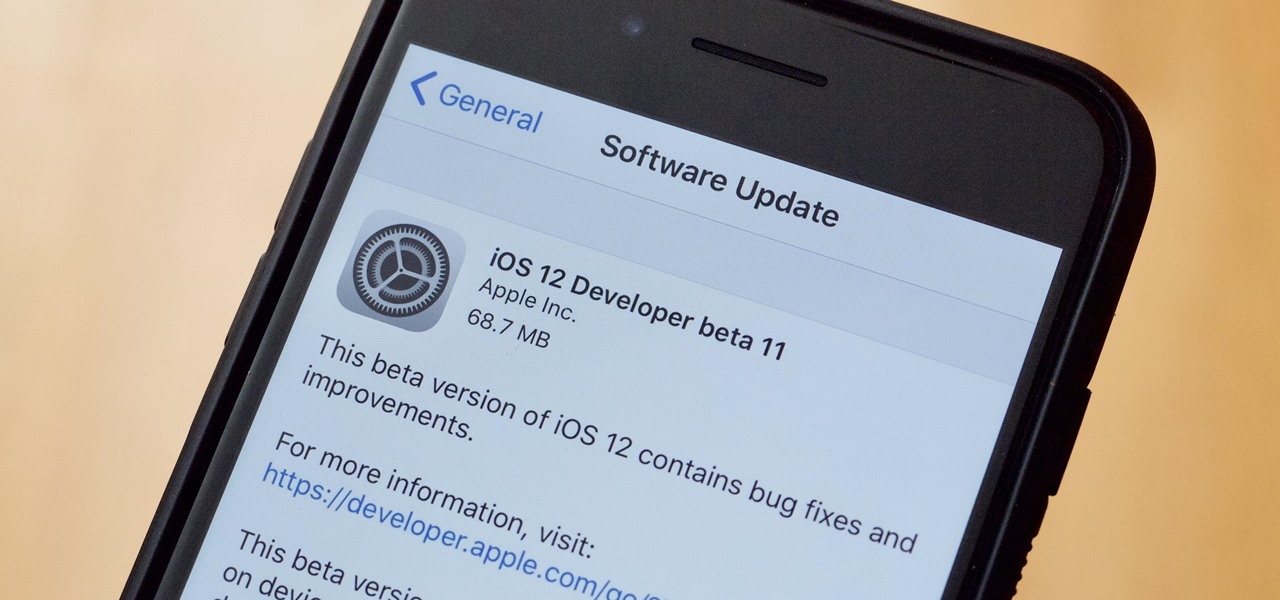
Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.
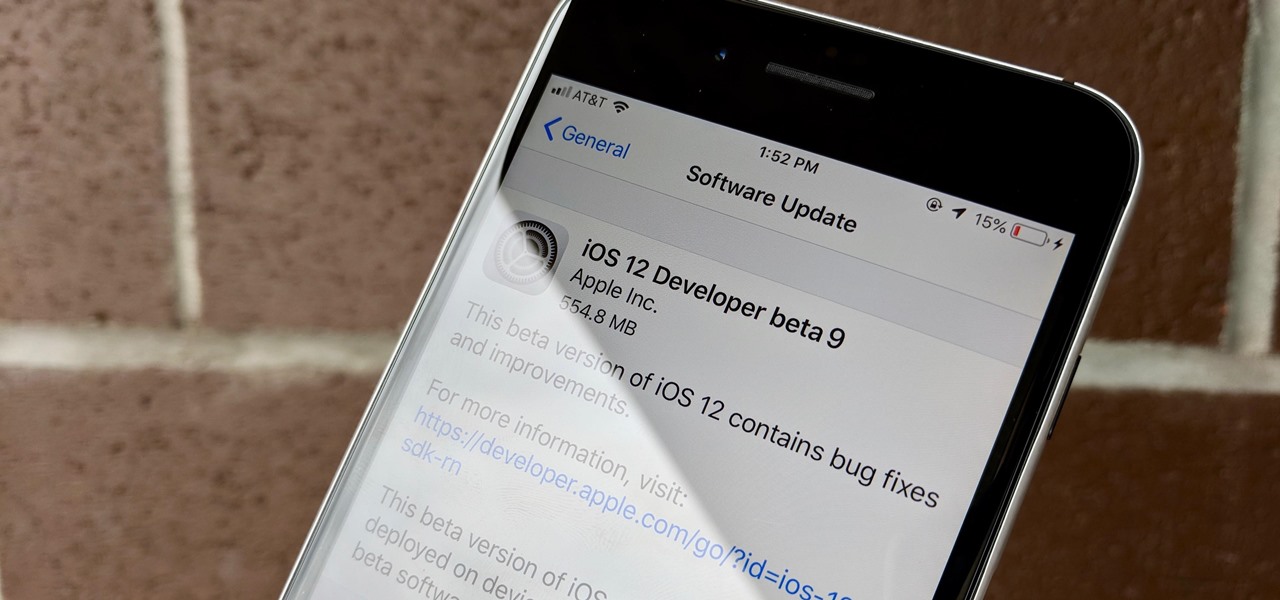
Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.
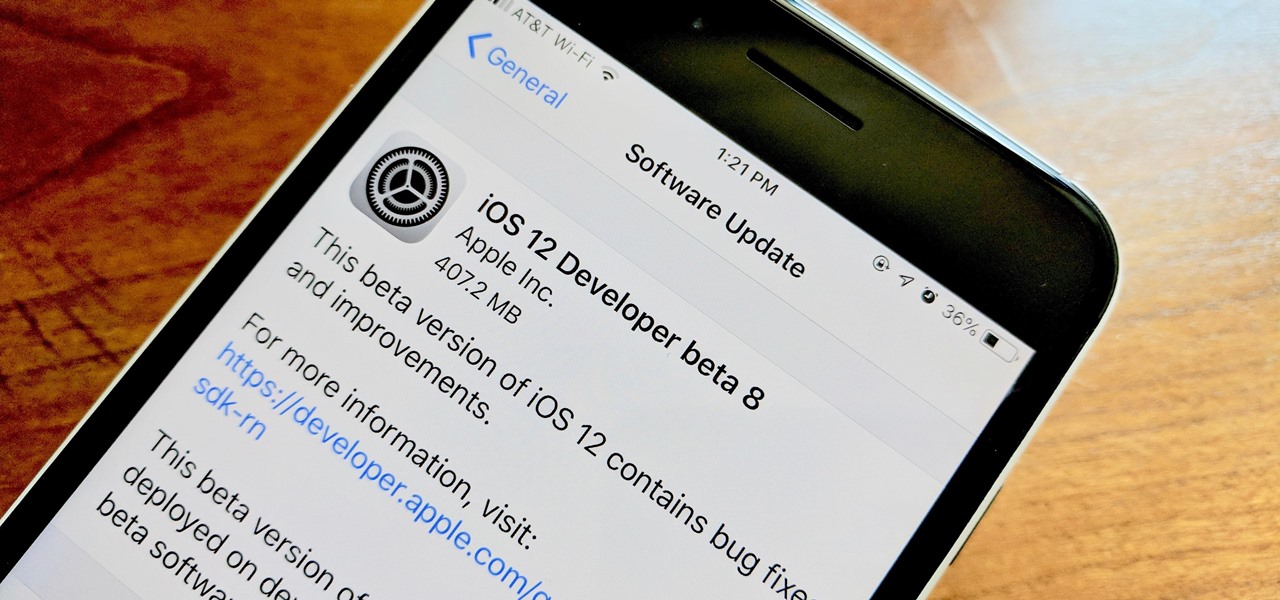
Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.
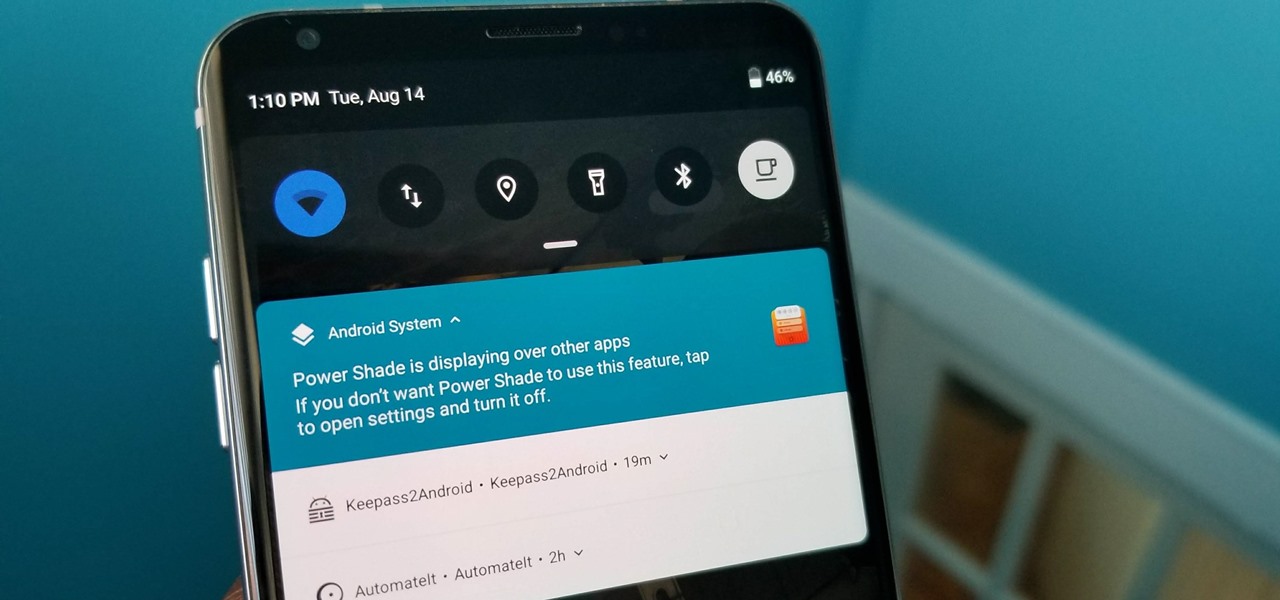
With all Android updates, there's a considerable wait before most phones get the new version, and Android Pie is no different. Until then, most of us are stuck just looking at videos of the newest update. Well thanks to developer Trey Dev, we can enjoy the new notification shade and Quick Settings menu while we wait.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

