-platform mobile AR platform?
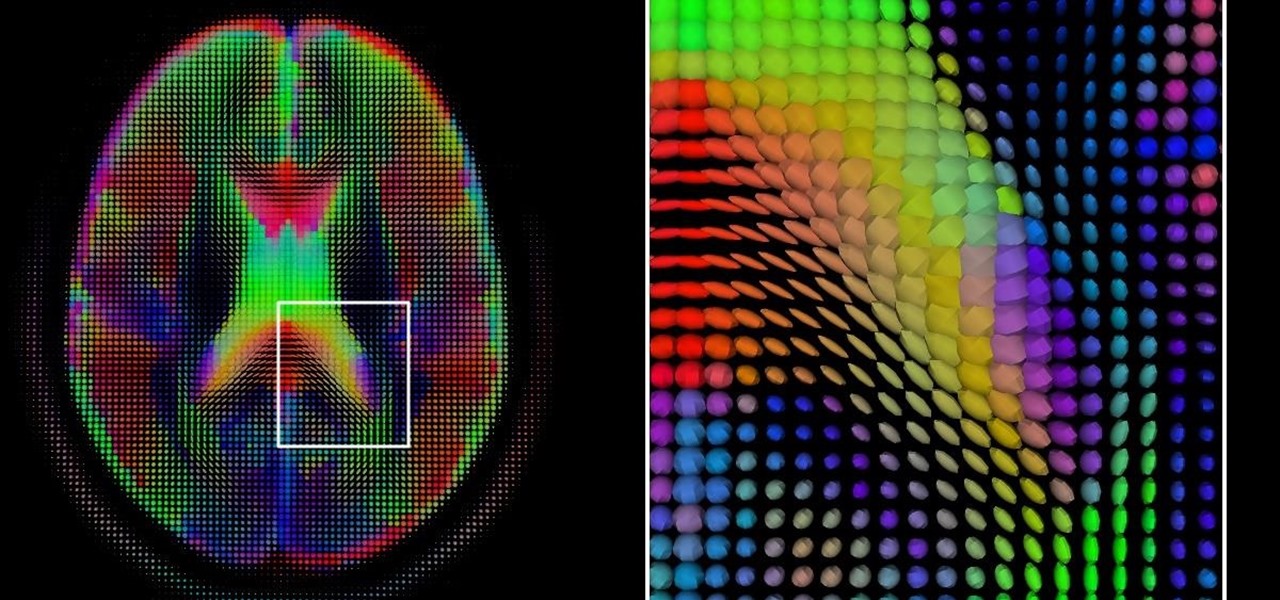
The world is a massive place, especially when you consider the field of view of your smartglasses or mobile device. To fulfill the potential promise of augmented reality, we must find a way to fill that view with useful and contextual information. Of course, the job of creating contextual, valuable information, to fill the massive space that is the planet earth, is a daunting task to take on. Machine learning seems to be one solution many are moving toward.
