The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.
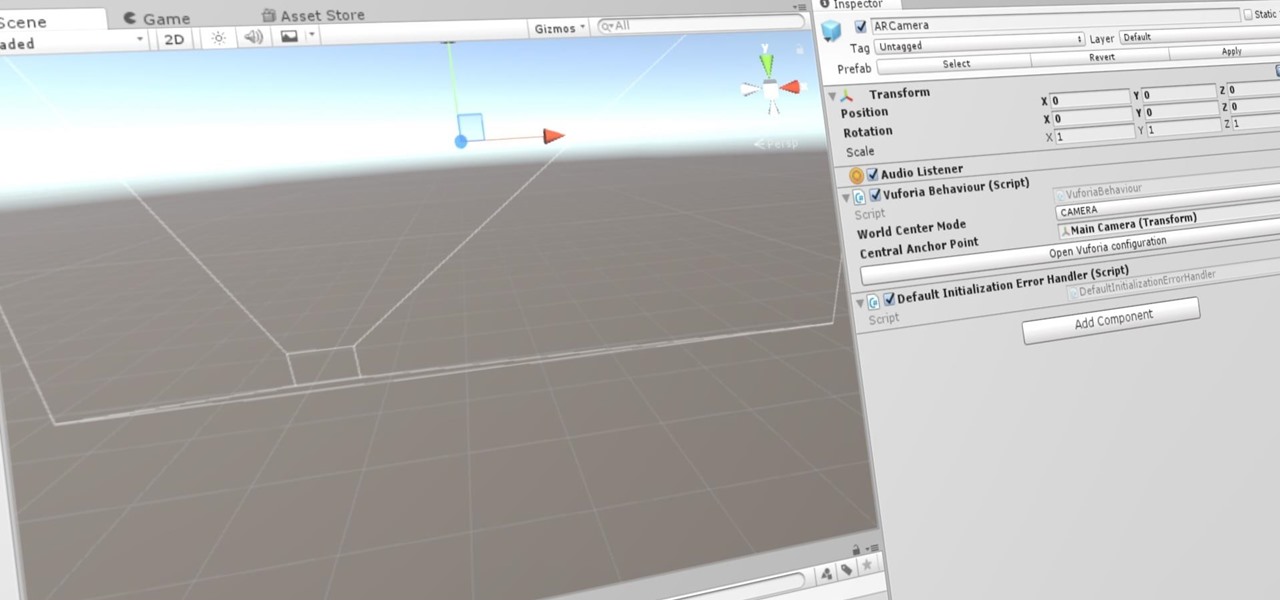
Now that we've set up Vuforia in Unity, we can work on the more exciting aspects of making physical objects come to life on the HoloLens. In this guide, we will choose an image (something that you physically have in your home), build our ImageTarget database, and then set up our Unity camera to be able to recognize the chosen image so that it can overlay the 3D holographic effect on top of it.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and novices alike.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

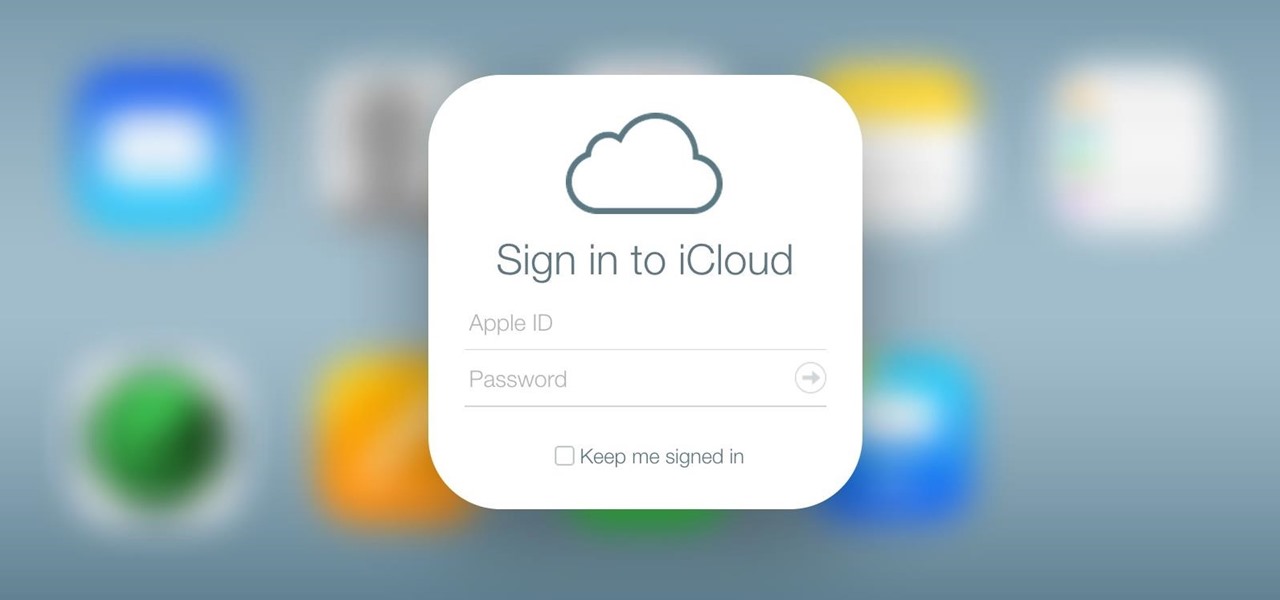
We've already shown you how to free up internal space on your iPhone, and now it's time to tackle another problematic storage issue—your iCloud account.

