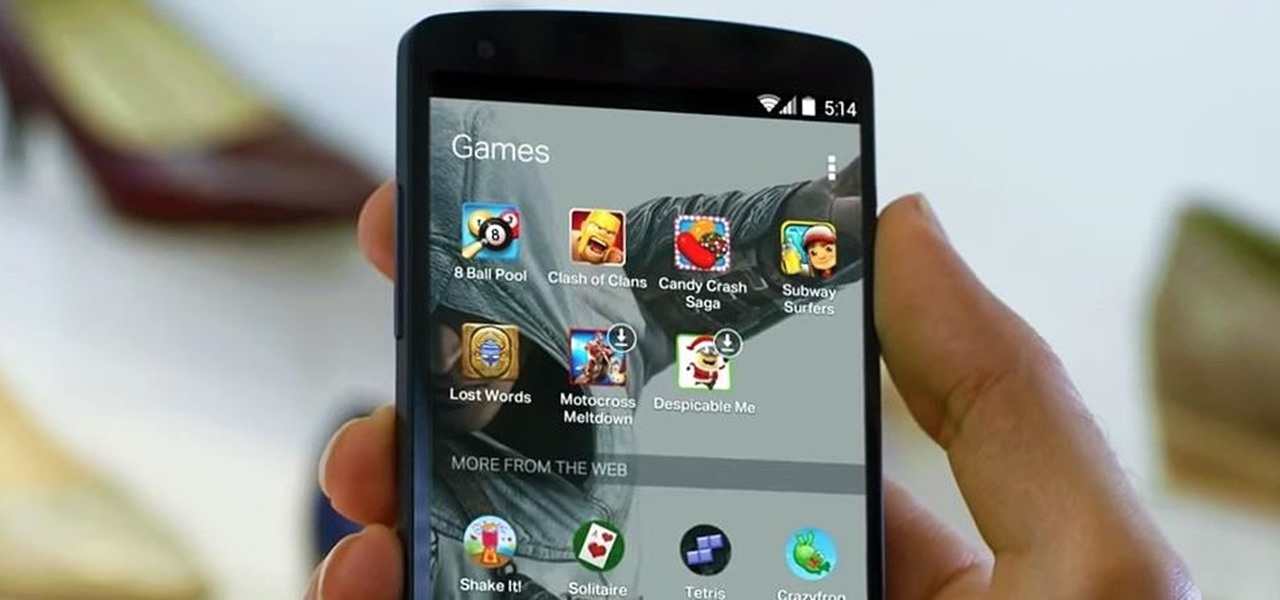
Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusing.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Ask a thousand Nexus owners why they chose their device over an iPhone, and after getting an earful of Apple hate, you will likely hear a clear pattern in their responses, namely, the freedom to customize their phones.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

Greg French talks to us about the different ways to reboot a computer to resolve issues in the computer. The first way is by pressing F8 key while startup after rebooting the system. When you insert a wrong driver for video card or something, sometimes when you boot the computer, it gives a black screen. Now he says you can resolve this problem by rebooting the computer and pressing the F8 key while startup. This will take you to a menu selection where you should select 'Safe Mode' and hit en...