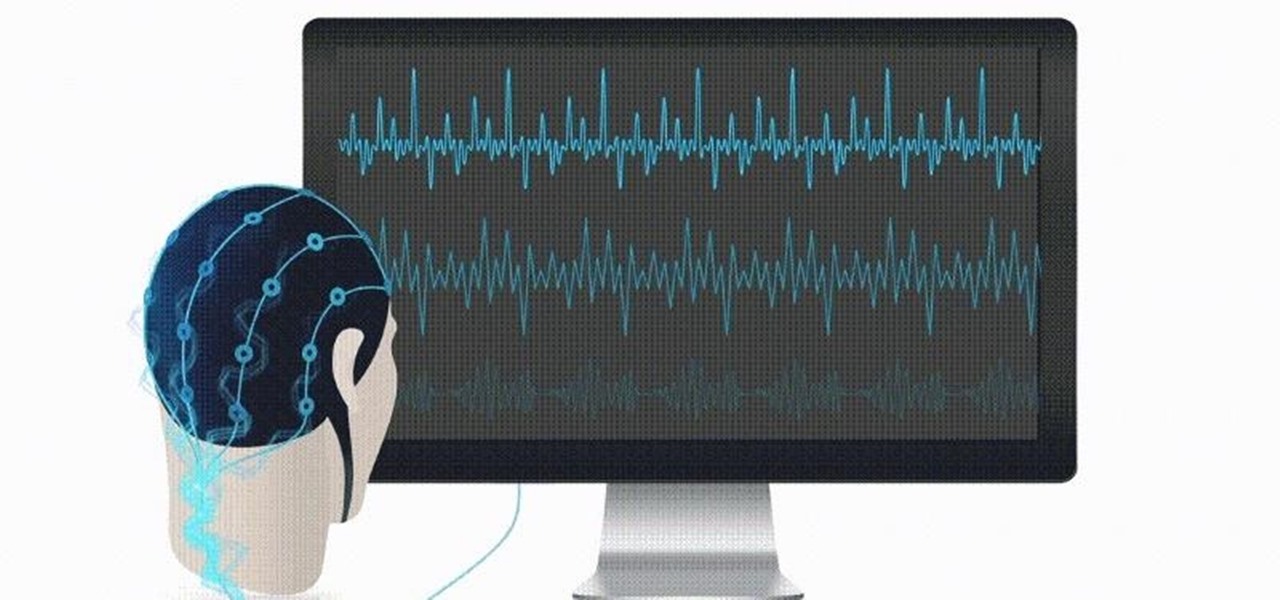
As promised earlier this year, Neurable has introduced limited beta of a Unity-compatible software developer's kit (SDK) for its brain control interface (BCI) for augmented and virtual reality.
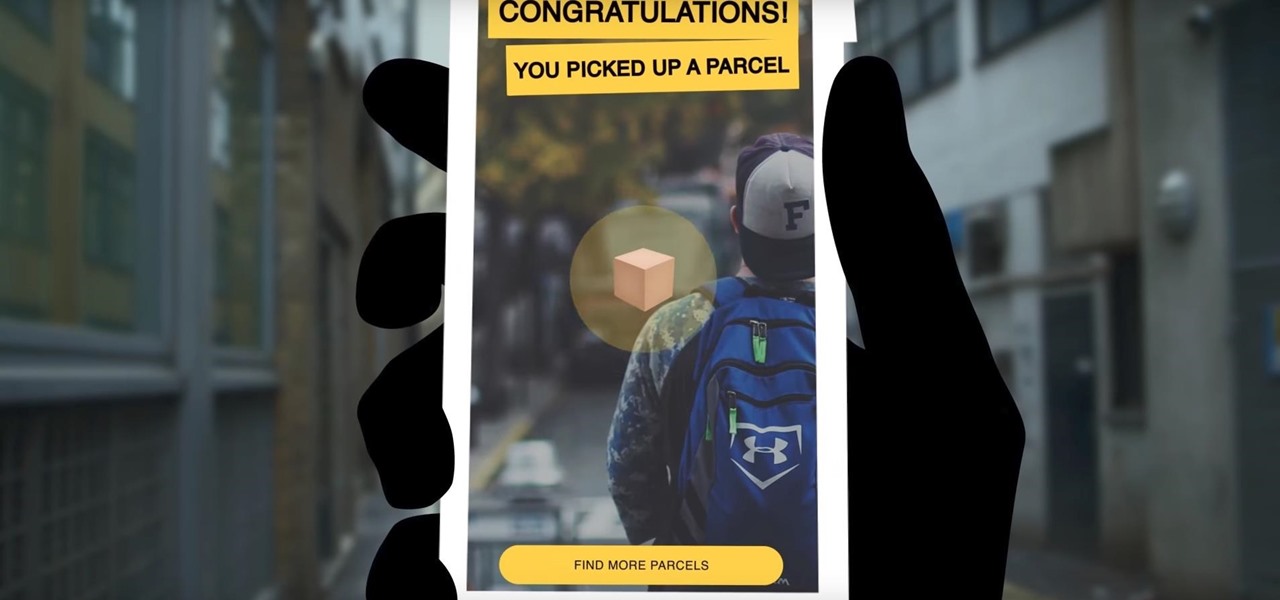
Free beer and AR? What could be better? Amstel, a Dutch beer brand, has launched an innovative sampling campaign using an AR app called "Snatch." Snatch is a treasure hunt gaming app, and if you win the game, your prize is 10,000 free pints of Amstel beer, redeemable at Mitchell & Butler pubs.