"The best season for food is the worst season for cooking." These words, spoken by food blogger Dave Klopfenstein of Dave's Kitchen, couldn't be more true.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

One little known feature on Android devices is TalkBack, which provides you with spoken feedback and vibrations in order to help you navigate your device. Obviously, if you're not blind or visually impaired, this isn't a feature you're likely to use.

Thought I would cross-post a piece I did a while ago.

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

Mechanical locks have been around since ancient Egypt, with the oldest known artifact found in the ruins of Nineveh, an ancient city in Assyria, Mesopotamia, which is just across the Tigris River from what is now Mosul, Iraq.

There are a surprising number of hidden features in your iPhone's Phone app, from secret dialer codes that provide info or perform actions to special characters that dial extensions automatically. However, there's one little-known trick every iPhone owner should know when using the Phone app for calls — and it's the simplest and most useful of them all.

Your iPhone's clipboard can only save one item at a time, so it may seem impossible to retrieve your entire history of copied text, images, and other content. Luckily, there is a workaround you can use to find and copy your past clipboard contents, but you have to implement it first.

Have you ever wondered where you'd come out if you drilled to the other side of the world? Now, if you have an Android device and Chrome web browser, you can find out.

Apple just released the eighth public beta for iOS 14 today, Wednesday, Sept. 9. At this time, beta 8 (18A5373a) seems to be a minor update to iOS 14, introducing bug fixes to improve the software's overall stability.

Apple just released the eighth developer beta for iOS 14 today, Wednesday, Sept. 9. Beta 8 (18A5373a) appears to be a minor update offering bug fixes to improve overall stability.

Anything from work or a missed flight to a worldwide pandemic (COVID-19, anyone?) can make it difficult or nearly impossible to see your loved ones. You can make phone calls or send iMessage, text, or email messages, but nothing compares to seeing family and friends right in front of you. That's where FaceTime comes in.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

Samsung Experience (better known as TouchWiz) can take some time to get used to when you switch to a Galaxy from another Android device. It's a bit heavy-handed with the features, and many consider the UI theme to be a little over the top. Thankfully, there are several stock settings that can dial this back.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Google has a few hidden tools you might not have discovered yet, and they work in Google Search, in the Google app, and with Google Assistant — on both iPhone and Android phones.

TikTok is all the rage right now, and its green screen effect is one of the more popular augmented reality tricks creators use to boost their viewership numbers. Now Snapchat has leveled the playing field by making it easier to access its own green screen effect.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

During its annual autumn keynote address, Apple didn't move heaven and earth. Instead, the company pushed the envelope ever so slightly forward for its marquee consumer devices.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

Apple seeded public testers the second iOS 14.6 beta today, Friday, April 30. The update (build number 18F5055b) comes three hours after Apple released the second 14.6 developer beta, four days after the launch of iOS 14.5, which introduced over 60 new features and changes to iPhone, and eight days after the first 14.6 beta hit developers' iPhones.

Apple released the eighth iOS 14.5 developer beta on Tuesday, April 13. The update (build number 18E5199a) comes six days after Apple's last 14.5 beta update, which Apple pushed out to both developers and public beta testers.

It's a bit surprising that Apple hasn't seeded beta testers the release candidate for iOS 14.5. The next big iPhone update is rumored to be out soon, so it stands to reason that we'd see a "final" version of that software hit our test devices rather than another beta. But that simply isn't the case here, as Apple decided to release a seventh 14.5 beta.

Earlier this month, the rumor mill suggested that Apple was gearing up for a Mar. 23 event, with a possible release of iOS 14.5 to boot. That event, as we can now see, never came to be. It seems Apple is also not quite ready to unveil iOS 14.5, either, as we now have a fifth beta to test on our iPhones.

Apple released the fifth iOS 14.5 developer beta on Tuesday, Mar. 23. The update comes eight days after the company released 14.5 beta 4 for public testers and developers.

After a slow phase-out, Google Play Music was shut down in December 2020. The songs you uploaded or purchased are still on Google's servers, but even those will be deleted on Feb. 24, 2021.