Being able to run mobile apps on a computer is nothing new. Maybe you don't have a mobile device, or maybe you just like seeing the apps on a larger screen. Whatever the reason, with programs like Bluestacks, you can use your laptop to Instagram, play Angry Birds, and run countless other apps made for smartphones.

As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

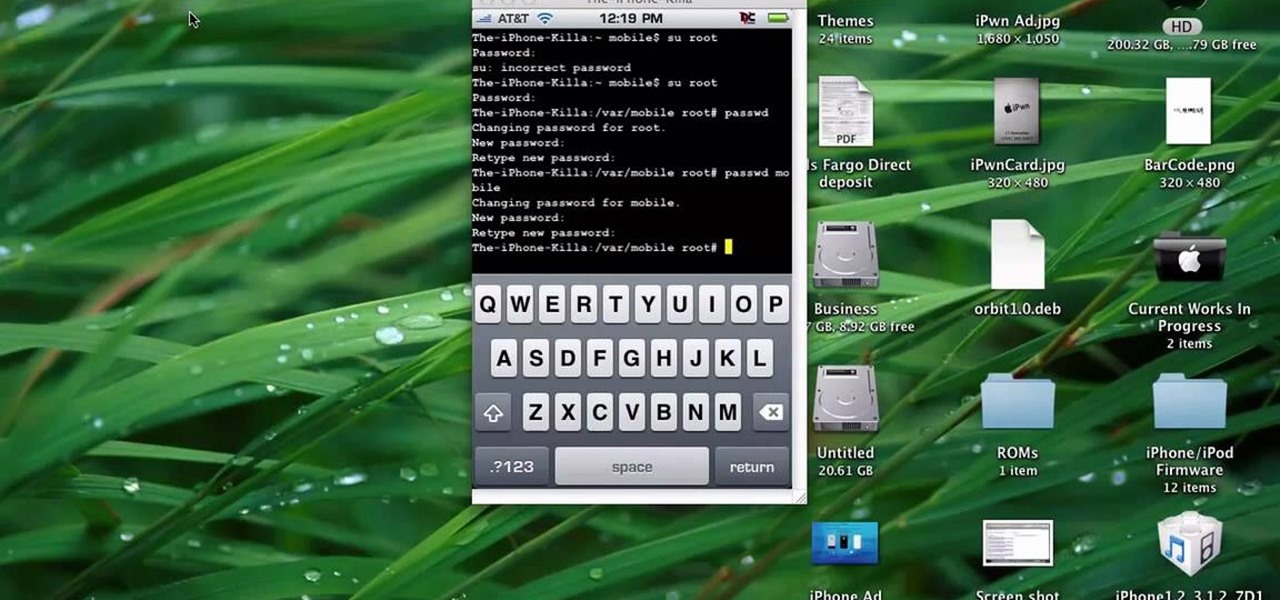
There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.
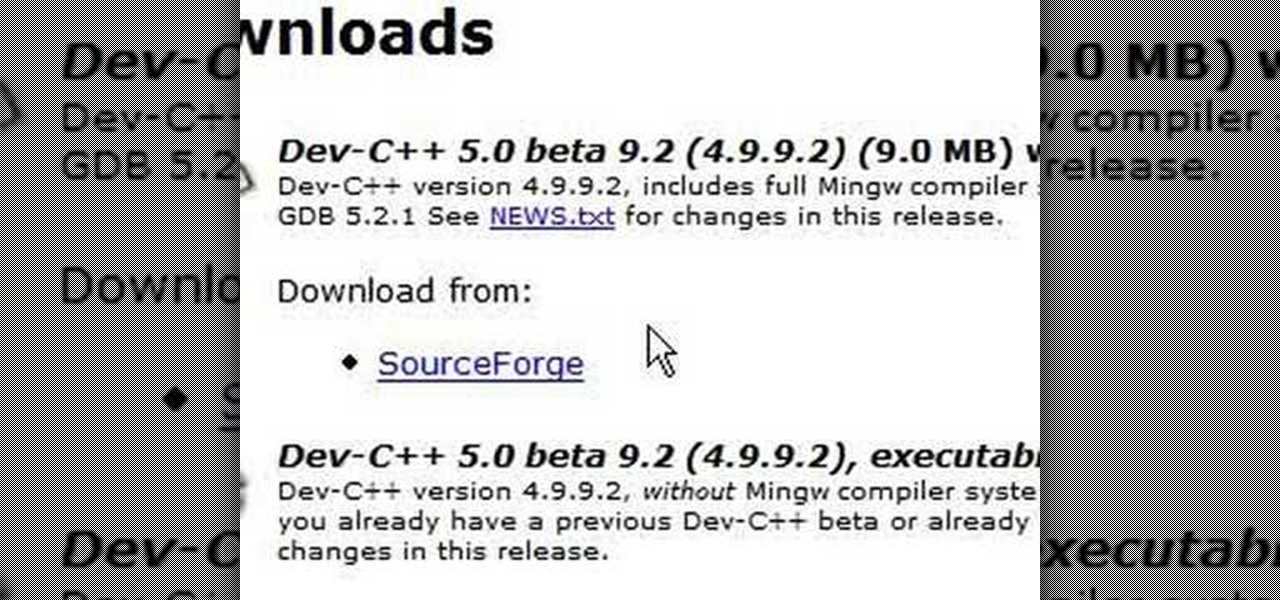
C++ is one the most powerful and fundamental languages commonly used to computer programming. If you've ever wanted to get started using, then please watch this video series. It's 29 parts will teach you everything you need to know about coding in this magnificent language, allowing you to create your own fairly full-featured computer programs. Honestly, if you have any questions about C++ at all, or want to learn it and don't think that you can because you've tried programming before and fai...
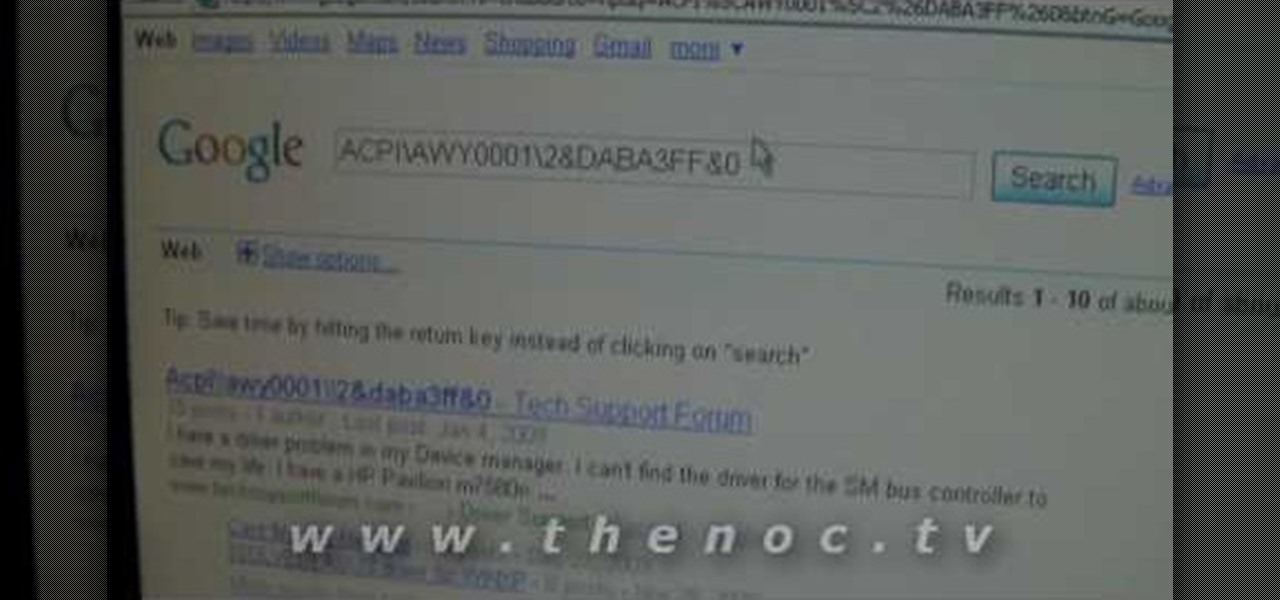
This video narrates and explains how to figure out how to install an unknown device using the device manager. The first step is to access the device manager through the control panel/system. Once in device manager you must select the show devices options. Once the device menu is visible you then find the unknown device section and copy the name of the device driver. The next step is to open Google search engine and paste the unknown device ID name. After the search is complete you will see ma...

