Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.
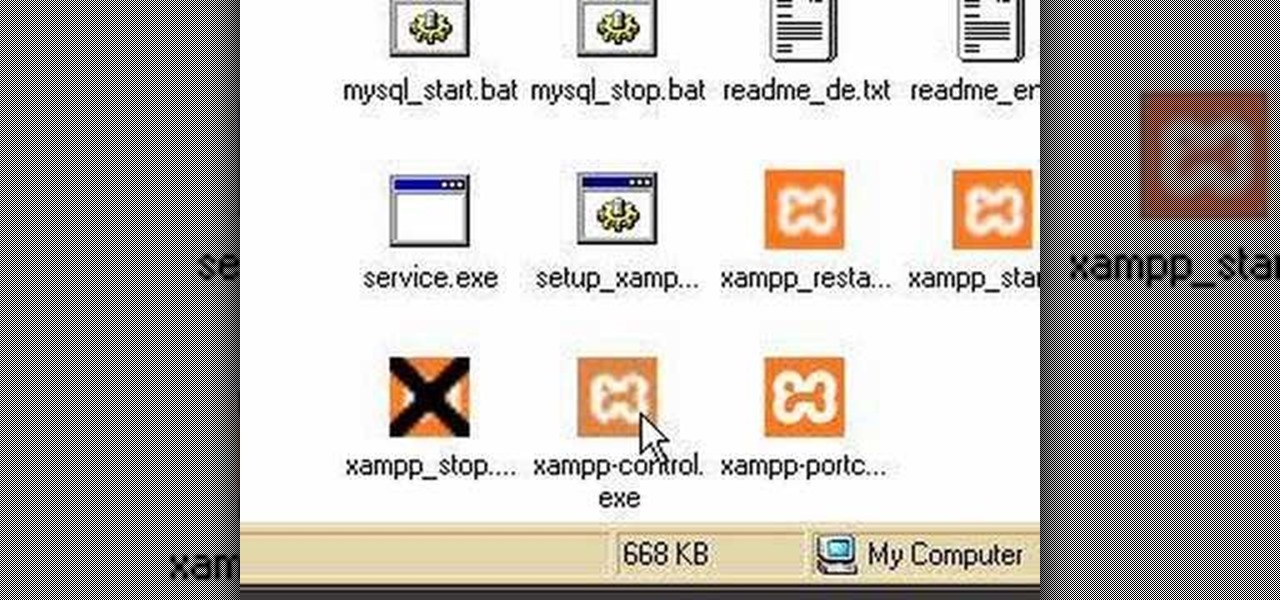
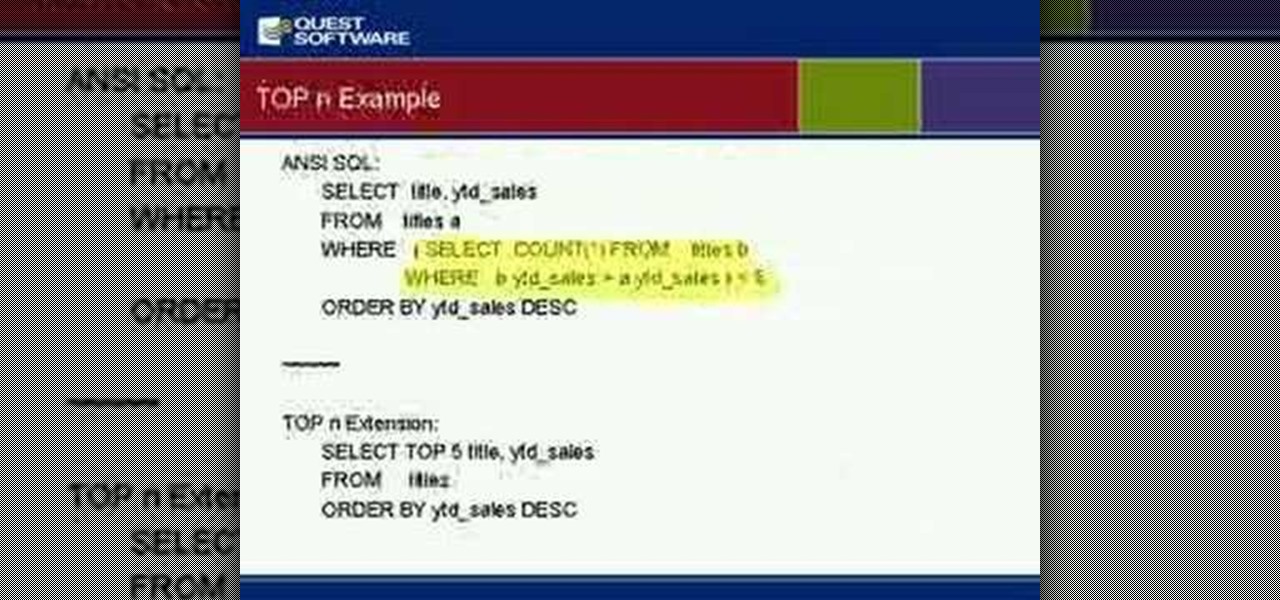
Using a simple peice of software XAMMP to streamline the setup process of apache+php+mysql
In this clip, you'll learn how to get started using Symantec Backup Exec to protect SharePoint & Exchange servers. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to get started using Sendmail's Sentrion messaging server. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

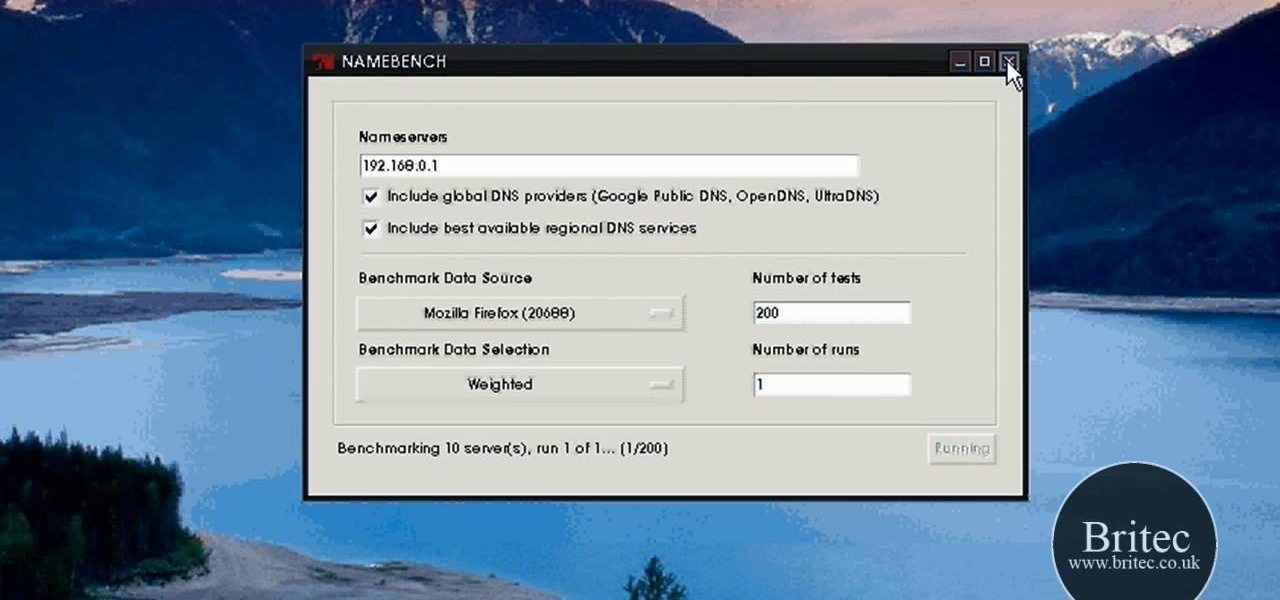
Looking for the easiest way to find the fastest DNS server for your PC? With NameBench, it's simple! So simple, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, watch this video guide.

