Out with the old, in with the new—but sometimes that phrase is reversed. Just take a look around and you'll see some high-top fades from the '90s and some hipster wearing his great grandmother's Depression-era reading glasses.

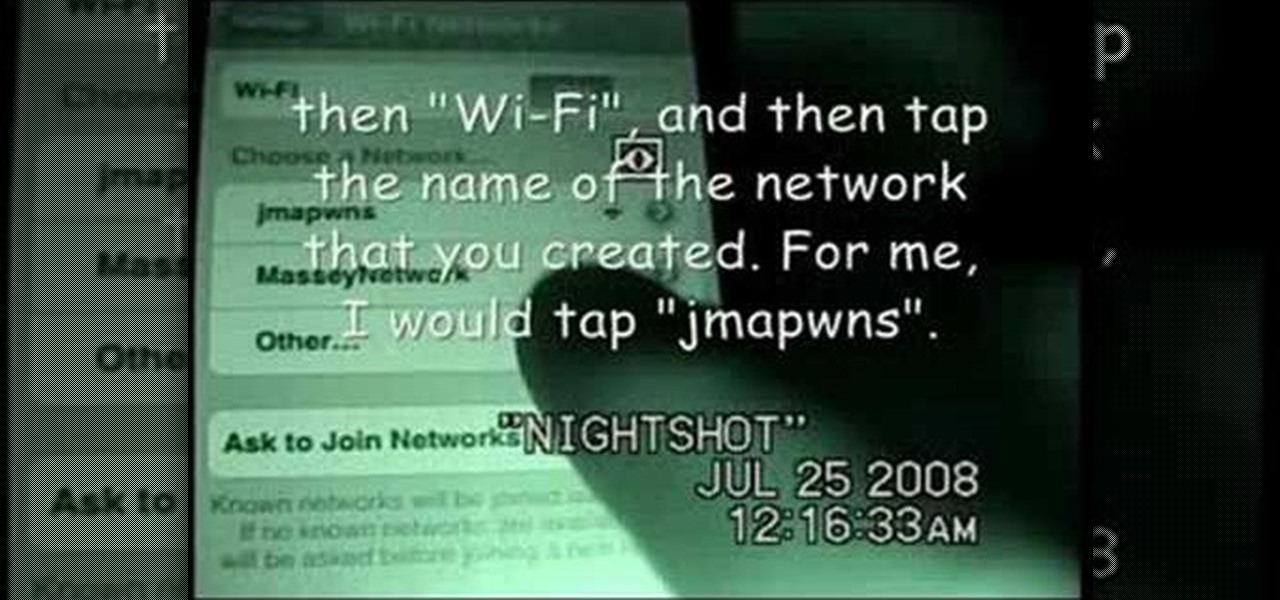
Lock screen exploits are becoming increasingly common in the mobile world. Four weeks ago there was the iPhone 5 passcode bug (which just got fixed yesterday...kinda). Then there were a couple lock screen bugs on the Samsung Galaxy S3 two weeks ago.

If you've ever found yourself wandering about a room, holding your phone up to the sky searching for a signal, this is just the trick for you. Edward from Redmond Pie found a great way to configure the readout with just a simple phone call, making your iPhone display its exact signal strength in decibels (dBm). Step 1: Put Your iPhone into Field Test Mode

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Samsung has stepped up its camera game with the Galaxy S10's dual- and triple-lens systems. But as impressive as the hardware is, the native Samsung Camera app still isn't as good with image processing and video stabilization as the Google Camera app for Pixel phones. Thankfully, you can get the best of both worlds.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Everyone should know how to perform basic first aid, especially for choking victims. This video will help deaf people and those with hearing impairment learn how to deal with choking, using sign language. Choking is serious life-threatening problem that need immediate attention. It could result in such problems as hypoxia or even death.

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

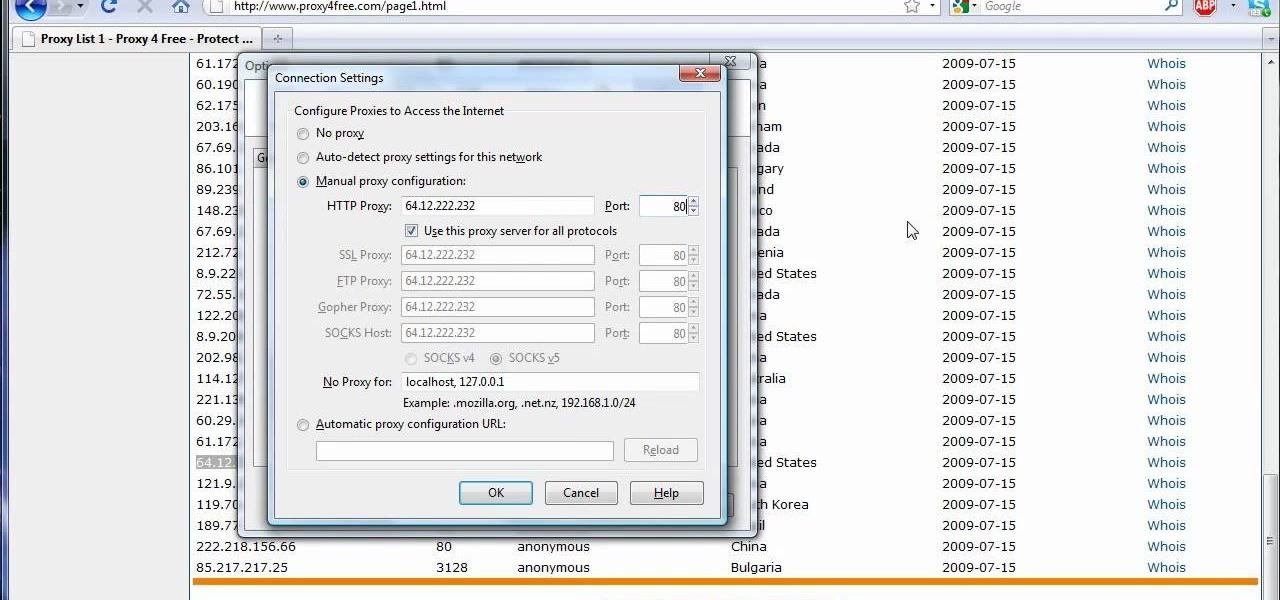
The video shows us how to use a proxy server with Firefox to hide your IP address. you can actually use this to avoid the hacking and various things that are blocking you from websites. Firefox is one of the easiest way to do this and for doing this you need to Google search the free proxylist and then you can select a proxy from the one which is related to the country you are residing in. Then copy that proxy server and then go to tools and click on options and under advanced tab click on ne...

A video that describes how to install Google Chrome OS onto your PC without changing your current PC configuration. What this means that you can use Chrome OS without changing your current OS (Windows Linux etc) and without making any changes to your dis partition or BIOS. The first section of this video explains how to use a simple USB drive to boot into Google Chrome OS. The second section of this video explains how to install Google Chrome OS onto your computer and launch it using your hos...

In this video tutorial, you'll learn how to speed up your Windows computer's startup efficiency (and so its startup time) with MSConfig, or the Microsoft System Configuration Utility. MSConfig will allow you to disallow unnecessary programs from starting up when you boot your PC. For more information on using MSConfig to speed up your computer, take a look!

Open work makes a project go really fast. You might not be the warmest on a cold winter night, but it still looks nice. An open work stitch is basically a three to two configuration. This is the perfect beginner's project. These crochet blankets will keep you warm but won't stifle you.

This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration steps required to properly tether an iPhone 3G in Windows XP so that you can use its EDGE or 3G internet connection on your PC, for free.

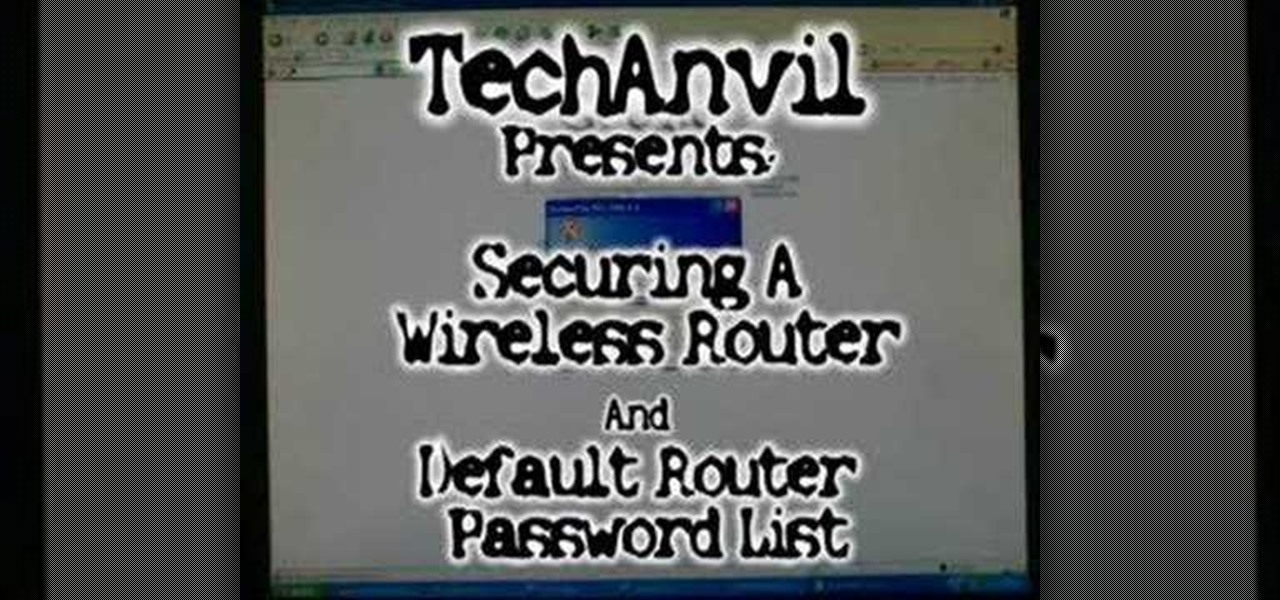
This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

Jeff Schell shows you some of the options and configurations available when working with images that do not match the dimensions of your program monitor in Premiere Pro CS3. In addition, Jeff will introduce you to the 'Automate to Timeline" feature that helps you quickly create a photo montage or slide show with the click of a button.

In After Effects 6.5, Adobe introduced Incremental saves. Rather than waiting for the auto-save to catch the latest revision to your project, incremental save allows you to manually save a new file, incrementing the name of your project in numeric integers. CINEMA 4D does the same. And with a little configuration, you can make it act exactly the same as in After Effects.

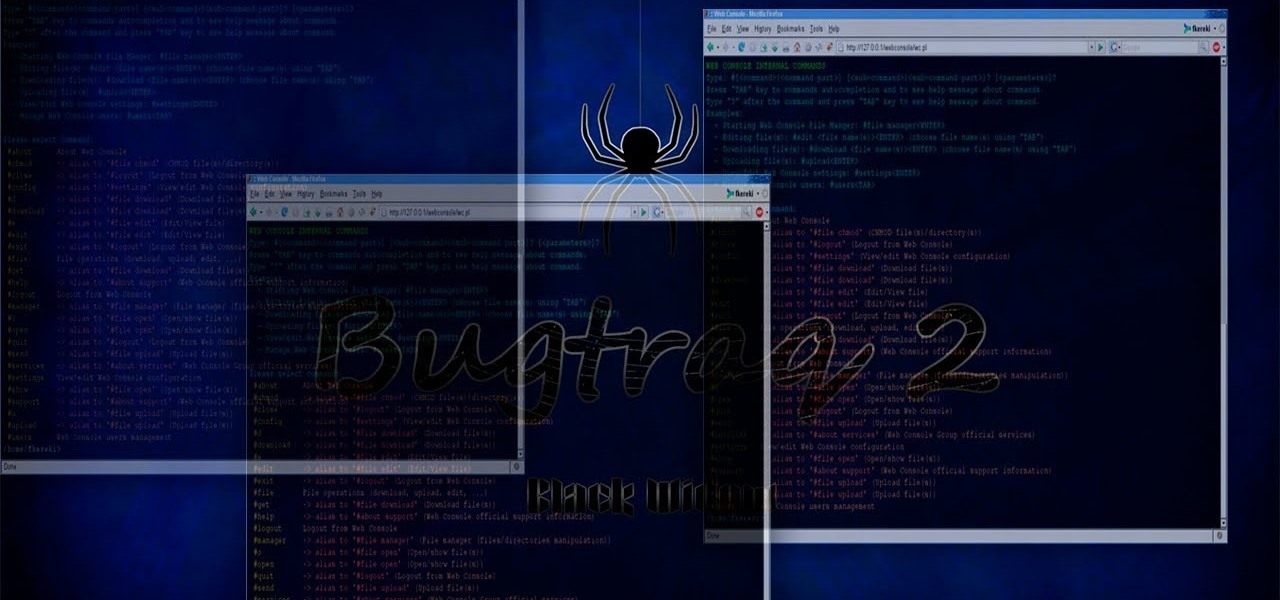
In this "HOW TO" I will show you how to install and mange yourself in bugtraq. You will jave to folllow a couple of videos and then you will know everything that you need on how to install and configure bugtraq.

