Green eye makeup, as shown in this how-to video, is very complimentary to brown eyes. The cosmetics used to create this look are MAC Liner - Teddy, MAC EyeShadows - Juxt, Humid, Juiced, Milani Liner - Golden Eye, NYX EyeShadow - Sahara, Urban Decay EyeShadows - Graffiti, Shag, Maybelline Define-A-Lash (pink bottle) - Very black, Max Factor 2000 Calorie - Black, MAC - Feeling beauty powder, Revlon Colorstay liquid - Caramel, Posner Coverstick - light/med, Revlon Colorstay Concealer - Deep, Mac...

Learn how to apply a makeup look inspired by Keira Knightley from the premier of Pirates of the Carribean: Dead Man's Chest. The products used for this look are Dark Brown Shadow (the palette's so old, the name's rubbed off... any dark brown shadow will do), Gold Shadow from the Profound Palette, Champagne Shadow from the Profound Palette, Maybelline Define-A-Line eyeliner in Ebony, MAX Factor Volume Couture Waterproof Mascara in Rich Black, Sonia Kashuk blush in Royal Rush, and Covergirl Lip...

China-based virtual reality headset maker ANTVR has decided to enter the augmented reality space, and to do so it's launching its headset on Kickstarter. The company claims that its new Mix AR device has a field of view that surpasses the Meta 2, the HoloLens, and others within a smaller form factor and at a fraction of the price. But there's a catch.

When the climate changes, so do all the things that rely on the climate, including people, plants, and pathogens. A European study recently took a broad look at what kind of microorganisms are most likely to be affected as climate change heats, cools, dries, and wets the world around us.

Building virtual portals are popular practice for developers to demonstrate the "wow" factor of augmented reality.

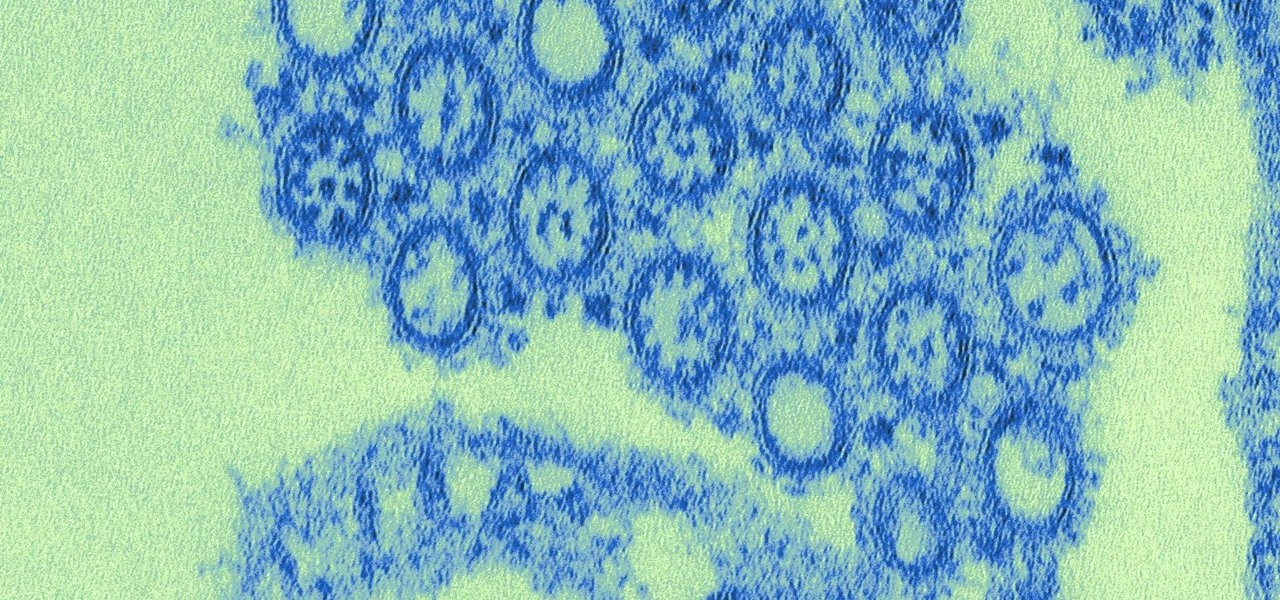
New research explores how the bacteria on the penis can leave men more susceptible to infection with HIV.

Growing evidence suggests that neurodegenerative diseases like Parkinson's may develop in part due to environmental factors, including infections that can cause inflammation in the nervous system. New research from investigators from Jude Children's Research Hospital and Thomas Jefferson University has strengthened that connection.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

For regions that experienced a boom in mouse populations last year, scientists say 2017 could see a surge in cases of Lyme disease.

