One of the latest home-improvement gadgets out there today, smart lighting, has become more popular as prices come down. That being said, its still quite a penny to shell out. In this article, I'll go through a few of the top products out there today, including the Philips Hue, Belkin WeMo, and Lifx.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Cheese might be one of the most satisfying snacks around, whether you prefer a slice of snappy Irish cheddar or a creamy, rich portion of Brie. It's been called "dairy crack" by a respected physician and for good reason: eating cheese produces casomorphins, which effect the human body like opiates. It also contains trace amounts of actual morphine.

It is a truth universally acknowledged that food molded into fancy shapes somehow seems tastier. That's true even with chocolate, which is inherently delicious. Now, while you can buy chocolate that's been pre-molded into fancy shapes, you can have a lot of fun and save a few bucks by making your own specialty chocolate molds. All you need to get started are items you most likely already own.

There are hundreds of delicious ways to enjoy caramel, from chocolate confections to sticky caramel apples and carnival bags of caramel corn. Caramel might be the special sauce that makes every dessert taste better, but it's also surprisingly simple to make.

A good, sharp knife is a cook's best friend, which is why there's so much passionate debate about what kind you should get. Most enthusiastic home cooks opt for a stainless steel knife, but it turns out there's a different option that the pros favor, and that's carbon steel.

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

Can you tell when your friends are serving up a bunch of BS, or are you constantly oblivious, unsure if they're spinning a valid story? With so many ways to lie and fake information floating around, it can be impossible to tell what's the truth from what's complete BS. Here's how to sort through what you hear and find the real truth.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.

Certain ingredients that a professional chef might work with in a restaurant-style setting may seem bizarre, dangerous, and even downright scary to a home cook, and for good reason.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

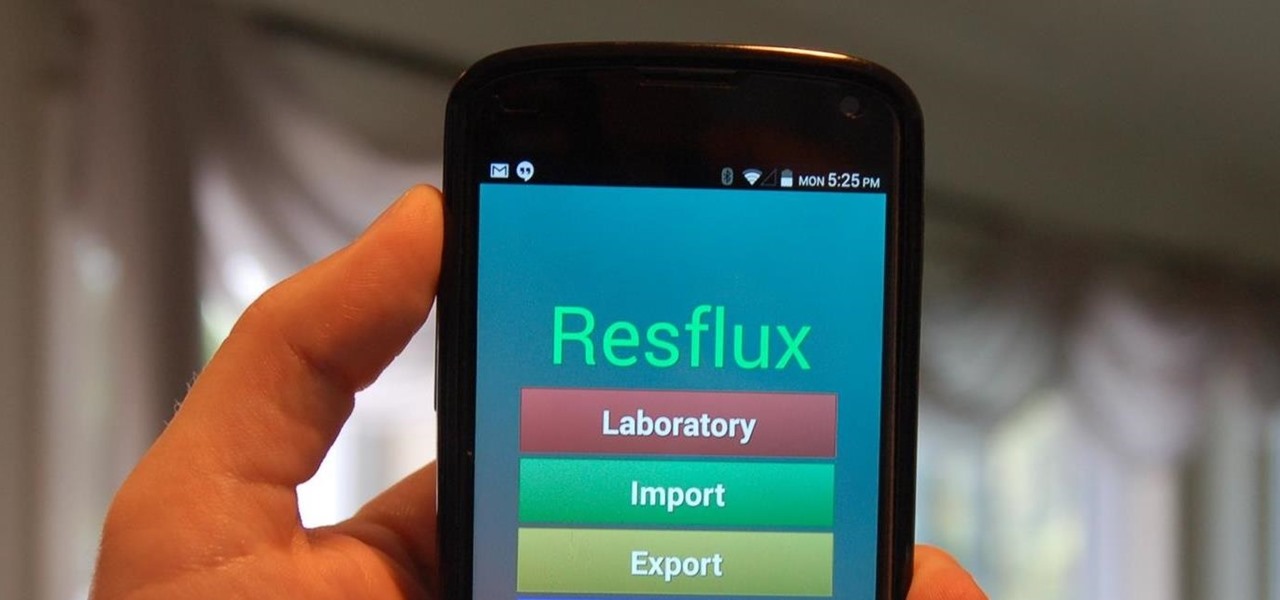
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

What would you say if I told you it was entirely possible—even desirable—to cook anything from a simple dinner to a great loaf of bread without using measuring cups, spoons, or a scale?

