I love me some salad, but I'm also kind of a big baby when it comes to eating them. The greens have to be perfectly crisp and fresh, which is why I'm such a nut about storing them properly, including rethinking how I use my refrigerator, using a paper towel or dry cloth to wrap them, or even puffing a little CO2 into the plastic bag to keep them fresh. I've even developed an arsenal of tricks to restore life to soggy greens.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

We all know that it's important to drink water regularly throughout the day. After all, it has so many benefits, including flushing toxins out of the body and maintaining kidney health and good bowel movements. Turns out that's only part of the story. While being properly hydrated is key to maintaining overall health, it's also a big component of maintaining and even increasing cognitive ability. Plus, drinking enough water regularly can help you lose weight, if you know when to drink it and ...

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Probably one of the most sought after features of the LG G2 is its "Knock Knock" capabilities. Rather than dealing with that pesky power button, you simply double-tap portions of the screen to either sleep or wake your device.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

The advent of a new Nexus phone begins with the bigwigs at Google partnering with a manufacturer, then selecting that manufacturer's flagship as the model for the new Nexus hardware.

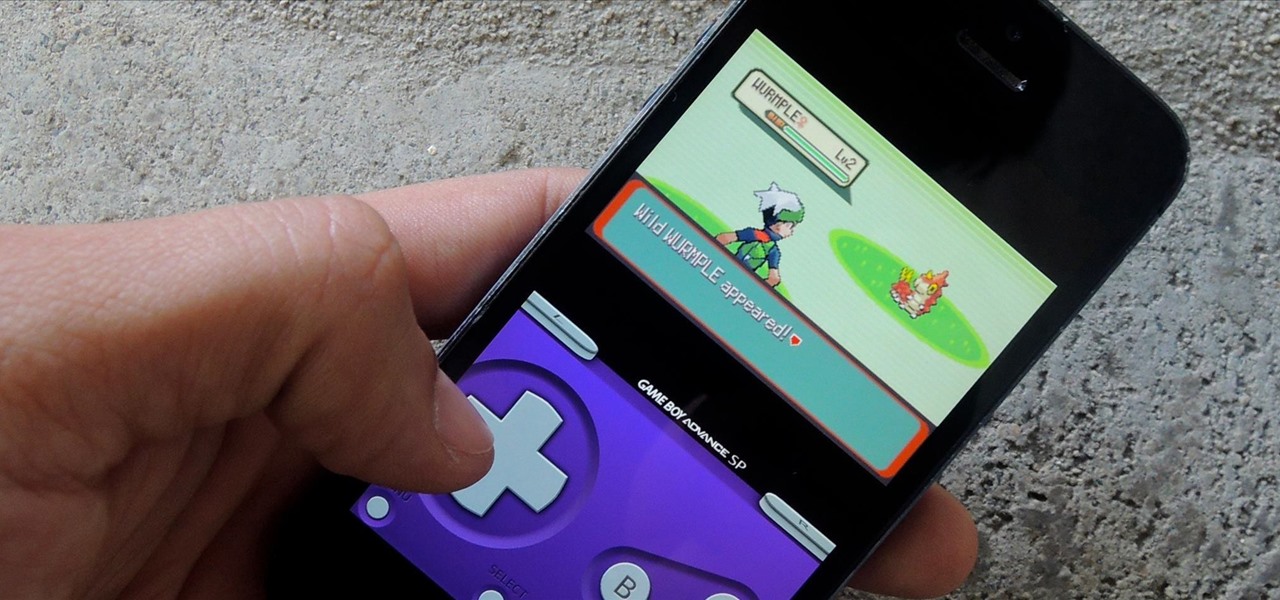
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Theming and modding are a big part of the softModder community, but there are endless ways to customize our Android devices. Which ones should you download? Which ones should you avoid? It's extremely frustrating to find them all—and pick and choose.

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

While the rest of Big Tech is still moving relatively slowly on augmented reality smartglasses, Snap continues to supercharge its own experimental AR wearable called Spectacles.

For awhile now, Google has offered the ability to translate text through smartphone cameras via Google Translate and Google Lens, with Apple bringing similar technology to iPhones via Live Text.

For better or for worse, Google started the race towards smartglasses for everyday use with Google Glass before scrapping the Explorer Edition and pivoting towards enterprise customers.

When most people think of Los Angeles they think of Hollywood and the movie industry, but in the last 10 years the city has rapidly transformed into a thriving new hub for visual artists.

Mobile augmented reality gaming pioneer Niantic is chomping at the bit to get games like Pokémon GO out of smartphones and onto smartglasses, and it appears to be taking matters into its own hands.

The moment many of the crypto savvy insiders in augmented reality and VR have been waiting for is here: we're finally getting our first big auction of NFT art that exists purely as a hologram.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

Apparently, we learned nothing from Jurassic Park, as scientists are still working on bringing extinct species back to life. Until that day comes, you can interact with long-lost animals through augmented reality...if you have a newer model iPhone.

Ever since China's Nreal unveiled its Light smartglasses at CES two years ago, an army of look-alikes have emerged from the Asian nation.

Waking up to buzzing alarm clock is so 20th century. Wouldn't it better if the first sound you heard in the morning was your favorite song? Whether it's a track to get you motivated or something to put a smile on your face, a song can do wonders for your mood and help you start the day right.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

You've just picked up your new Samsung Galaxy S20, S20+, or S20 Ultra — but wait. After you turn it on and restore your data, there a few apps you should install to get the most out of your updated phone. Installing these eight apps right away will help maximize your experience from the very beginning.

Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

Sorry, Galaxys S11–19, Samsung's jumping straight to Galaxy S20 this year. They're also going with essentially three base models before accounting for niche variants. Of these three models, it's clear which one's the best: the Galaxy S20 Ultra.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Though more well known for their OLED displays and advanced cameras, Galaxy phones like the S8, Note 10 & 10+ and S10 series are a force to be reckoned with when it comes to audio. In fact, flagships from the S9 on up feature AKG-tuned stereo speakers, along with a slew of software enhancements that make listening to music a truly pleasurable experience.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.