One of the most rewarding things about jailbreaking is theming. Unlike Android, iOS doesn't allow you to make small changes to certain aspects like the icons or the lock screen, so jailbreaking facilitates the ability to make some of these desired changes happen.

Finding the right mix of custom ROM, kernel, and tweaks for my OnePlus One has left me flashing every new release I come across. This has led to many hours going through thread after thread trying to find the latest and best software out there for my phone. While I do enjoy the hunt, I would rather have a centralized location that covers all my bases, so that's why I have started using OnePlus One, an app by Alex Inthiaano.

Did you know that your face shows others how much alcohol you drink? Whether you've never had a sip of booze with those around you or you're known as the party animal of the group, the genes that shape your appearance also show others just how much you enjoy liquor. Pinpointing the big drinker in any setting is easy to determine: you just need to make eye contact.
When I watched the first Cincinnati Bengals edition of the HBO series Hard Knocks back in 2009, among wide receiver Chad Johnson's bravado and attention-grabbing antics was a segment on backup quarterback Jordan Palmer and his newly-developed app, which was still in its infancy. Six years later, I've revisited his creation and have to admit—it's pretty damn useful.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

You can find hundreds, if not thousands, of complaints about Wi-Fi performance issues with iOS 8 across all Apple devices. Even I had the issue on my iPhone 5S. The Wi-Fi connection on my router was strong, but I was getting extremely slow speeds. So slow, that I would resort to using LTE instead of Wi-Fi, which in turn led to going over my monthly data allotment.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

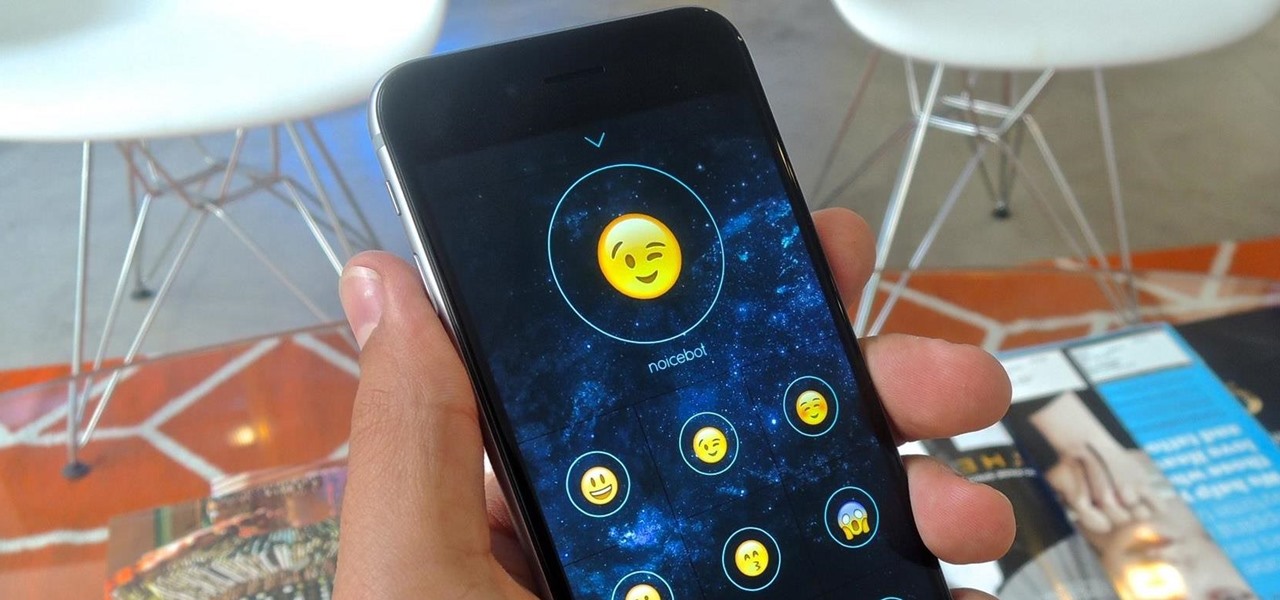
As messaging and texting have all but replaced the need to actually call someone, emojis have seemingly replaced our need to type out text. With a simple emoji, you can relay emotions like "I don't feel very well" or "I love you" quickly and easily, knowing that the other party will instantly know what you're feeling.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

I'm always looking for the best apps and services for my Android, and that means sticking strictly to the Google Play Store is a no-go. If you're like me and tend to install a lot of APKs (application files), you're probably tired of seeing the "Install" confirmation that always pops up.

Restoring data is not always the easiest thing to do when you flash a new ROM on Android. Google can back up your contacts and Wi-Fi passwords, and various tools can back up your apps and data, but the rest is usually lost in-between ROM flashes. This leads to a lot of wasted time getting everything back into place, and it'll take a long time before your new ROM feels like "home" again.

Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Just when you begin to doubt the future of humanity, advances in ice cream scooping science continue to develop. Yumi showed you some super-cool ice cream hacks just in time for summer, and we've already discussed how to use a knife to slice ice cream when it's too hard to scoop.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

Most of you probably spread ketchup all over hamburgers and fries. Some of you may even drink it straight. But did you know that tame (and slightly addictive) condiment in your fridge is also a powerful cleaning agent?

Fact: we live in a world where social media dictates our behaviors and shapes our perceptions. Maybe some of us are addicted more than others, but most of society uses some type of social media, whether it's Twitter, Instagram, Facebook, Snapchat , or something new that I've never heard of.

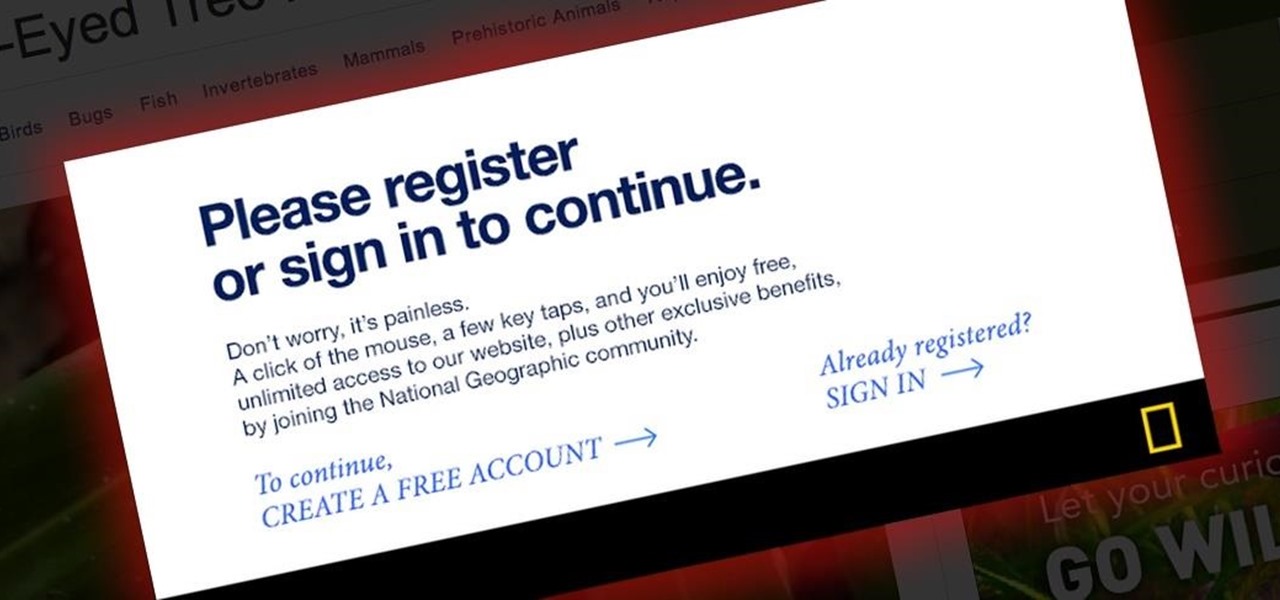
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

The old "my battery is dead" excuse for not calling your mother may soon be a thing of the past. A team from the Korea Advanced Institute of Science and Technology (KAIST), led by Professor Jo Byeong-jin, has developed a "wearable thermo-element" that can be built into clothing to power your electronic devices. The science behind the innovation converts body heat (thermal energy) into usable electric energy. Made with lightweight glass fiber, this small thermo-element strip can produce about ...

