Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Does executing a perfectly timed, no-scoped headshot, followed by a well-choreographed teabagging ever get old? No, no it doesn't, and neither do custom emblems for Call of Duty: Black Ops 2. How else are we going to kill time until Black Ops 3 arrives?

Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which multiplayer games are worth your time on Android or iOS?

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

Use Cheat Engine to hack into the popular Bouncing Balls game. It's as easy as that. It's not too hard to use Cheat Engine if you've never before, then… flash game hacking everywhere!

How much time have you wasted, wandering around your home trying to find one particular book? Without a good system of organization, finding the book you're looking for can become a hopeless task. Organize your book collection at home by following this tutorial.

Nobody likes it when a prank gets taken too far. Friendships are ruined, material possessions destroyed, even bodies broken. This video offers four perfect examples of pranks that go entirely too far and that you SHOULD NOT DO to your friends and neighbors. We're being serious, if only for a second. They involve killing your cat, possibly killing your friends, and erasing all of the computer data of your friends and family. Actually doing any or all of these things will probably lead to your ...

Forget Christmas, it's all about Festivus these days. But what is Festivus? When is Festivus?

Every summer my husband and I plant a tomato plant. We do this to enjoy the plump red tomatoes right off of the vine.

Killstreaks: Advantages and Disadvantages 3 Kills – Spy Plane: Advantages: This lets you see enemies on the radar in the upper left hand part of your screen. Though it is one of the lowest killstreaks, it is very beneficial and gives you a huge advantage. Disadvantages: It can be shot down and it will not detect enemies who use the ghost perk.

Criminal “Expungement” is the process of going to court to ask a Judge to seal a criminal record. When a record is sealed, it does not show up in a criminal background check. It is important to remember that a sealed record is not destroyed. The police, immigration authorities, and other public officials may still see sealed court files for certain purposes.

Synopsis: Tell one guy that a girl that one of the other guys knows just had some sketchy demonic encounter/satanic experience at some Wicca gathering she went to last night while she was trying to get answers from the past. Then say she’s incredibly creeped out right now and is home alone tonight so they are going to seize the opportunity(while she’s still scared) and have him dress up as Satan himself and go to her house late at night and “appear” to her in her bedroom. (Don’t be overly des...
The US judge handling the Megaupload case noted today that it may never be tried due to a procedural error, a comment that has sparked the anger of Megaupload’s founder. Kim Dotcom is furious with the US Government for destroying his businesses and rendering hundreds of people unemployed. According to Dotcom the case is the result of “corruption on the highest political level, serving the interests of the copyright extremists in Hollywood.”

UK Independence party leader Nigel Farge says Greece will be destroyed if she does not leave the Eurozone

Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotgun, Gamespy, The Verge, Joystiq and many more websites!Exciting!You can see the full details below are head straight here for the downloads.

Amazing animation by Patrick Jean. NYC is destroyed by 8-bit evil forces from 70s and 80s video games such as Space Invaders, Pacman and Donkey Kong.

Here's today's morning news: Rising Gas prices: The United States has seen a big inflation in gas prices throughout the nation. Many stations in New York have hit $4 per gallon, while Hawaii sells at $4.247. Experts predict another increase before memorial day. When will you reach your gas limit? Seen any outrageous gas prices?
I'm new here, but wanted to add formufit to the list of links on your cork board. They are solely sellers of structural PVC items, used to build greenhouses and such. I am currently building some outdoor PVC furniture as the weather here in Missouri has destroyed our previous 'durable store bought' furniture. I saw some other resources on here, but I just bought a slew of products from formufit.com and I thought I would share. I will post some photos of the completed furniture soon.

MGMT, more commonly and colloquially referred to as "Management," broke into the indie music scene with their 2008 debut album Oracular Spectacular. The most popular song on that album is "Electric Feel" — the original music video is often considered to be an acid trip. Some even think it's a depiction of Sodom and Gomorrah, the two cities destroyed by God. Check out the original music video for "Electric Feel" below.

The last tree on earth The world looks new today.