Learn how to make an origami paper buffet server for kids. This origami animation is brief and to the point. If you are looking for a no frills origami tutorial, this video is for you! Learn how to make a cute origami napkin to hold your silverware.

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

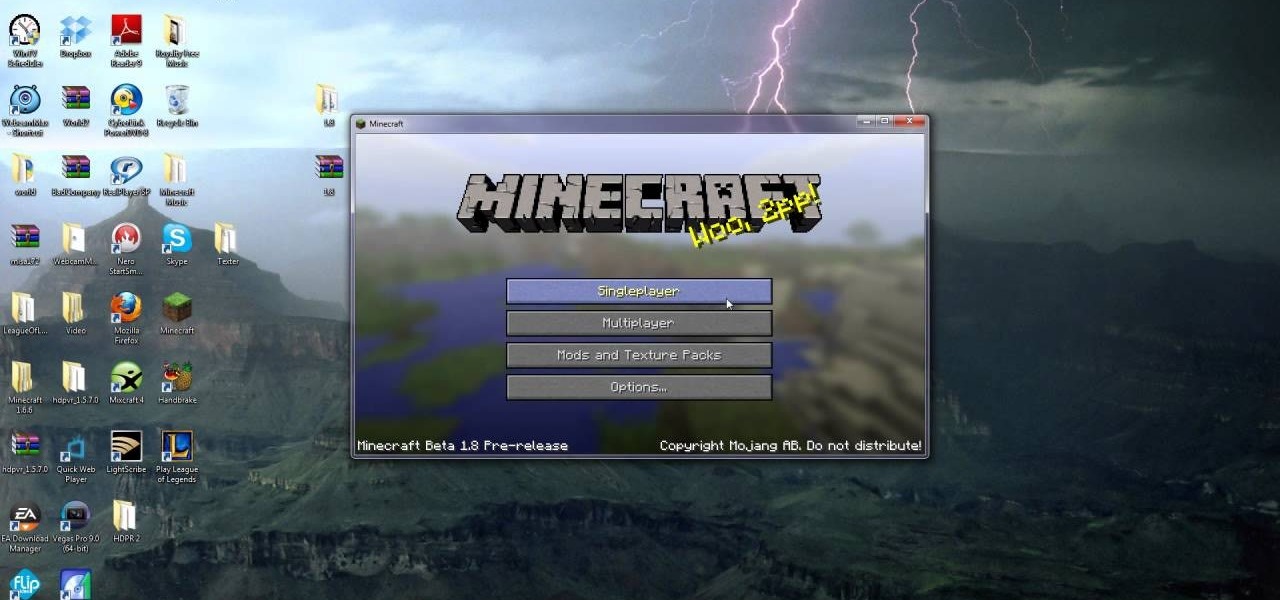
If you want to play the Minecraft 1.8 pre-release you can try it out on a test server. This guide shows you how to download and install the Minecraft 1.8 pre-release and try out the beta on a server before the official release comes out. It also details how to uninstall Minecraft 1.8 so that you can play Minecraft 1.7.3 instead if you have problems starting or playing the newer version.

Needing to load website content with AS2 into Flash? You've come to the right place. In the following video, learn how to load text from a text file sitting on a web server and display it in Flash using dynamic text and Actionscript 2.0. Also taught? How to load a jpg, gif, png, and/or swf file using Actionscript 2.0. All files loaded into the flash movie within this video will be loaded from an external web server.

