In this Software video tutorial you will learn how to mount an image using Daemon Tools Lite. This software takes many different types files and puts them on a virtual DVD drive. Go to www.daemon-tools.cc and download the Daemon Tools Lite program. You then install it. After that double click on the icon on your desktop and it will appear on the bottom right hand corner of the screen. It will say Daemon Tools and the version. Right click > virtual Cd/DVD ROM. To mount an image, click on ‘mo...

In this video tutorial, viewers learn how to convert .docx file format to a .doc file. Begin by downloading and saving the file to your desktop. Then open your internet browser and go to this link: Zamzar/]. In Step 1, click on Browse and locate the file that you want to convert. In Step 2, select .doc as the format that you want to convert the file to. In Step 3, type in your email address. In Step 4, click on Convert and wait for it to upload. Now open your email to find the sent converted ...
In this video, we learn how to delete hidden driver viruses. First, scan your computer with anti-virus and try to delete the virus that is harming your computer. If you have done this and your anti-virus can't delete it, download HijackThis from Trend Secure. Go through the download stages and install the new software. Now, open up HijackThis on your desktop. Once it's opened, open up the "misc tools" section. After this, click on "delete a file on reboot". Now, write the virus location name ...
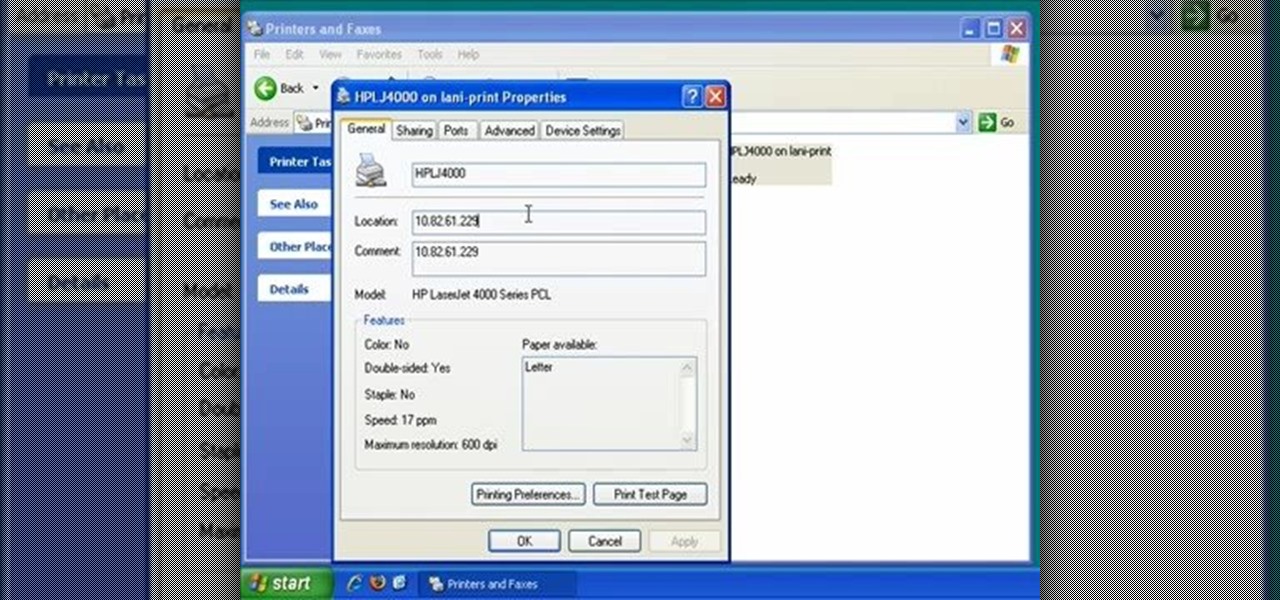
In this video, we learn how to find the IP address of a printer on your computer. Before you begin, make sure you start on your main desktop. First, click on the "start" menu, then click on "control panel" and last click on "printers and faxes". Once you're in there, right click on the printer you want to see the IP address for and then click on "properties". After this, you will find the IP address under the "location" section. You can look up the IP address for all the printers in your netw...
This is an instructional video on how to make a logo in "Inkscape". This video is filmed from the desktop of gamerworld14 and includes oral instructions as well as a step by step guide shown in detail from the computer. In this video gamerworld14 helps you learn by using an example logo he used. This video includes everything from adding text to your logo, pictures, and resizing of the images in the logo. In this paint style program you can draw out your own images to add to your logo. In the...