Hours after iOS 11.4.1 beta 4 was released on Monday, June 25, Apple's webpage for its public beta software programs was unavailable because of an "update." Sure enough, that meant the public beta for iOS 12 was being prepped to drop shortly thereafter, which is exactly what happened. In other words, you can now install iOS 12 on your iPhone without a developer account!

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

As manufacturers try to differentiate their smartphones from the sea of Android devices, a new genre of smartphone has emerged: gaming phones. Razer Phone was the first to gain traction, but the likes of Xiaomi, Asus, and ZTE have all announced gaming-first phones coming soon. Still, you don't really need to buy a "gaming phone" to play games like a pro on your smartphone.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

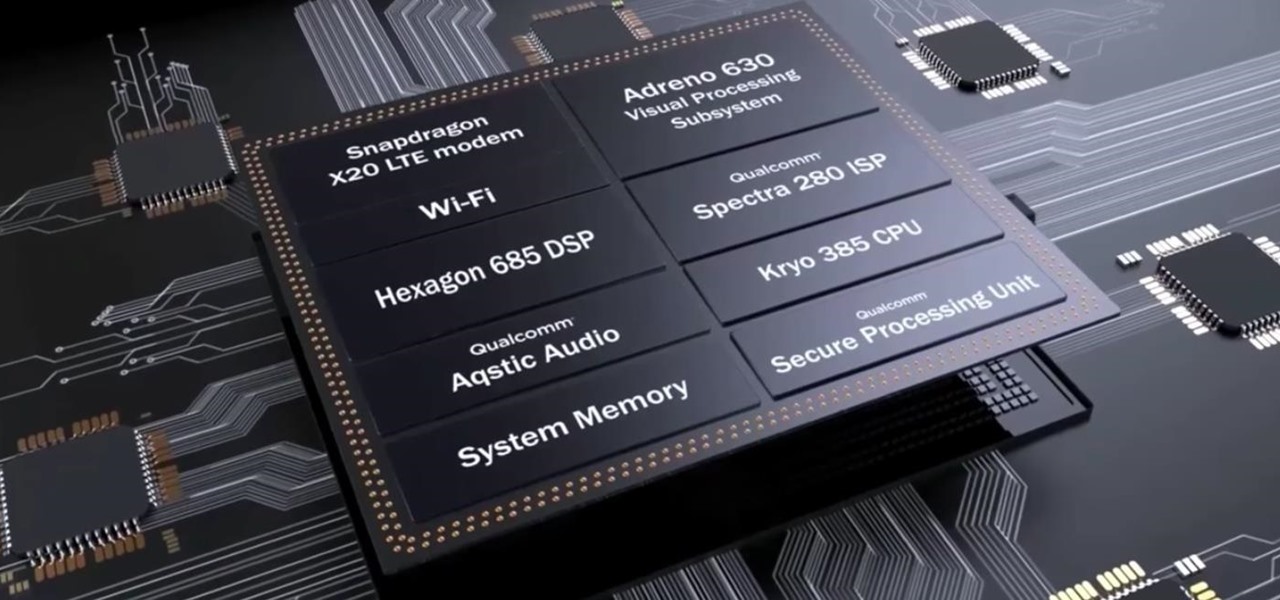
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

