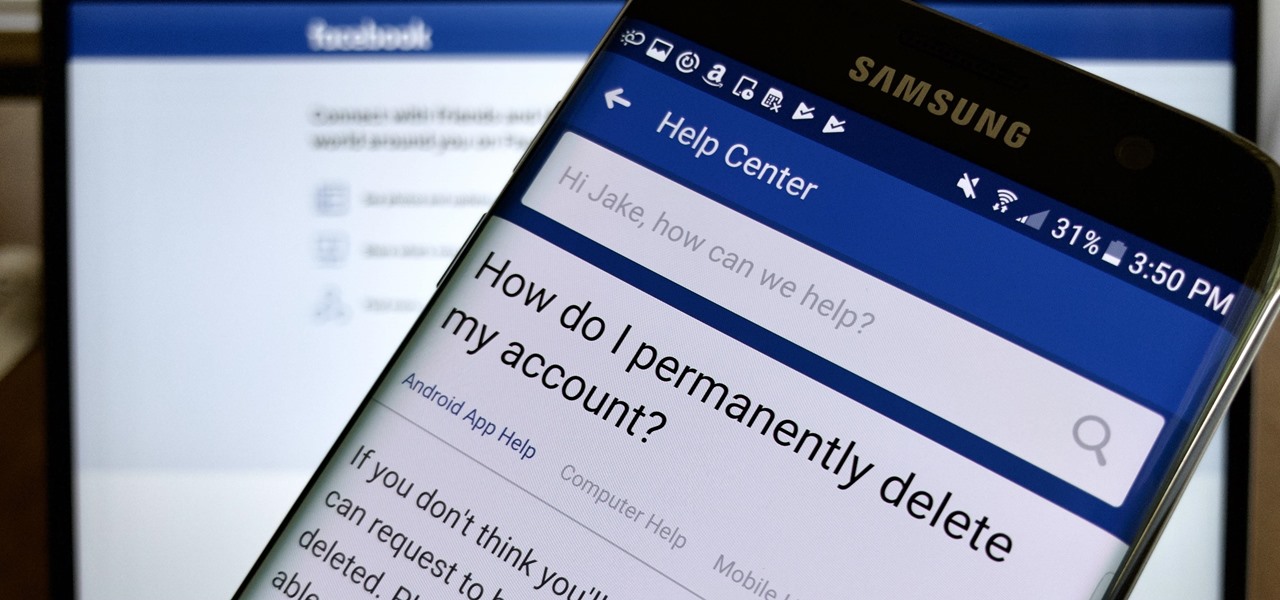
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

While TouchWiz as an Android skin isn't a favorite among many, Samsung Internet is a fantastic web browser that S9 owners should be happy to have preinstalled out of the box. But you don't need to buy Samsung's latest flagship to try their browser — Samsung Internet is available to all compatible Android phones.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

Not all microwaves are created equal, so when you use the recommended cooking time on any microwaveable meal, chances are you're actually cooking the food too much or not enough. And unless you're really good at mental math or have a virtual assistant that's smarter than Siri and Google, you have to do things the long way — but not with these helpful apps for iOS and Android.