There's nothing better than real, homemade tomato sauce, but to really develop the flavors, it usually has to simmer for a few hours. And while it's totally worth doing if you have the time, some nights it's just not an option. That's where the pre-made stuff comes in. Jarred pasta sauce certainly doesn't taste the same, but it's really easy to dress up when you need something quick. If you don't want anyone to know your "secret recipe," here are 10 ways to make store-bought spaghetti or mari...
What is Programming? Why need to learn? How to get started? Which language to choose? While surfing web, you must be encountering various softwares, games, etc. and might be thinking to make one, but don't know where to start. Here, I am starting series in Programming.

There are some ingredients I cook with so often I can never buy too many of them, and most of them are produce. Onions, garlic and fresh herbs are staples in a lot of dishes, and they may be inexpensive, but when you use them on a daily basis it can add up.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Xposed, by XDA developer rovo89, is a framework for your Samsung Galaxy S4 (or other Android device) that lets you add tweaks and customizations to your ROM (either stock or custom) without any real hassle.

One of the most heated topics in the Android community now (and probably forever) is stock Android, with lots of users requesting the ability to use it rather than the manufacturer's skin.

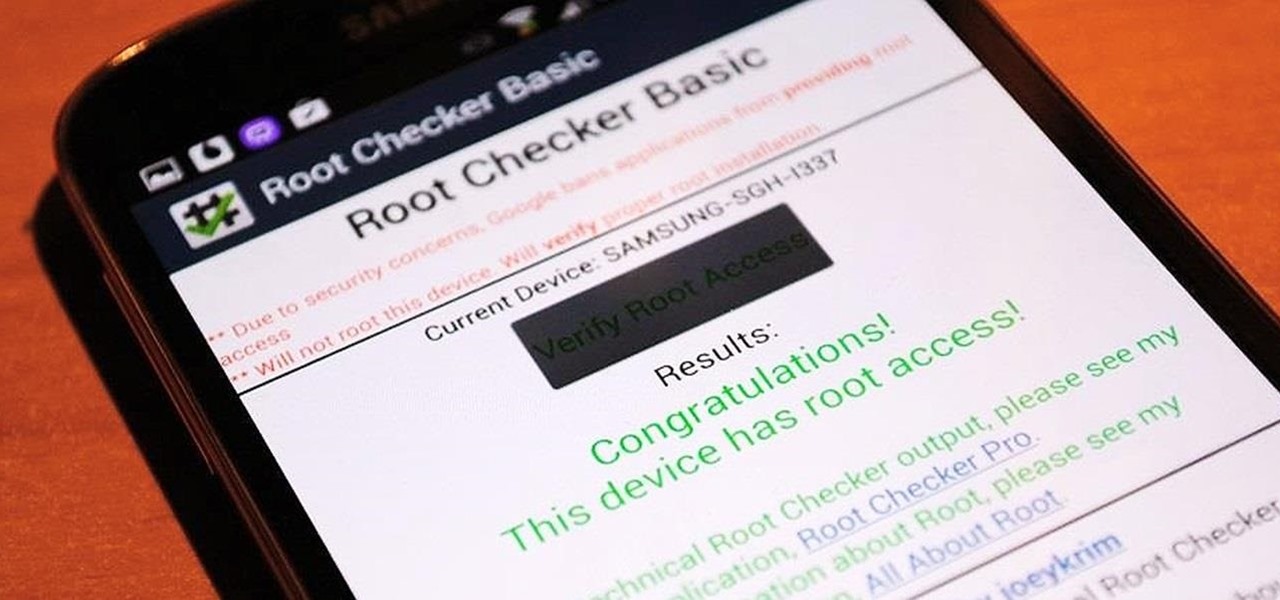
Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

The biggest complaint I have with my Nexus 7 is the lack of support for different types of media files. I have a lot of movies and music that I've downloaded off the web, in many different formats, and I want them on my tablet.

