
News: Breathtaking "City of the Gods" by NEWDeStRoY1 Wins This Week's Minecraft Staff Choice Awards
Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!


Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!
Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly by using specific search criteria that should yeild results, should it find matches to known mistakes/errors in a website or webserver.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead to mistakes, discouragement, or fighting among a community. What better way to relieve stress and entertain the troops than some old fashioned competition?

Is that House? Built in Minecraft? Well, time to cross out one more item off my bucket list! As inspiration for this week's Minecraft-themed Tuesday Giveaway (enter here to win an awesome Minecraft Pickaxe!), I present a roundup of amazing things found in Minecraft.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

As I was listening to Apple's WWDC conference today, what ran through my mind the most is if there were ever a time to switch to the world of Apple computing now is it. Today's WWDC keynote presentation was chock-full of new and updated iOS mobile software—too much to cover in this one article. But the most "new thing" coming from Apple this Fall is iCloud, a file sharing and streaming service that requires no wired connections.
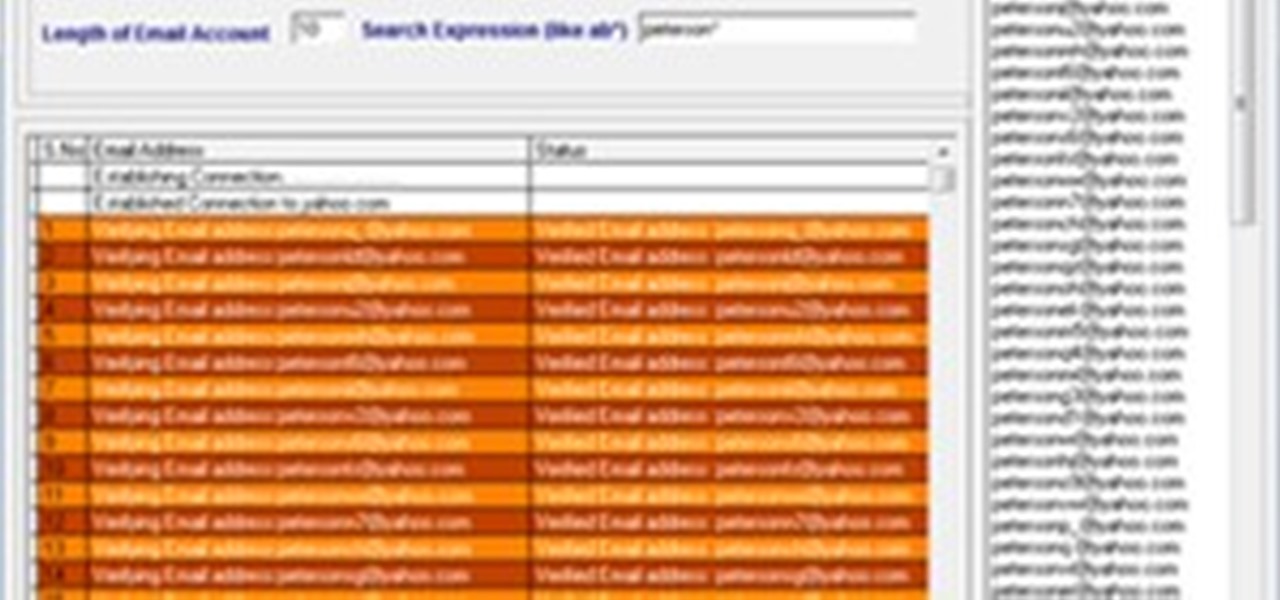
Description: Admit it, having thousands of valid email Ids give you the power to do anything! Such as adding thousands of friends to your Facebook, MySpace, Twitter, etc profiles or promoting your article or blog in just a single click and much more! But how do we do it? I searched all over the internet in a hope to get a perfect email producing software but ended with just two -

Today, we're pleased to announce that WonderHowTo is getting a major site-wide update to make it easier to follow the subjects you're passionate about and to share your creations with people who will give you the kudos you deserve!

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exactly what we do! In our sessions, we have started to both code and complete HTS missions. This means that there is something for everyone here, so make sure you join us.

In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user).

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.

So many of you like to save up your gold coins to buy things like castles, treasure cards and clothing. But sometimes when you buy something, an error message pops up. One of them is this extremely annoying one: "Transaction was not successful."This error happens mostly when buying clothes. Let's say you want to buy a robe, but it is too expensive. You change the color of the robe to brown, yellow or white and try to buy it. When you click Buy, the error pops up. You switch realms. No differe...

The Fake Adult Website Prank is an incredible trick if you happen to have the necessary access and work in the internet industry. Luckily, I had both.

How to set up a Counter-Strike LAN server. You'll need a router. Start a server on Counter-Strike.

This will show you how to host your own teamspeak server for PC games. Very simple and easy, hope you learn something from it. Host your own teamspeak server.
Technology: The Less You Know the Better?
I was looking around on this site and this article caught my eye. It was about hiding text in ADS or Alternate Data Streams. While this is nothing new in the tech world, it seems that more and more people are looking at ADS for one reason or another.

You may have read an earlier post about Egypt blocking popular social websites like Facebook, Twitter and YouTube due to demonstrators disseminating videos and photographs, along with coordinating movements, during the protests against President Hosni Mubarak. In that article, you learned how to use proxy servers and VPN services to bypass those website governmental blocks.

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.

Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...