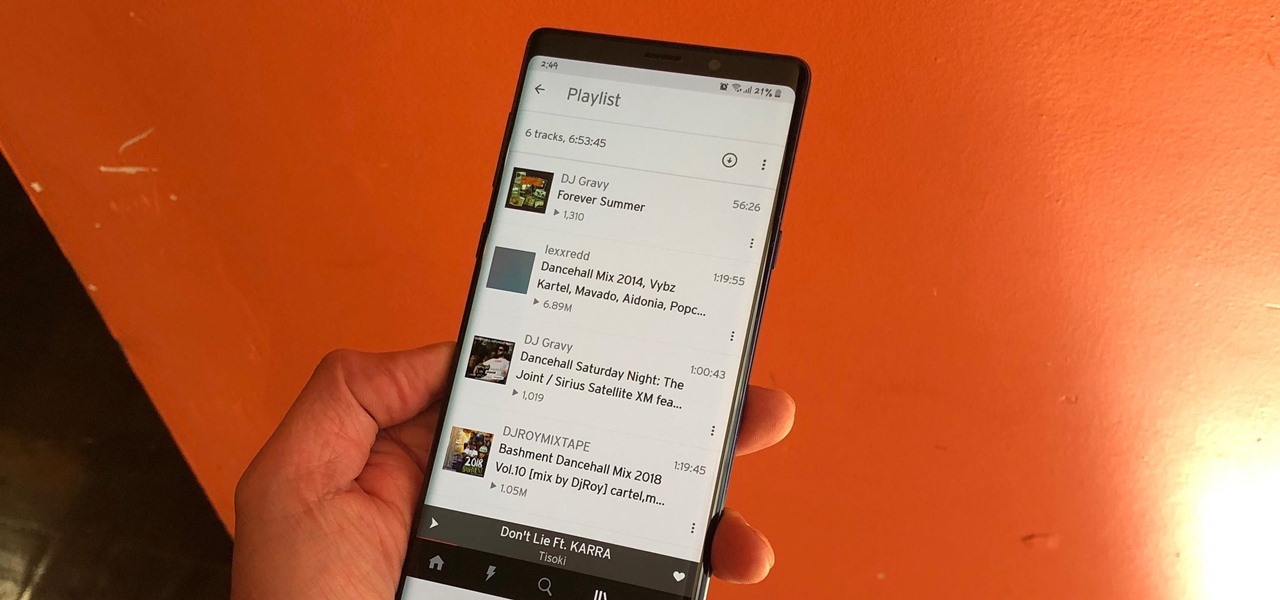
For those times when we need music grouped together for a specific task, we have playlists. Playlists are the next natural step after mastering your library and radio stations. While you've probably been an All-Star of curating playlists since your mid-90s mixtapes, Google Play Music has some pretty neat features that are going to really Smash your Mouth.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

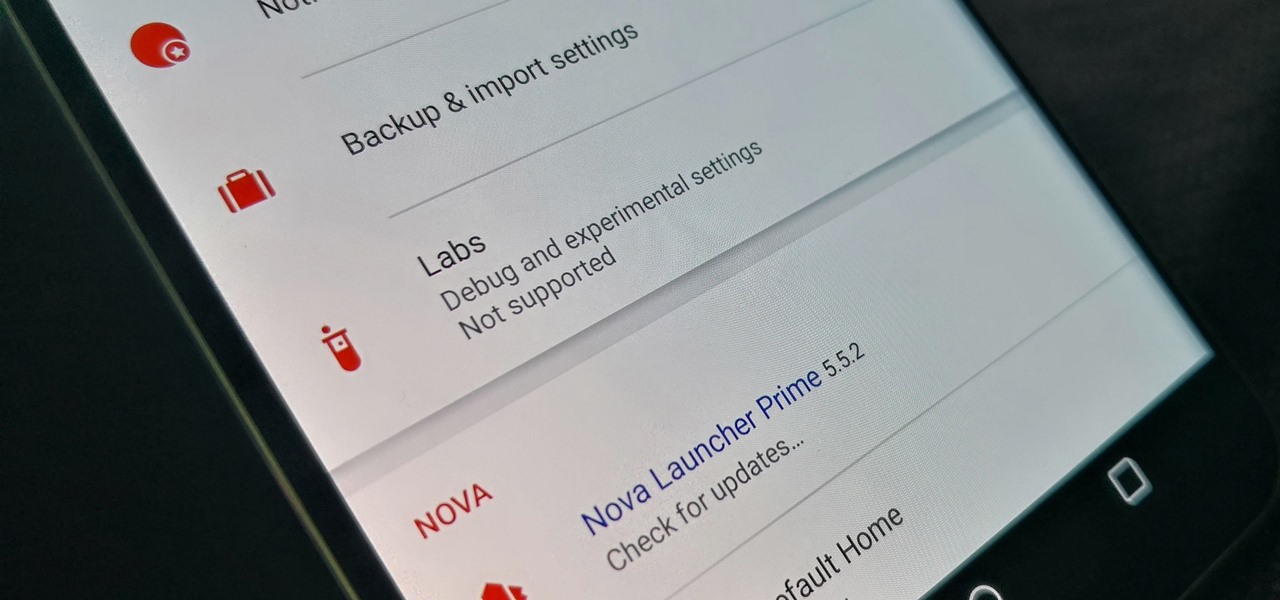
TeslaCoil's Nova Launcher is one of the best home screen apps on the Play Store. It's about as fast as it gets, and it's always among the first to add the latest Android features. However, it looks like Nova Launcher isn't showing users all of the customization options available — apparently, there's a secret menu, and it's pretty simple to unlock.

