
How To: Use BeEF and JavaScript for Reconnaissance
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.


Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.
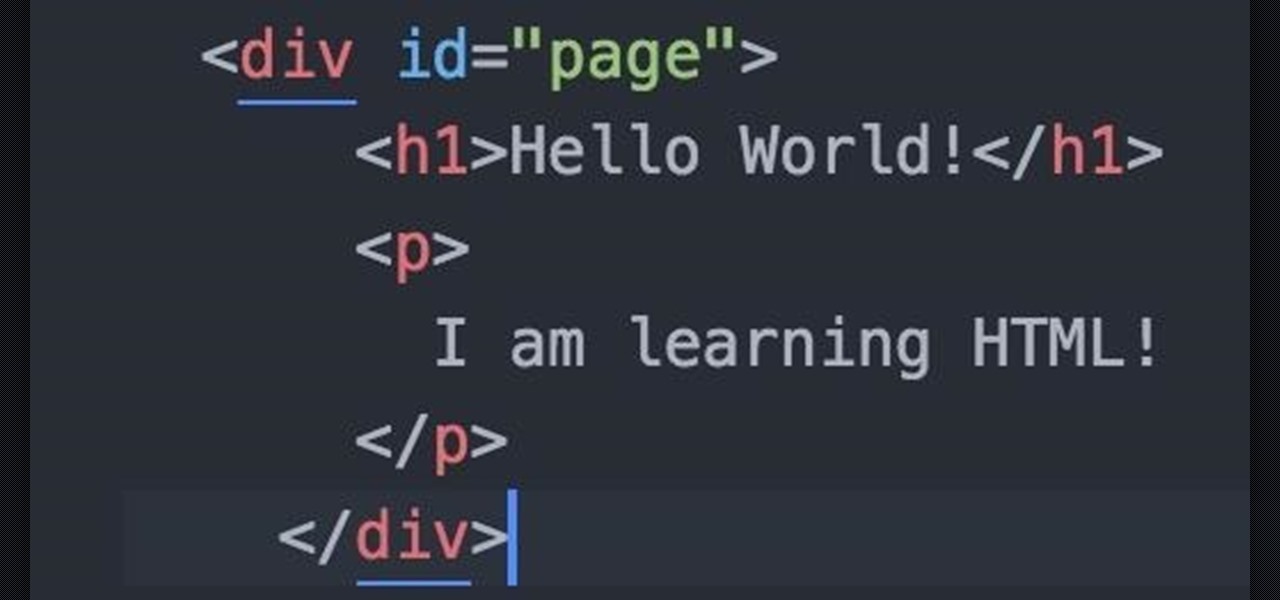
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.
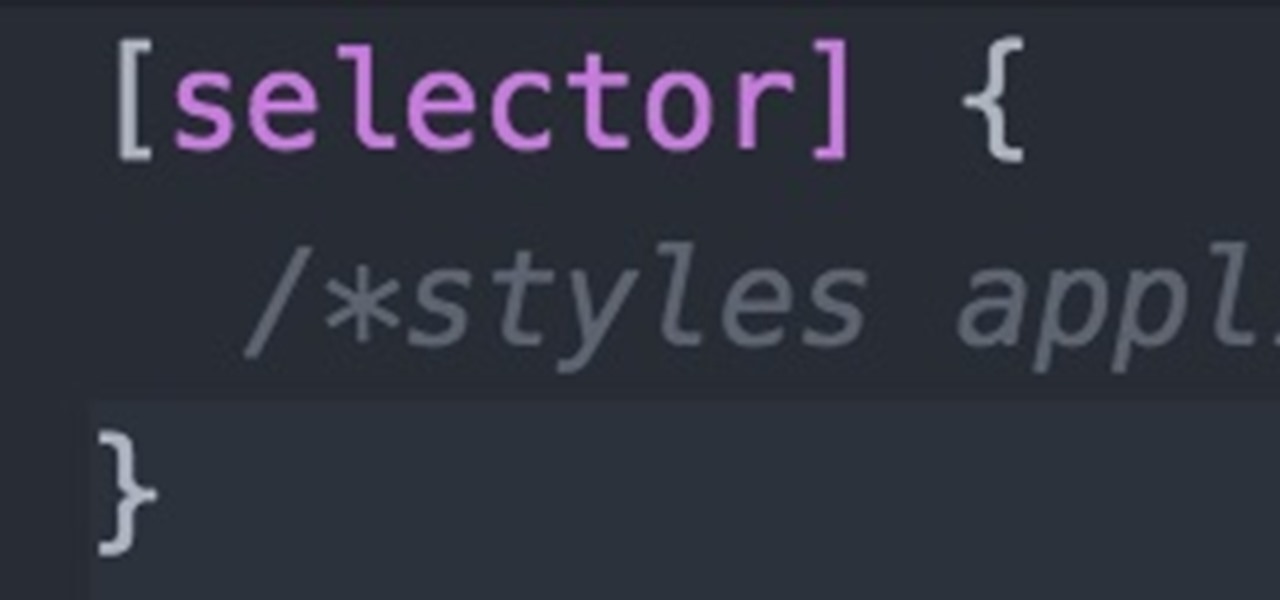
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.
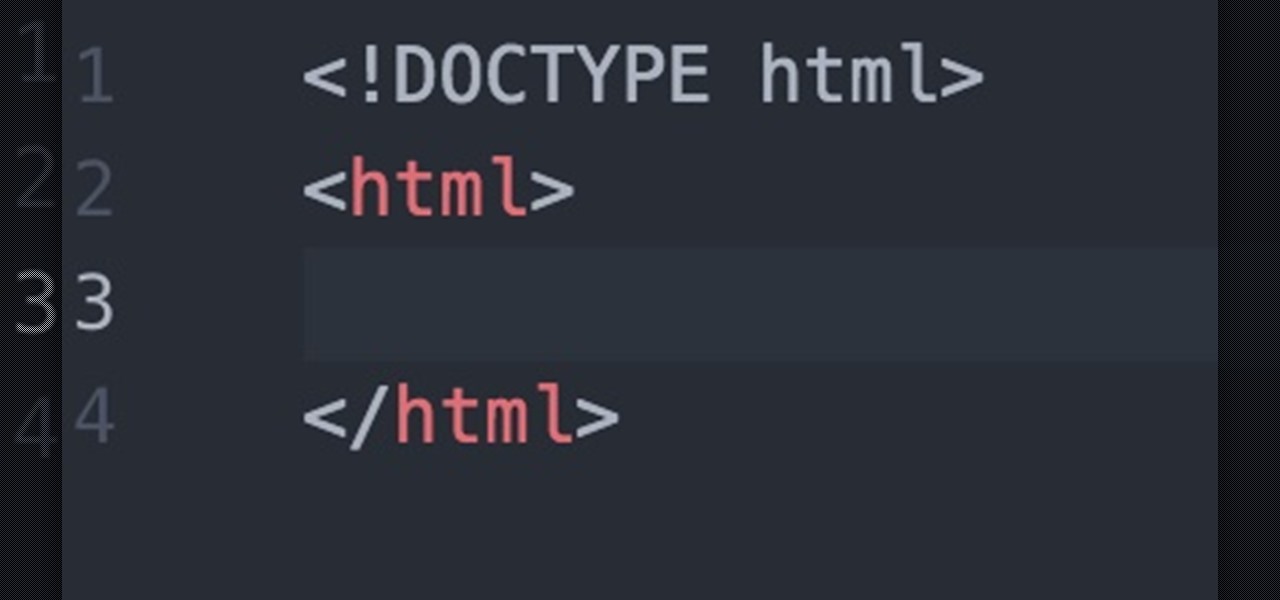
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.
Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