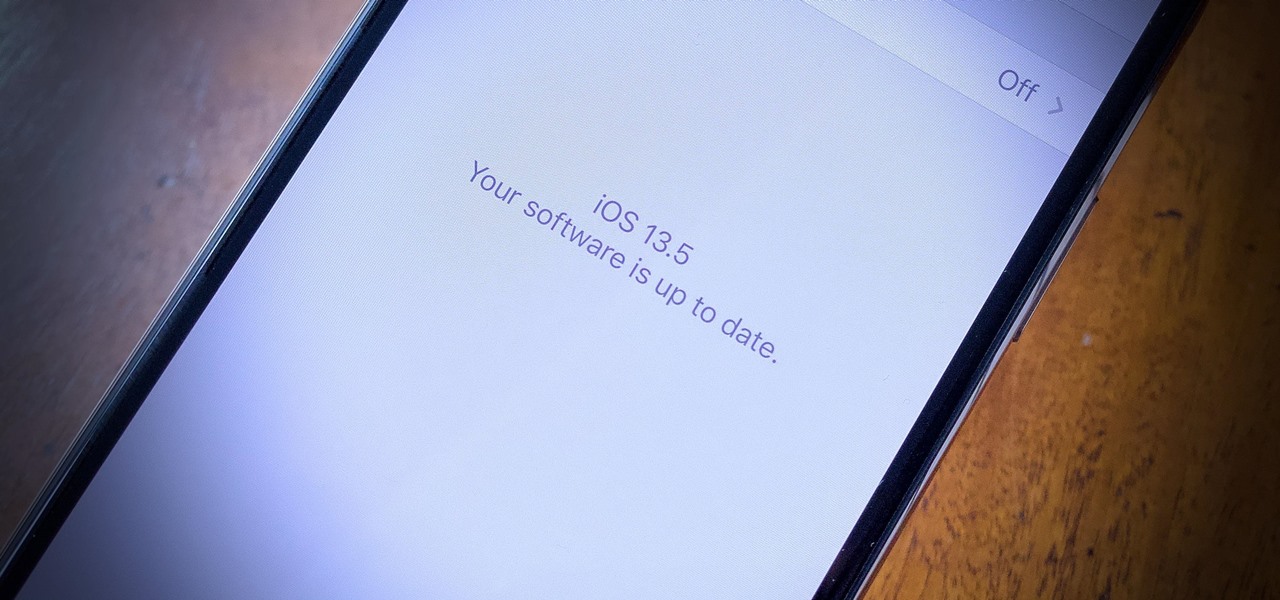
Apple released the first developer beta for iOS 13.5.5 on Monday, June 1. The update comes on the same day Apple released iOS 13.5.1 to the public, which patched the unc0ver jailbreak, and 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, in addition to other new features.

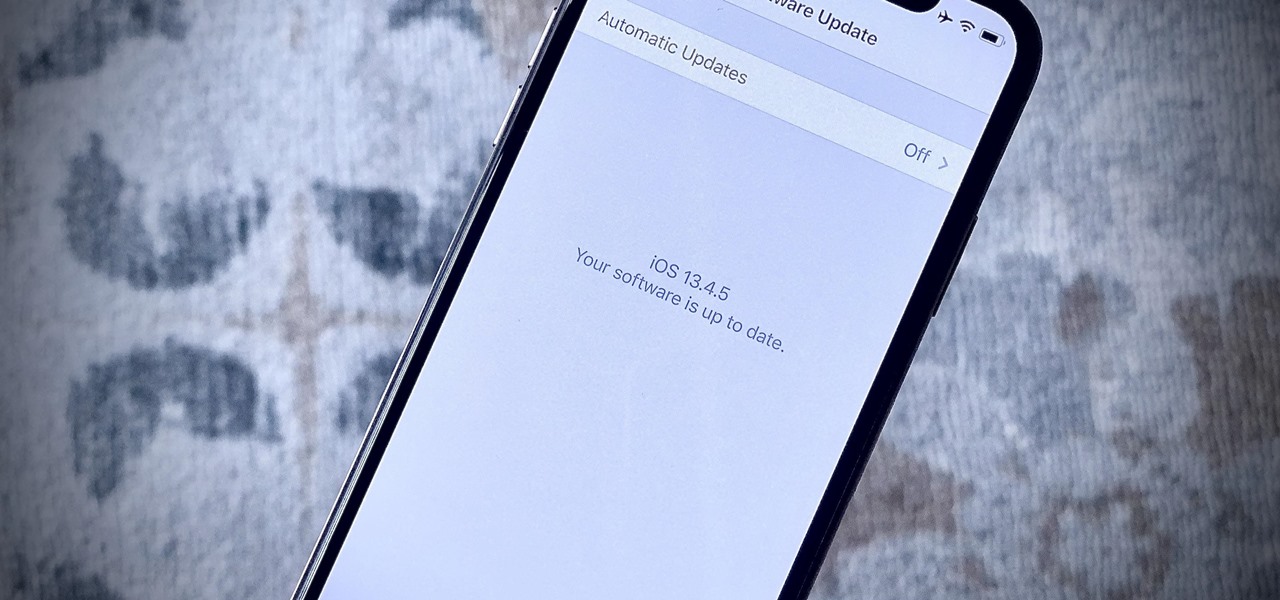
If you're a public beta tester, you woke up this morning with your iPhone running iOS 13.4.5. Today, Apple released the second beta for iOS 13.5. No, Apple didn't skip a version — 13.5 public beta 2 is essentially 13.4.5 public beta 2. So why the name change? Apple included the first API for its joint COVID-19 contact-tracing and exposure notification program with Google.

