
How To: Use color theory when decorating your home
Do you want your house to look dull or colorful? If the latter, then be sure to check out this video to learn how to best utilize the color theory.


Do you want your house to look dull or colorful? If the latter, then be sure to check out this video to learn how to best utilize the color theory.

If you're struggling a bit with algebra, check out this video to learn how to isolate a variable. Isolating a variable is a matter of separating and simplifying.

Holidays such as Thanksgiving are doomsday for most garbage disposals due to clogs. If you're garbage disposal is clogged, check out this video to see some helpful tips on how to fix it.

Superman is one of the greatest and most known superheroes out there. Developed by DC Comics, Superman has seen the world… as in comics, television, newspaper strips, video games, movies, radio serials, etc. See how to make a Superman costume in this video from GiannyL.

Whether you want to save money by making your own clothes or you just enjoy working with fabrics, choose the best sewing machine so your projects turn out great.

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Everything old is new again – even stale bread, if you know a quick trick. You Will Need

Making a storyboard before shooting a movie is like drawing a blueprint before grabbing a hammer and nails. Do it well, and make sure your film is structurally sound.

Don't hide in a cave when the market is down. Find stocks that will pay off when the bull makes its return.

Growing plants from cuttings is an inexpensive way to expand your garden. With patience and the right technique, it can be done fairly easily.

Prevent soreness and bruising after running by using this parallel lacing technique. You Will Need:

A small light tap is one of the easiest and most basic embellishments, and is a nice way for the follower to mark and express the double-time ('quick, quick') - or the 'and' count in between the beats - while the leader is leading a step on the whole beat ('slow'). A tap can be done in the middle of virtually any step - back, side, forward, ocho.