Mimesys, whose core focus has always been about creating holographic representations of humans for virtual and augmented reality, has released a video showing off their holographic communication platform in action. This new communication tool uses a combination of virtual reality, with the HTC Vive and a Kinect, and mixed reality, with the HoloLens, to allow the users to have virtual meetings from anywhere in the world as though they are in the same room.
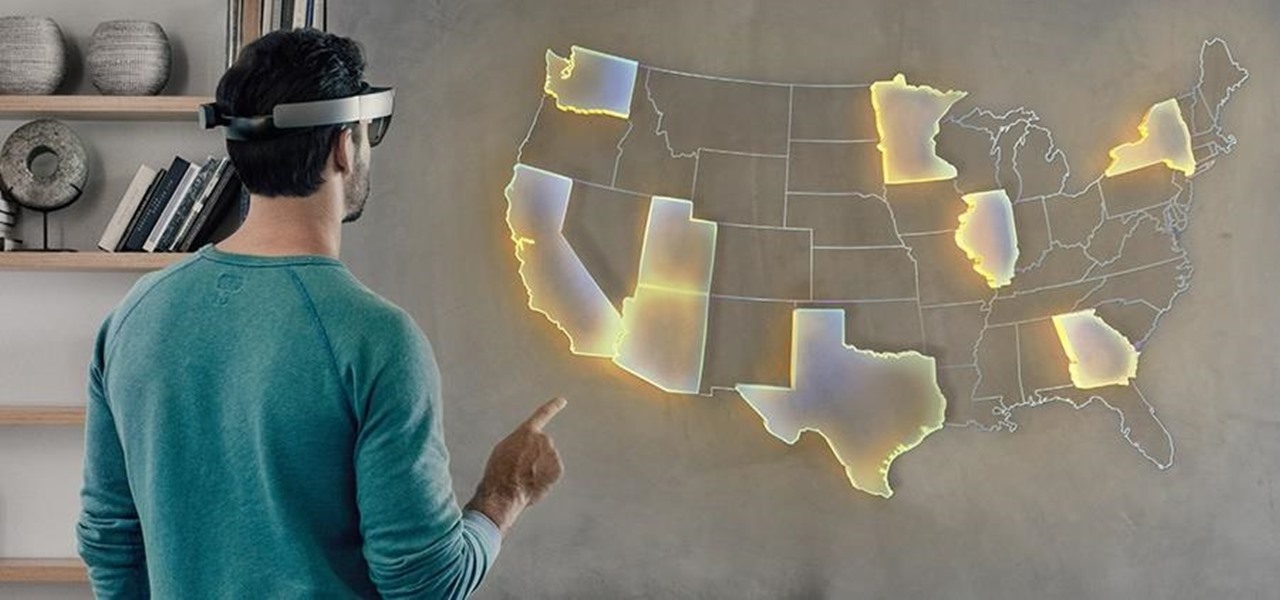
Mixed reality (MR) feels like an amazing, almost mind-blowing futuristic technology—but only once you've experienced it for yourself. Words, images, and even videos simply cannot describe the experience in full. If you want to really peer into the future and experience MR for yourself, you can sign up and just go in many cities.