In the first video, it introduces the principles and terminology of mechanical electrical switches. It covers terms such as contacts, normally open, normally closed, poles, and throws.

Choking is serious life-threatening problem that need immediate attention. If waiting too long, it could result in such problems as hypoxia or even death. Being able to respond to a choking victim could save someone's life, and everyone should know this first aid procedure.

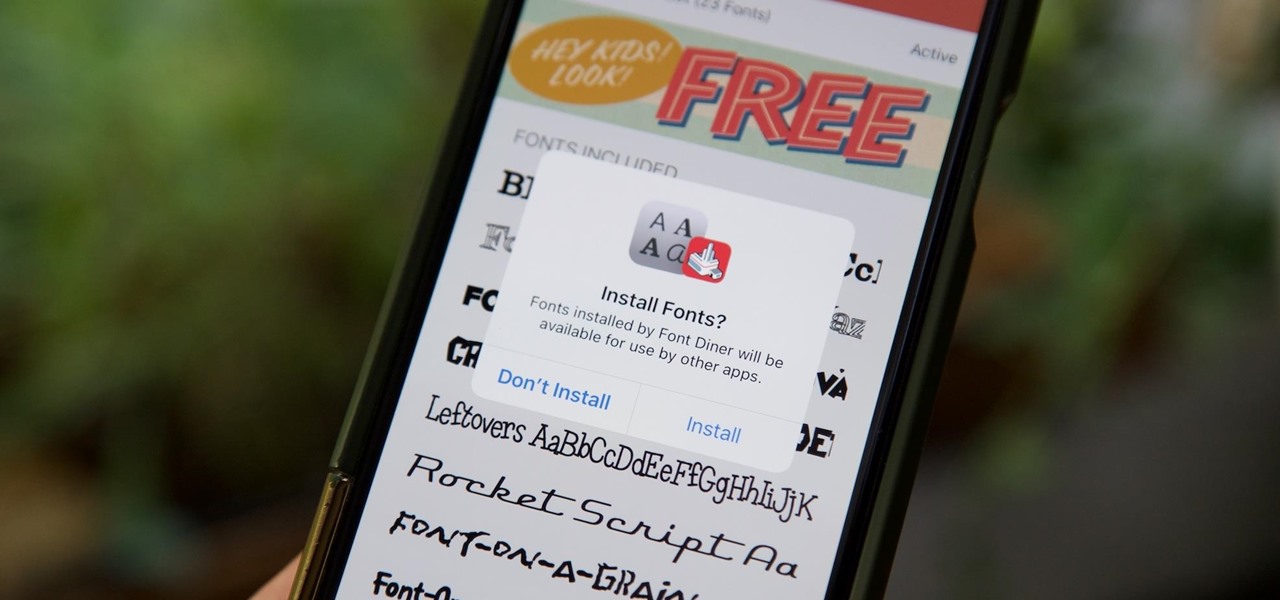
Apple added the option to install custom fonts and use them in different apps on iOS 13. The rollout has been a bit confusing, with Apple announcing partnerships with vendors such as Adobe, but also limiting the feature to work with only certain apps. Nonetheless, you can now download and install custom fonts on your iPhone.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Notice anything different about your Google searches lately? Your favorite businesses are becoming even more reachable online. Now, you can simply Google a business and click on its highlighted phone number to give them a call immediately from your computer.