Apple released the third developer beta for iOS 13.5 today, Wednesday, April 29. If you're confused where 13.5 betas 1 and 2 are, join the club. This appears to be, for all intents and purposes, iOS 13.4.5 developer beta 3, following 13.4.5 developer betas 1 and 2. The biggest change? The addition of Apple's joint COVID contact-tracing program with Google, which likely inspired the name change.

Apple just released the first public beta for iOS 13.4.5 today, Thursday, April 16. This update comes one day after Apple released 13.4.5 developer beta 2, which itself arrived just over two weeks after 13.4.5 dev beta 1.

Though Microsoft has had trouble keeping up with the demand for HoloLens 2, the company has been able to supply modified headsets to the US Army.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?

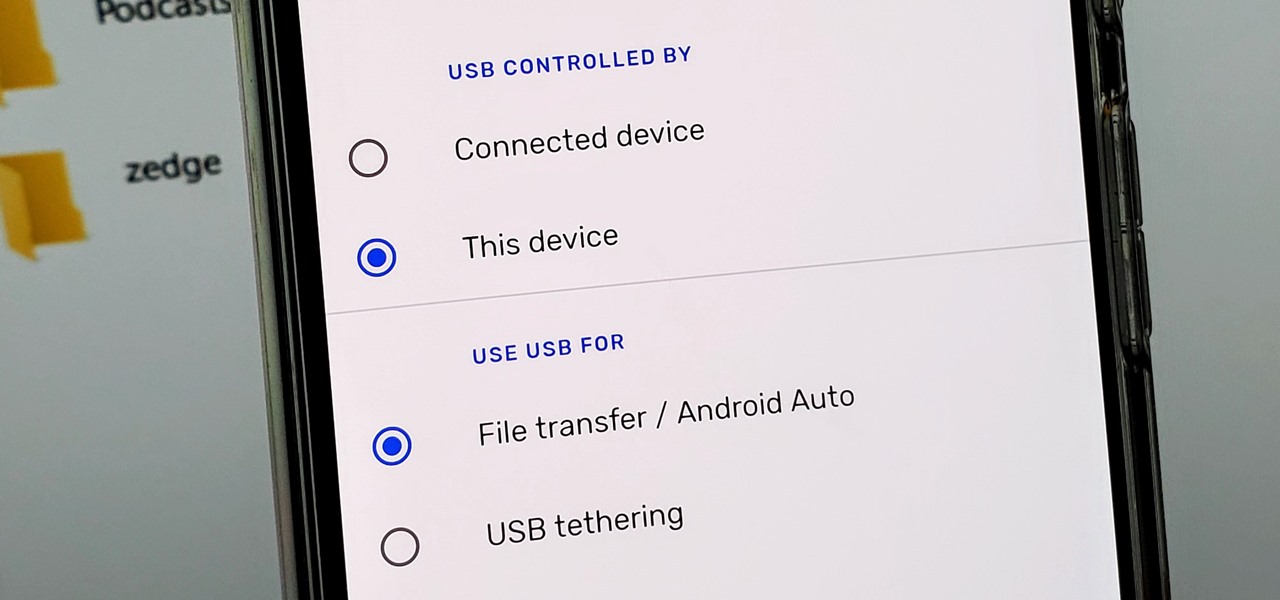
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

While some of us thought Apple might pass on a new beta update in favor of an official release, it appears iOS 13.3.1 is here to stay in beta testing. This time, it didn't take four weeks to get here. The third public beta for 13.3.1 is now available, eight days after the release of public beta 2.

The great iOS beta hiatus is over. After 28 days of waiting, Apple finally seeded the second developer beta for iOS 13.3.1 Tuesday, Jan. 14. Lucky for us public beta testers, we didn't need to wait long to get our version of the beta, as Apple just released 13.3.1 public beta 2.