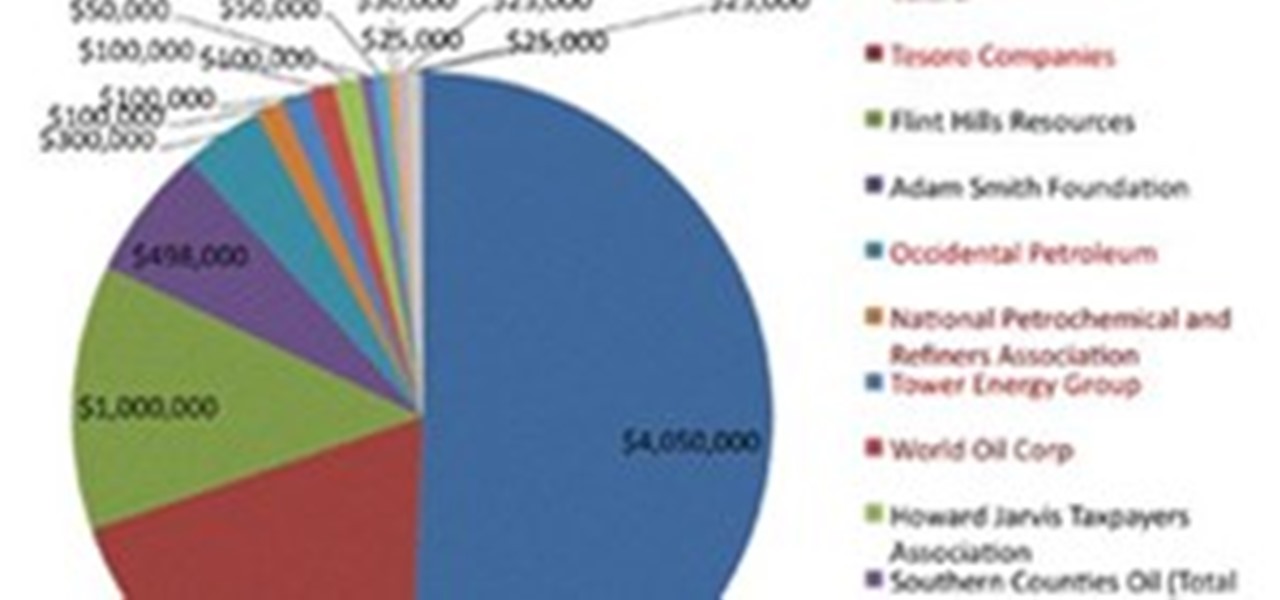
Proposition 23 is the act where they would suspend AB 32, the global warming act of 2006. If proposition 23 is enacted by voter this would pause the porvision of AB 32 until California's unemployment rate drops to a 5.5%. The unemployment rate at this current point is as high as a 12% and has been like that for the exception of 3 times since 1980. supporters call it California Job Anitiative and opponents call it the Dirty Energy Proposition.In this article it states the reason proposition 23...

A radical art group of Russian political pranksters, who go by the name of Voina, have delivered a giant "Up Yours!" to the Russian government... in the form of a 213-foot-tall penis.

It's no secret that Jimmy Kimmel is a SCRABBLE man. He hosted and won the SCRABBLE 60th Anniversary Celebrity Doubles Tournament (SCRABBLE Under the Stars), and for the last couple of years, featured the National School SCRABBLE Champs on his late night show "Jimmy Kimmel Live!".

Store bought Nerf guns don't always achieve the velocity necessary for an effective assault. Zach Scott's solution: mod the toy. Known for his fantastic cat videos, Zach claims this hack increases trajectory by at least 25%! Every bit counts when you're in an all out foam war.

Mitt Romney has been on a winning streak recently, with small breaks by Rick Santorum. Ron Paul is slowly coming in third, but it's hard to say he's making a dent in those who support the top two contenders. Newt Gingrich has gone down, down to the bottom. He's still fighting to make another break in the race.

1/3 of the city gone, the red colored buildings and homes are the ones that got destructed in the fire..

Del The Funky Homosapien ft. Khaos Unique "Proto Culture" Chorus:] Let me tell you about the Proto Culture