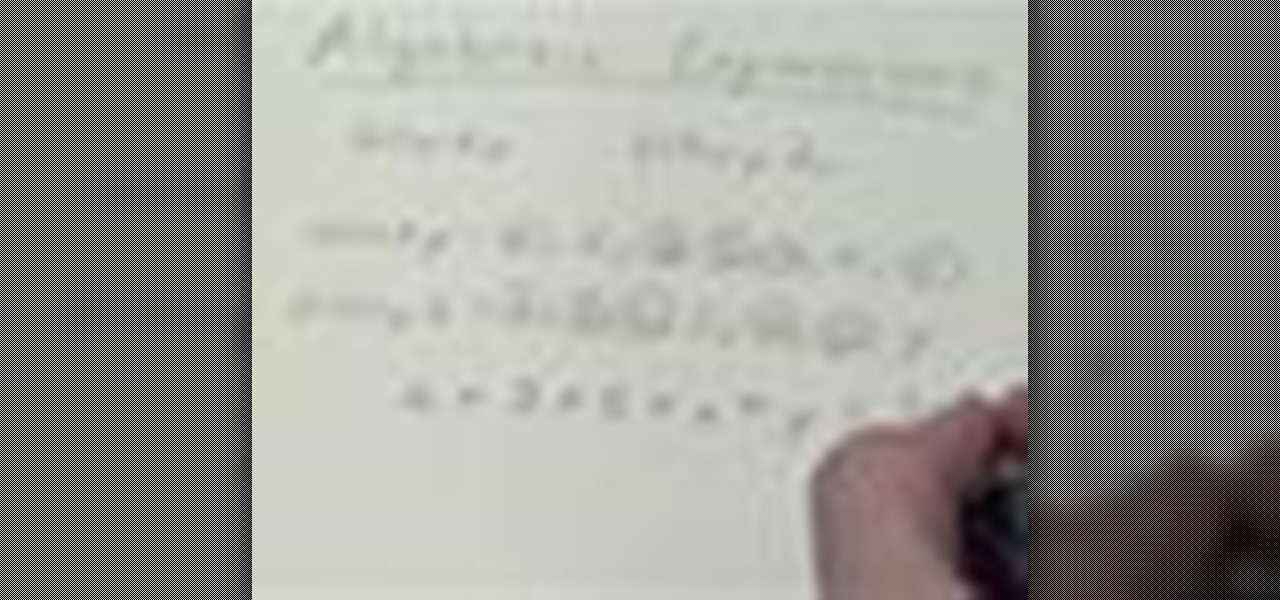Netmarble's ChronoBlade, a mobile role-playing game, has made its way to iOS and Android by way of a soft launch that will make it exclusive to users in Canada and Singapore for a couple of months. Its console-quality graphics and extra features will surely make it a hit when it's released worldwide, but if you've got a little gumption, you can skip the wait and install it today.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.
As Intel steps up their investment in driverless technology with a $15 billion acquisition of Mobileye, so have automotive supplier Bosch and NVIDIA teamed up to manufacturer driverless car systems with the much-awaited Xavier chip.

Antibiotic use in infants has been associated with a host of childhood conditions later in life. Yet when an infection is suspected in a newborn, usually a sample of their blood is drawn to check for the presence of bacteria and 5 to 8 percent of them receive antibiotics while the diagnosis is pending.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.

The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually been around for 20 years now. Watch the video below to see how the colorful roll is created.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Welcome back, my nascent hackers!

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Ever since the early days of their existence, cell phones have been reducing the common wristwatch to nothing more than a fashion accessory. I'm not exactly a watch aficionado, but I do own a few that I wear on a daily basis. Since I have family in different parts of the world, I love my watches that have a second time zone, allowing me to see what time it is where they are.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

Watch as professional guitar teacher and country guitar player Jim Dufresne teaches how to get the perfect country guitar tone. Learn what strings to use, what settings to set your amp, the best acoustic tone, the best classical tone, the best amplification, and how to use the slide for a great country guitar.

How to grow pineapple inside your home

Did you know that you can zoom in on your Mac laptop just as easily as you can on the iPhone? All you need is your fingers, your mouse and to activate the zoom function on your computer. Check it out!

In this video, you will be walked through the game Foreign Creature. There are human characters in this one, with word clouds, in an office setting with bulletin board, desks, rolling shelves, and tack boards. In another scene of the game, you will see a hospital setting with nurses, surgery table, patient, medical equipment, and doctors. In this setting, the patient is a foreign creature who blacks out the medical staff and proceeds to stalk the hospital. Police try to capture the humanoid-l...

Roughly half of all Americans believe in extra sensory perception... Are you part of that statistic? Ever get the feeling you have a paranormal ability? You can investigate your psychic abilities and hone your skills with these tips.

Make your own custom characters for Icy Tower! It's as easy as drawing stick figures, believe it or not. Only stickman don't look as cool, unless of course it's a stickman that you want to use as your Icy Tower character.

This guide is all about hacking Icy Tower. You will need to download Cheat Engine 5.5 before you can try this hack. See what you can do.

Find a way to get a combo achievement in Icy Tower… by cheating. With Cheat Engine, it's easy to hack Icy Towers. See for yourself.

If you've ever been asked to find the GCF, or Greatest Common Factor, of a series of numbers or algebraic expressions, check out this video to learn how.

Do you ever feel as if your mind is running away from you? What if you could map out all of those thoughts into a coherent map that helps you make sense of your reality? Well, now you can.

We all know how volatile the stock market is, especially during times of crisis. That does not mean that the market is impossible to gauge, however. Day traders are trained to read charts in order to recognize market trends and price patterns, giving them the insight they need to make their trades as profitable as possible.

