You can easily set up your devices in studio one. Run the studio one. You should now on the start page of the studio one. There you can see the recent files, news feed etc. Now studio one automatically select an audio device
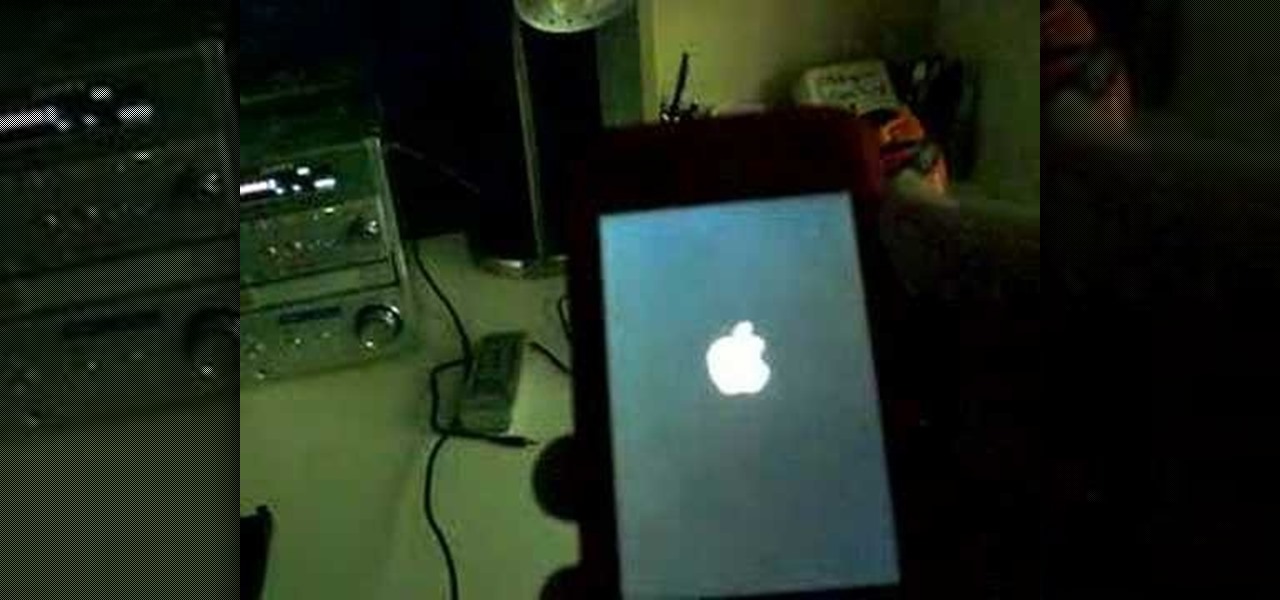
Jeremy teaches us how to unbrick an iPod touch in this tutorial. First, hold the bottom button and top button simultaneously until the device shuts off. Hold these together until the logo comes on the device, then let go. The Apple logo will stay around for several seconds, maybe even minutes. Once the logo has disappeared, your regular screen should come back on the device. Now you will be able to resume using your device. If the logo stays on the screen for a long time, don't get worried, i...
In this video tutorial, viewers learn how to boost the volume on an iPod Touch or iPhone. Begin by opening the iTunes program and select all the songs in your library. To select all the songs, simply press the Control and A keys. Then right-click and select Get Info. When a window pops up, click on Yes. Now click on the Options tab and set the Volume Adjustment to 100%. Finish by click OK. This video will benefit those viewers who have an iPod device, and would like to learn how to boost the ...
DO you have an iPod Touch, but not know how to use Bluetooth devices with it? This video is here to show you the way. It features a simple demonstration of how to connect a Bluetooth device to an iPod touch using it's internal menus. Wireless headphone, playing your music in your car, and all other sorts of Bluetooth functions are now part of your iPod Touch's repertoire!

Where do you get all of those cool apps for you Android mobile device? There's one place to go to find all of the latest apps for your mobile phone, so what is it? Best Buy has answers. The Best Buy Mobile team explains how simple it is to add a contact to your Android enabled cell phone.
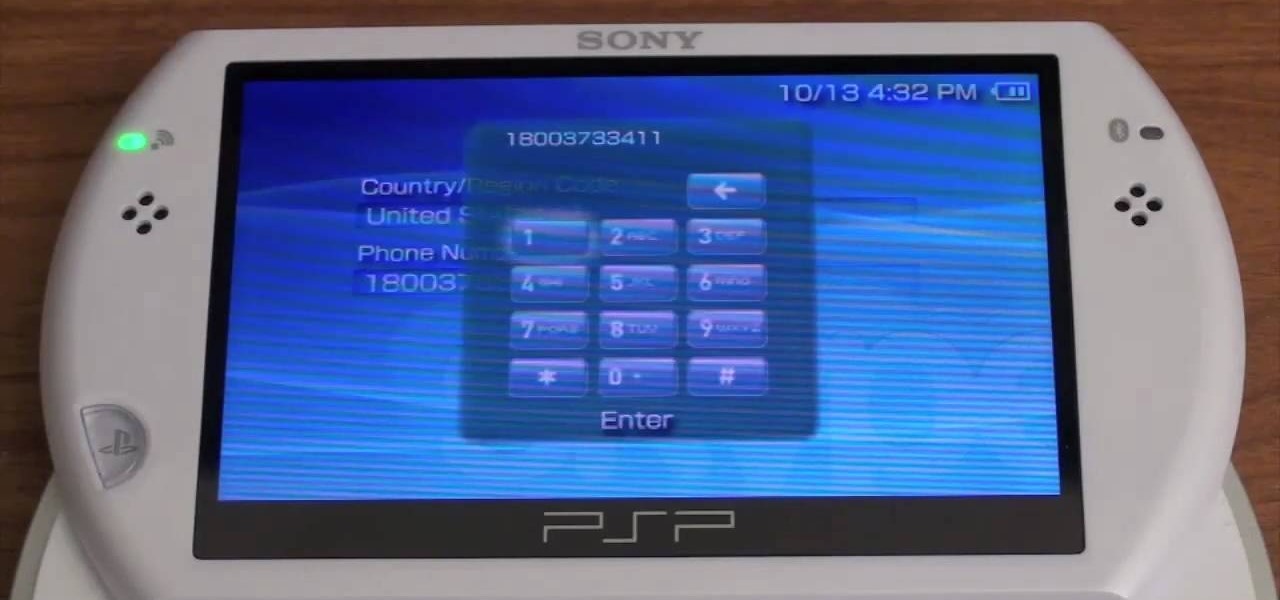
The materials you will need to do this are a "PSP GO" and the downloaded program "Skype". Once you've got the program and are ready to make some phone calls you can open up the program and scroll down to dial. Before you began using this to make call there's a few things you should no. For example you cannot make any phone calls except for business calls. Once you've got The dial tab open simply type in the number you wish to call and then enter the number. Then it will make an attempt to cal...