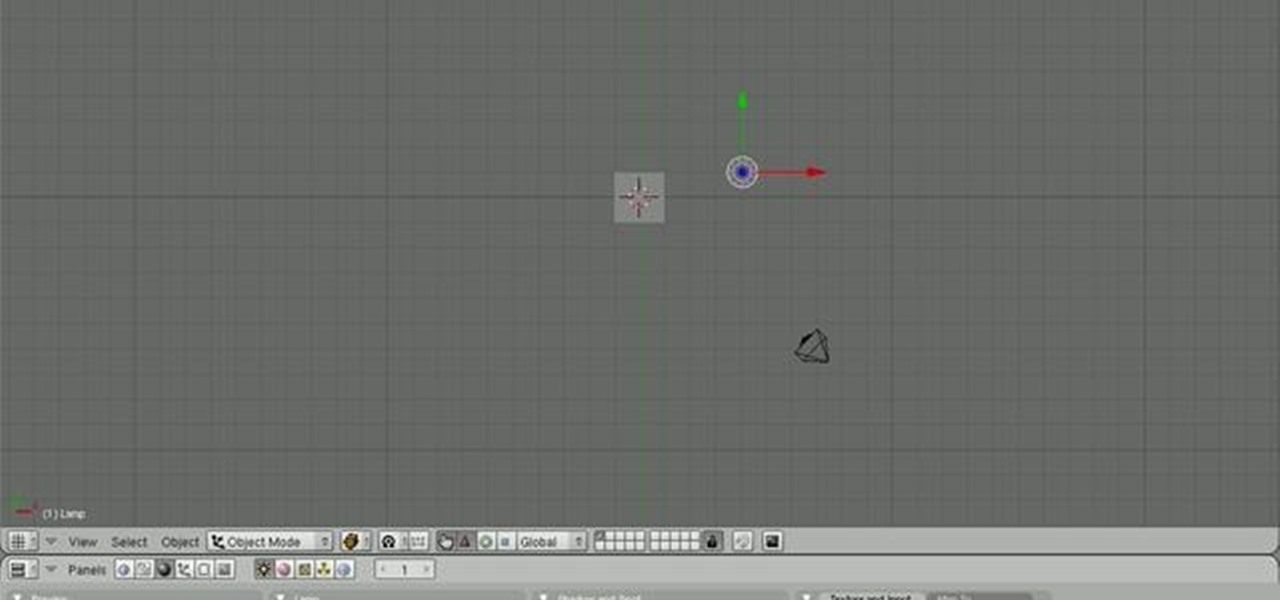
A good lighting setup is essential to effectively displaying your model. Without it your hard work might as well be for nothing. This tutorial takes a look at how to make a good three-point (+) lighting setup in Blender. The tutorial covers the different kinds of lights within Blender, the different configurations needed, and some general tips and tricks to creating a good setup within Blender. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application...

An easy way to use a voice command to dial your iPhone is by downloading an ap that enables you to do just that. Without a built in voice dialing system, you will have to turn to external solutions if you wish to have this ability.

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo, will show you how to extend Widows Media Center to your XBox 360 using Windows 7. This video assumes that your XBox is already connected to your home network, so you may want to be sure to do that first. With this configuration, you will be able to not only watch movies, but view, pause and record TV on your personal computer, as well. You will learn how to access the Media Center section of your XBox, and get the...

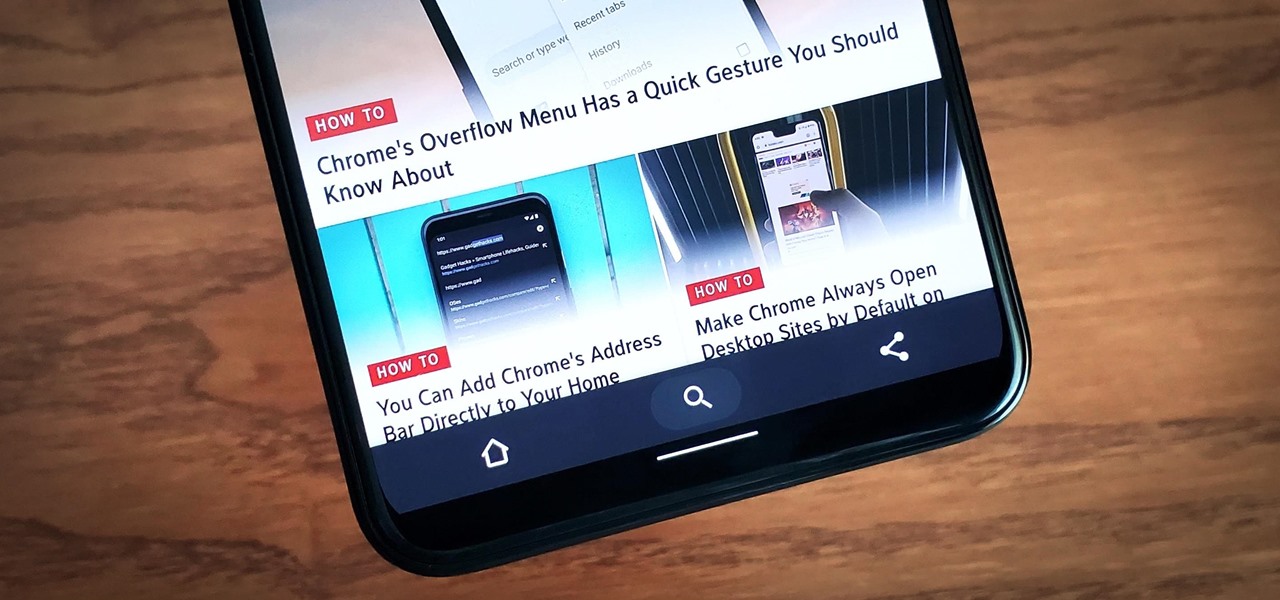
Google has always experimented with Chrome's UI, but when they make more drastic changes, they start by hiding them in the feature flags menu. One of the latest designs makes Chrome more accessible in a world of big and tall phones.

Few companies have maintained such intense secrecy, in the face of such extreme hype, as Magic Leap, but the closer their mysterious Mixed Reality product comes to mass production, the harder it becomes to hide the details. Hopefully we'll find out way more details soon, as a Magic Leap job posting for a supply chain manager hint that they're readying for release in the next couple years.

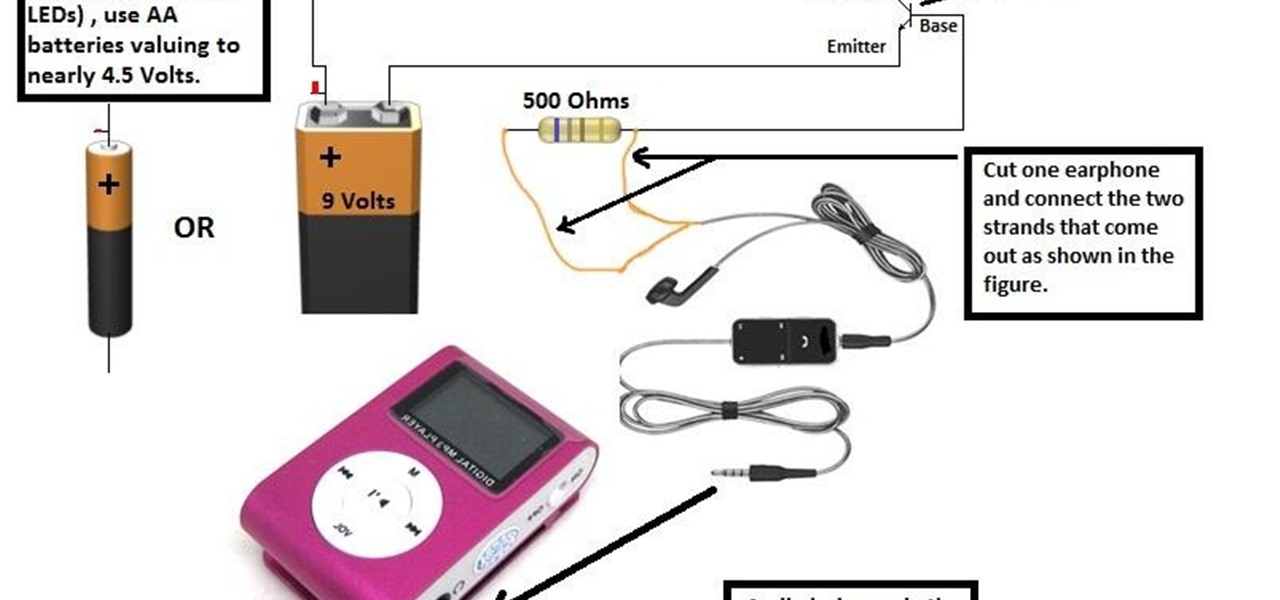
You must have seen some expensive mp3 players and CD players which have LEDs fixed on them and they dance to the tune looking really pretty.

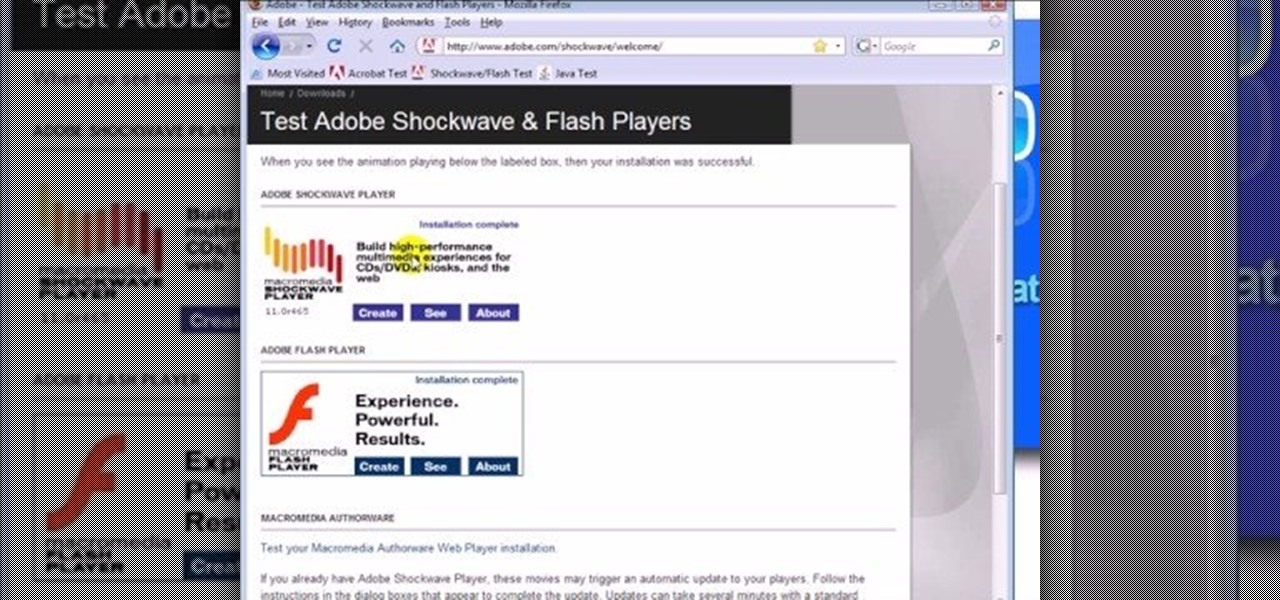
In this video, we learn how to test Adobe Flash, Shockwave, Acrobat & Java. First, see if you have Acrobat Reader installed and working properly by reading this PDF. If you have it installed properly, you will see a PDF with a configuration guide. To see if Shockwave works, go to: Shockwave. If working properly, you will see a "create, see, about" link, not one asking you to install it. Last, to test Java you will go to: Java Test. If you have installed this properly, you will see an animatio...

First of all, feel free to disregard the first 2:05 of this video, it is not a how-to but behind-the-scenes footage of this guy's short film. After 2:05, however, you will get a great tutorial on how to make a set of prop Wolverine claw quickly, easily, and cheaply. They are made out of cardboard and spraypaint, and as long as you don't do any closeups on them or require you Wolverine to open his hands with the claws out at any point (impossible in this configuration) they look plenty real. Y...

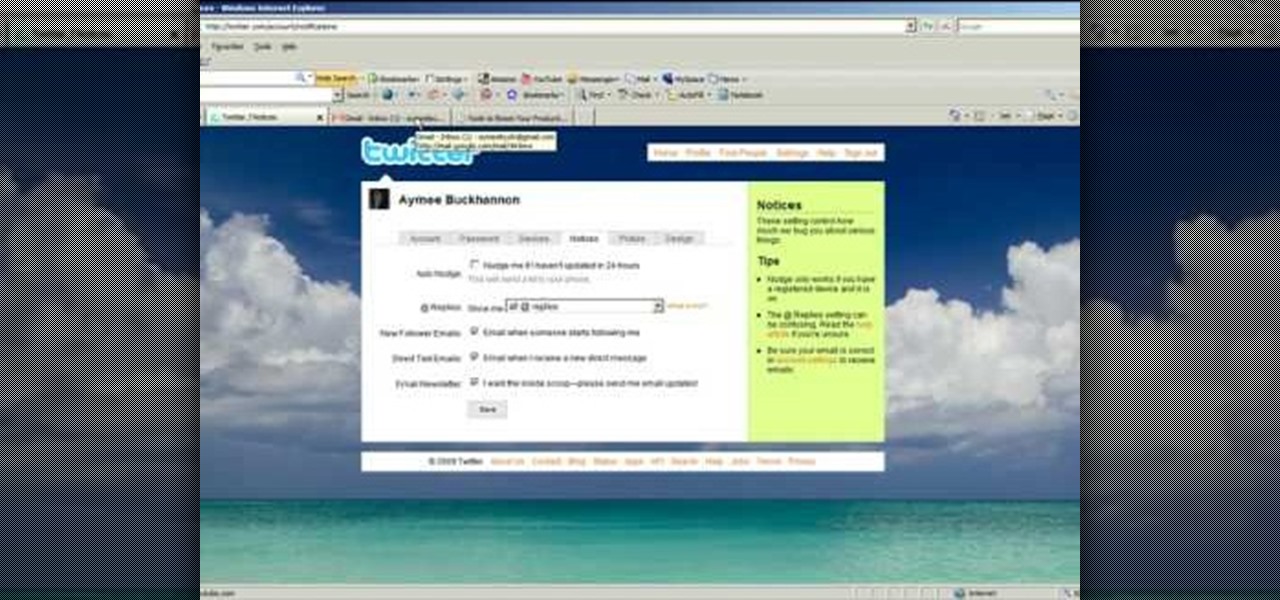
Twitter is the latest popular social networking forum. Twitter is used to keep your friends updated with what you are doing using 140 character messages called tweets. In twitter you can follow your friends and you will be notified when ever your friends posts a new message. Similarly other people can follow you on twitter to know what you are doing. In twitter you can customize to send an automatic private response to your new followers. To do this open your twitter account. Go to the notice...