We all know you are what you eat—or so the expression goes—but it's good to remember that what you are (at least intestinally) is mainly bacteria. A new study has shown that what you eat, and how your gut microbiome reacts to that food, might be a key player in your risk of developing a certain type of colon cancer—and changing your diet can help decrease your risk.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

The guys over at SamMobile were lucky enough to get their hands on an early preview build of Android 5.0 Lollipop on the Samsung Galaxy S5, as you can see in their video below. The operating system has definitely not reached its final form yet, but the progress is very clear.

Lenovo didn't have as much to show off at IFA 2014 as Samsung and Sony did, but its new Android-powered Tab S8 is certainly worth a look.

Samsung has shown off its new smartwatch, the Gear S, and its two new Notes, the Note 4 and the Note Edge at IFA 2014, but it had one more trick up its sleeve.

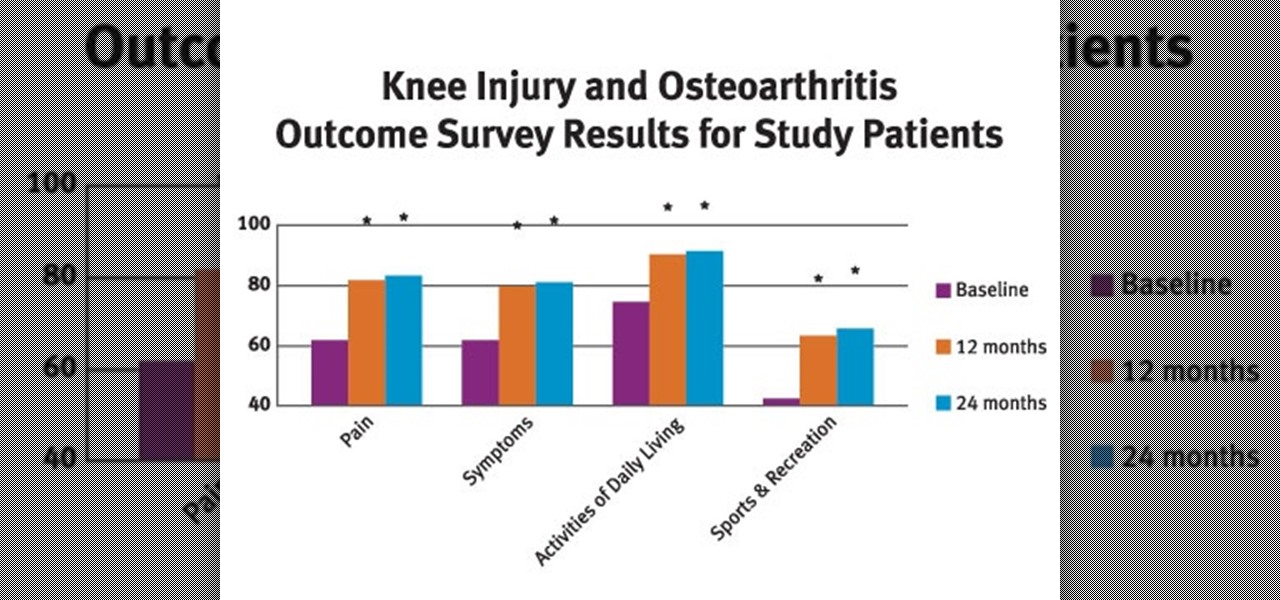
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

Can't decide between the Galaxy S4 or the Galaxy Note 2? There are advantages to both the Galaxy S4 or the Note 2, it all boils down to what your needs are such as screen size, battery life, and more.

We'll show you how to use an attachment for a power washer called a "Foamer" - you'll never hand wash a car or boat again!

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

Smartglasses and AR headset makers like Microsoft, Magic Leap, and Google (and aspiring AR wearables makers like Apple and Snapchat) need display components for their products, and LetinAR is among the companies ready to supply those components.

Smartglasses maker ThirdEye has announced that its X1 model wearable will be updated by the slimmer, as yet unreleased X2 model. Both devices will be promoted and sold through its partner, brick and mortar technology retailer b8ta.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

On Thursday, waveguide maker WaveOptics announced that semiconductor and microelectromechanical systems supplier EV Group (EVG) will provide the manufacturing infrastructure for the production of its waveguide displays designed to support lower-cost, third-party augmented reality wearables.

While Apple usually sets the precedent for its consumers to follow, the iPhone SE returned the company's iconic smartphone to a small form factor, one that had been ditched by the iPhone 6 and beyond. However, it appears Apple is finished with 4-inch phones for good, as the iPhone SE 2 looks to be even larger than last year's iPhone X.

