The LG V30 is an amazing device that will contend for best smartphone of 2017. It has all the major features you'd expect from a high-end flagship, and it even includes what's become a rare commodity these days — a headphone jack. However, for the purists out there, the LG UX skin strays too far away from stock Android. Have no fear, for with the LG V30, you can have your cake and eat it, too.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

If you want to make clothes for your cat, you're on your own. As I recently said in this article, cats will just totally flip out if you make them wear things. Your dog may also flip out, but I've found them to be more tolerant, personally.

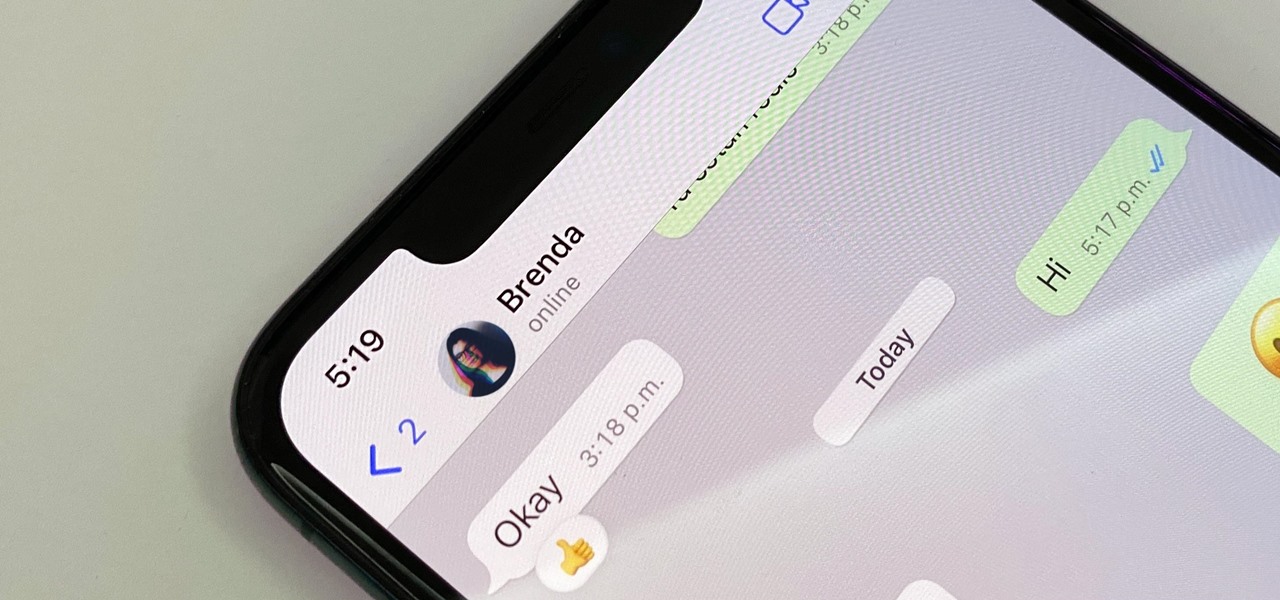
By default, everyone on WhatsApp can see when you're using the app. If someone recently messaged you and sees you're currently online, they may think you're avoiding them if you don't respond right away — especially if you don't share read receipts. However, you can block them from seeing your online or last seen status and apply it to everyone or just specific contacts.

With the new Samsung Galaxy S22 Ultra release, the first thing you may be wondering is how its battery life compares to the iPhone 13 Pro Max, Apple's biggest model from 2021. We've rounded up some of the most popular Galaxy S22 Ultra and iPhone 13 Pro Max battery tests from across the internet to bring you answers.

Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for Apple Music, new features that will require iOS 14.6 to run.

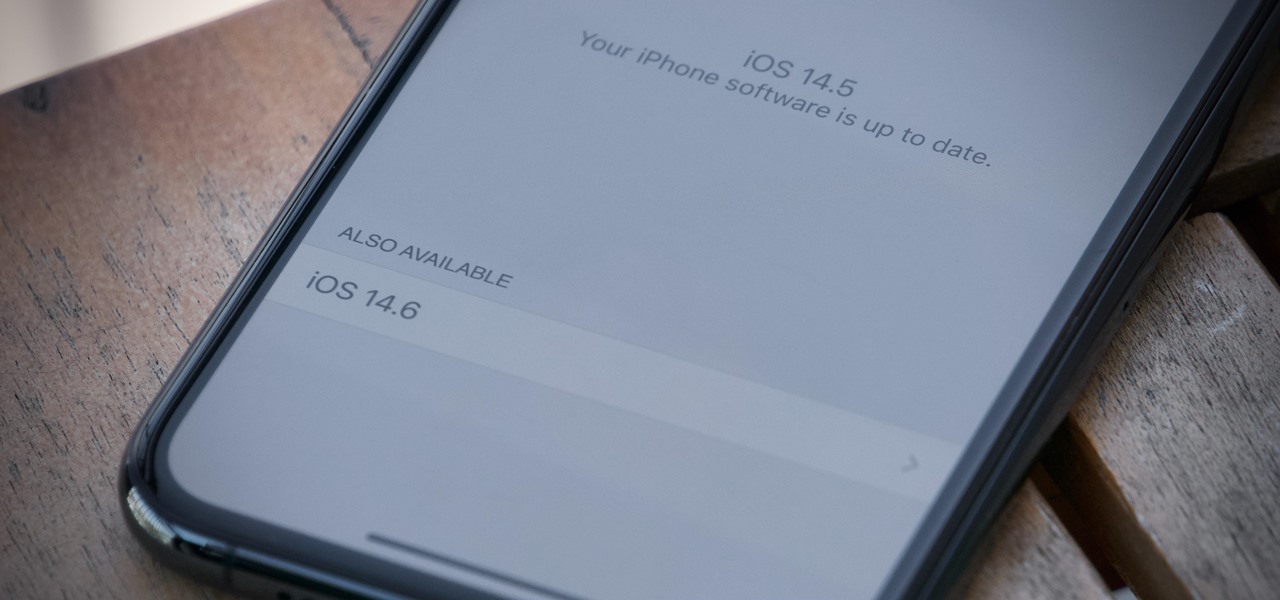
Apple released the first public beta for iOS 14.6 today, Friday, April 23, one day after the company seeded iOS developers 14.6 beta 1. The update introduces an easy way for testers to update from an iOS RC (release candidate) to the latest beta, via a simple option in Software Update.

