Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

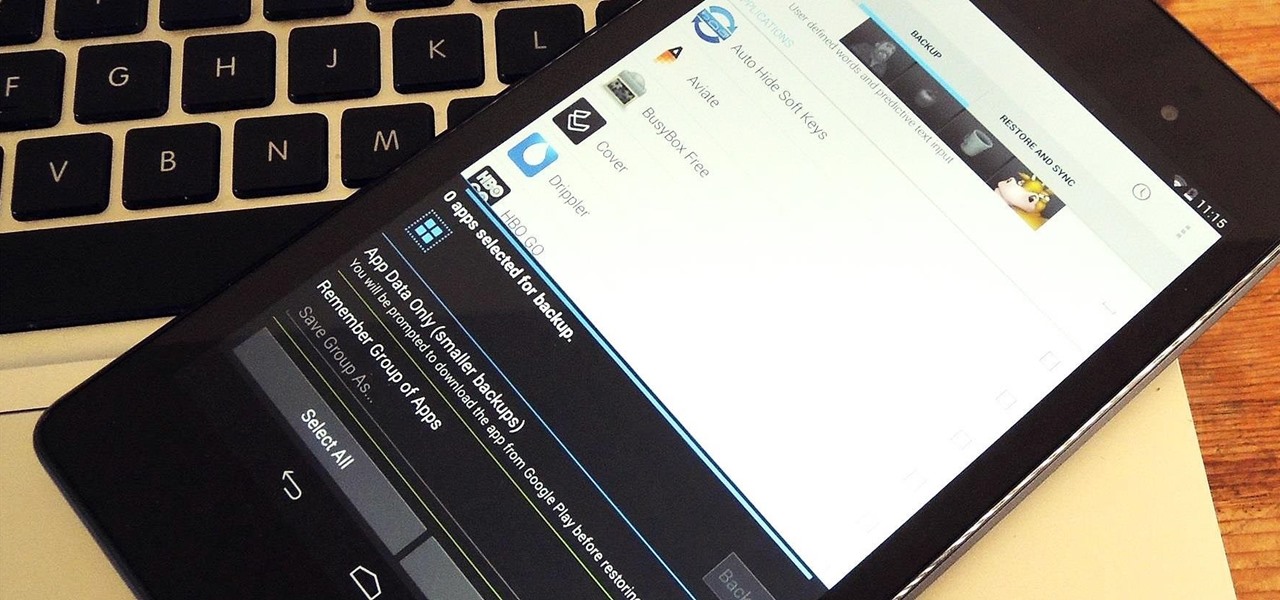
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

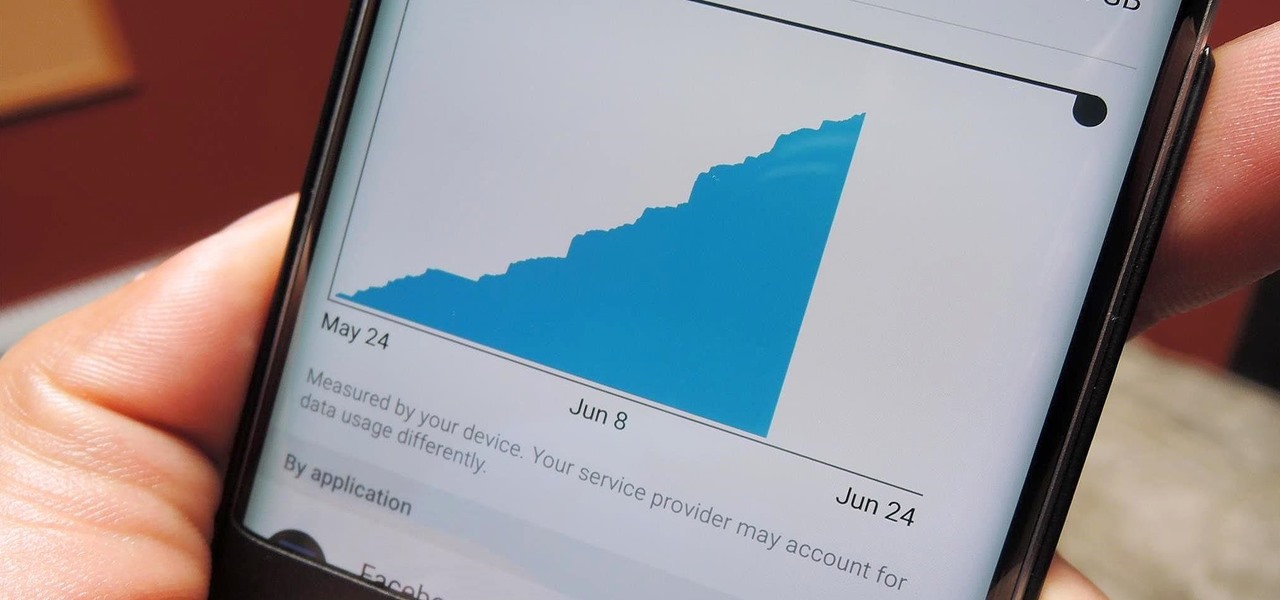
A single movie download can consume a good ten percent of the storage on your Nexus 7 tablet, unless you went all crazy and opted for the 32GB model. Even then you're bound to run out of space fast, especially if you're like me and have tons of media files you want readily accessible on your tablet.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Sometimes you just want to kill a whole bunch of things at once, or to paraphrase Samuel L. Jackson in Jackie Brown, sometimes you absolutely, positively got to kill every mob in the room. Well, the automatic machine gun is the way to do it; accept no substitutes!

