Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

HIV infections persist despite treatment that successfully decreases viral blood levels to the point where doctors can't detect the virus. But that doesn't mean the person is cured. The virus hides in the body, not replicating, just waiting for a chance to jump out of the shadows and reemerge.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.
Dengue fever is a danger to anyone living or visiting tropical or subtropical regions. It can be hard to detect the infection in its earliest and most treatable phase, especially in children. Luckily, new research highlights better techniques for triaging the disease in infected children with more severe symptoms, potentially saving lives.

Could your fever, body aches, cough, and sore throat be the flu? Soon, finding out may not involve a trip to the doctor.

An innovative new wound dressing has been developed by a research team at Lodz University of Technology in Poland that uses crustacean shells to create a bandage that packs an antimicrobial punch — and even more potential to help solve a global problem.

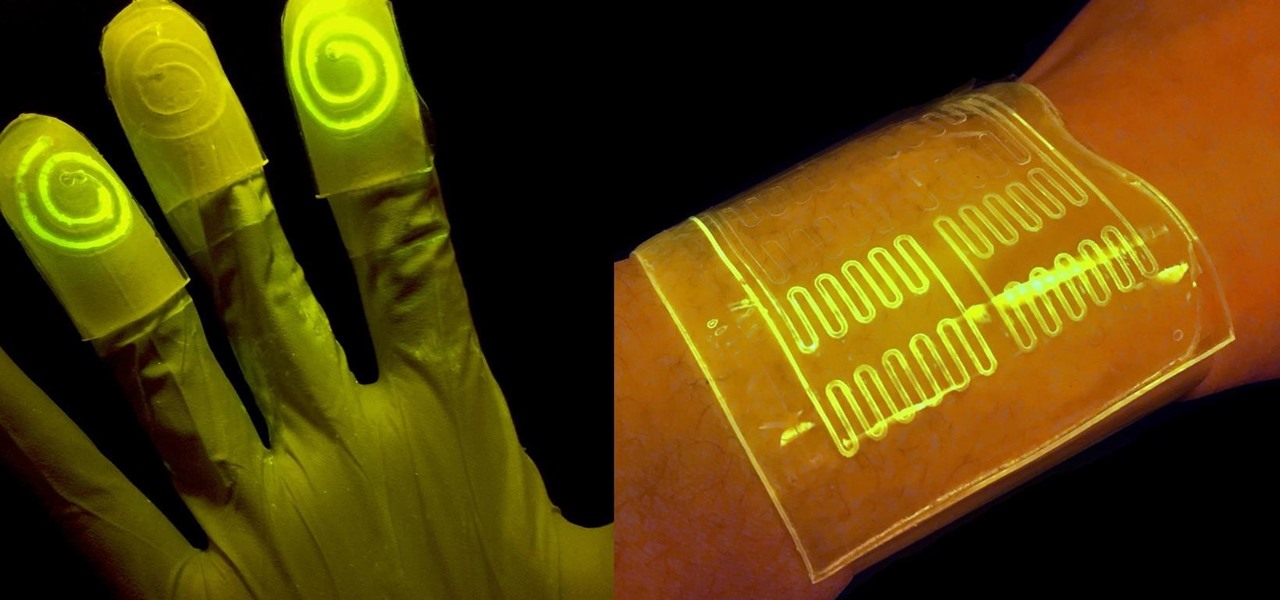
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

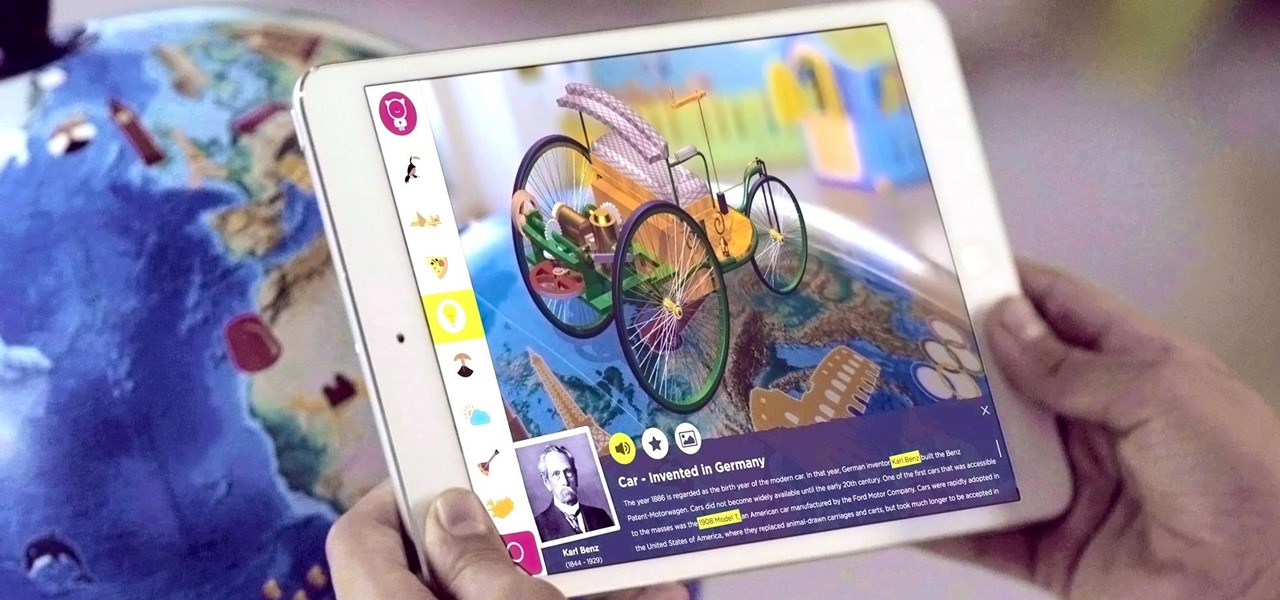
Globes used to be standard in households, usurped in many ways by modern mobile and desktop applications. But one company believes they can upgrade the globe for the 21st century.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

How to instantly bond with anyone and persuade them

In this in depth, four part series learn how to draw a cartoon dog. The adorable puppy you will be learning to draw is top notch and would fit in nicely in any children's book or comic strip.

This video shows how to properly set up a green screen, to set up the screen we are taking into account this four factors:

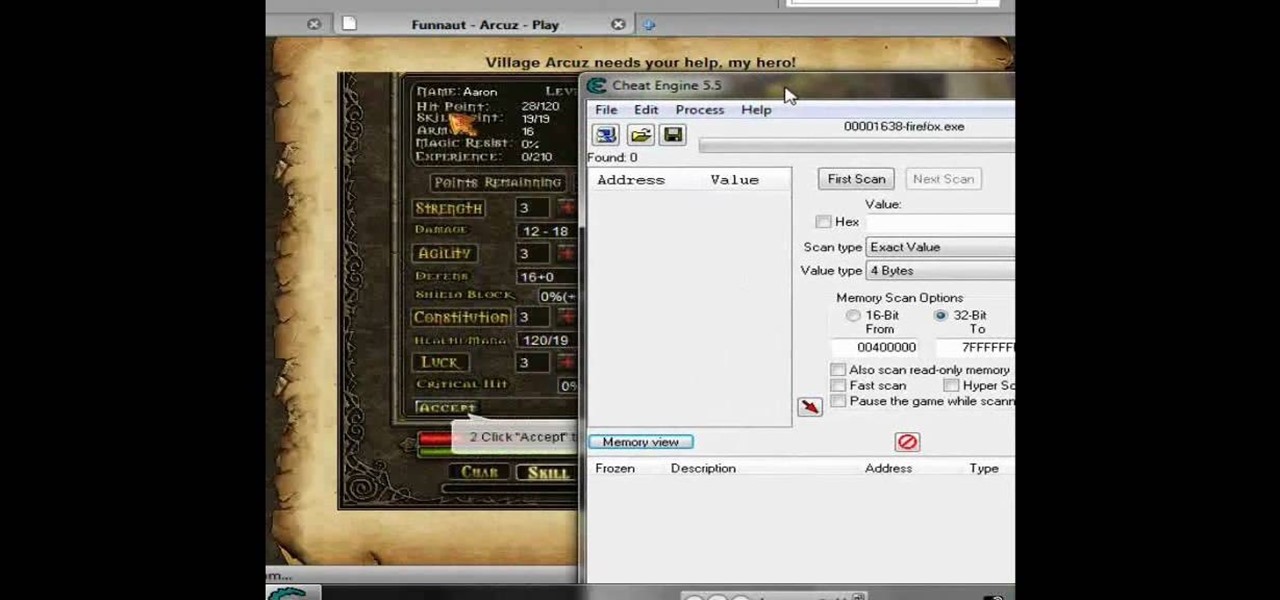
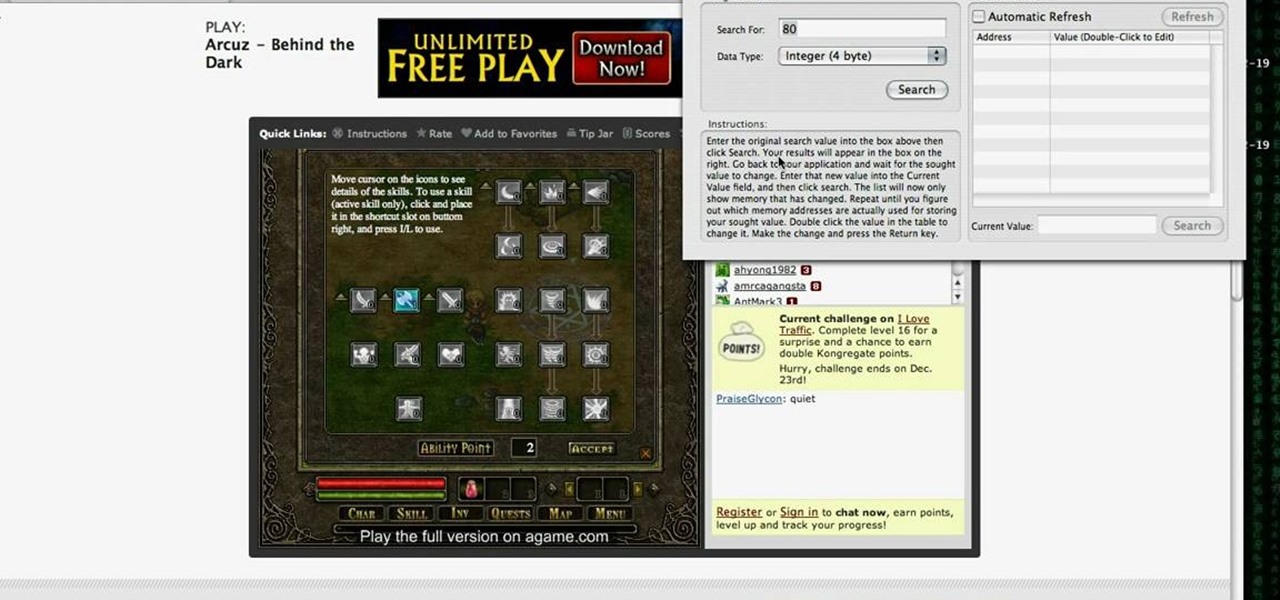
Play Acruz online and hack it, too! With this handy hack, you can cheat your stat points, levels, and money. You just need Cheat Engine.

If you want more money, character points, and skill points on Arcuz online, then this video should solve your dilemma. Just use Cheat Engine.

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Nope, you don't need Cheat Engine to hack into Icy Tower, but this handy dandy controller is just as good, if not better. Hack Icy Tower like you've never hacked before.

Without looking, peeking, or even cheating, you will be able to figure out who will win in a virtual game of rock-paper-scissors.

Why make a flip book? Because all animation – even stick-figure Flash animation and multilayered, highly technical 3-D effects – is built on, and can benefit from, the basics of the craft first developed by artists working at the beginning of the last century. And while fancy computer programs are nice, you can teach yourself these basics using nothing more than a pad of paper and a pen, and replay them over and over without any extra technology needed.

Check out this strength trick from Revision3, Brian Brushwood and Scam School. We're back with another dirty trick, designed to teach you how to FAKE your way into (almost) duplicating the feats of the world's strongest men.

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...