Apple released the first beta for iOS 14.6 today, Thursday, April 22. The new beta (build number 18F5046e) comes just two days after Apple's spring event, as well as the iOS 14.5 RC, and features an easy way for beta testers to update to the latest beta software when running an RC.

Apple's iOS 14.5 is the biggest update since iOS 14.0 came out, with over 50 confirmed features and more being discovered every day. There are new emoji, support for AirTags, more privacy controls, and exciting upgrades to Siri, Maps, Reminders, Podcasts, Music, and even Shortcuts. So it wouldn't surprise us if you want to get this on your iPhone ASAP.

Apple seeded software testers iOS 14.5 public beta 6 today, Wednesday, March 31. The update includes a new battery calibration for iPhone 11, 11 Pro, and 11 Pro Max, as well as two new Siri voices.

Apple just seeded developers the sixth iOS 14.5 beta today, Wednesday, Mar. 31. The update includes a calibration for battery health measurements for the iPhone 11 line, as well as two new Siri voices.

I always keep my iPhone's Portrait Orientation Lock on so that my screen doesn't randomly rotate while I'm lying down. However, there are certain apps that I do turn it off for. It's kind of a pain since you have to swipe down the Control Center and toggle the orientation lock — but that ends now. Instead of doing it manually, a new iOS update can automate app orientations for you.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

Apple has finally seeded the release candidate for iOS 14.4 to iPhone developers and public beta users, build 18D52. The update adds scanning support for smaller QR codes in Camera, the ability to classify Bluetooth devices to improve audio notifications, and alerts on the iPhone 12, 12 mini, 12 Pro, or 12 Pro Max for if the camera is detected not to be genuine. There's also a short list of bug fixes.

While Apple has been making strides in iPhone customization, it's still not up to par with what Android is and always has been. You can hide apps from the home screen now in iOS 14, but for everything that's still there, you can't add gaps between icons on the same page to segregate them where you want. However, some workarounds give that effect.

Apple does not provide a native way to lock apps on your iPhone behind Face ID, Touch ID, or your passcode. For a long time, we've wanted that option for improved privacy and security, but Apple does allow developers to use its authentication protocols. Apps like Messenger, Outlook, and WhatsApp give the option to lock them down, but for the apps that don't, you can force it with a little time and effort.

Apple just released the third public beta for iOS 14.2 today, Wednesday, Oct. 14. This update includes new glyphs for the HomePod mini and Beats Flex, support for HomePod's upcoming new "Intercom" feature, new core media features, and SwiftUI fixes.

Apple released iOS 14.2 developer beta 3 for iPhone on Tuesday, Oct. 13. The update adds new glyphs for HomePod mini and Beats Flex, support for HomePod's upcoming "Intercom" feature, new Core Media features for developers, as well as resolved SwiftUI issues.

Apple released the first beta for iOS 14.2 to iPhone developers on Thursday, Sept. 17. A significant new feature that iOS 14.2 brings to the table is a new Control Center tile for Shazam music recognition. A simple tap of the tile will launch the operating system's built-in Shazam capabilities, scanning for music playing in the immediate area.

Apple just released iOS 14 public beta 7 for iPhone today, Thursday, Sept. 3, and features new dark mode wallpaper options. Choose from any of the rainbow wallpaper's color backgrounds, and iOS will automatically shift the background to black when you enable dark mode.

Apple just released iOS 14 developer beta 7 for iPhone today, Thursday, Sept. 3. The new update (18A5369b) features new wallpaper options. Now, you can choose any color background for the rainbow wallpaper, and iOS will turn the background black when you enable dark mode.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Apple released the second developer beta for iOS 13.6 today, Tuesday, June 9. This update comes one week after the release of its first developer and public betas, previously called iOS 13.5.5, as well as the general release of iOS 13.5.1. Apple's first 13.5.5 beta introduced evidence for Apple News+ audio support.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.