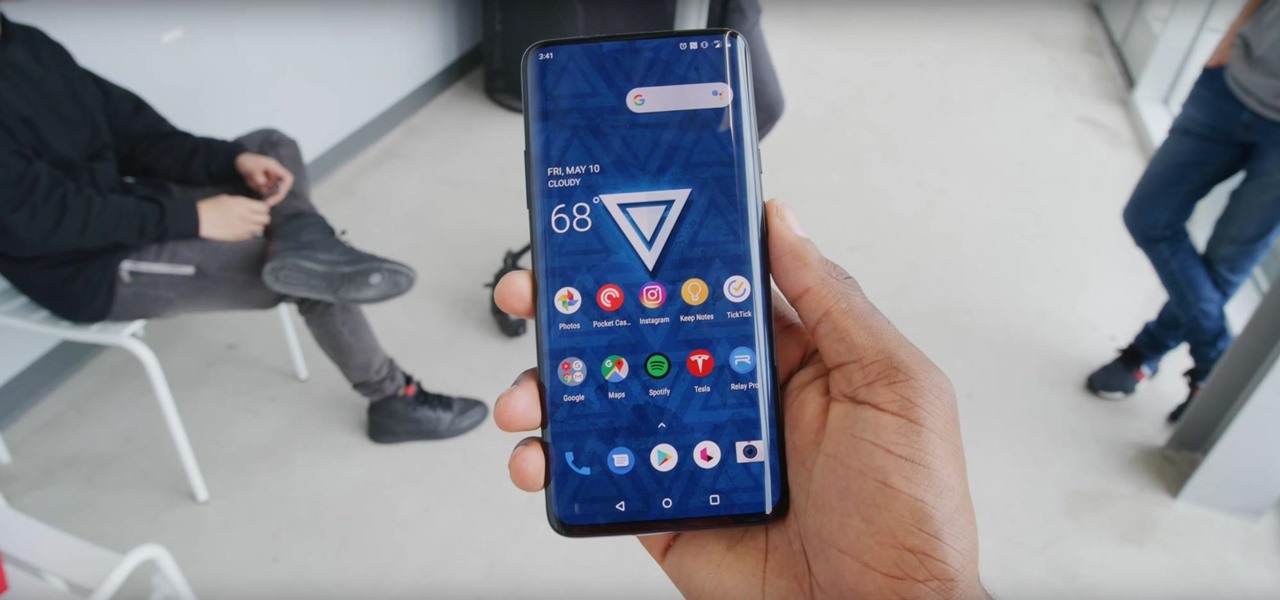
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past Saturday we had a great turn out for the Weekly Workshop, and we even managed to get a few of you in TeamSpeak. Thanks to all who joined in, hope you learned some awesome new things!

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

Things just got a lot better in your iPhone's Messages app, and the most significant change lets you text Android users with iMessage-like features such as typing indicators, read receipts, large file sharing, high-quality photos and videos, and even emoji reactions.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

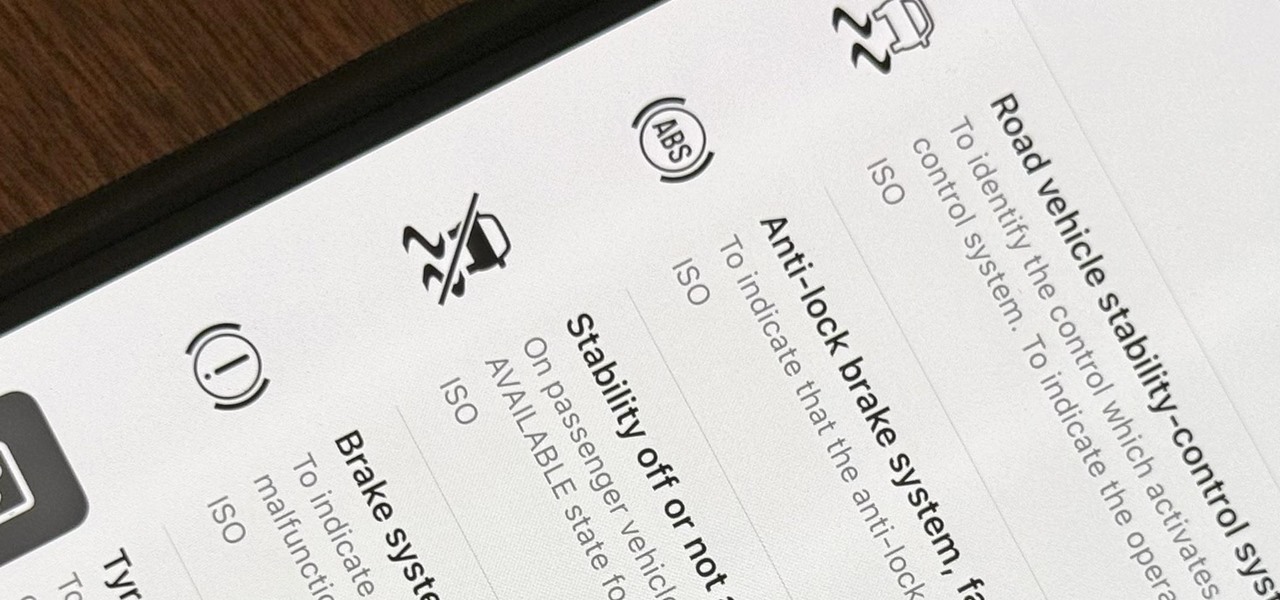
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.