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

If you've never done it before, making a podcast can be tricky, with multiple programs to use and multiple file types to deal with. But, this video series helps you through the complete process of creating a podcast, everything including recording, editing, images, exporting, converting, uploading, and finally… sharing. Watch this whole series to learn how to make podcasts using GarageBand, iWeb, iTunes, and Fugu.

In order to set up your email in Outlook Express IMAP, you will need open Outlook. In accounts, enter your user name in the box above: "for example John Smith". Switch the incoming mail server to IMAP. Fill in your server and outgoing mail SMTP.

Are you aware of your water usage? Are you really doing all you can to conserve water, our most precious resource? Here are some simple ways you may not have thought of and some facts about the amount of water wasted on a daily basis in America.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

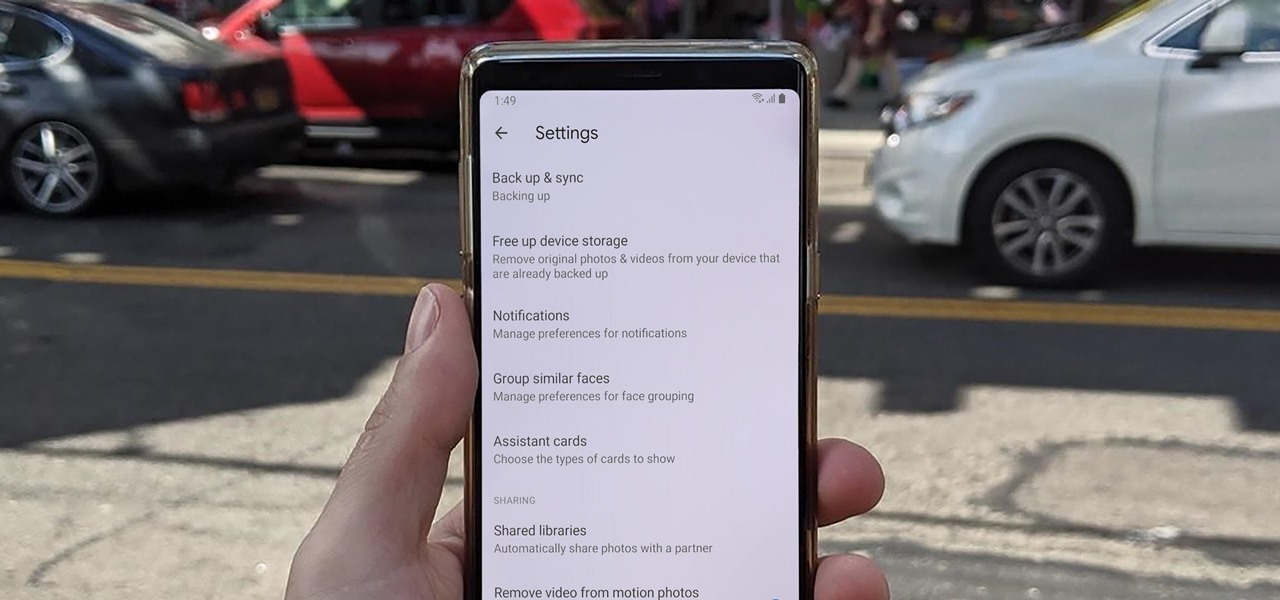
Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.

The augmented reality cloud and multi-user experiences are shaping up to be one of the hotter areas of augmented reality, and now Google is the latest entity to back these emerging branches of AR.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Harry Potter fans can set down their wands for a spell, as the highly-anticipated augmented reality game from Niantic based on the franchise won't arrive until after July at the earliest.