The Visual Prototyper is a wireframe design solution that allows you to design a fully functional application wireframe and simulate it.

Tutorial on how to create a shutdown shortcut on the desktop to shutdown the computer when clicked. shutdown -s -t 1000 -c "comment"

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

The coronavirus pandemic has ushered in an unprecedented time in modern history where terms like "social distancing" and "self-quarantine" have pushed their way into the zeitgeist.

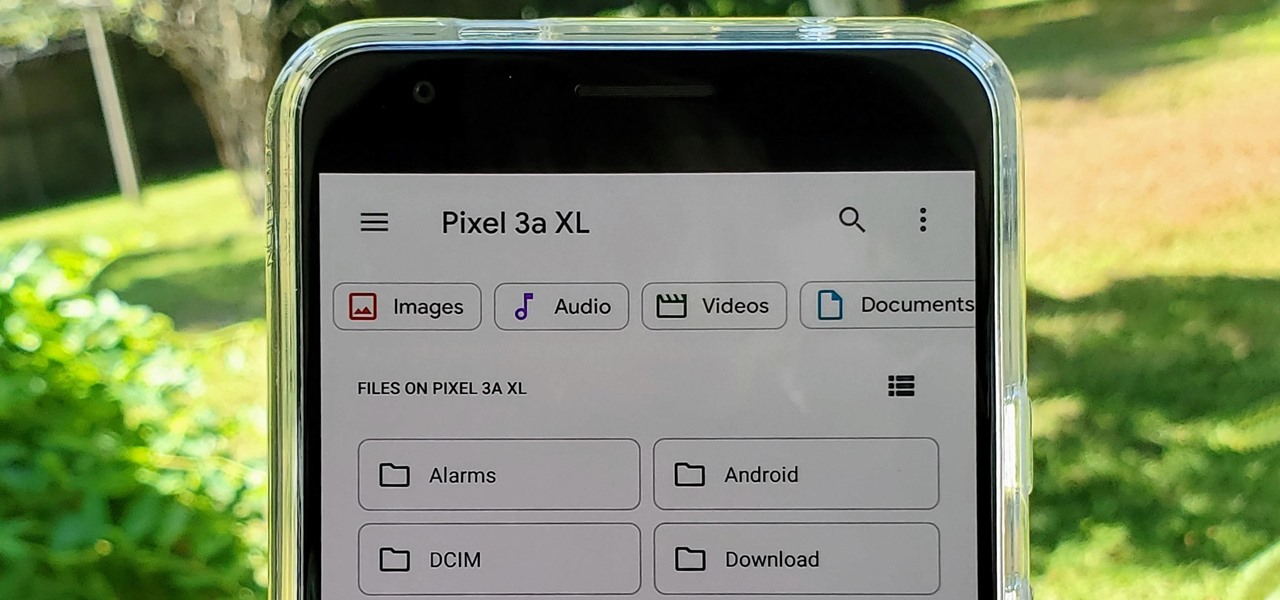
With the files on our devices getting more important as the years go by, the need to keep things organized continues to rise. The longer you have a device, the messier the internal storage might become. Having a file manager would be extremely useful in this situation. You could also reorganize the folder structure as well, just like you could on a desktop computer.

Just weeks after revealing plans to port one of its most vital augmented reality products from HoloLens to the smartphone world, Microsoft has finally opened the mobile software floodgates to the public.

