Acanthamoeba keratitis (AK), a rare eye infection caused by the Acanthamoeba ameba found in tap water, affects a few dozen people in the US every year. In some cases, it can have devastating effects, like what Irenie Ekkeshis has experienced; She was blinded by AK in her right eye due to a contaminated contact lens.

Growing populations and higher temperatures put pressure on world food supplies. Naturally occurring soil bacteria may save crops in drought-stressed areas, put more land into crop production, and produce more food.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

Bacteriotherapy sounds a lot more amenable of a term than "fecal transplant," yet they're both treatments that use bacteria itself to cure or treat infections. Fecal transplants, specifically, are an up-and-coming treatment option for a potentially deadly and difficult-to-treat diarrheal infection called Clostridium difficile.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

In the Western world, the only time you'd associate food with cockroaches is health code violations. And while other cultures and countries are more open to cooking with and eating these and other little buggers, insects are probably not a food trend that will be adopted by the West anytime soon.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

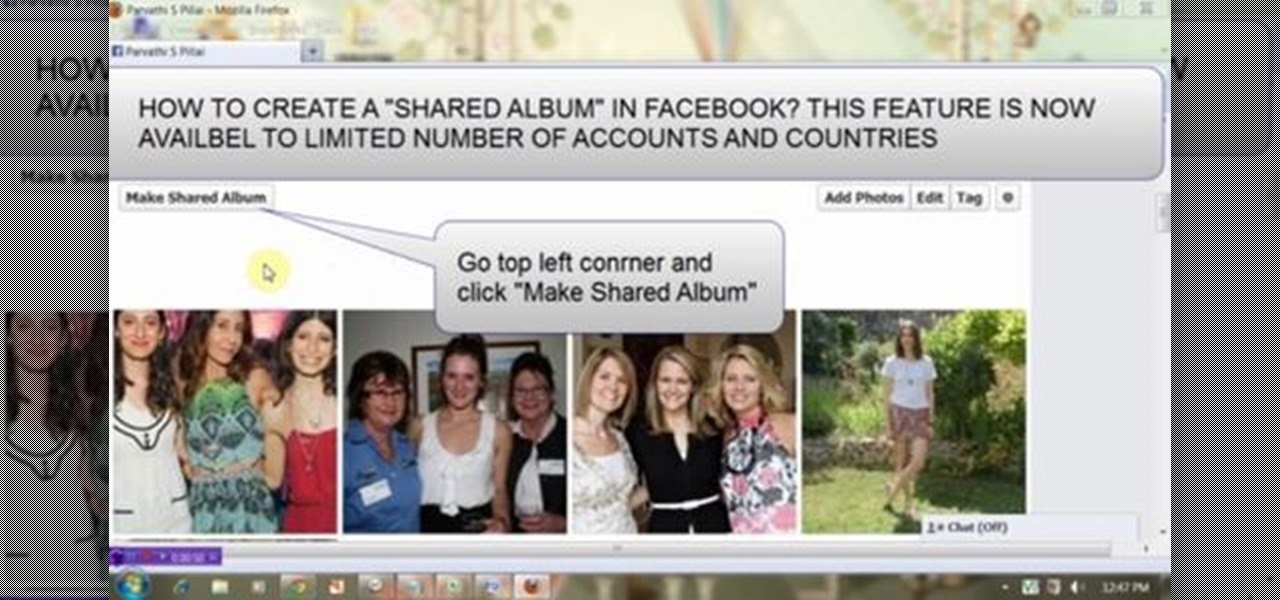
Facebook is a very useful social media sites. Shared album is a place where multiple users can upload, view and edit photos. Maximum of 50 people could share a Shared album. This video will show you how to create a shared album on Facebook. Hope this feature will be available to all users and countries in near future. Watch the video and Employ the technique in your Facebook account.

Sometimes pills aren't the best answer. Doctors do not need to prescribe medications for common health problems, such as high blood pressure. They can be helped by simple adjusting your lifestyle. If you have high blood pressure, you are more than twice as likely to develop heart disease and six times more likely to have a stroke than people with normal blood pressure. Manage your condition through diet.

Salsa is the prefect summer time snack, perfect for any kind of chip. And this version made with corn is even better than your standard salsa. Throw some spice into your day with this refreshing recipe that will always find itself in your fridge. Watch the full video recipe for making the fresh tomato and corn salsa.

Ali Alami with Fit Climb demonstrates how to get in shape for mountaineering. You can do these exercises in a park or at home. Your core and lower body are important in mountaineering. First, find a wet, wood bench that is four to six inches off of the ground. Do step ups to work your quadriceps and glutes. Balance briefly on one leg and then bring the other leg up. You can also do side steps. Step downs help you get you used to gravity. Calf raises are also helpful. To strengthen your core u...