When you take a screenshot on your iPhone, it's automatically saved to your Photos app. You can ignore the screenshot thumbnail or swipe it away, but you shouldn't. If you open the screenshot editor instead, you'll gain access to your iPhone's most useful screen capture tool: full-page screenshots.

With iOS 17, Apple News integrates more deeply with Apple Podcasts and Apple Stocks and has become a bit more fun thanks to new crossword puzzles. But that's not all that appears in the updated News app.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

If you can't access your iCloud data such as emails, contacts, calendars, photos, notes, reminders, files, and other documents via a web browser on untrusted devices, like one at a library or friend's house, there's an easy way to regain access.

You may be tempted to install the iOS 16 developer beta on your iPhone to try all the exciting new features it has to offer, but it may be a good idea to wait if you only have your personal iPhone that you use every day.

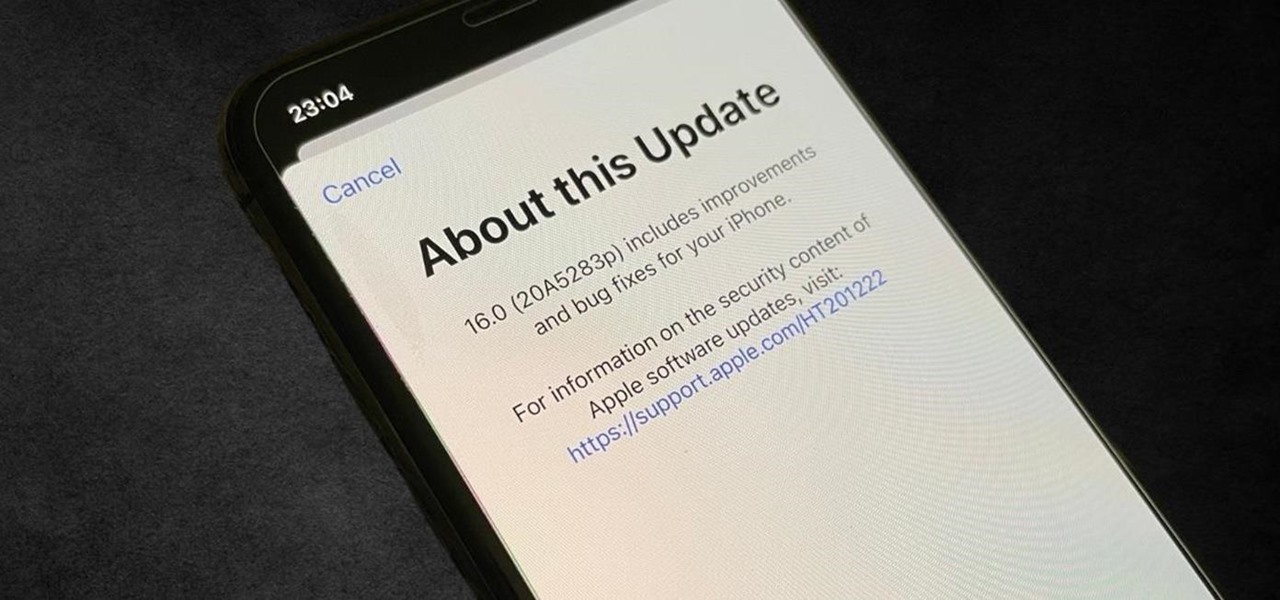
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