Hello again, ***UPDATE: Adding links to the other Two articles****

At first glance, the Big Green Egg looks like it was created by Dr. Seuss or some other whimsy-driven being, like Zooey Deschanel. And while this earthenware cooker may look cute, it produces serious results that can rival the best barbecue or grill. In fact, it's got quite a large cult following. Entrepreneur and former Navy serviceman Ed Fisher fell in love with the taste of food cooked in kamodos (traditional domed, covered earthenware vessels in Japan) and began to import them for sale in...

It sounds like a dream come true: just press a button on your phone, and 30 seconds later, a machine produces a custom-made, ready-to-eat meal. Finally, science comes through for the truly lazy!
I wrote this about two years ago to help people make realistic passwords. The best part was while writing it I realized I encrypted the list in a manner only the maker would know.... on to the show

By now, everybody knows that overcharging a battery will reduce its overall life span. This is why many smartphone manufacturers recommend that you charge your device to 100%, then unplug it immediately. Some even go so far as to automatically stop charging when the device is fully juiced, although not all devices have this functionality.

Say goodbye to your boring stock Apple keyboard, because when iOS 8 is finally released, you'll be able to use Fleksy, SwiftKey, Swype, TouchPal, and other third-party keyboards on your iPad, iPhone, and/or iPod touch.
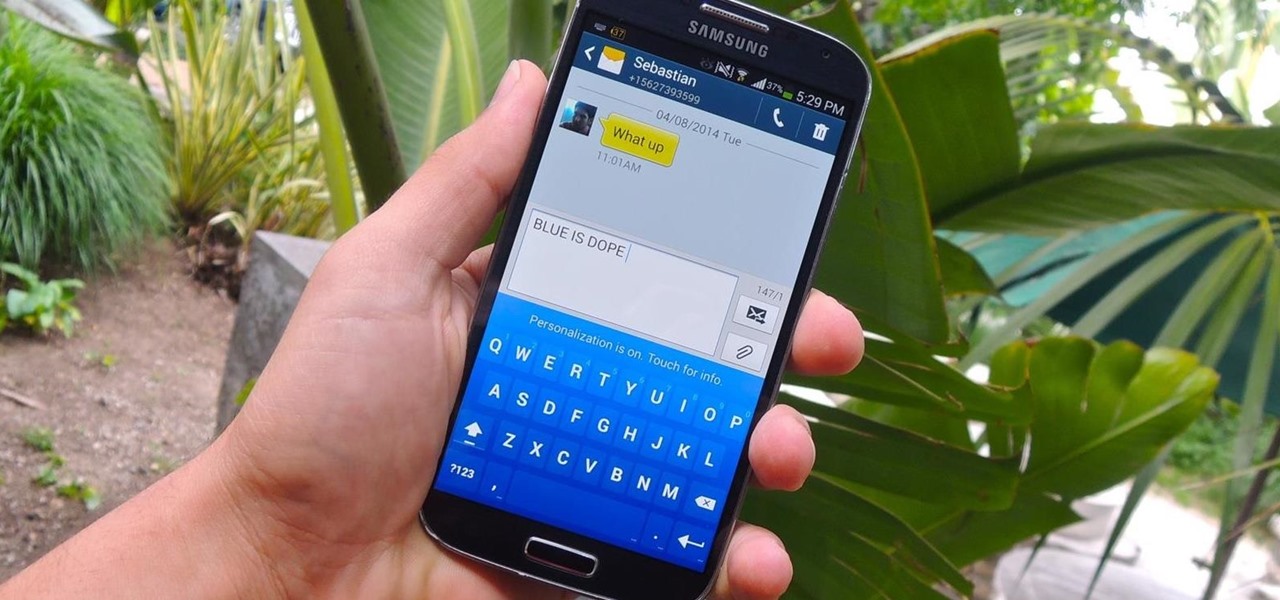
The Galaxy S5 may be the new kid on the block, with fancy features such as a fingerprint scanner and dust/water protection, but the Galaxy S4 is no slouch by any means. While the S5 may be newer, the S4 remains beast of a device, and few simple mods can make it feel new again.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.
When it comes to our smartphones and tablets, we're always on the lookout for ways to beat the oh so common rapid battery depletion problem that affects practically every mobile device. We'll do anything and everything to keep our battery life at an optimum, from turning off certain features (Wi-Fi and Bluetooth) to removing widgets and applications that use an exorbitant amount of CPU. One of the most popular and efficient ways of saving battery is to lower the screen brightness. Usually, we...