Dropping upwards of $60 on a new game can really break the bank, and being a struggling college student leaves me having to decide whether to pick up the latest title or, you know, eat. But often my more primitive urges win out, meaning the only way to enjoy the latest and greatest games are vicariously, using increasingly-popular live streams.

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

With an Android device, you can replace almost any default app with a third-party offering. Don't like your home screen app? Replace it. Tired of the text messaging interface? Upgrade it. The same can be said for Android's lock screen. But while many third-party lock screen apps are available, so far, only one has been designed with the Samsung Galaxy S6 and its fingerprint scanner in mind.

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

It's that time of year again, folks. Each fall, Google debuts a new device alongside the latest iteration of its mobile operating system—but this year marked the release of three new Nexus gadgets.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.
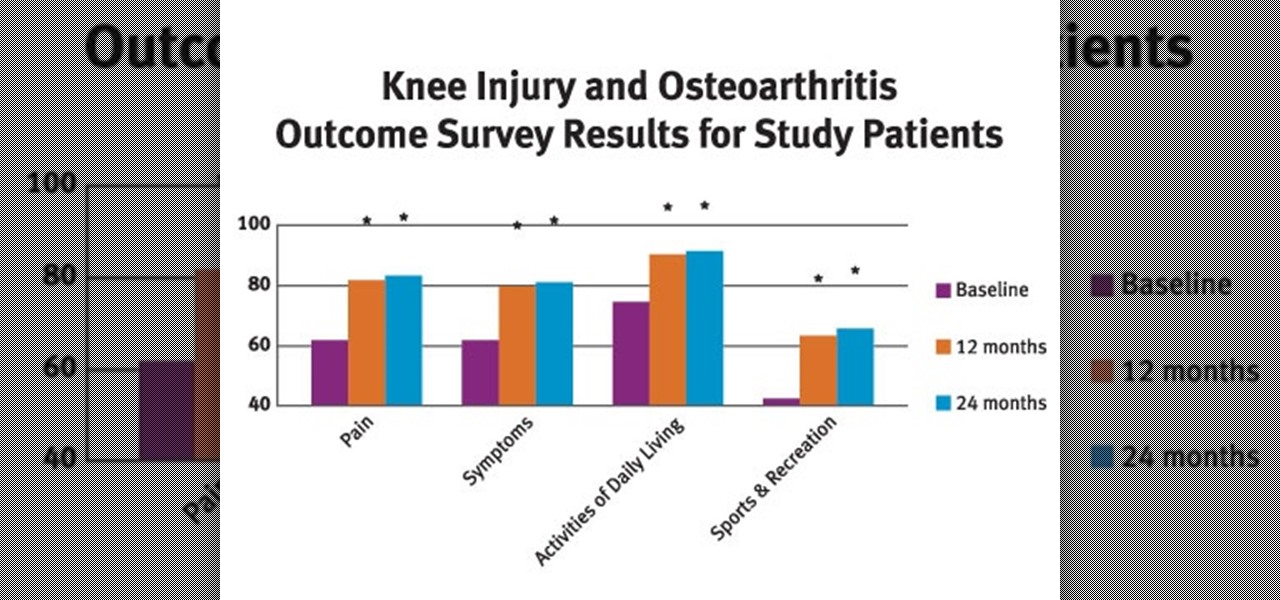
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

