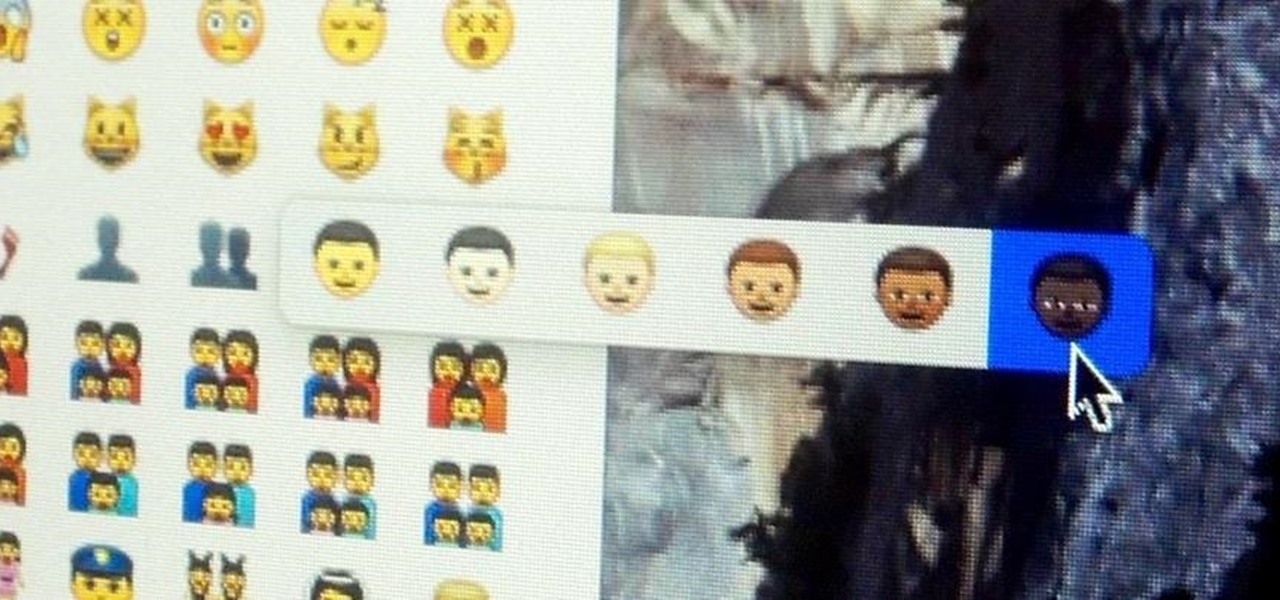
Apple just recently launched its 10.10.3 Public Beta for Mac OS X Yosemite, and while it comes with mostly bug fixes for 10.10.2, it also includes a brand new Photos application that's meant to replace iPhoto and Aperture, as well as the inclusion of more diverse emojis.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Each flavor of sake, the national spirit of Japan, comes with its own fans, not unlike whiskey aficionados here in the States. While sake is often called "rice wine," it is more akin to a malted beverage like beer.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

Surely you're aware of the Sony hacking scandal by now (here's a quick primer if you're not), as well as the multi-billion dollar company initially bowing to threats by canceling the Christmas release of the The Interview, the film at the center of the whole debacle.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Summer is here and flocks of people will make their way to beaches, lakes, and rivers across the country. But before heading out to places like these, it's always a good idea to check the local weather forecast first.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Ask a thousand Nexus owners why they chose their device over an iPhone, and after getting an earful of Apple hate, you will likely hear a clear pattern in their responses, namely, the freedom to customize their phones.

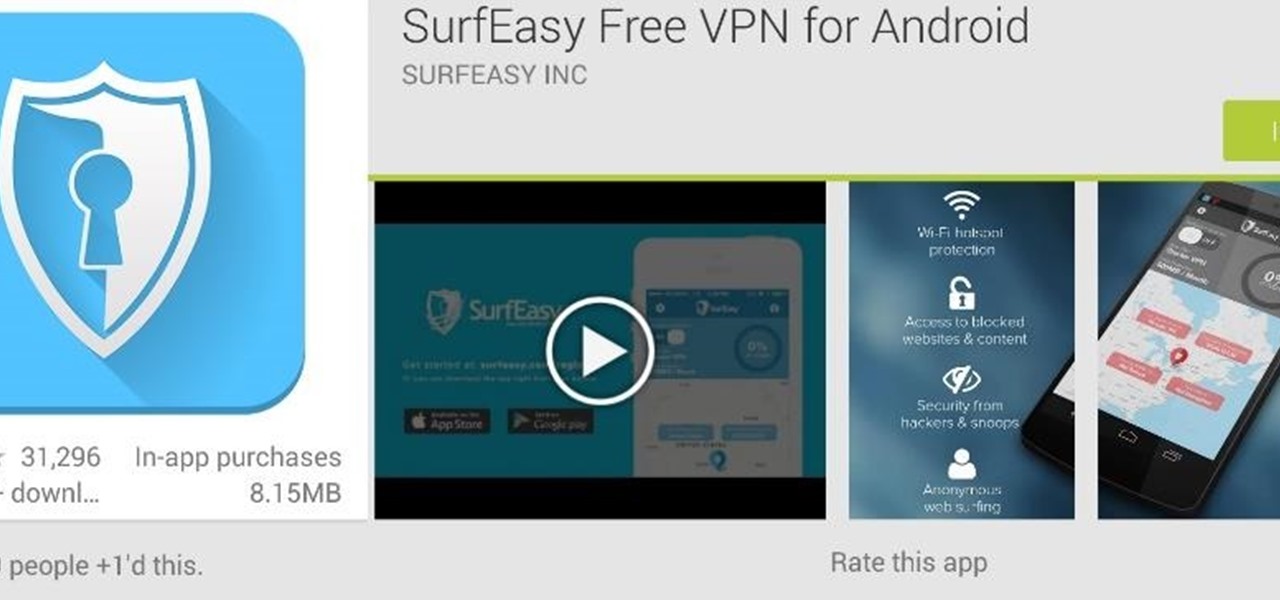
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Sprint and T-Mobile have agreed to a $31.6 billion deal that, if it gets through federal regulators—which is far from a sure bet—would create a formidable carrier to really compete against AT&T and Verizon. The deal comes packaged with a $1 billion "breakup" fee that Sprint would have to pay T-Mobile in the event the deal does not go through. After the deal, Deutsche Telekom, which owns about 67% of T-Mobile, would maintain a 20% ownership stake.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