Believe it or not, there are legitimate iOS apps beyond the App Store that you can install on your iPhone. Some of them even work for iPad, Apple TV, and Mac, and there are also benefits to using them over apps found in the App Store.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

Apple's iMessage is one of the main reasons to use an iPhone, and there's a lot you can do in chats without being overly complicated. But there's one issue that continues to drive people nuts, and that's the blue typing bubble indicator with the moving ellipsis (•••). Can you stop it? Not officially, but there are workarounds.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

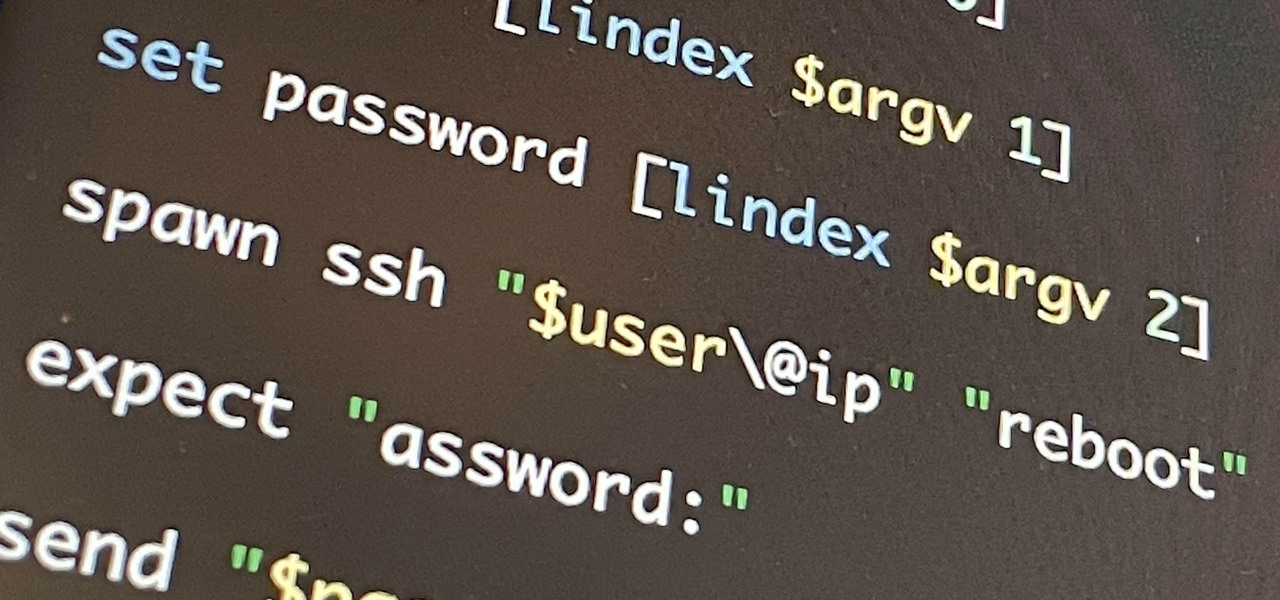
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

