If you want to improve your violin technique then this lesson is for you. This violin tutorial teaches you a way to improve ear training with octave exercises. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should r...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to improve your octave playing in scales. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your finger...

Enjoyed throughout the Middle East, Arabic coffee is deliciously rich, and easy to make at home. Watch this video to learn how to make Arabic (or Turkish) coffee.
This glitch is a simple one on Killzone 2 for PS3. To do this glitch, you'll need to perform the medic technique Just watch the whole video walkthrough to find out how to find the Radec Academy Glitch.

On this map, you can do this great glitch on Killzone 2 for PS3. There's a lot to do on this map, so there's sure to be many more glitches, but you'll have to figure that out yourself. Just watch the whole video walkthrough to find out how to find the Outside Pyrrhus Rise Glitch.
In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

Check out this supernatural tutorial video that offers 7 tips on getting started in becoming a paranormal investigator. Just follow these simple steps:

New to the lathe or simply interested in further developing your skill set? In this four-part tutorial, you'll learn how to create a hollowed-out ball form using a lathe and a captured hollowing rig.

In this installment from his video tutorial series (in which he covers everything from improving timekeeping to creativity and orchestrations in patterns and drum fills), Brian Ferguson demonstrates how to play the train beat, a favorite of country music.

Swing dancing dates back to the 1920's, where the African American community, discovered the Charleston and the Lindy Hop, while dancing to contemporary Jazz music. The term "Swing dancing" is used to refer to one or all of the following swing era dances: Lindy Hop, Charleston, Shag, Balboa and Blues and extends to include West Coast Swing, East Coast Swing, Hand Dancing, Jive, Rock and Roll, Modern Jive, and other dances developing in the 1940s and later.

Learn how to do the "Steam Shuffle" or "Scooter Shuffle" with this line dance tutorial. This is a 48 count, 4 wall country western line dance. Follow the steps in this how to video and you'll be doing the "Scooter Shuffle" in no time.

Learn how to do the Texas swing line style dance with this tutorial. This how to video instructs you on variations of the country western line dance such as the Grapevine, heel taps and heel toe moves.

The Apple rumor mill never stops churning and when it comes to augmented reality smartglasses, the chatter has been particularly hot in recent months.

The augmented reality smartglasses race is getting a major new entrant that could significantly change the entire landscape.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

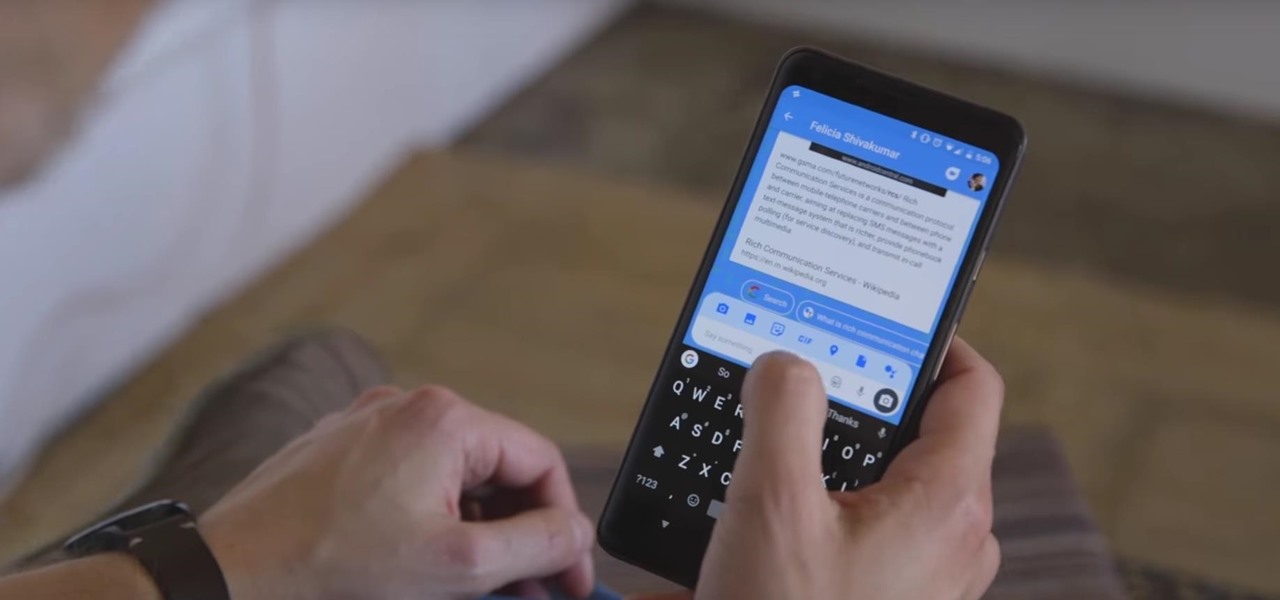
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

What's the best way to celebrate your independence? Alcohol. There's no a soul out there that can't enjoy a few drinks during a nice celebration. So, why not go a step further with some crazy shots? Shots are the quickest and easiest way to get drunk fast. Do it for your country — but don’t overdo it. Mix up a batch of patriotic cocktails for your Independence Day party.

To play "People are Crazy," you begin with what is called the intro. For this song, the intro includes playing the same group of notes or strings two times; this is called "repeat" on the sheet music. All of the these notes will be played on the B-string except for one. The exception is played on the G-string and this is just played open. Start on the 10 thread (fifth string capo) holding it with your ring finger, count to the fifth string and play it twice, pause, then play 5, 3, 1, and then...

In this gardening tutorial, Martin Fish from Garden News demonstrates how to prick out Foxglove seedlings. "Pricking out" is when seedlings are transplanted into larger pots or trays to give them more room to grow on. The ideal time to do this is when the seedlings are at the two-leaf stage and before the true leaves have developed, or as soon as they are large enough to handle.

DBAs, developers and designers are often tasked with building and managing databases. Especially when the database has been developed by someone else, you have little to no insight into the database structure. Join Quest Software to learn more about Toad Data Modeler and its features that provide: