
How To: Prune apple tree spurs
In this installment from the Fruitwise Heritage Apples guide to apple pruning, Stephen Hayes goes over the essentials of thinning spur systems, which develop naturally over time and can lead to overcrowding.


In this installment from the Fruitwise Heritage Apples guide to apple pruning, Stephen Hayes goes over the essentials of thinning spur systems, which develop naturally over time and can lead to overcrowding.

Superglue (cyanoacrylate) has many uses. Besides the typical household function of sticking things together, it's used in surgical procedures and even in crime labs to develop unseen fingerprints. Originally marketed as Eastman #910 in 1958, this stuff is sneaky and it goes everywhere if you don't keep an eye on it.

Every once in a while, we need our motorcycle tires to be properly balanced. This video will show you how to Balance a motorcycle tire using a Balancer developed by Scudman.

This video shows how to drift with electric and petrol(nitro)model RC cars. Learn how to develop the right skills and find the right parts to drift with a toy model car.

This video shows how to do a Jiu Jitsu chess drill. This is an excellent way to develop skill and technique.

Grow your psychic and magic skills like a muscle with tips from this training video. This is an introduction or a new way to look at the basics if Wicca. Practice every day.
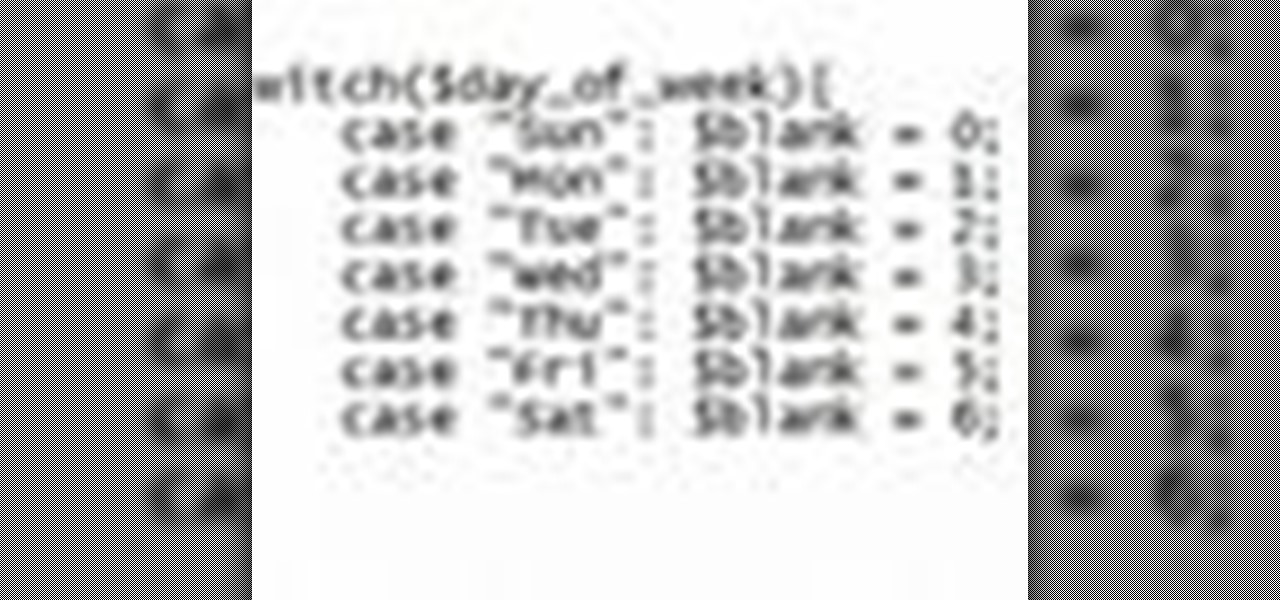
PHP is a script language used for developing web pages. On a website, you can use PHP to create complex organizational systems like a calender or even a reservation system (great for a restaurant's official website).

This 1949 film demonstrates how self-confidence and right attitudes are necessary to good health.

A drill that helps you develop the ability to force your opponent to make a low percentage shot when just the money ball is left on the table.

Learn how to develop your own stroke and improve your technique in pool. Part 1 of 2 - How to Play pool with good stroke technique.

Adolfo explains how to use a punching bag. You can also learn how throw a proper jab. The punching bag is where you develop your strength and learn the combinations.

This free drum lesson includes four simple warm-up exercises you can use to develop your double bass drumming. All of the patterns are designed to sync up your feet with your hands, and to improve your overall footwork.

This Lightroom tutorial is about a feature that a lot of people miss in the Develop module called Auto Sync. It comes in really handy when you’re trying to work on multiple photos at the same time.
Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.

Grandmaster Henrik Danielsen explains the different lines in his F4-System, the Polar Bear System. If you need a new way to play chess, then this is just right for you. See what he has developed in this two-part video.

Learn how to practice your hook shots and develop a soft touch around the basket with these baby jump hook shot basketball drills.

Pound board and put back is a great drill for developing arm strength and lay-ups for post play. This video explains how to practice this basketball drill.

Learn the correct and safe technique for this speed oriented weight lift - the power snatch. Great for developing power in athletes.

Learn a core set of drills that can be used to develop a player's conditioning and strength during the football season.

Learn how to practice head to head tackling - a good drill for developing quick tackling reaction skills.