Google just rolled out a revolutionary feature to its Pixel devices — Google Lens. Previously, Lens had only been available in the Photos app, but now, whenever you want to learn about something in the real world, you can just bring up Google Assistant, turn on the camera, then let Google's famous AI analyze the scene.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Let's face it — our phones are our heart and soul. We do everything on them, from banking to media consumption. However, sometimes we download apps that we don't want others to see. Sometimes, we wish to hide apps so that, in the rare times we lend our phone to someone, we don't get judged for a lifetime by what they find.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The nice part about creating a song playlist is that it's essentially like your own customized album. You can organize all your different music tastes into one large collection or separate them into each of their own genres.

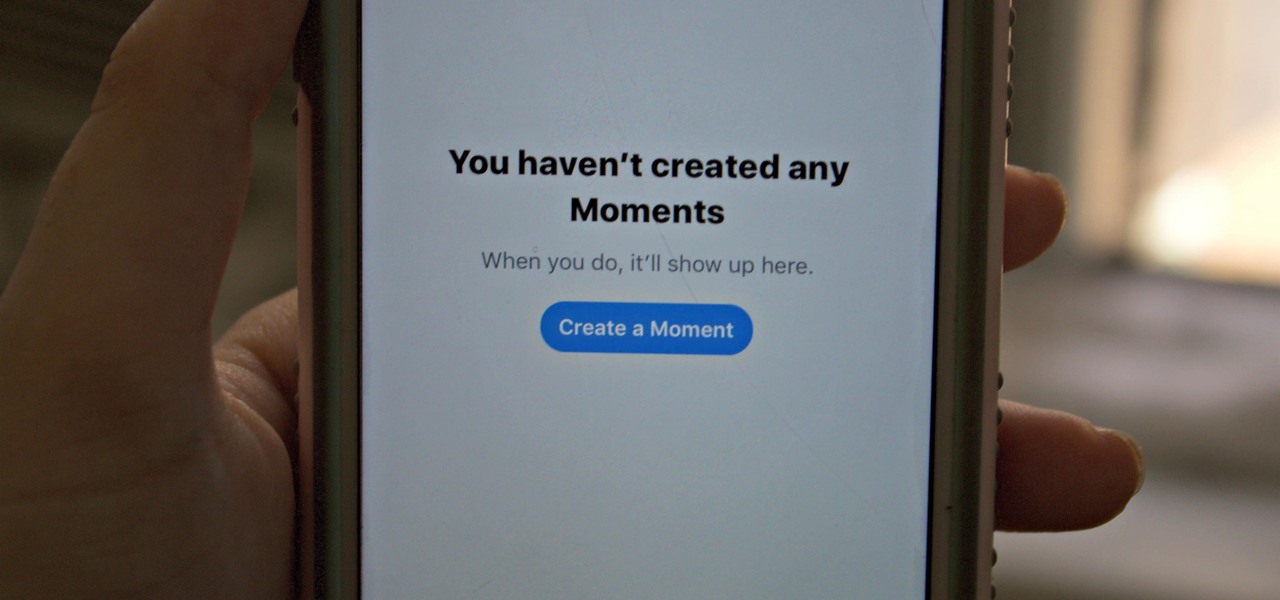
Twitter's Moments feature stitches together multiple tweets into a slideshow-esque story. This is particularly cool for you to keep up with major things that are happening in the world without having to follow and search for a ton of people to figure out the scoop.

Hashtags are one of the most important marketing tools available to you on Instagram. Although, it's hard to know which hashtags are working for you or not. You may think #fun is a good one to use but is it really? Okay, yeah, it's a popular one. But that doesn't mean it's the right one for you to use.

There are so many tips and tricks on how to improve your Instagram photos, but one really easy way is to use the HDR camera setting. HDR is high dynamic range imaging and takes three exposures of a photo — overexposed, underexposed, and one in the middle at the normal exposure. The end result is just one image of the three exposures combined.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Google has an exclusive launcher for its Pixel devices, and it's pretty slick. But even though we've found ways to get this home screen app on other phones, certain features simply wouldn't work unless you were rooted. That's finally changed.

Carrier-branded Galaxy S8 models come with a ton of bloatware that you usually can't get rid of without rooting. If you dig a little deeper, however, there is a way to debloat your S8, and it's relatively hassle-free.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, a post on Medium uncovered a group of scammers on the iOS App Store that are costing victims up to $400 a month.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

If you've ever wanted to turn your favorite GIF into a live wallpaper for your iPhone or even just make it a 3D Touch-friendly Live Photo that you can share, there's a super simple way to do so.

Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

Scientists are constantly on the search for new organisms, species, and other types of life. A special group of these researchers, calling themselves "bioprospectors," dive deep into mines to find unique lifeforms with special properties not found anywhere else.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

Google makes Android, but now, Google makes its own phones, too. Until this point, they've always stayed on the software side of things and let Samsung and friends handle the hardware, but their new Pixel phones are changing all of that.

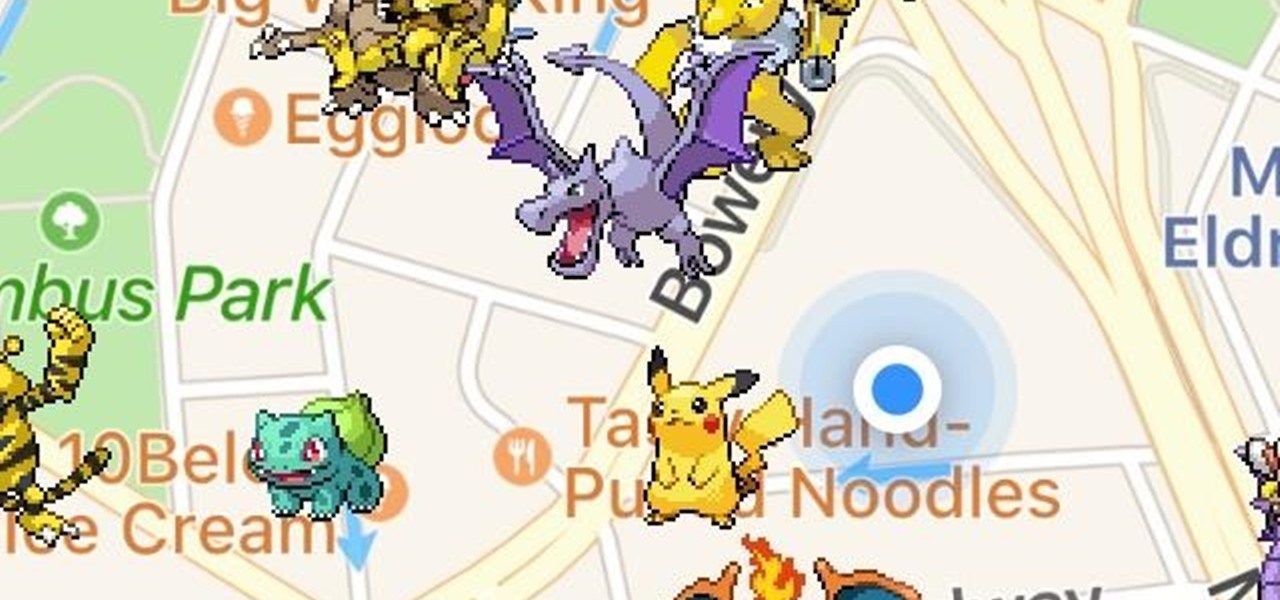
The only way to know which Pokémon are in your area in Pokémon GO is the cryptic "nearby" list, which sometimes doesn't work—and also doesn't tell you which direction to head off to hunt that Pokémon you're looking for.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