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Hello again, ***UPDATE: Adding links to the other Two articles****

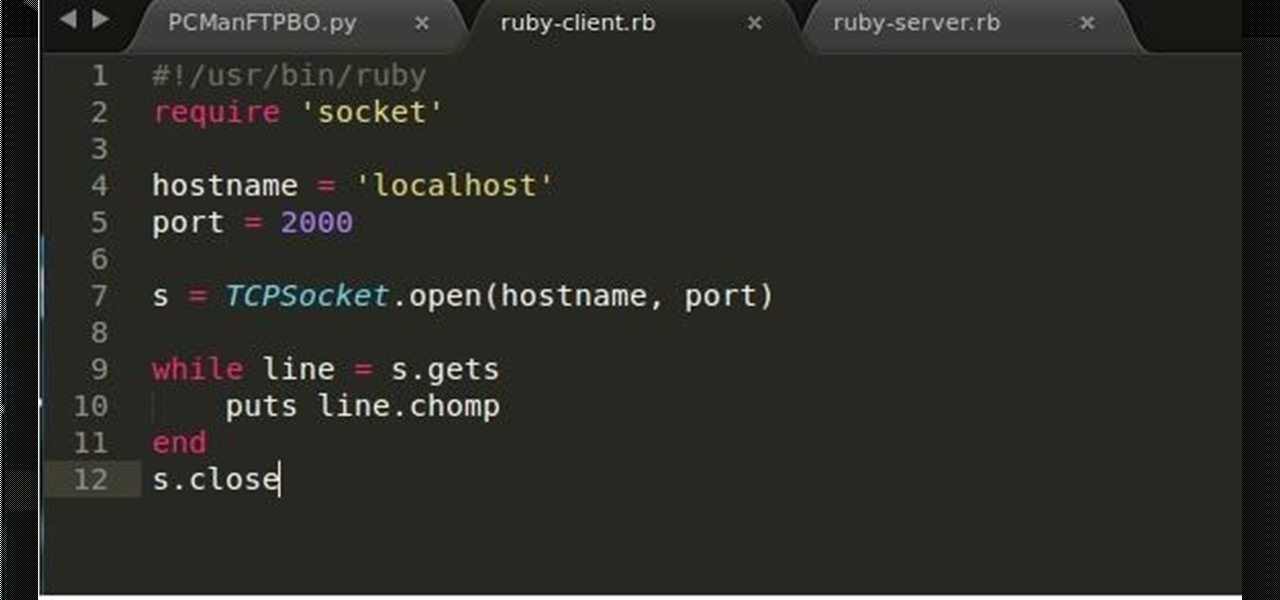
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Hey guys, today I bring you the fabulous BronzeSMP Server series! I hope you guys will enjoy this video as much as I enjoyed making it!

Welcome back, my greenhorn hackers!

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

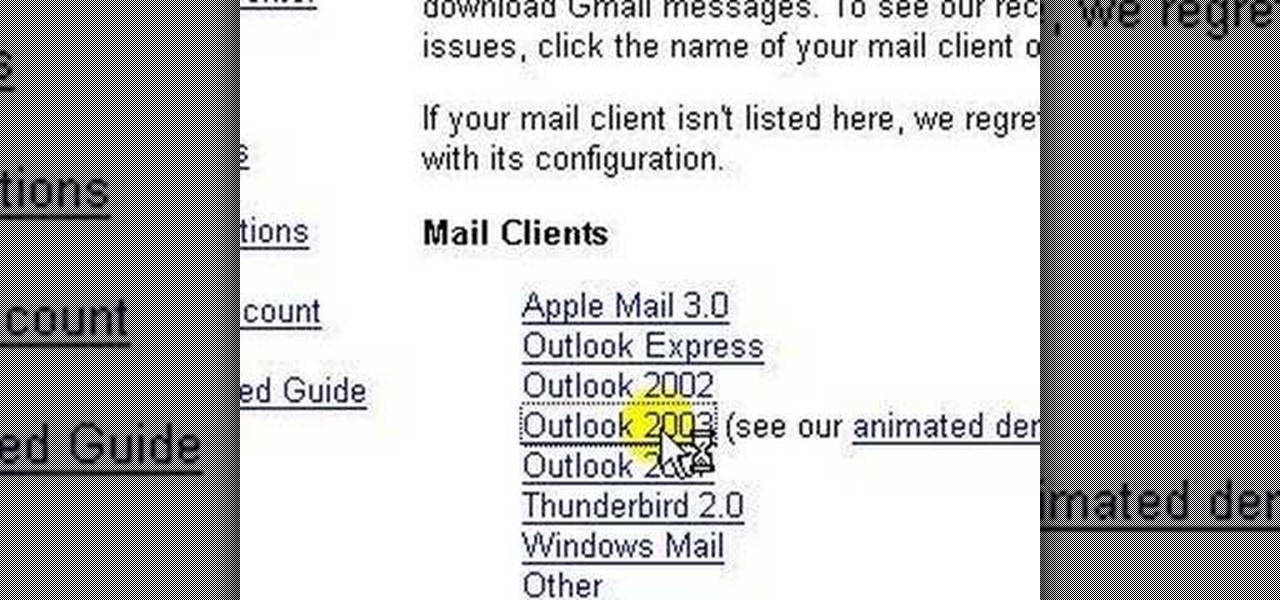
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