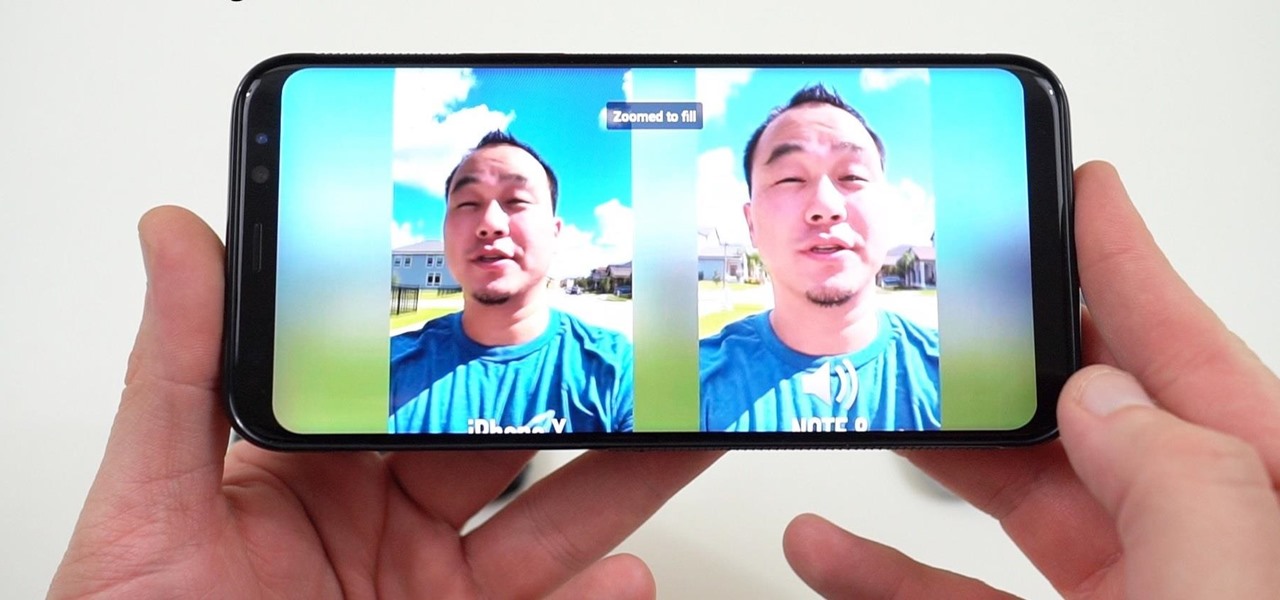
Google launched the Pixel 2 XL with a unique pinch-to-zoom feature in the YouTube app. The feature is pretty basic, allowing users to expand the video to full-screen on devices with 18:9 aspect ratios with a simple pinch gesture. Considering its simplicity, it was strange that the feature was limited to the Pixel 2 XL. Today that exclusivity has ended as the feature is rolling out to the Galaxy S8, Galaxy S8+, Note 8, LG V30, and LG G6.

A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.

If you're new to Plex, there are a couple of things you should know up front. First is how to use it — simply install the Plex server app on your computer and point it to your media library, which you can then access anywhere using the Plex app for iOS or Android. All of this is free.