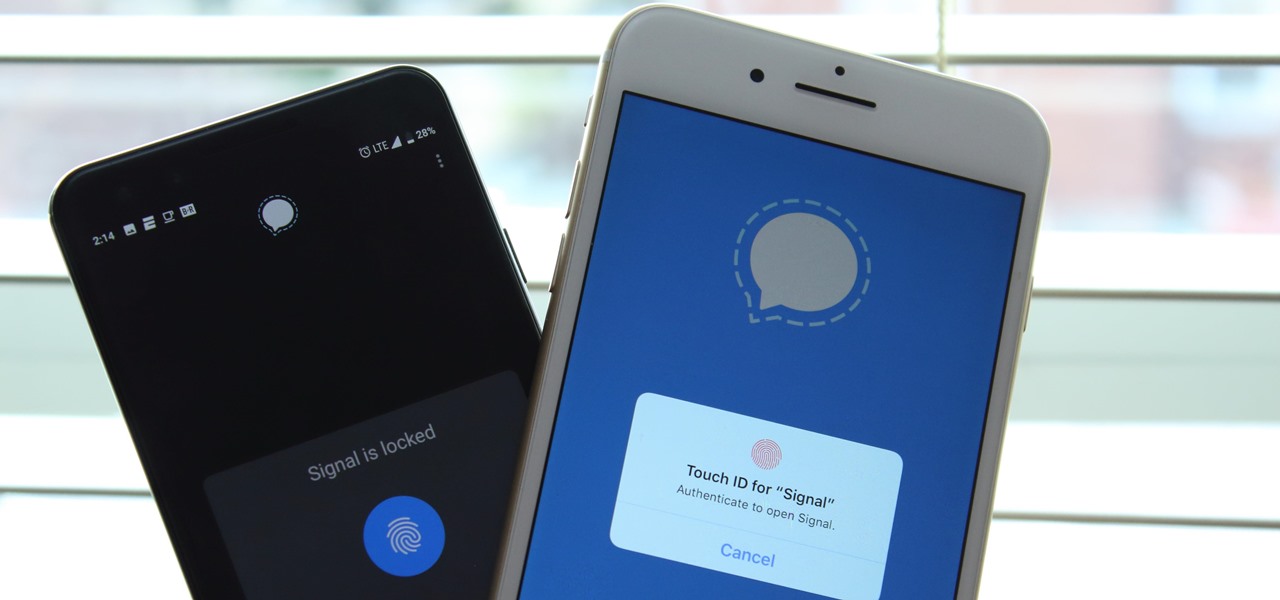
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