This is a video from the Certified Horsemanship Association (CHA). See more at CHA-ahse.org and CHAInstructors.com. In this video, Brent Morgan, Christy Landwehr, and a horse named Phoenix show us the correct riding position. In the basic, safe riding position, what you're looking for is a line from the ear, through the shoulder, through the seam of the jeans, down through the heel. That is the correct riding position. As riders, we have a tendency to let our feet slide forward like we're put...

First of all whenever there is low rainfall and higher heat then there are problems.You shall notice that there are brown colored needles which dry up and then drop of. Sometimes they start at the tip and then move towards the branch. This shows drought and you need to soak in lots of water to overcome. However if you notice the brown needles going from the middle to the tip then these are due to natural process. Another problem is the presence of spider mite. Take a white sheet of paper and ...

If this is your first novel or you want to make a better one then this video will give you good advice on how to write fiction character for a great novel. The animated animals and people in this video will give you some great advice to improve your novel.

Begin hacking your way through the hordes of minions in the Xbox 360 game Darksiders. The Prologue is where you really start to develop your creature killing skills. The apocalypse has begun on earth. Angels and Demons reign chaos upon the planet in a battle for the souls of humans. This is when War steps in. One of the four horsemen, War is here to restore balance. You begin the game with a powered up War. Note that he has 7 Lifestones (the little green skulls above the health meter). Each o...

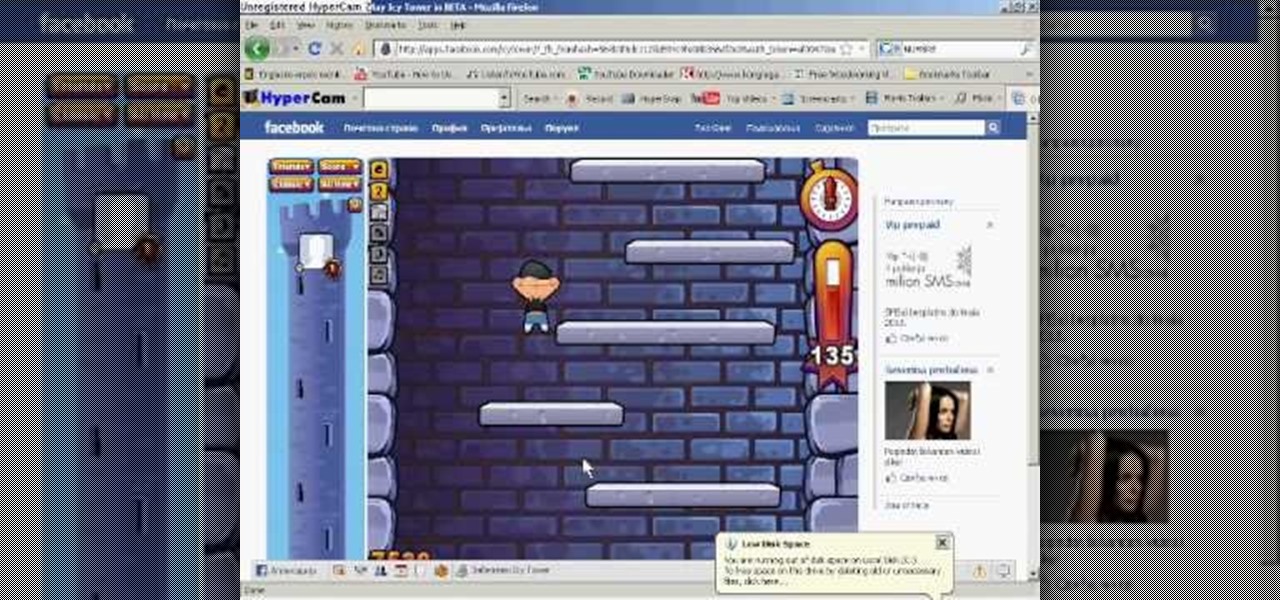
Make your Icy Tower score the highest ever. Break records. Impress friends. Rule the game! How? Cheat Engine, a simple hacking program.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Learn how to reduce your risk of allergies. Transform your home into a sanctuary for your eyes, nose, and throat by reducing the risk of allergies.

Check out this Scam School video on leanring the ultimate strength tricks. Bend frying pans and horseshoes with your bare hands! Watch Brian make you think he can use his bare hands to bend a horseshoe and to roll a frying pan!