Apple just released the second iOS 13.4.5 developer beta today, Wednesday, April 15. The update comes just over two weeks after the release of 13.4.5 dev beta 1, which introduced a new way to share Apple Music songs to Instagram and Facebook stories.

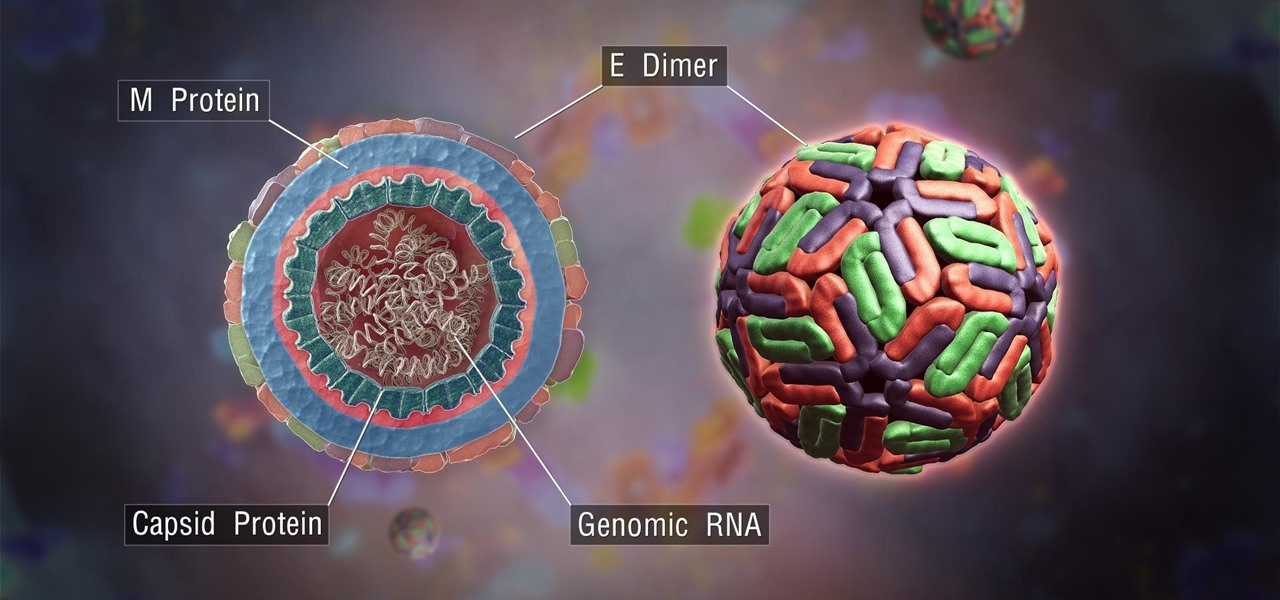
The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

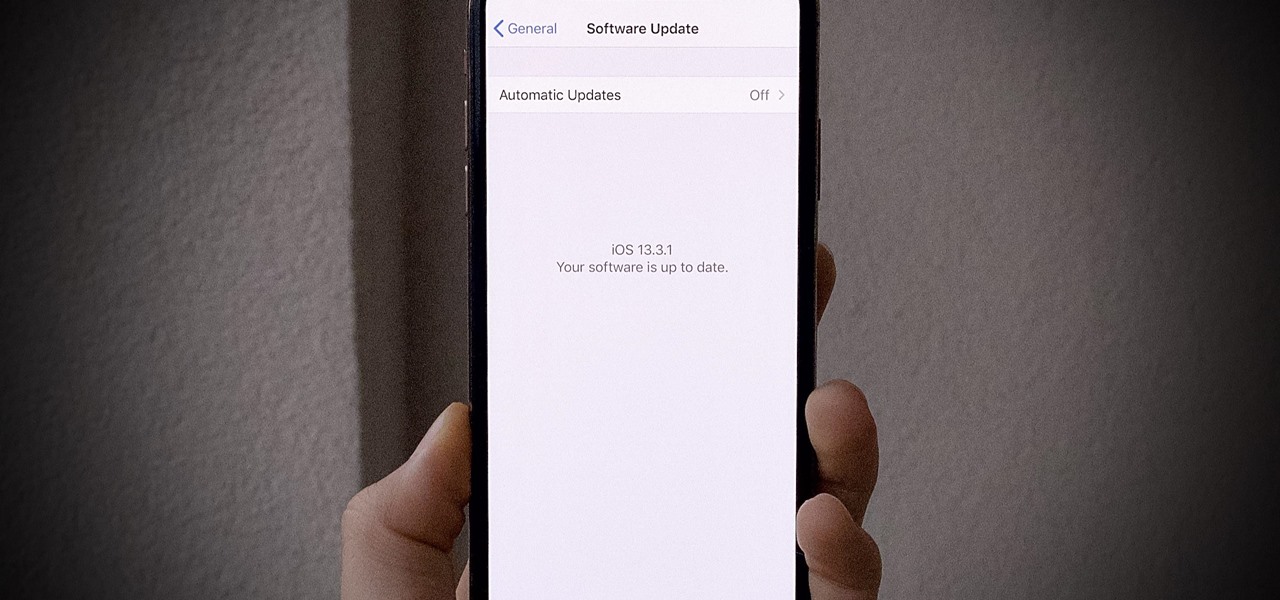
Yesterday, Dec. 17, Apple released the first developer beta for iOS 13.3.1. The update marked the first new beta in almost a month since iOS 13.3's fourth beta dropped on Nov. 20. Now, one day later, Apple has pushed out iOS 13.3.1 public beta 1 to everyone who wants to try out new features first.