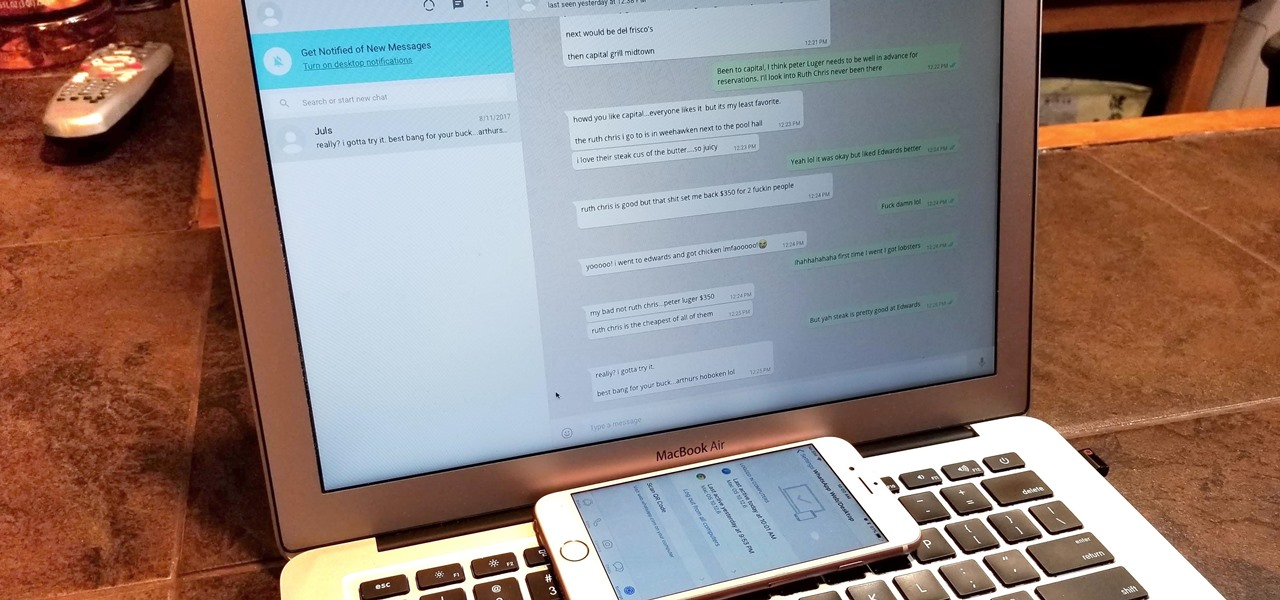
Typos are a constant annoyance that we all deal with thanks to the cramped touchscreen keyboards on smartphones. For many, nothing beats the feel of a good old physical keyboard when it comes to typing fast with minimal errors. Fortunately, WhatsApp has an awesome feature which lets you use their messaging service right on your computer.

Mobile augmented reality developer Blippar has escalated the augmented reality advertising arms race, introducing a new rich media ad format that enables augmented reality experiences without a dedicated app.

Mixed reality headsets have limited hardware capabilities and naturally imprecise interfaces. While that works just fine for games and entertainment, can they actually function as a tool for productivity?

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

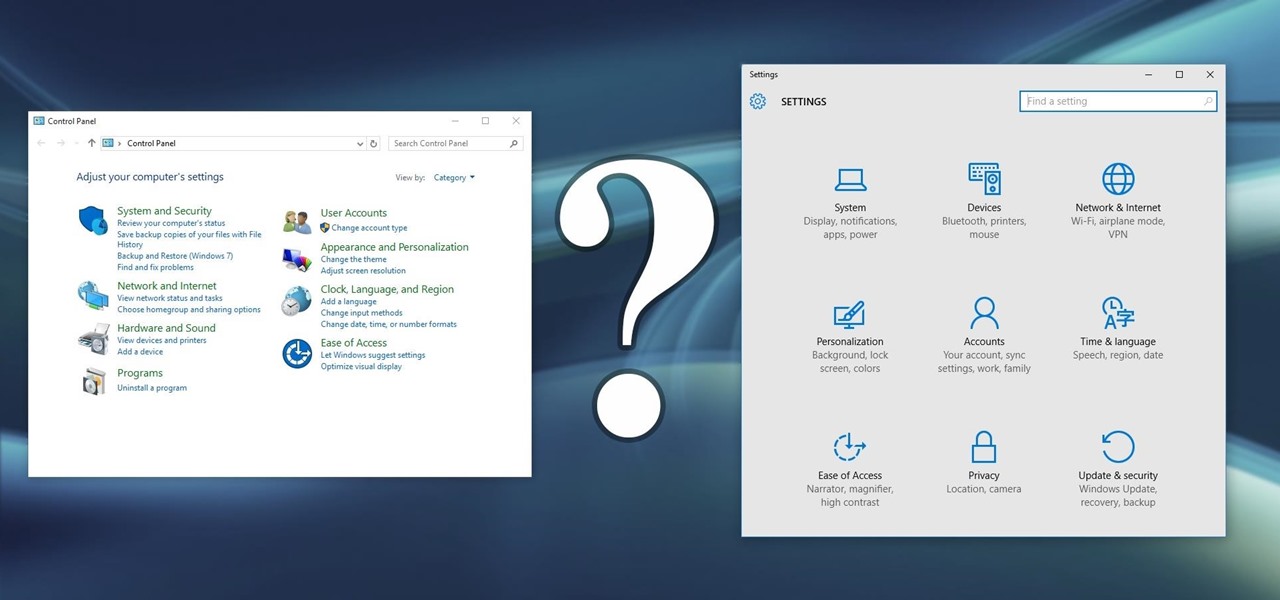
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up.