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

In this video, the instructor shows us how to tell if a device (cell phone or other device) is tethered or un-lockable. Before you begin, you must download a tool called f0recast onto your laptop or desktop computer. After the application is downloaded, you must plug in your device to your computer (Windows only). Once you've done this, a window will show up from F0recast that will show you all of your phone's information. This includes if it's lockable, if it's tethered, the serial #, model ...

This video demonstrates how to restore your iPhone or iPod Touch if you are experiencing freezing or errors. You will need to restore your device if you experienced problems after attempting to have a jailbroken device. First, you have to make sure the device is turned on and plugged into your computer and connected to iTunes. To start restoring the phone, you want to hold onto the "home" button and the "unlock" button at the same time and continue to hold it until the device turns off. Next,...

In this video we learn how to disassemble a T-Mobile G1 HTC phone for repair. First you want to make sure to wear an ESD wrist strap and make sure it's secure around your wrist. Then remove the battery from the device. Next unfasten the screws from the back of the housing on the G1. Then separate the housing from the device and then the speaker from the housing. Next unplug the UMTS cable and the GPS coaxial cable. Then remove the UMTS board and GPS boards from the device. Then disconnect the...

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

In this video, the author explains how you can use software called "Pinnacle Video Transfer" to convert your audio and video files to other audio, and video forms. This is so that you can carry them on whatever devices you want, and play them whenever you want. This video takes you through all those steps to convert your favorite audio and video files to different file formats. You would get a clear idea as to how you can easily capture videos by watching this great tutorial.

If you own an Apple iPod or iPhone, and you want to unbrick it, you'll need to prepare the device first. This video will show you how to put your Apple iPod or iPhone into DFU mode, which means Device Firmware Update. You'll need to attach the Apple device to your computer for iTunes. If you're looking to jailbreak the iPod, this will help you get to that step.

Check out this video tutorial on how to make free phone calls from your iPod Touch or iPhone to any other phone out there. You will be using a free application from the iTunes App Store called Fring. This allows you to make VOIP phone calls.

With .Mac Sync, you can ensure your contacts, bookmarks and other information is synchronized between all of your Apple devices. For more, and to learn how to synchronize your own Apple devices using .Mac Sync, watch this video tutorial from Apple.

Want to play old school Nintendo on your Windows Mobile devices, such as smartphones? Well, this video tutorial will show you how to install the NES emulator on that Windows Mobile electronic touchscreen device. Just sync up your cell phone, and download the software off of the Internet. Just think, you could be playing Mario in the palm of your hand, on your mobile phone.

Check out this two-part video tutorial to see how to make a VB.Net timer program in Microsoft Visual Basic 2008 Express Edition.

This video covers creating and programming a a PHP-based web forum. Topics include basic layout, login and logout, Admin start, creating categories and subcategories, creating topics, and more...

I have never had any device that is easier to update the firmware than my iPhone. For anyone who may not be sure, firmware is basically the 'software' that runs a device's hardware. That's the easiest way I can think of to put it.

Interested in 3D programming, physics and Python? Erik Thomspon introduces 3D programming using the VPython toolkit covering a number of subjects including gravity, friction, and tension demonstrating falling balls, weights, wind and satellites.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

On Thursday, Magic Leap decided to step up its efforts to foster its developer community by launching the Independent Creator Program.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Just a week after news leaked out about Intel's 2018 plans for smartglasses, the company revealed what the device looks like and how it works in a new video (bottom of this page) released on Monday.

The Pixel 2's camera is one of the best you'll find on an Android phone. Among its standout features is the incredible Portrait Mode, which Google accomplished with some impressive software processing. Thanks to a few clever developers, you can now enjoy the Pixel 2's Portrait Mode on your Galaxy S8 or Galaxy Note 8.

We've been running the Essential Oreo Beta on our PH-1 over the past week and compiling a list of important changes. If you're interested in getting the Beta yourself, we even put together a quick guide on how to do that. Now that we've ran down the best new features, let's take a look at all of the bugs and performance issues in Android 8.0.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

With all of the Pixel 2 excitement the past few weeks, many Samsung fans are feeling left out on that new software hotness. If you're anxiously awaiting the Android Oreo update on your Galaxy S8 or S8+, that wait may come to an end this week. Users over on Reddit decompiled the APK for the Samsung+ app to reveal multiple mentions of the upcoming Oreo Beta Program for the Galaxy S8 and S8+.

The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept. 19, is available to install again — and anyone can get it.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.