Whether you're the proud owner of a brand new Apple iPad or are merely considering picking one up, you're sure to appreciate this video tutorial, which presents a complete overview of how to use the mobile device's user interface. For more information, including detailed, step-by-step instructions, watch this iPad user's guide.

HP TouchSmart PC is a powerful computer with various features. You can use you PC to connect to other hardware devices like printer, scanner etc. A hardware device might not even work with you computer because the connecting cables might not match. So if you want a printer to connect to your computer you will need a USB connector. If your printer has a normal pin connector, you cannot work with it directly. In this case the other option is to print wireless, provided your printer supports it....

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

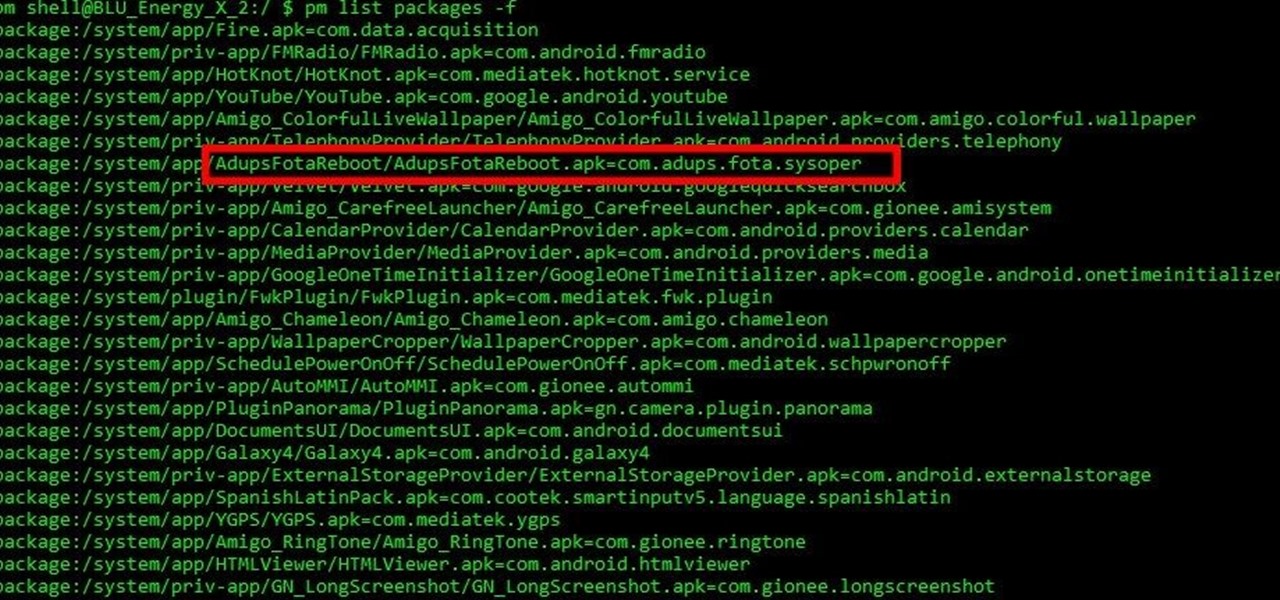
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

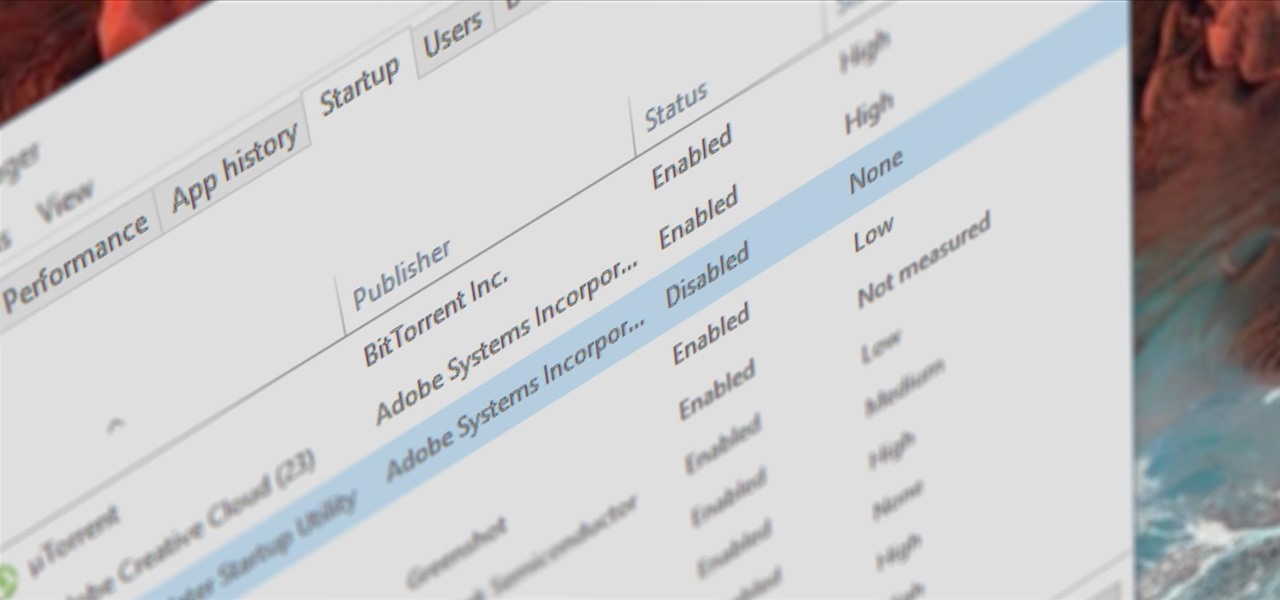
Microsoft had boasted that Windows 10 starts up as much as 30% faster than Windows 7 would on the same device, but depending on your setup, this can still be incredibly slow. Many programs choose to start up alongside Windows, which can make booting your PC quite a hassle.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the power button mechanism, free of charge, for certain iPhone 5 models.