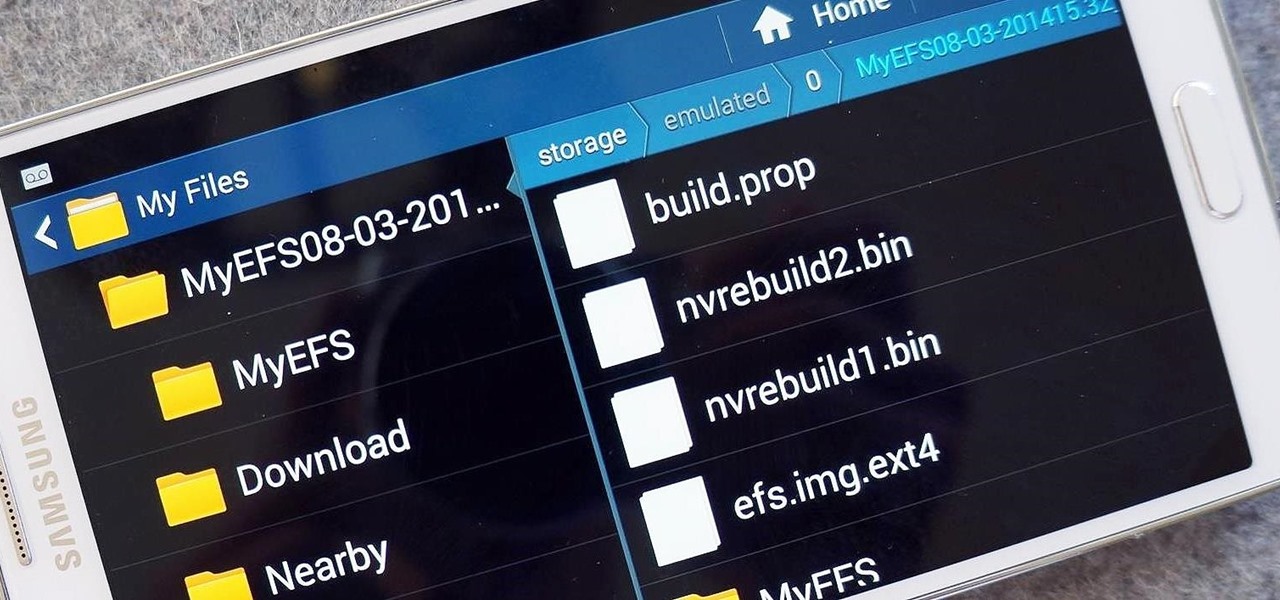
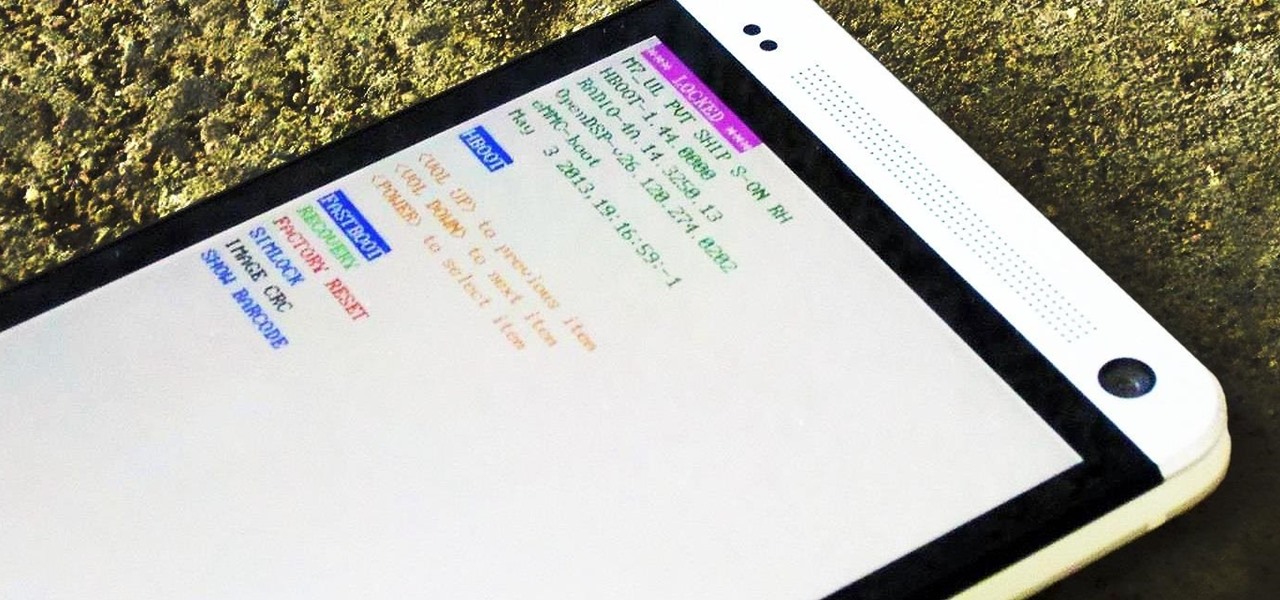
The options for customization are virtually endless when you're rooted and have an unlocked bootloader and custom recovery. However, there is always risk involved when flashing new mods or installing new ROMs. I always make backups in case something happens, but when I'm testing certain mods out, I sometimes get a damaged EFS partition.