As I begin my move across the country, I find myself dodging all kinds of Craigslist scams, particularly in the apartments and housing classifieds. Fortunately, I've discovered a little trick that will tip me off to a scam before I lose $1,000 in a fake security deposit.

Netflix has received a lot of publicity lately, and not because of its impressive worldwide library. From blog wars with Comcast to streaming deals with Verizon, it's easy to forget that the company exists for our entertainment, but sometimes that entertainment has drawbacks.

Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the power button mechanism, free of charge, for certain iPhone 5 models.

Imagine that Tinder fornicated with Facebook and had a baby. The product of that union would be the hideous, yet overwhelmingly interesting SocialRadar, an app dedicated to stalkers and stalkees.

After many beta builds, Apple has finally released iOS 7.1 to the public. It includes bug fixes for the old iOS 7.0.6, along with UI enhancements and even some new features.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

It's always the snack you're most looking forward to that ends up being moldy when you open the fridge to grab it. Always. That slice of leftover pizza or chunk of cheese you've been thinking about all day? We've all been there. What separates us is how we choose to deal with it. Personally, I toss anything that has even the slightest hint of mold, but not everyone errs on the side of caution. Some people don't mind the risk and just cut off the green or fuzzy parts and eat the rest.

Most people have a few different knives in their kitchen drawers, but not everyone knows which one does what. Sometimes it seems easier to just grab whatever's clean, but choosing the right knife for what you're trying to do can actually make a pretty big difference.

Whether it's because you travel quite often or have loved ones in another part of the country, Android makes it easy to place dual clocks on your home screen using a widget. While there are several other widgets you can use to tell the time, that's pretty much the only way you can get two different time zone clocks on your Android device. If you want an alternative option, I'm going to show you a mod that lets you get two different clocks in your Status bar on your Samsung Galaxy Note 2 or ot...

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

While the legality of secretly recording phone calls varies in each country, sometimes it's useful to have audio documentation of conversations you have on your Samsung Galaxy Note 2.

For the most part, Xbox Live is amazing, but there is one thing that has been annoying for pretty much everyone, to say the least. Microsoft Points.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

I've never been much of a runner. I've tried running alone, with a partner, on busy sidewalks, and back country roads, but I just never got it. There are a few other forms of exercise I genuinely enjoy, but have yet to experience that "natural high" that avid runners are always talking about.

Samsung just concluded their live unveiling of the Samsung Galaxy S4! A more in-depth look can be found here.

Did you buy your new iPhone 5 without a contract? We'll, if you bought it from Apple, AT&T or Verizon, you can have it unlocked pretty easily. Why Have It Unlocked?

Later today, the Olympics are kicking off in London on NBC and its partner stations. However, if you don't have cable or a television with some good reception—or if you'd rather just follow the events on-the-go or at your desk—you're not out of luck. Photo by Locog

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

In this video, we learn how to keep your backpack safe while riding on trains in Europe with Scott Dean. When you're on a long train ride, there are high chances your bag could get stolen while on a train. If you have to leave your bag in the back, make sure you use a bag lock on it. If you are able to keep it next to you, lock your bag onto a nearby rack or the shelf. You can find a number of bag locks at www.pac-safe.com, they make a ton of different locks and travel gear that's beneficial ...

This how to video teaches you how to play the natural scale, and chord changes especially the ii-V-I which is something every musician should know. Watch this how to video and soon you will be able to play the natural scale on harmonica.

Even as we look forward to returning to work in person, the last year has changed how work can be done. That means there will always be a demand for good programmers and coders who can support the digital infrastructure of the online working world. The Backend Developer Bootcamp Bundle can give you the expertise you need to become a highly qualified programmer for only $29.99.