Currently in its alpha stage, Facebook has pushed forward a redesigned mobile app for Android users that provides a flat user interface and rearranged navigation tools.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

For being an inexpensive tablet, the Nexus 7 packs a 1,280 x 800 pixel resolution into a relatively small display, offering a very sharp-looking 216 pixels per inch. What does that mean? It's one of the best e-readers on the market.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

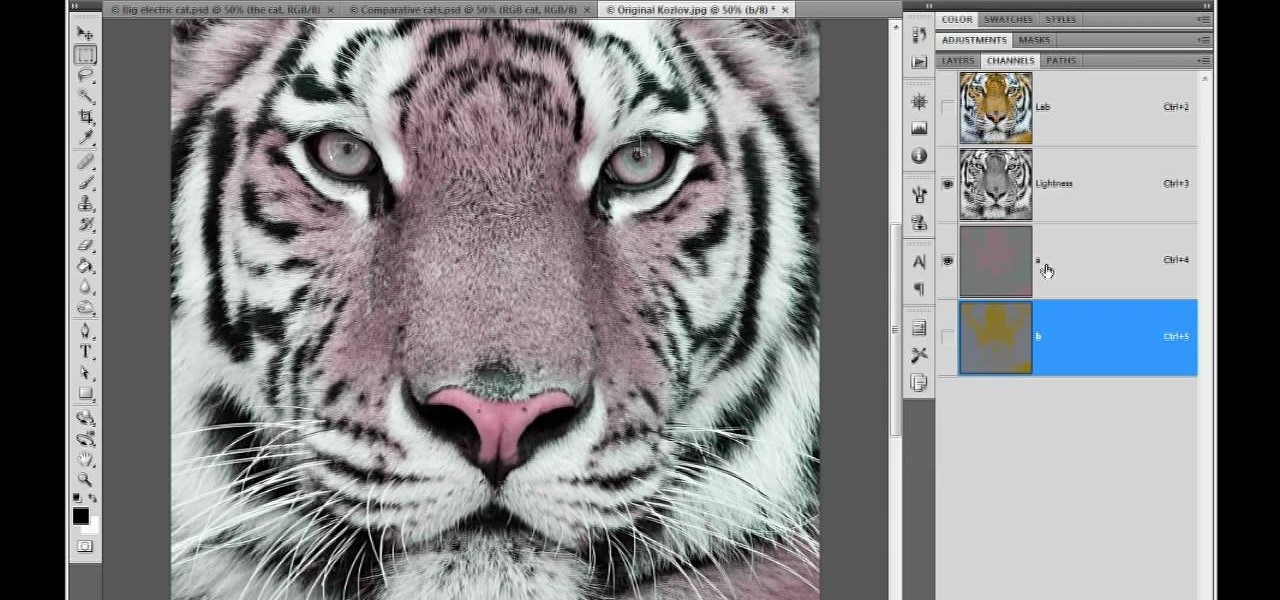
Photoshop doesn't just support multiple color spaces, it supports infinite variations on the device-dependent ones. You can open an RGB photo, process it in Lab, and output it to CMYK, with certainty that the conversions will work. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more informat...

In this video tutorial, viewers learn how to import, manage and export 16:9 footage in Adobe Final Cut Pro. Begin by opening the Log and Capture.Then configure the Logging, Clip Settings and Control Settings. For the Control Settings, set the Device Control as Fire Wire NTSC and the Capture/Input as DV NTSC 48 kHz Anamorphic. Then scroll through the sequence setting of the footage and check Anamorphic. To export, click on File and select Export. Click in Options set the the size to Compressor...