Amazon's Fire TV set-top box has been out for over a month now, and the hacks are starting to come together. Sure you can play your Amazon Instant Video, Hulu, and Netflix content without any issue, but what about your personal media, like movies and music?

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang for your buck, here are a few ways you can hack your own Nook.

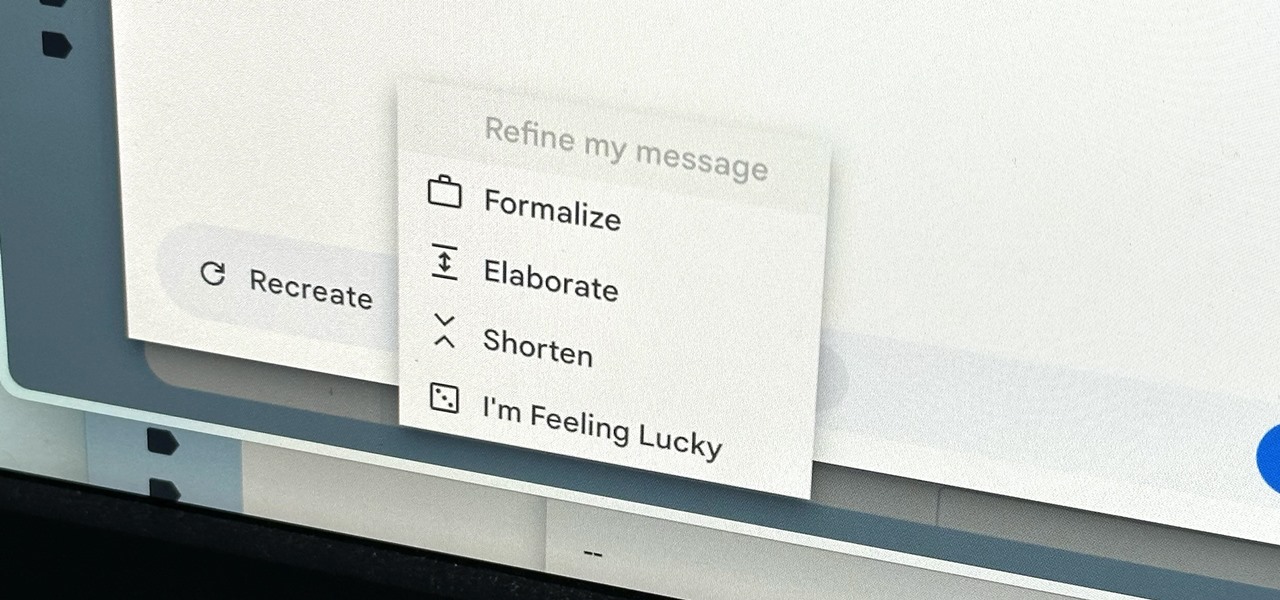
Thanks to rapid advancements in the field, generative AI can do some amazing things already, from generating text, images, and video with just a prompt to automating tasks and developing new products and services. Now, artificial intelligence can even help you craft emails directly in Gmail.

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

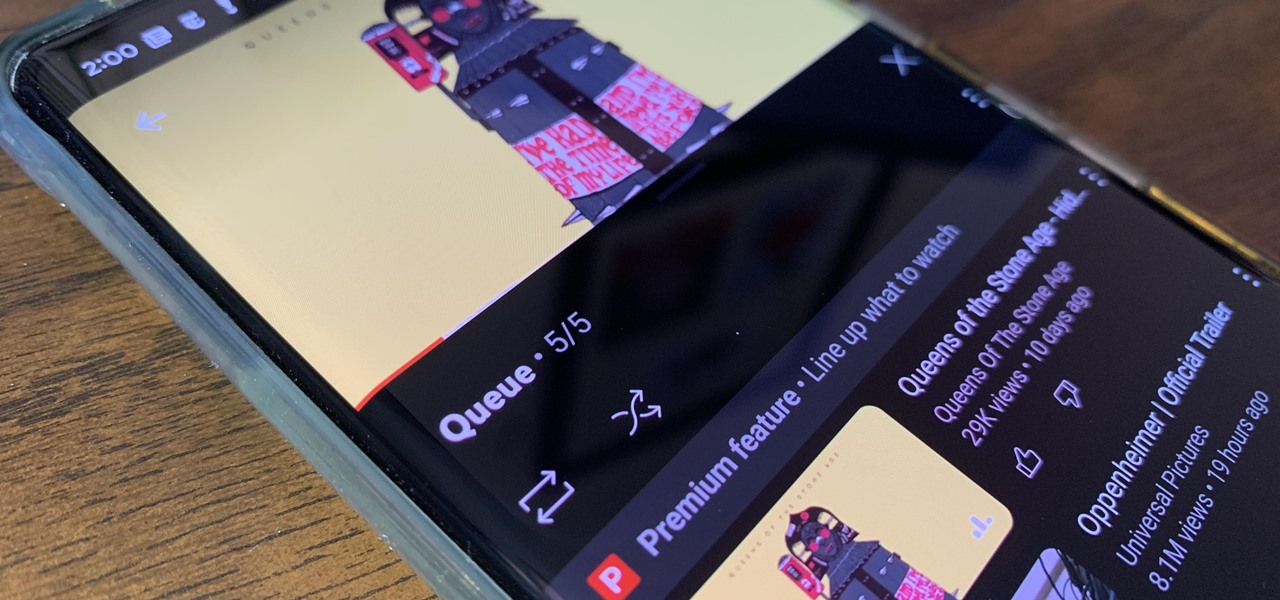
YouTube has offered viewers a video queue on desktop browsers for some time, and the world's most popular video site is preparing to finally bring the queue feature to its Android and iOS mobile apps.

When it comes to finding the exact moment you want to see in a video, the seeking function can be hit or miss depending on the streaming service you're using. On YouTube, though, it just got much better.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.