Even though I am not cool enough to use Instagram on a daily basis, I still try to stay in the loop. I did take photography in high school, so I know a thing or two about picture taking. I just can't seem to find the motivation to take a picture of random crap during my daily routine, but I guess that's why I'm Instalame.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

The cost of scrapbooking can really add up. You can still create wonderful scrapbooks to artistically document your memories by shopping smart and cutting costs by being resourceful. You can use things you already have around the house.
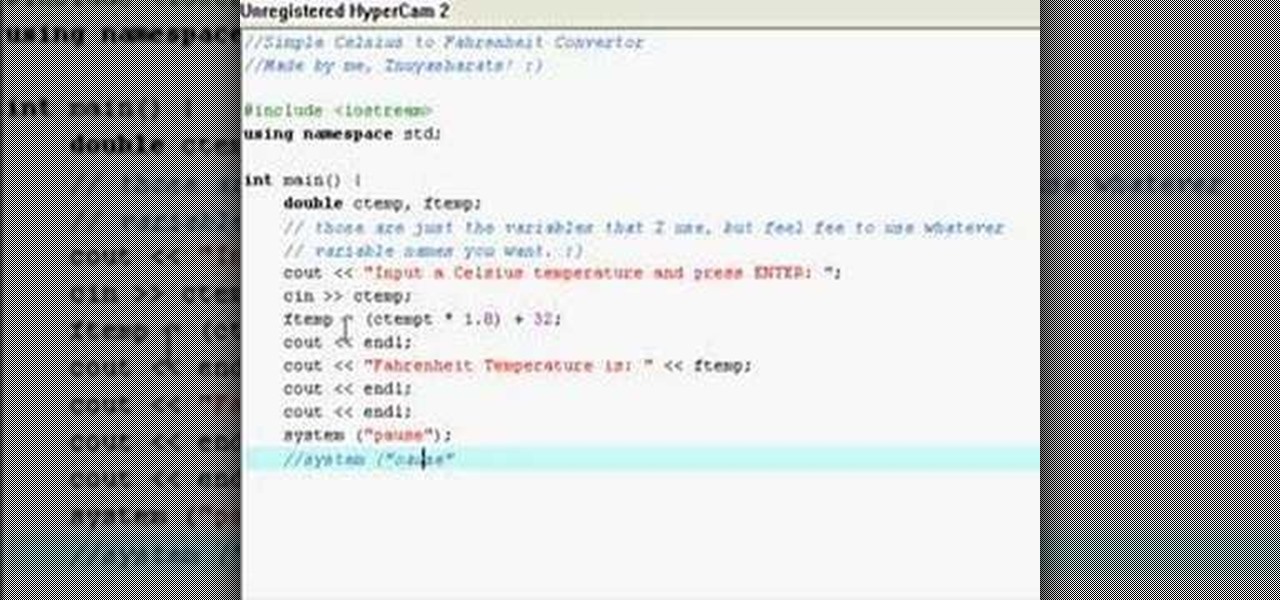
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

Glass art incorporates many different types of glass including beveled glass, rippled glass, water glass, and many more. See samples of these and many other types of glass in this free video series.