Not many people use film cameras anymore, so it can be hard to find the materials to develop your own photos at home since most local camera stores are closing. But it's actually relatively easy to make homemade developer, and you can make it with a few relatively common ingredients.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.
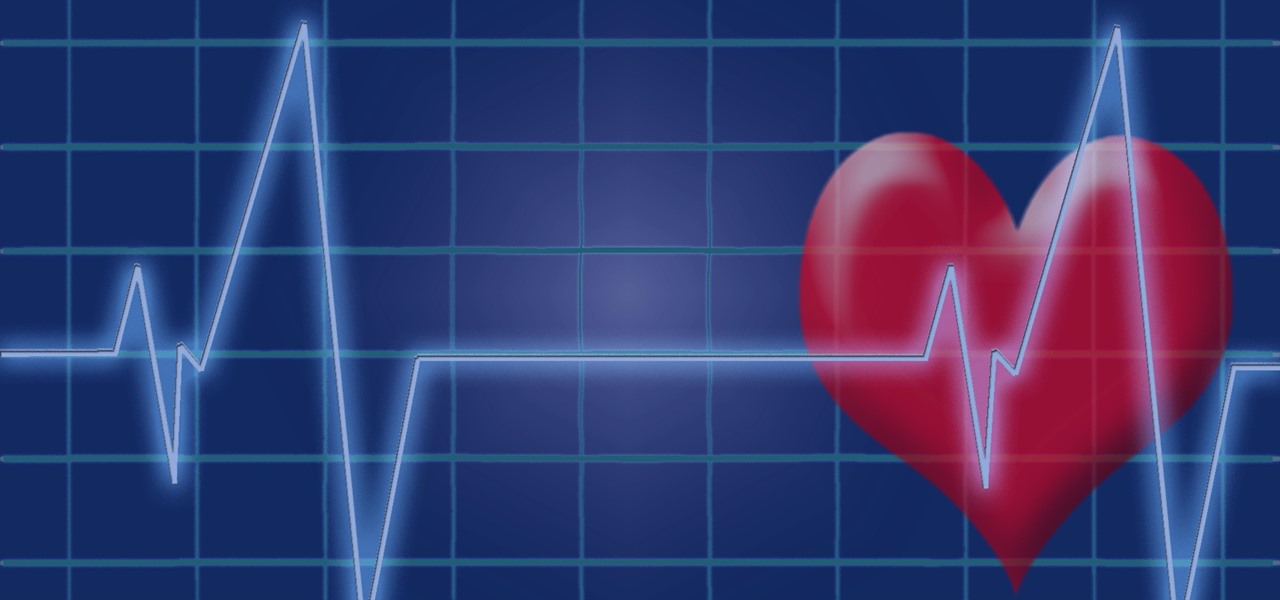
Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the blood, diabetes, and high blood pressure.
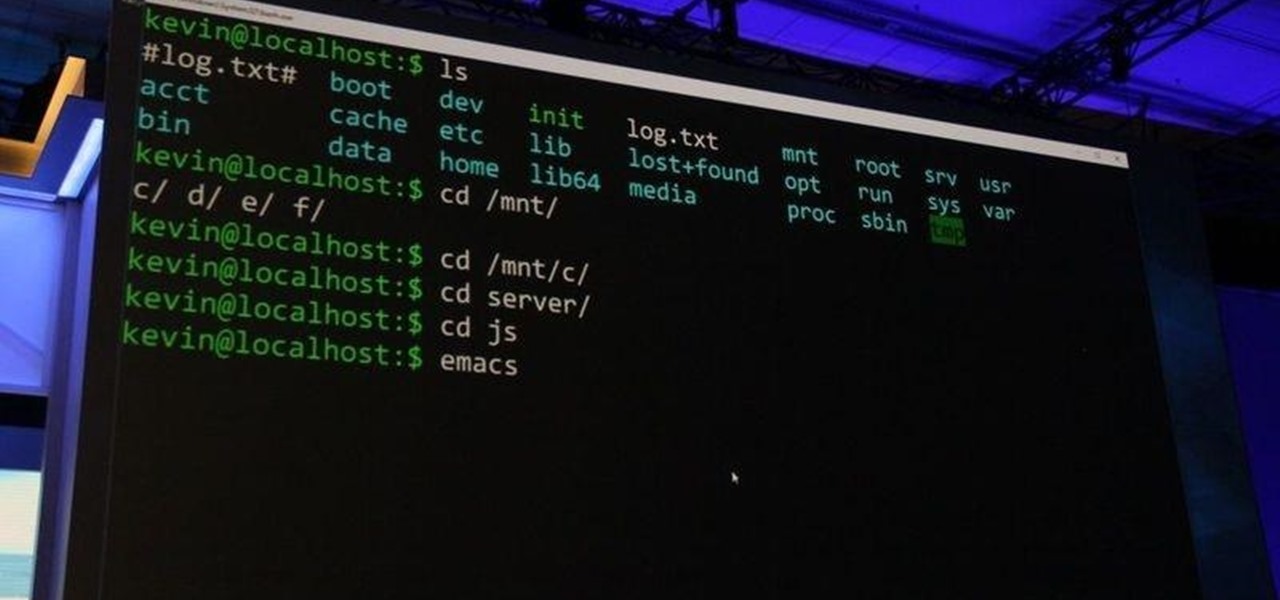
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Collodion—it's one of those things that you probably never heard of before, but have actually come across many times in life. It's used for all kinds of applications, from photography to special effects, and it even has a few medical uses. So, what exactly is collodion? Photo by Bostick & Sullivan