In this video, it demonstrate how to check and configure Windows firewall. In order to check to see if firewall is enable or not. You would click on start which locate bottom left corner of the screen. Then you would click on control panel. On this screen you would see an option for firewall, and click on it. When you click on firewall, it will let you view all the description about firewall configuration. There are also many other option which locate on the left hand side. If you are an adva...

A video from HelpVids that shows how to disable Windows Aero visual style in Windows 7. Nero makes your windows look more beautiful by adding effects like transparency / translucency, live thumbnails, live icons etc. All these effects however use valuable system resources like memory (RAM) and processor time. This may lead to a noticeable decrease in performance in some PC configurations especially those in which the processor speed and the amount of RAM is low.

If you're into arts and crafts then you know that there is more that you can do with a long piece of string than just tie your shoes. On this TyingitAllTogether video you have the opportunity to tie the teacup decorative knot using one long piece of string folded in half. The author of the video first shows you what the end product will look like then methodically begins to walk you through setting up the string in Y-configuration to "crossing each bights crook" which involves overlapping and...

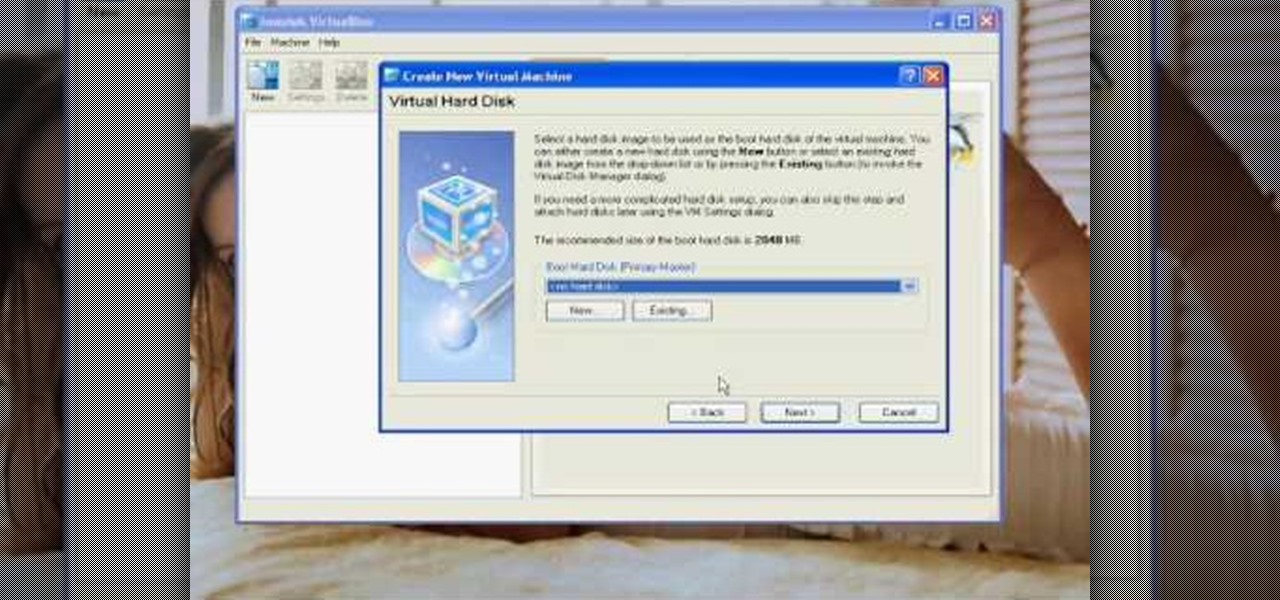
The author shows how to install Puppu Linux 4.3.1 in Innotek VirtualBox 1.5.2. He shows steps to create a new virtual machine in Innotek VirtualBox, by showing the various configuration settings like the RAM size, hard disk space etc. He shows how to boot the virtual machine with the Puppy Linux installation ISO file. Next, during boot up, he shows how to set the language and regional settings, resolution settings etc. In the next screen he shows how to access the local drive and partition it...