Learn how to create a pretty blue eye look with the MAC Naughty Nauticals collection with this makeup tutorial. You will need Lancome Liquid Foundation Sample, Clinique Perfectly Real Powder, CoverGirl Cheekers Blush in Plumberry Glow, Jordana Eye Liner in White, MAC Pigment in Mutiny, Milani Eye Shadow in Blue Lace, Urban Decay Eye Shadow in Polyester Bride, Clinique Mascara in Black and CQ Lipstick in Royal Red. This is a perfect tutorial for drag queens and transexuals. Watch this how to v...

For awhile now, Google has offered the ability to translate text through smartphone cameras via Google Translate and Google Lens, with Apple bringing similar technology to iPhones via Live Text.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

After hosting an augmented reality experience using its Snapchat Landmarker technology at the Statue of Liberty, Snap is now giving creators the opportunity to create their own Lenses with Lady Liberty.

When it comes to building luxury cars, Bentley certainly knows what it's doing. However, when it comes to building an AR app, Bentley is looking less Continental GT and more Geo Metro.
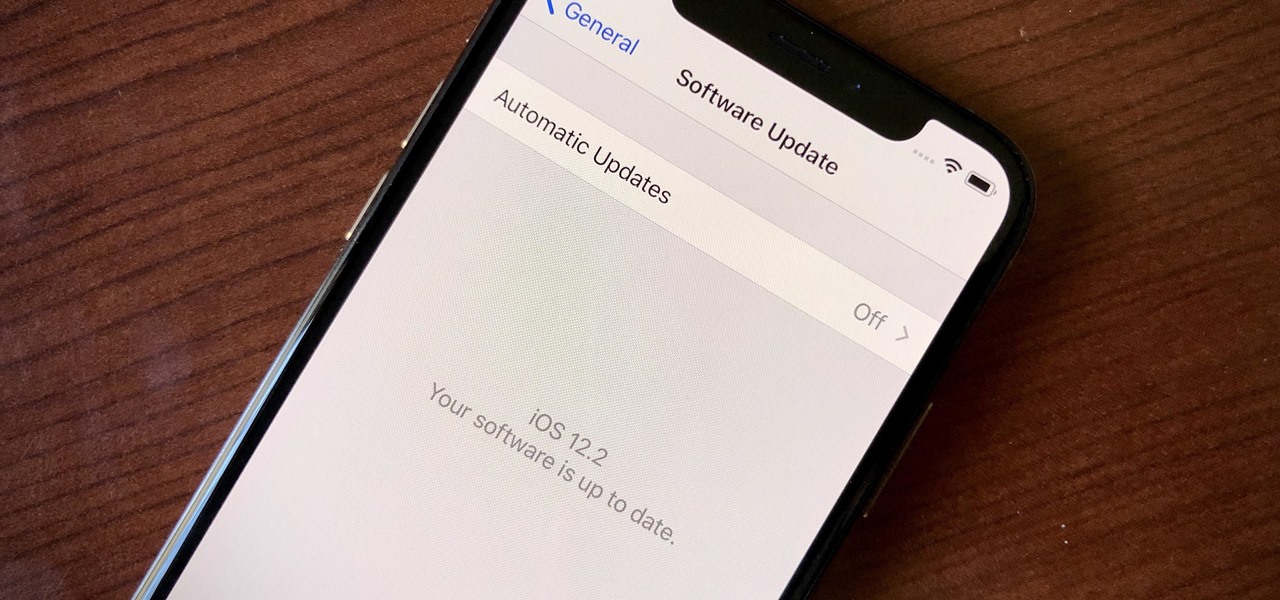
Apple just released the sixth beta release for iOS 12.2 today, Monday, March 18. Just as expected, the update to the developer version dropped just past 1 p.m. EDT (10 a.m. PDT), and comes with new changes and features from iOS 12.2 beta 5 and beyond, including a new warranty status in the "About" page in Settings.

The Oscars are fast approaching, which means that all the most talked about films are getting a second dose of heavy promotion in hopes of winning an Academy Award.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.
On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.