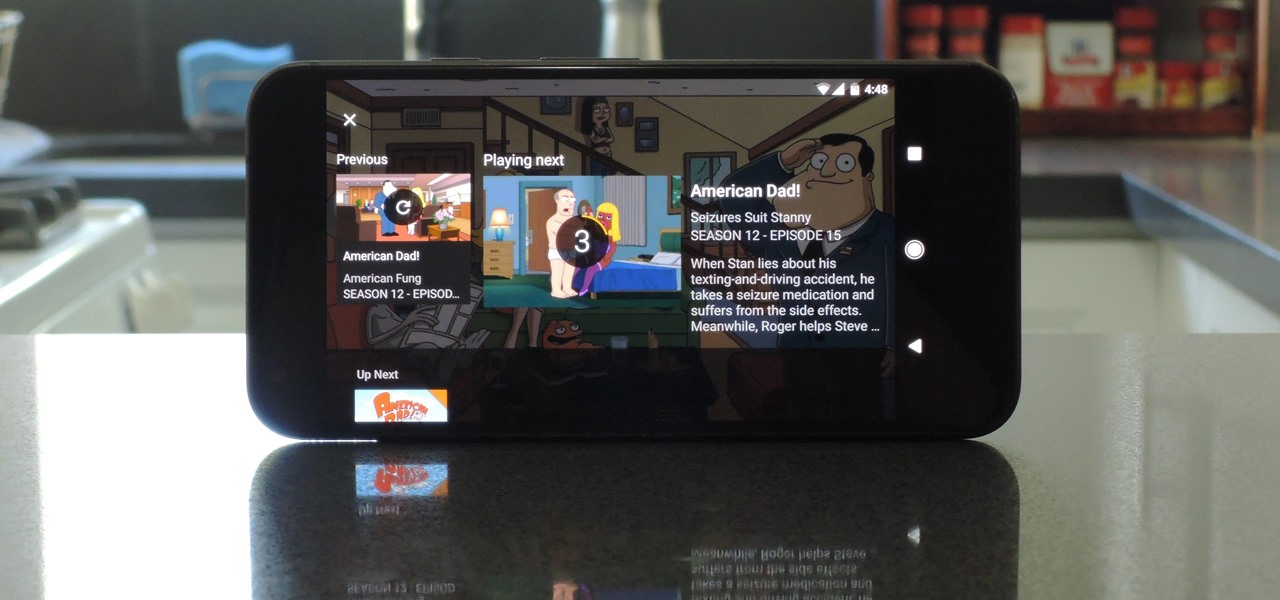
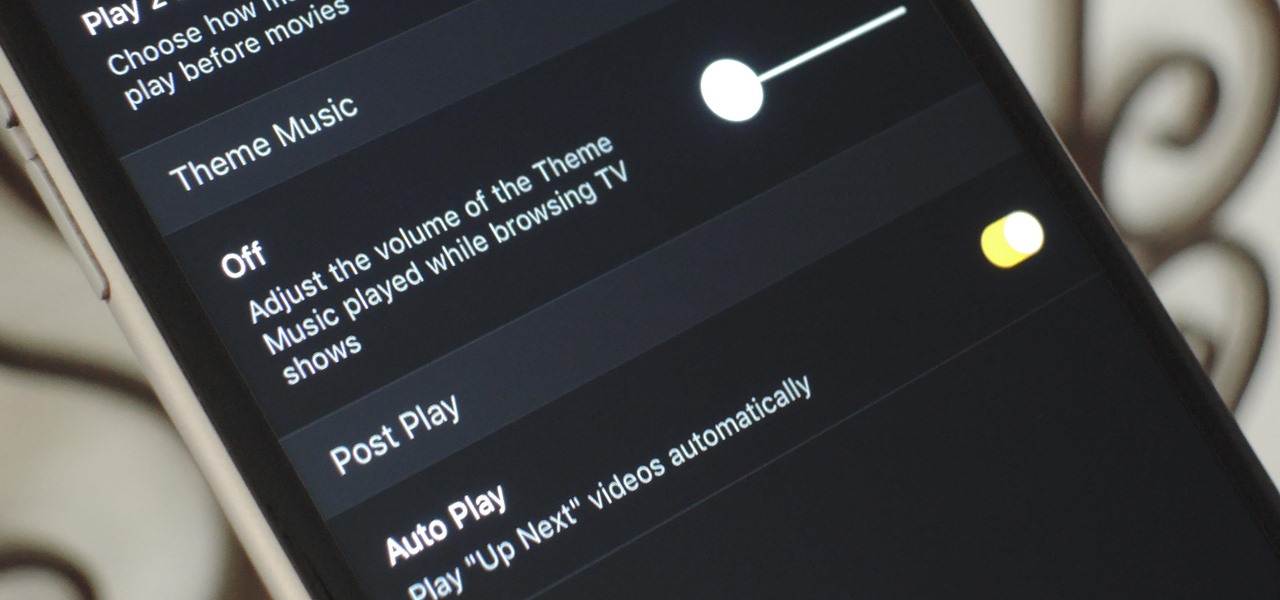
Overall, Plex is a great service. You just install the server on your computer, then you can stream your media library to wireless devices with the Plex app for iPhone or Android. But it does have one annoying feature that's enabled by default: Theme music plays automatically when you're viewing the details page for a TV show.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

Google just announced that it will be bringing the Google Assistant—previously an exclusive feature on Pixel phones—to many more devices in the coming days. The only requirement they're giving is that the phone must be running either Android Marshmallow or Android Nougat, so according to the most recent Android distribution numbers, that's roughly 32% of all existing phones and tablets.

Kazendi, a London-based HoloLens development and rapid prototyping studio, just released a new iOS app in Apple's App Store that lets developers stream HoloLens applications live from the headset to an iPad or iPhone. It's called HoloStream, and is the first iOS/HoloLens crossover app we've seen so far.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.