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.
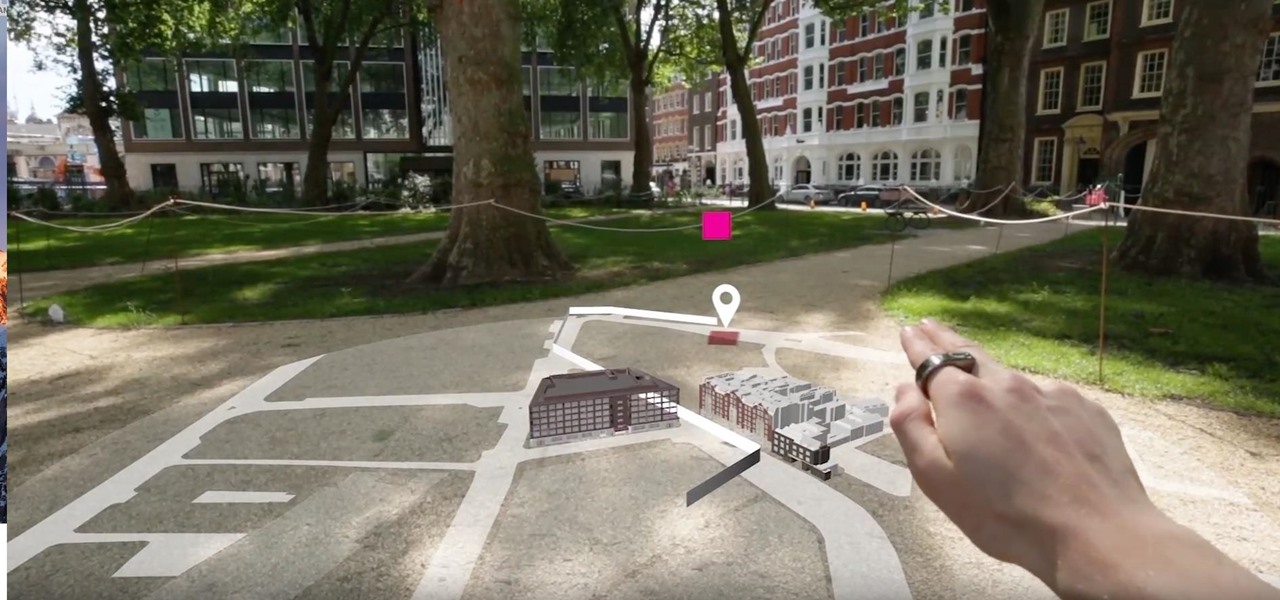
Forget what you know about controlling augmented reality experiences. "Scroll" lets you interact with augmented reality using a much more subtle approach: A ring.

Getting support for your mental health is now as easy as opening up Facebook Messenger. By just opening up the Messenger app, you can connect to Woebot, a new chatbot developed at Stanford trained in administering cognitive behavioral therapy (CBT).

The Centers for Disease Control and Prevention estimated that there were 212 million cases of malaria across the world in 2015, and 429,000 of those people died — mostly children living in Africa. Preventing and treating those infections has been a challenging world priority. That makes a new malaria drug discovery — published in Science Translational Medicine — incredibly important.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

The Albright Knot, demonstrated in this how-to video, was developed for fishing, but as it was created to tie together to diameters of rope or line, can be useful for many different reasons to tie knots. The Albright knot is relatively strong, so it's good to be able to tie this knot in various emergency situations. Check out this video survival training tutorial and learn how to tie an Albright knot variation.

This tutorial demonstrates an agility exercise. This star drill exercise workout was developed to increase your overall sports performance. This video explains the star drill exercise and how you can incorporate this agility training to develop your flexibility, balance and power.

This tutorial is a demonstration of a speed and conditioning exercise. These stair running workout was developed to increase your overall sports performance. This how to video explains the stair running exercise and how you can incorporate this speed training to develop your flexibility, balance and power.

This tutorial demonstrates a speed and conditioning exercise. This sprint high knees workout was developed to increase your overall sports performance. This how to video explains the sprint high knees exercise and how you can incorporate this speed training to develop your flexibility, balance and power.

This tutorial demonstrates a plyometrics sports training exercise. This side box jump workout was developed to increase your overall sports performance. This how to video explains a plyometric side box jump exercise and how you can incorporate this explosive training into your routine to develop your speed and power to become bigger, faster and stronger.

This tutorial demonstrates plyometrics sports training exercise. This knee tuck jump workout were developed to increase your overall sports performance. This how to video explains a plyometric exercise and how you can incorporate this explosive training into your routine to develop your speed and power to become bigger, faster and stronger.

This tutorial shows speed and conditioning exercises. This 4th quarter workout was developed to increase your overall sports performance. This video explains the fourth quarter drill exercise and how you can incorporate this speed training to develop your flexibility, balance and power.

This cone drill workout were developed to increase you overall sports performance. This how to video explains the cone drill exercise and how you can incorporate this agility training to develop your flexibility, balance and power.