Hello everyone, In this video I will be going over what in my opinion are the top 10 bukkit plugins to make a great minecraft server. First thing I would like to state is that Essentials or commandbook was not featured in the video because I didn't want to feature something that big (or essential). I would also like to say it really does matter what kind of server you are going to be running becuase different types of server need different types of plugins.

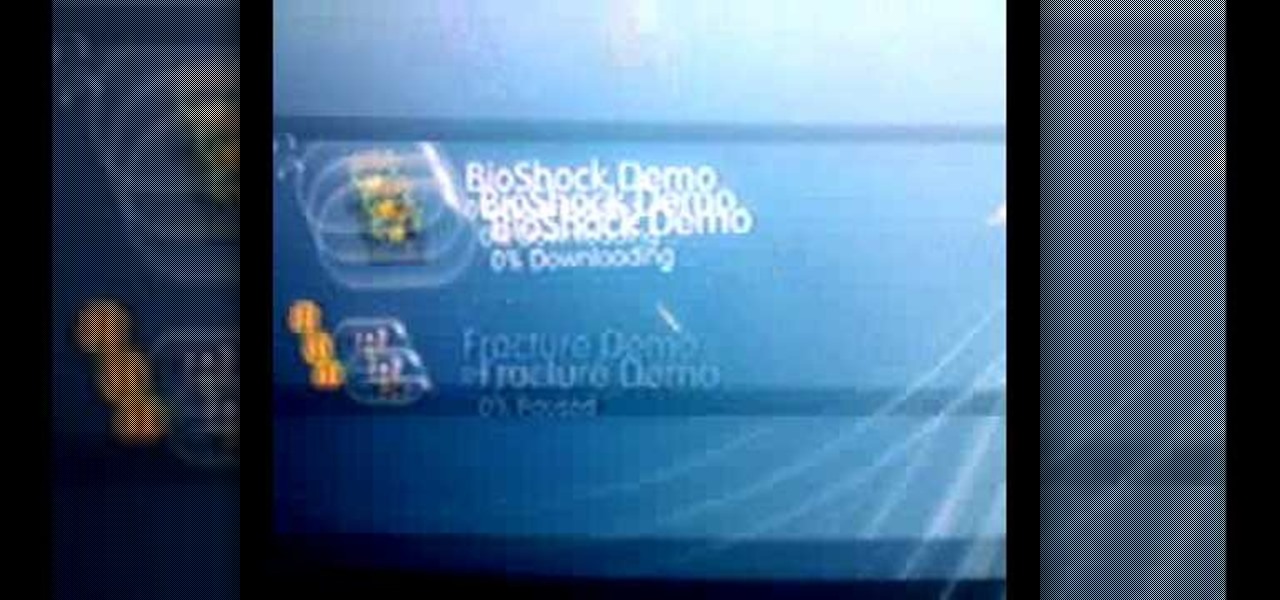
In this video we learn how to use a proxy server to hack PS3 store. First, go to settings and then internet settings. From here, go to the custom method and then click continue until you see the option for a proxy serve. Then, enable this with it and make sure all your connections are automatic. Then, your internet connection will be tested. When it's finished, test out the connection to see if it's working. Then, go to the PS3 store and you should be able to hack it using your proxy server. ...