Amidst reports of the newspaper industry struggling to survive, it's becoming more and more clear that people are increasingly turning to their smartphones for the news. In fact, a new study by the Pew Research Center has found that 85% of US adults check the news on mobile devices. Surprisingly, seniors constitute a sizable portion of this.

Lens Launcher was one of the winners of 2106's Android Experiments I/O Challenge a few months ago, and with good reason—it gives us a new way to browse for apps on our Android phones. It's slightly reminiscent of how the Apple Watch does it, but even better.

With a price that undercuts flagship devices like the iPhone 6s and Galaxy S7 by hundreds of dollars and a smaller size, new tests show that the iPhone SE incredibly packs just as much power as its bigger brother.

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

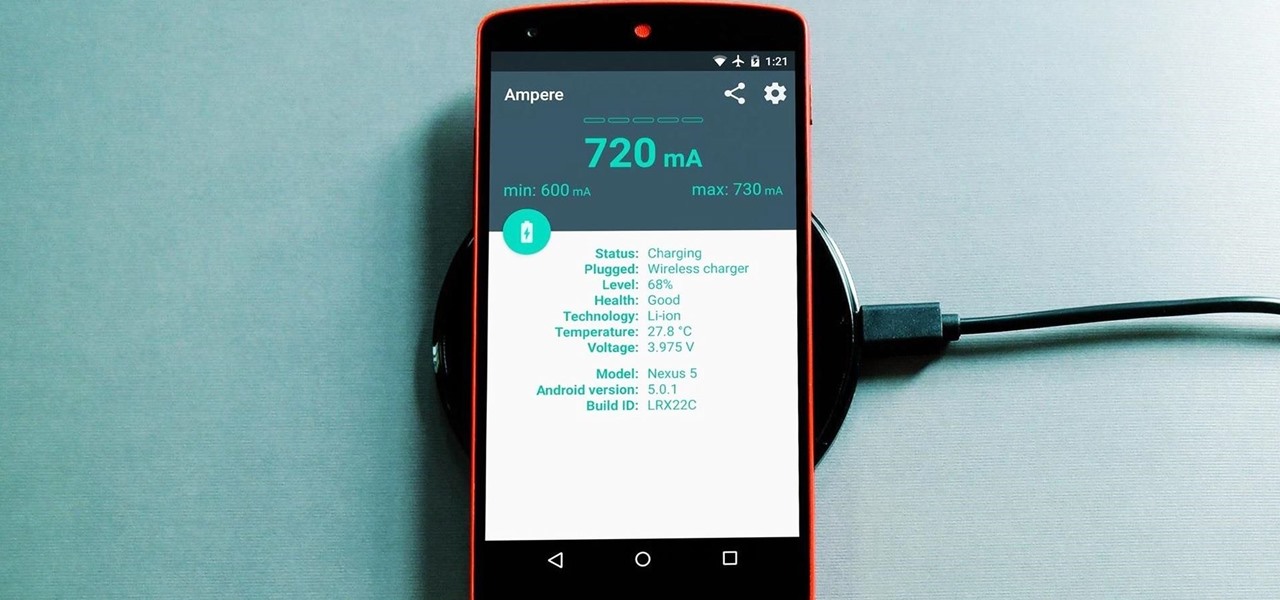
Not all smartphone chargers put out the same amount of current. The adapter in your car probably charges your phone a lot slower than the one plugged in at your bedside, and if you use wireless charging, it may be a bit slower still.

At one point, Netflix did have trailers for movies online, but they have long since abandoned the practice for a number of reasons. Firstly, trailers have to be licensed in addition to films themselves. Secondly, previews apparently did not increase the number of titles added to user queues.

An open bottle of wine can be dangerous. You intend to enjoy—nay, savor—a single glass, but then two episodes of Top Chef later, that sucker is empty. Now you have to go to work the next day with a wine hangover. What happened? Turns out there are some unconscious reasons you might be chugging more wine than you wanted. Never fear. Along with clenching your fists to make better food choices, there are some tricks you can use to moderate your wine intake. Researchers at Cornell University disc...

Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel.

Toss aside that Sudoku. Take a stab at the new craze to hit the Times: KenKen. New York Times puzzle editor Will Shortz introduces KenKen and gives a brief play-by-play demonstration of this new puzzle craze.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

We don't know about you, but we're wondering how the hell Katy Perry even has time to work out these days with the countless number of promotional appearances, hostess jobs, planning a wedding, and singing gigs she's doing on a daily basis. But, after looking at a few recent pictures of the singer's fit and curvy body, she must be doing something to keep all that in shape.