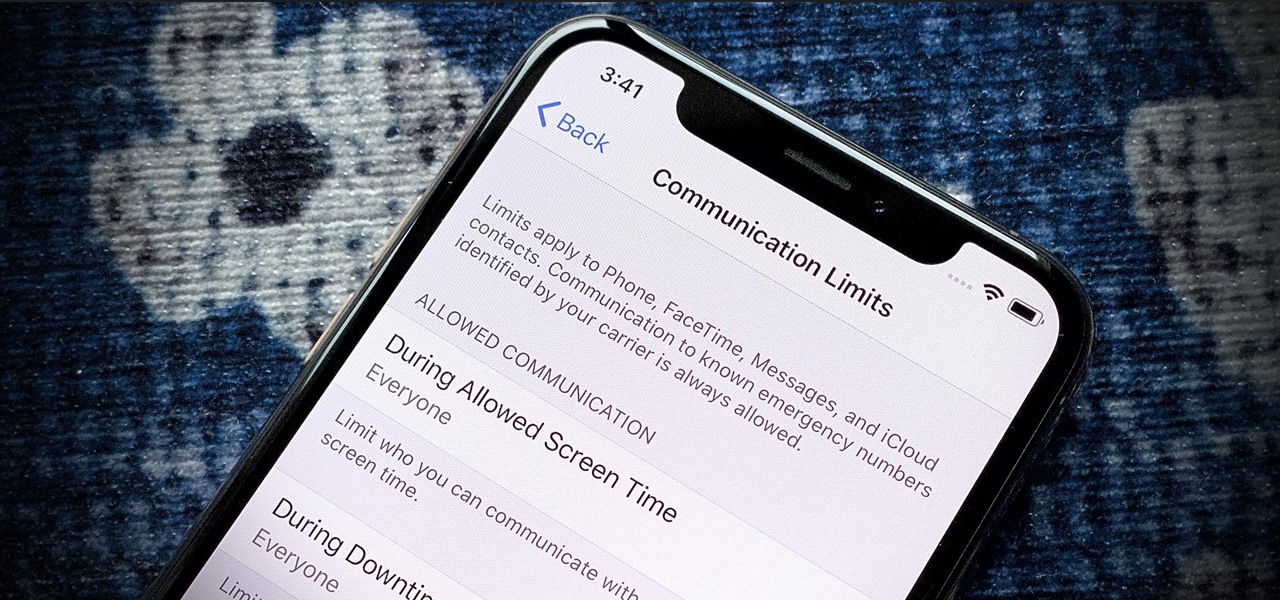
We spent four beta updates with iOS 13.3. In that time, we saw fun new features like Communications Limits in Screen Time, an off switch for Memoji stickers in the Emoji keyboard, and new mouse options, among other things. Once Apple made 13.3 available to the public, it was only a matter of time before it began beta testing new software. That software is iOS 13.3.1, and that testing starts today.

Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.

Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.

Apple's upcoming update for iOS 13 adds a host of fun new features, piggy-backing on the changes both iOS 13.1 and iOS 13 brought to the table. When you update, expect new emojis, Deep Fusion on 2019 iPhone cameras, among so much else. Want in on the action? Apple just released the fourth public beta for iOS 13.2 today, Wednesday, Oct. 23.

Another day, another beta, right? Well, that's not always the case. Apple can be pretty inconsistent when it comes to beta releases. In the past, a beta release once every two weeks was pretty much guaranteed. Nowadays, these updates can come at any time. Consider today's release, iOS 13.2 developer beta 4, which comes one week after the release of dev beta 3.

When you sign up to be a public tester for Apple's iOS, you get early access to features most users won't see for months. But you aren't the first — developers get priority when it comes to beta releases, made clear when they received 13.2 beta 3 while public testers were still on beta 2. Well, we public testers finally caught up, after Apple released iOS 13.2 public beta 3 Wednesday, Oct. 16.

There's nothing quite as exciting in the beta testing world as a new update. Battling overloaded servers to download the latest update as fast as possible, just to scour through the new OS looking for the biggest features to the smallest changes. It was only Thursday that Apple seeded iOS 13.2 developer beta 2, so count us surprised that we get to experience today's release of developer beta 3 so soon.

We public testers are in luck. Today, Apple released the second developer beta for iOS 13.2. As is the case with most beta releases, developers get theirs first, while public testers are left waiting. Will we get our update the same day, or will we need to wait? As it turns out, Apple decided to throw us a bone. The second public beta for iOS 13.2 is officially here.

The company that supplied some of the technology behind the Star Wars Jedi Challenges AR playset now has its own headset to offer.

Thanks to a new update to Amazon Sumerian, developers will now be able to not only create more realistic 3D content, but also build AR experiences more easily.