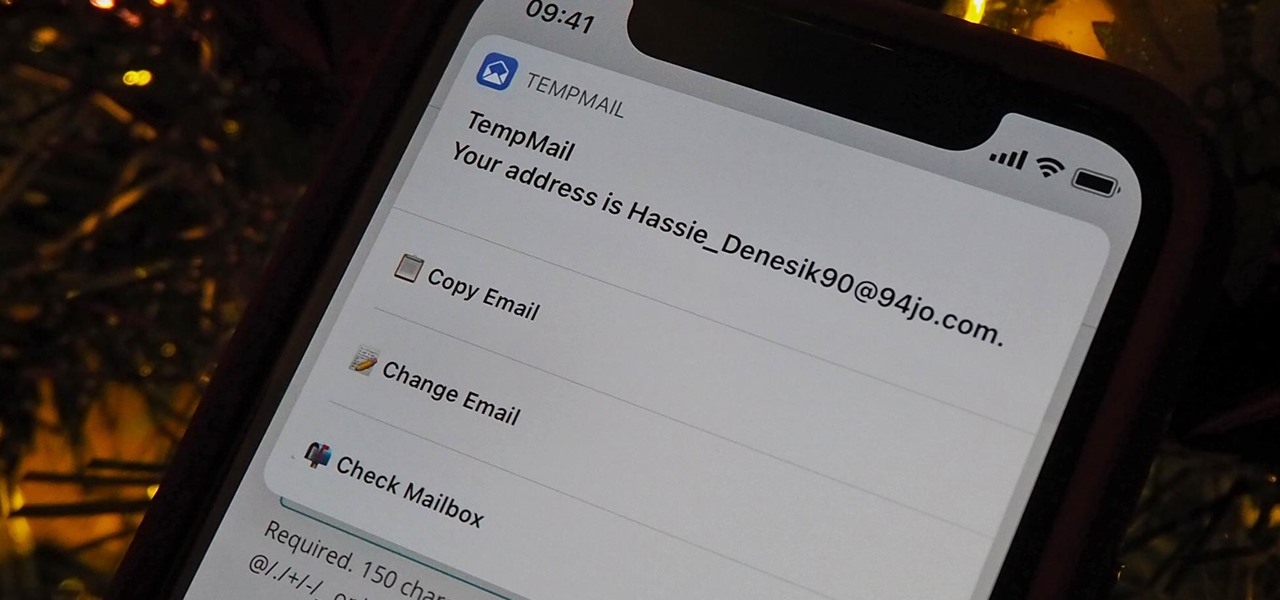
A temporary email can go a long way. Using your actual email to sign up for a mailing list to receive 10% off a purchase doesn't make sense if you don't use the website much. It means you'll have to deal with spam emails from then on, which is why an anonymous email is perfect not to have to deal with all that trouble. And that's where the TempMail shortcut for your iPhone comes in handy.

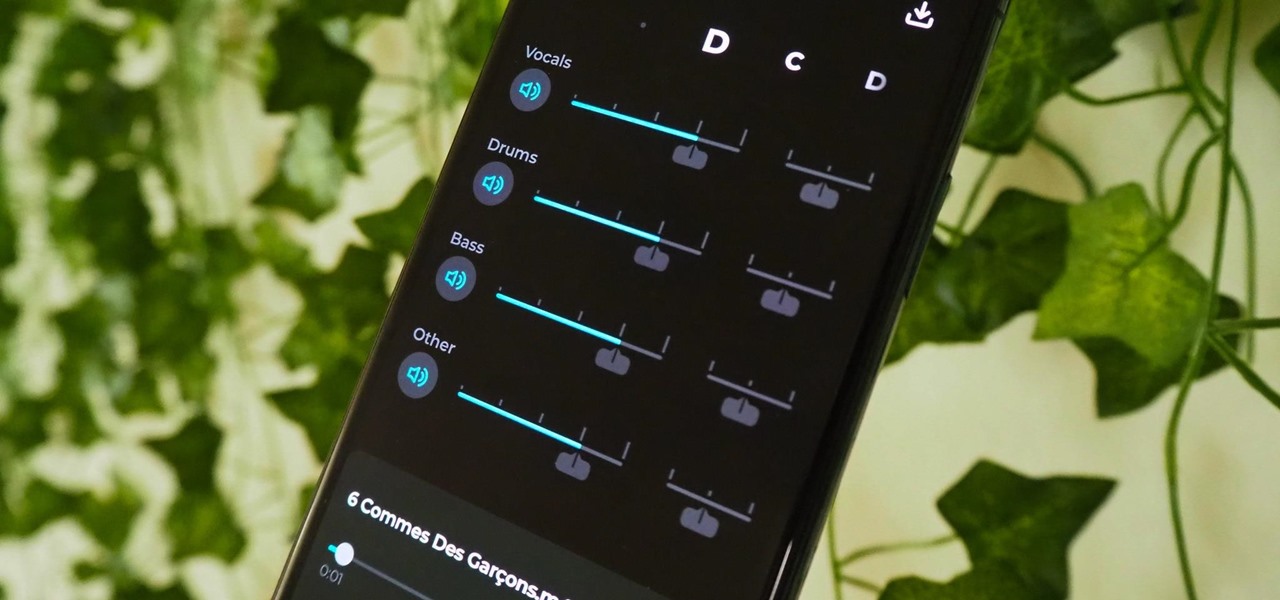
Adobe Audition, Audacity, and other audio editing software have tools to isolate vocals and instruments in regular songs so that you can get an instrumental track for karaoke, vocals for an a capella version, or solo drums, bass, keys, etc. that you can use to learn the song yourself. The software is mostly for desktop computers, and it doesn't always do a good job, but that's where Moises comes in.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.

You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're out of luck, there's a simple way to buy yourself more time.

Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.