The Droid Bionic was rooted the same day it came out with the one click method used to root the Droid 3. This tutorial will walk you through the process of rooting Motorola's Android device so that you can unlock the full potential of Verizon Wireless's flagship device.

If you haven't bought a new iPhone or iPod Touch since the 3G and 2G models of those respective devices, iOS 4 has probably been a major problem for you. It slows down those devices mightily, but there is a solution. This video will show you how to adjust some basic settings in your phone or MP3 player to make it run the new operating system faster and allow you to keep enjoying you device as you have for years.

In this how-to video, you will learn how to perform basic circuit bending. You will need a screw driver, alligator clips, solder, a soldering iron, wires, a wire stripper, a button or switch, and a drill. Open up the device you want to circuit bend. Once the side of the board with the solder points is exposed, take your alligator clips and find two solder points that make an interesting noise. Be careful of areas where the battery is connected, as you might shock your self or destroy the devi...

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

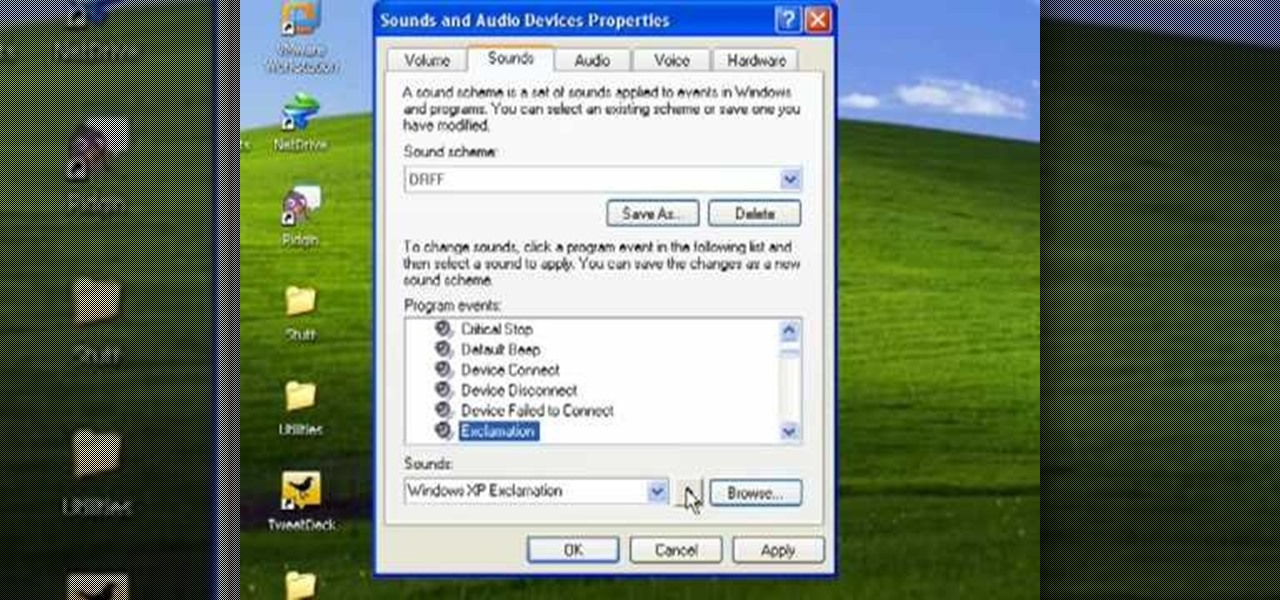
Butterscotch is here to help you create a sound profile in Windows. First, go to "start", then click "settings", and then "control panel". When the "control panel" menu comes up go to and double click on "Sounds and Audio devices". Once you have that window up, click on the "sounds" tab. After doing so you'll see a menu called "program events" which is all the sounds that Windows uses. You can highlight one of the titles and click the play button on the bottom to preview the sound. But in thi...

Bill Myers shows us how to record live video direct to your computer from your camcorder. You will need: long firewire cable, camcorder with firewire output, computer. Procedure: Connect one end of the firewire cable to your camcorder, then connect the other end to your computer. Start your video editing program. Turn the audio down on your speakers to avoid feedback. Turn your camcorder on then check the capture option in your screen. Record the video then hit the stop button when you're fin...

This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Check out these general tips to get the most out of your hurling training program.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.