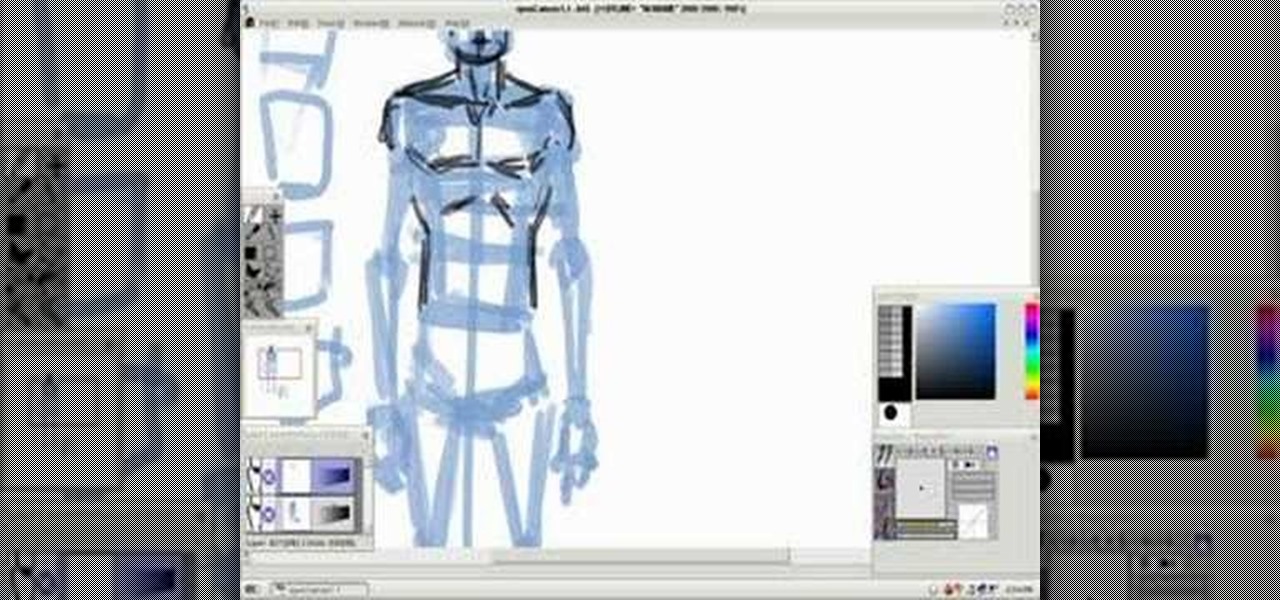
Learn how to draw a realistic and proportionate male human body on the computer. Learn how to draft a man's figure on a paint program, from basic sketch to developed drawing by following along with this instructional drawing video.
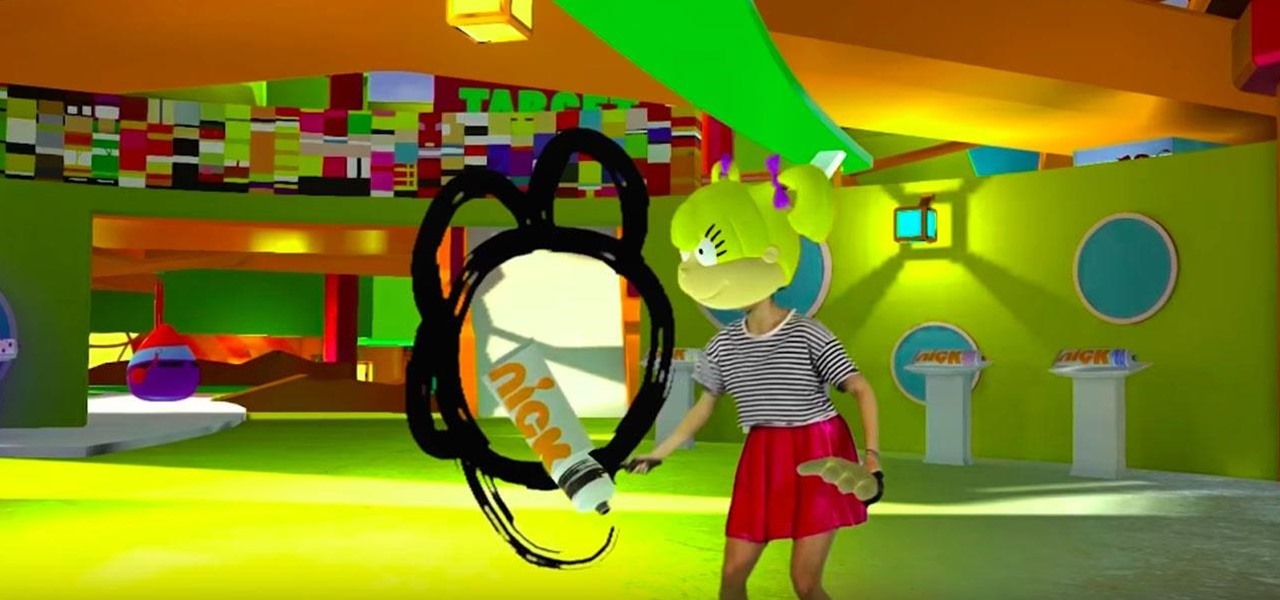
Cable TV network Nickelodeon is looking to break new ground with a new series that will be experienced in virtual and augmented reality.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