It's always a good idea to have a pack of mints on hand, especially right after a cup of coffee or a lunch made with loads of garlic. Whether you're going on a date, to the dentist, or to an interview, bad breath is a major faux pas and totally avoidable. Simply pop a mint! But not just any old mint — homemade ones not only freshen your breath but can give you a sense of pride every time you need one.

One of the best aspects of Android is its customization options. You can change launchers and icons, add widgets, and replace standard apps with others that allow full customization. Android allows your device to really take on your personality, from the inside and out.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

As I said in this earlier post, there's no easy way to explain or define the Steampunk aesthetic. There are a large number of Steampunk tropes or "cues", as I call them, that bring to mind the feeling of Steampunk. These cues combine to push past the "not-Steampunk" threshold into firmly "Steampunk" territory.

Vampires and bad dreams aren't the only enemies of the unwary sleeper. Teeth grinding while asleep is an annoying and possibly painful problem afflicting may people. There are a variety of reasons you may grind your teeth but, luckily, there are also a number of solutions to this nocturnal problem.

In this video series, expert Bo Feng shows you the proper stroke order for writing Chinese characters properly. The long tradition of calligraphy has developed techniques for writing that will make your characters seem more authentic. Bo teaches you the seven rules of writing Chinese characters: top to bottom, left to right, upper left to bottom right, outside to inside, horizontal before vertical, left slant before right slant, and center before wings.

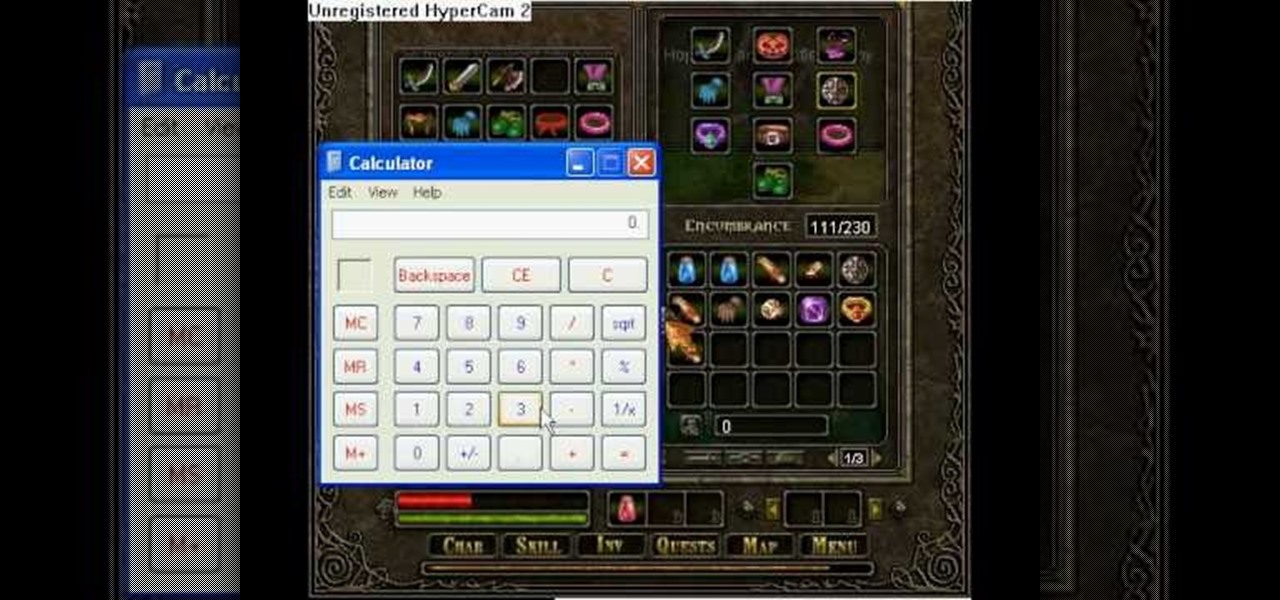
Wish things were free? Well, with this hack, you can make sure all the gold is zero and everything costs nothing. How? With Cheat Engine!