When it comes to theming your Android device, it's the little touches that count the most. That's why developer SArnab created the Android Theme Engine, an Xposed Module to theme those hard-to-reach corners of the Android System that often go untouched with other themes.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.
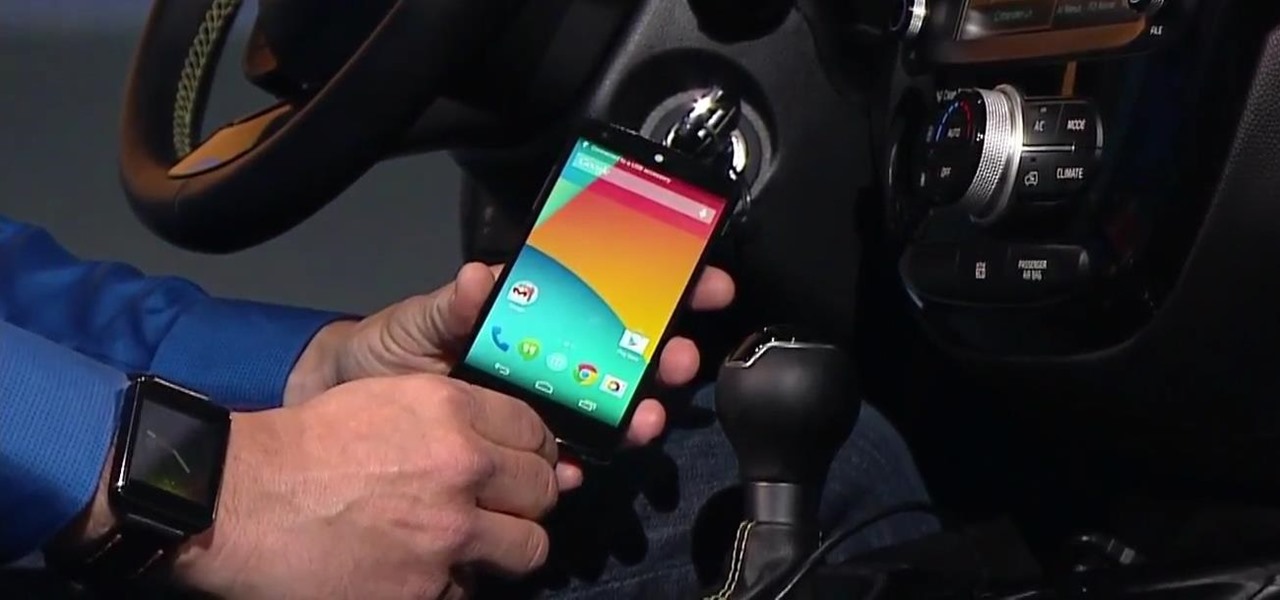
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.
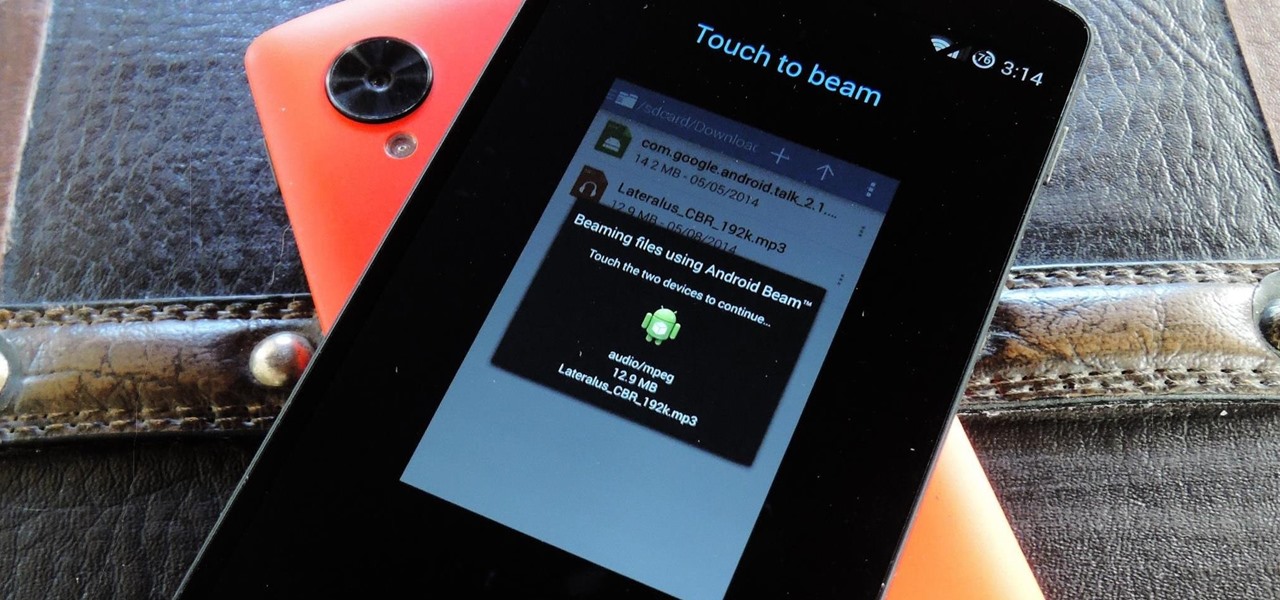
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

Recently, Sprint announced a partnership with Harman Kardon to deliver exclusive sound FX technology to their variant of the HTC One M8. The joint effort between the two companies is both to entice customers to switch to Sprint as well as improve the overall audio quality coming from the already extraordinary BoomSound speakers. But while this is great for new and existing Sprint customers, it does leave the rest of us out in the cold.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Android developer Roman Nurik, famous for his open-source DashClock widget, recently released his latest creation, Muzei Live Wallpaper. Now, live wallpapers (LWPs) may not seem like a huge deal as far as mods go, but they're a great way to add flair to your device—and Muzei adds it in spades.

I'm one of those types of people who waits until the very last minute to find a Halloween costume, and thanks to last year's attempt at buying one at a local costume shop the day before Halloween, I will just settle for the things I have lying around in my house from now until eternity. It's like Black Friday chaos, only with more gropers.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

The biggest complaint I have with my Nexus 7 is the lack of support for different types of media files. I have a lot of movies and music that I've downloaded off the web, in many different formats, and I want them on my tablet.

Video: . Video: .

Here at WonderHowTo, we've been following the Minecraft LEGO set for quite some time, through its development on LEGO CUUSOO (a LEGO site where users can submit ideas for LEGO sets) to its eventual implementation.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

SCRABBLE was invented by Alfred Mosher Butts, an architect in New York, in an attempt to make a word game that combined anagrams and crosswords, which involved chance, luck and a great degree of skill. Together, Butts and game-loving entrepreneur James Brunot, refined the game and made the games by hand, stamping letters on wooden tiles on at a time. They eventually came up with the name SCRABBLE, which means "to grope frantically."