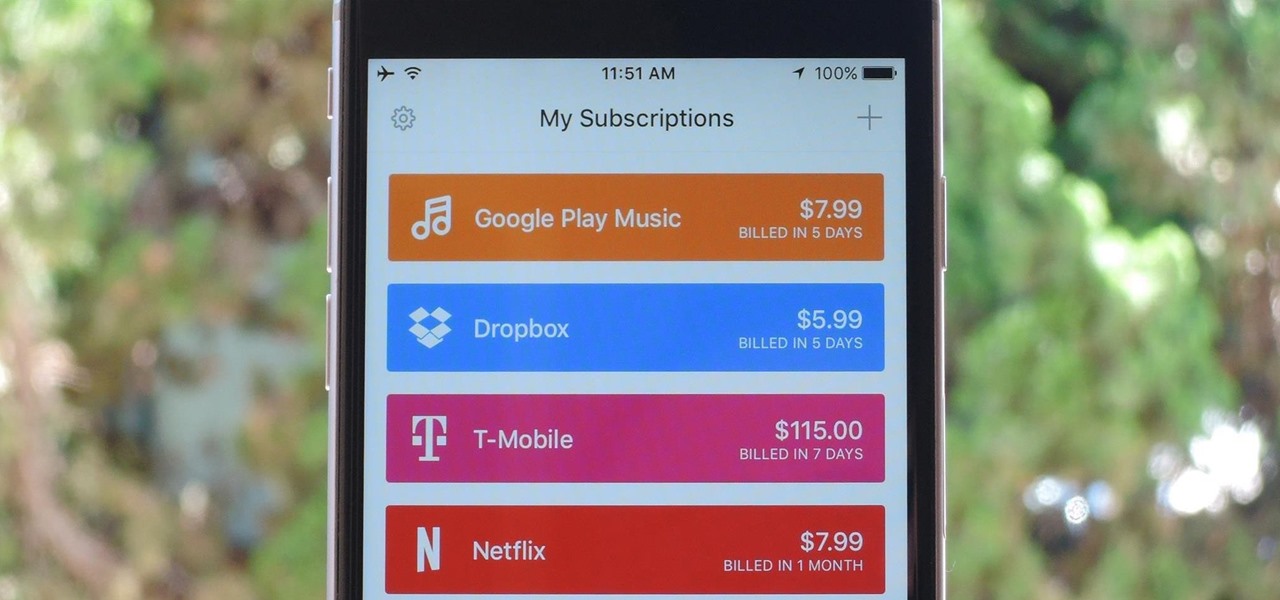
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

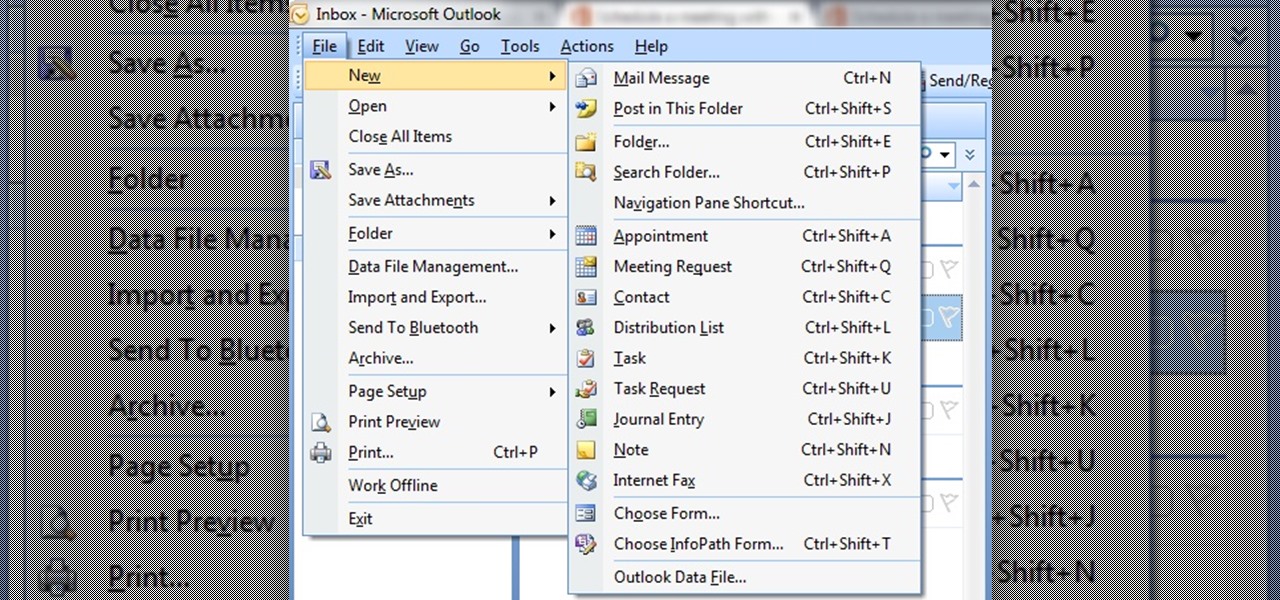
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

As one of the most popular home screen apps on Android, the Google Now Launcher is used by millions of people across the world. The two main reasons behind this success are its integrated Google Now home page and an elegant, easy-to-use design.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Because of Apple's iron grip over iOS, hiding stock applications is a topic we frequently like to cover. While not everyone may think that Apple's preinstalled iOS apps are bloatware, that's exactly what some of them are. For instance, the Apple Watch app; it's basically just an advertisement on your home screen unless you actually have an Apple Watch.