Learn how to develop good trap blocking technique for playing football.

Learn how to develop good pass blocking to protect your quarterback when playing football.

Learn how to use the fire off drill - a drill that develops conditioning and quickness of the ball, even in the football off-season.

With the carcinogenic additives in today's microwave popcorn, we at HoopajooLabs.com have developed a method of microwaving popcorn that is healthier, cheaper and (in the opinions of our test tasters) tastier. A delicious and healthy treat for about $0.10 that just about anyone can make. Great for students!

Here we introduce two easy to learn rhythms for the didgeridoo student. There is also some advice on developing your own rhythms too!

This video shows you how to perform the full kata using the kuwa (hoe) as a weapon, a technique primarily developed in Okinawa.

Matt, the Shirtless Apprentice, demonstrates how to create dramatic lighting effects on a budget. This episode will help you to develop control of your audiences attention.

Justin Cantor discusses how to develop a good tone on the cello. Several techniques to get a range of sounds are discussed along with the variables, bow speed, pressure and contact point.

Katherine and Kimberly Corp show you how to do the Half Roll Down with Obliques pilates exercise. This exercise is used for strengthening your core and helps develop the muscles to do more advanced pilates exercises like the Hip Twist and Teaser.

Katherine and Kimberly Corp show you how to do the Long Plank Series pilates exercise. This exercise is used for developing ab and lower back strength.

Katherine and Kimberly Corp show you how to do the short plank with leg lifts pilates exercise in this how-to video. This exercise is used to develop core stability and balance as well as build a strong foundation for proper push-ups.

Plants dominate the living landscape around us. Learning about this essential part of ecosystems by collecting and identifying plants should be a part of any life sciences curriculum. Designed to support the Plant Press project at Hila Science Camp, this video discusses collecting and classifying plants and the importance of the classification system developed by Carl Linnaeus.

Learn to do a parkour-style backflip while balanced on a rail or ledge. A good backflip can be the foundation of developing style in your free running. See how it's done in real time and slow motion.
Final Cut Pro has a lot of excellent options for working with sound, but Sountrack Pro was developed specifically for working with sound, and can often fix problems that Final Cut Pro can't. This tutorial will explain how to use Sountrack Pro with Final Cut Pro.

This exercise is an M hum vocal warm up. Squeeze your cheeks together, focus on an open throat and relaxed jaw with an open mouth. Sing through your basic warm up exercises. A great way to develop your vocal tone and warm up.

Lars discusses an organic fire ant control method developed at Texas A&M university. Lars stresses on the safety and environmentally friendly factors these products practice.

A new survey of game developers paints a somewhat less than rosy future for augmented reality gaming, but there's still some hope for its long-term prospects.
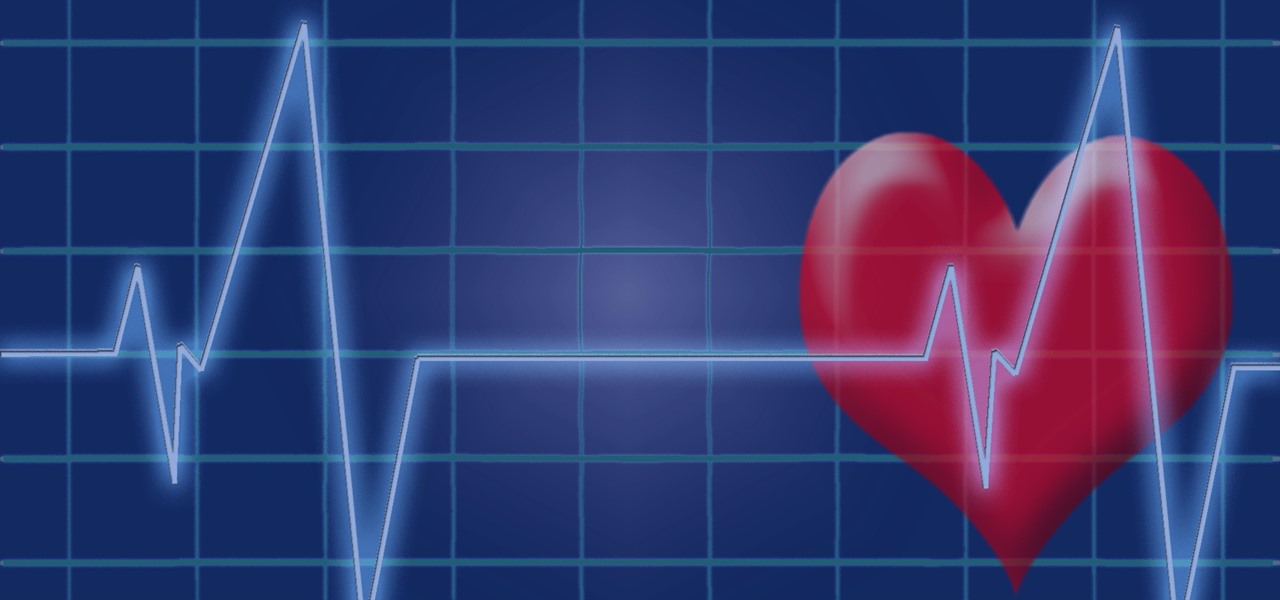
Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the blood, diabetes, and high blood pressure.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.