A Swedish digital artist has developed an app for the iPhone X that creates mind-bending 3D illusions that correlate to the user's point of view.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

Innotek, an LG subsidiary, announced today (link is in Korean) that it has developed a 15-watt wireless charging module that can recharge a battery three times faster than other wireless chargers available on the market.

While autonomous vehicles are almost assuredly the future of personal transportation, we are likely many years from seeing self-driving cars become as ubiquitous as manually-driven ones, as the auto industry has a myriad of government regulations and other constraints to contend with. Until then, augmented reality is looking like the next big thing in automotive technology.

Samsung Experience isn't for everyone. While it's a far cry from the TouchWiz days, it is still too heavy of a skin for Android purists. But you shouldn't let that dissuade you from a powerful device that checks nearly all other boxes — there are ways to make the Galaxy Note 9's software look and feel almost exactly like stock.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

Coming soon to an Android device near you: Diminished Reality! What's Diminished Reality? A lot like Augmented Reality, really, but with one big difference: Where AR giveth, insinuating virtual elements into a live representation of the real world, Diminished Reality taketh away, hiding actually-existing objects within a live feed.

Much like Mac OS X's Dashboard, which contains Widgets, Windows 7 has developed their own uniqued version, which they call Gadgets. This quick tip video from Microsoft will help you understand where and what Gadgets are, and how to use them to best suit your needs.

More and more, young athletes are developing staph infections. It's a serious topic and every coach or parent should know the basics of staph infections and preventative methods to make sure young athletes stay safe and healthy. Staph infection is MRSA — Methicillin-resistant Staphylococcus aureus. It's a staph bacteria that, overtime, has developed resistance to antibiotics like penicillins (methicillin, dicloxacillin, nafcillin, oxacillin) and cephalosporins. Learn more about staph infectio...

The Survival Podcasting present how to handle leggy or spindly seedlings that have grown too fast. Potted swiss chard seedlings are used as examples. The seedlings are growing well but are a bit floppy or spindly. This happens because the warmth from being started indoors encouraged their fast growth but since there is not enough light for them, they started reaching for the light. A `head space` is developed between the root and the leaves that makes the seedling flop over. A simple trick to...

Another innovative use of augmented reality - we've seen transparent walls, t-shirts that play Rock, Paper, Scissors, an iPhone operated video game drone; and now, a tattoo that comes to life. Just tattoo a simple "barcode", point a webcam at it, and a flying animated dragon will appear, hovering.

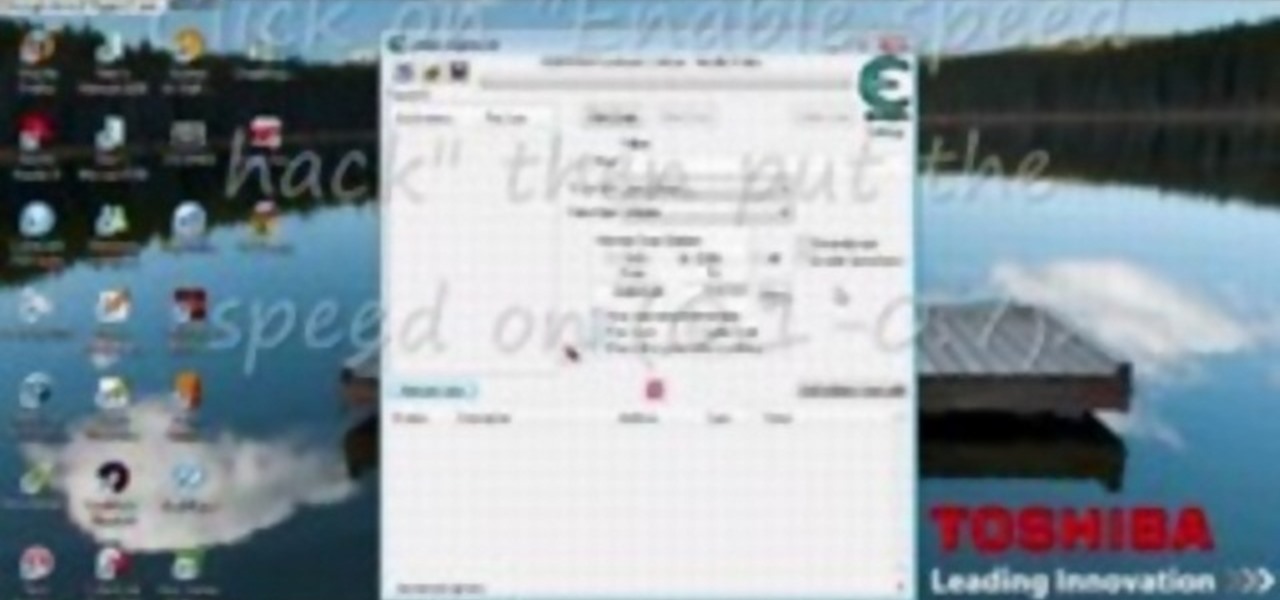
See how to hack the flash game Jetman, which you can play on Facebook. This Jetman cheat will give you top score using Cheat Engine.