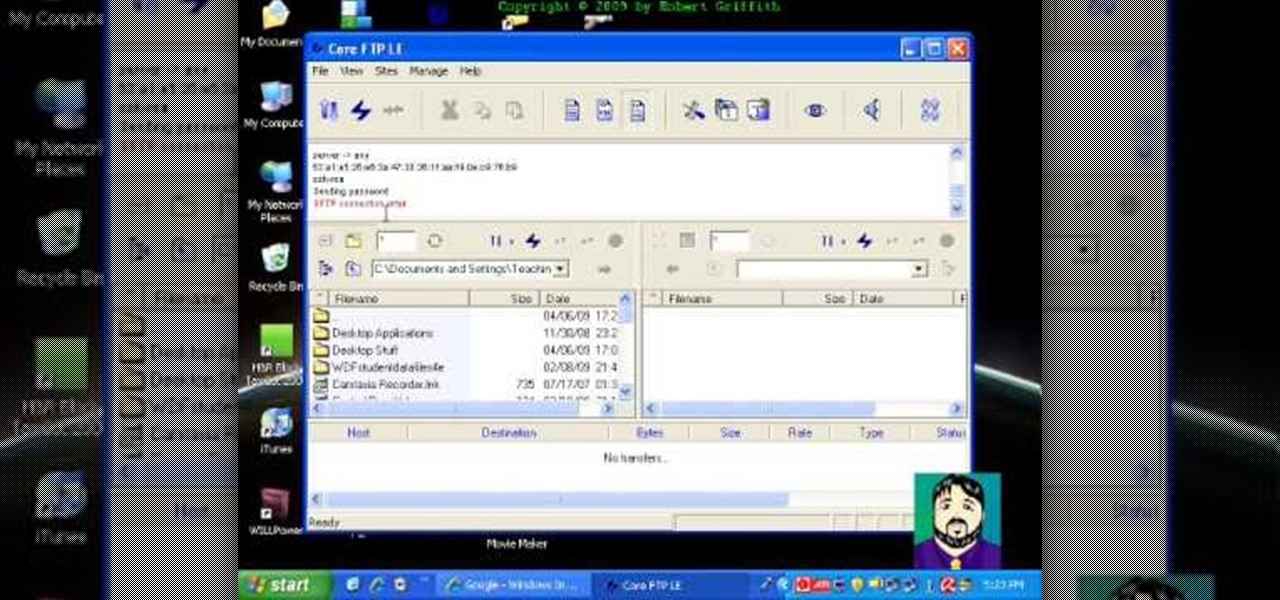
Select an FTP client that allows you to connect to the webserver. Download a free Core FTP Le software. Install the program. Use the site manager to name the internet site. Create a host/url, a user name, password and a connection. Connect to the web server. Create an index file to make files viewable. Open the Core FTP LE software. Drag files from the desktop (left side of the dialog box) to the internet server (right side of the dialog box.)

Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Still working on mega project builds. This one is going into my own PVP server which (will) contain 4 theme'd biomes inside of a 155m sphere - inside of a 255 meter containment sphere inside a 1000m+ void. The outer sphere acts as both artificial sunlight and a drop-death height of 50m. 4 more outer panels to go (water and lava) and it's ready for interior work and redstone - including command-block powered proximity traps that don't have any triggers marking them as well as hidden walls that...

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.