The first thing I do when I wake up in the morning is run to the kitchen to make coffee, and I know I'm not the only one. According to a survey by the National Coffee Association (yes, there's such a thing), 83% of Americans drink coffee, and I'd bet most of that consumption happens in the morning.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

If you've tried watching a video that requires Adobe Flash Player installed on your Samsung Galaxy Note 2, then you're probably well acquainted with the "Flash Player is not installed" message. If you try tapping the deceiving Install Flash Player button it takes you directly to the Adobe website, where you're greeted with a message saying:

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

In early 2000, at the age of 19, Noah Kalina began taking a photo of himself with the same facial expression—every single day. Six years and over 2,000 photographs later, Kalina turned his project into a time-lapsed montage on YouTube. In just one day, his video received over a million views.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Samsung does a good job of making their devices fairly open, and the Galaxy S3 is no different. There are numerous way to root a device, but sometimes the jargon and steps can be a little intimidating for new rooters, and even pro rooters.

If you've ever listened to your loved ones sing in the shower or watched a few minutes of American Idol, you would think that the majority of the population is tone deaf. In reality, only about 4 percent of the world's population suffers from tone deafness, or the inability to distinguish between different pitches. Che Guerava, Charles Darwin, and Ulysses S. Grant were all tone deaf.

There's a lot going for the Samsung Galaxy Note 2—smart screen rotation, huge HD display, great rear camera—which makes it an awesome device for reading, watching videos, and taking pics. But all of those luxuries will end up hogging up your internal memory, which is one of the few things the Note 2 could use some help in. The device comes with 16 to 64 GB of internal storage, depending on your model, with the option of adding a microSD card for more space. Only problem is, everything automat...

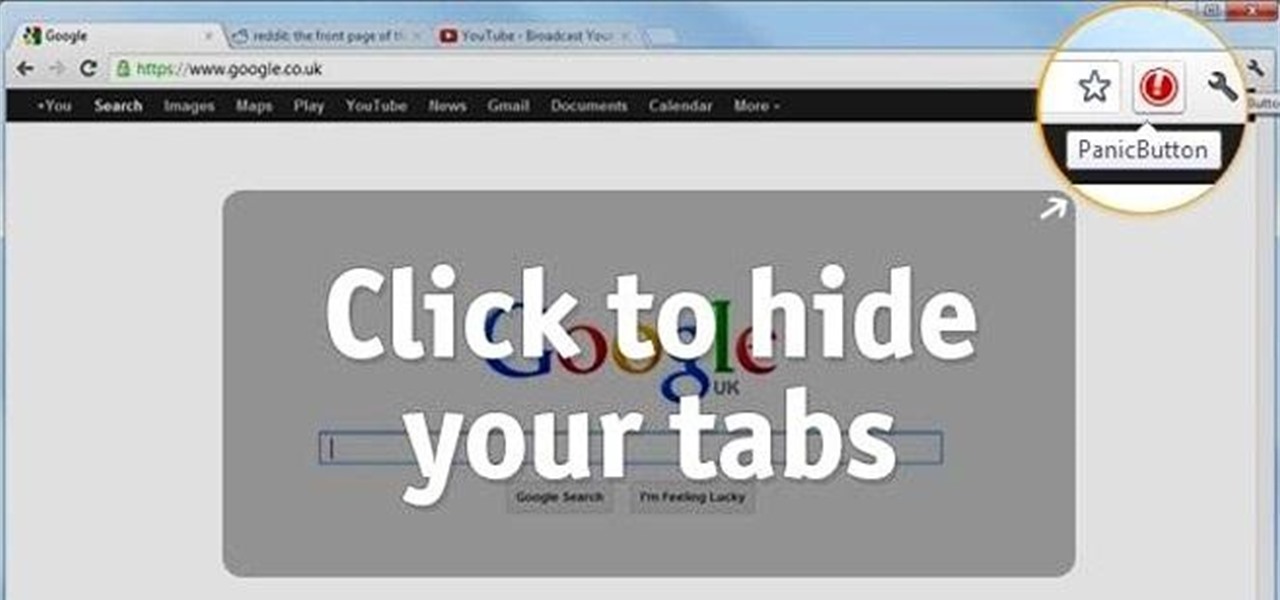
At some point or another, we've all been in that awful situation when someone walks up behind you while you're looking at something you don't want them to see. Whether you're tweeting during class, shopping for gifts online, or looking at something a little more NSFW, there are times when it would be nice to just click a button and have all your open tabs disappear.