It's the end of your first trimester, so your baby has graduated to full-fledged fetus status. You still probably have early pregnancy symptoms like morning sickness, and you may have developed a baby bump. Learn about month 3 of pregnancy in this video!

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

Fans of the friendly neighborhood Spider-Man have yet another way to experience the web-slinger in augmented reality.

Snapchat and Snap Camera aren't the only augmented reality apps available for couples to use on Valentine's Day.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

The thrill and excitement of great tourism generally requires visitors to take part in the country's local fare in person. But Air New Zealand's new augmented reality experience for the Magic Leap One gives visitors an immersive taste of what the country has to offer without ever setting foot in the country.

In the wake of the smoke from the meticulously orchestrated launch of Magic Leap One, the company has revealed what "leapers" can expect to experience via Lumin OS when their devices arrive between now and the end of the year.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

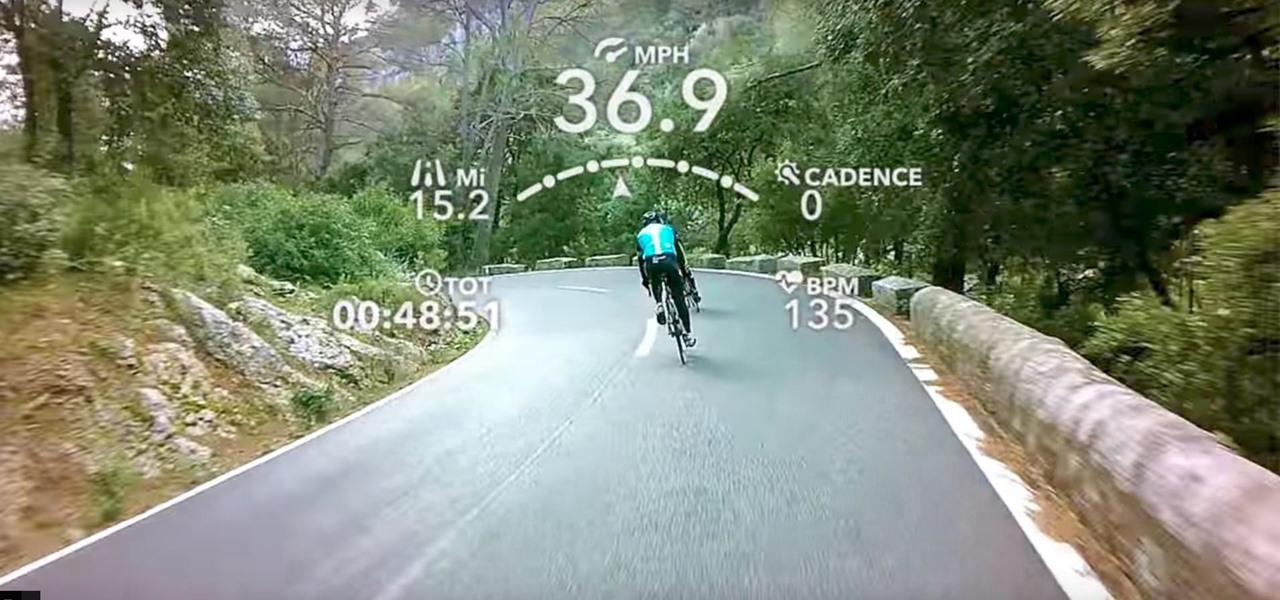
Cyclists of the world, new AR glasses are here to improve your rides. Possessing 2 GB RAM, a quad-core CPU, GPS, 16 to 32 GB of storage, an accelerometer, camera, gyroscope, magnetometer, barometer, Bluetooth, speaker, WiFi, and a mic, these aren't your regular UV-blocking sunglasses. Called the Everysight Raptor AR glasses, these shades project all of the information a cyclist could need to optimize their rides.

Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility.

Could the technology that powers games like Pokémon GO be used for surgery in the near future? Researchers at the University of Maryland think so.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.