In 2017, major breakthroughs in smartphone-based simultaneous localization and mapping (SLAM) opened up new doorways for developers and users of both Apple and Android phones. Unfortunately for Android users, the solution that Google is previewing, ARCore, currently only works on three Android smartphones. But Silicon Valley start-up uSens is stepping in to fix that with its new engine called uSensAR.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

When it comes to technology, there are no bigger names than Google and Apple. They're the two most valuable companies in the world, and they've swapped places a few times over the last year, so they're truly neck-and-neck. But let's put business aside for a moment — which of these companies makes the better flagship phone?

I don't know about you, but I love options. Personally, I think Android's notification system is easy to use — providing access to new notification with a swipe down from the top of the screen. But, as Android users, we like the ability to do things differently whenever we see fit, so what if you wanted a different way? Well, with Action Launcher, this is possible.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

More than one in ten people in the US have type 2 diabetes — that's over 29 million people. It's characterized by excessive sugar (glucose) in the blood due to the development of resistance to insulin, the hormone that normally metabolizes glucose.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

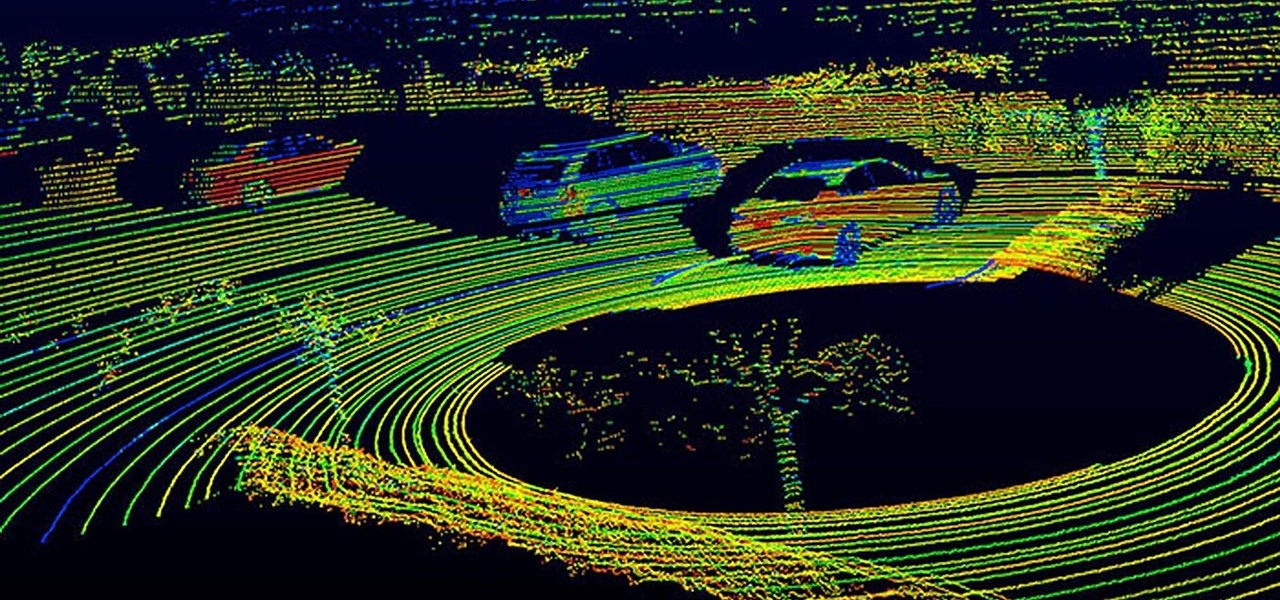
The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Since I recently had this problem and fixed it, I might as well share the solution. This is actually REALLY simple to fix but will impact your cards' performance.