The newly enhanced focus from Magic Leap on enterprise, announced on Tuesday, also came with a few companies opting to weigh in with their experiences developing for the platform.

Sorry, Galaxys S11–19, Samsung's jumping straight to Galaxy S20 this year. They're also going with essentially three base models before accounting for niche variants. Of these three models, it's clear which one's the best: the Galaxy S20 Ultra.

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

When it comes to building luxury cars, Bentley certainly knows what it's doing. However, when it comes to building an AR app, Bentley is looking less Continental GT and more Geo Metro.
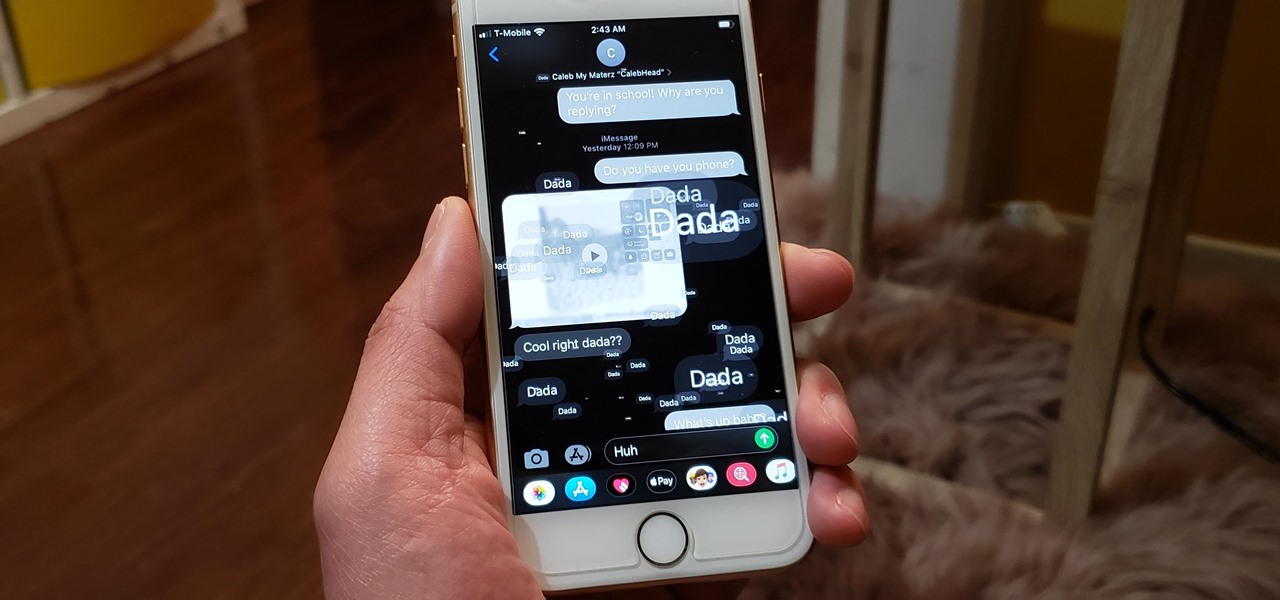
Message effects in iMessage lets you add a touch of flair to otherwise bland communications. With the feature, you can complement a birthday wish with a stream of balloons, send a congratulatory text along with a shower of confetti, or make the chat bubble slam itself in the thread. If you're on the receiving end, however, they may be distracting and even jarring.

The idea of remote assistant apps in augmented reality has been taking off in the last couple of years, but Epson is introducing a differing kind of solution for companies that may benefit from a more straightforward dynamic before going full-on immersive with higher-end AR remote assistance tools.

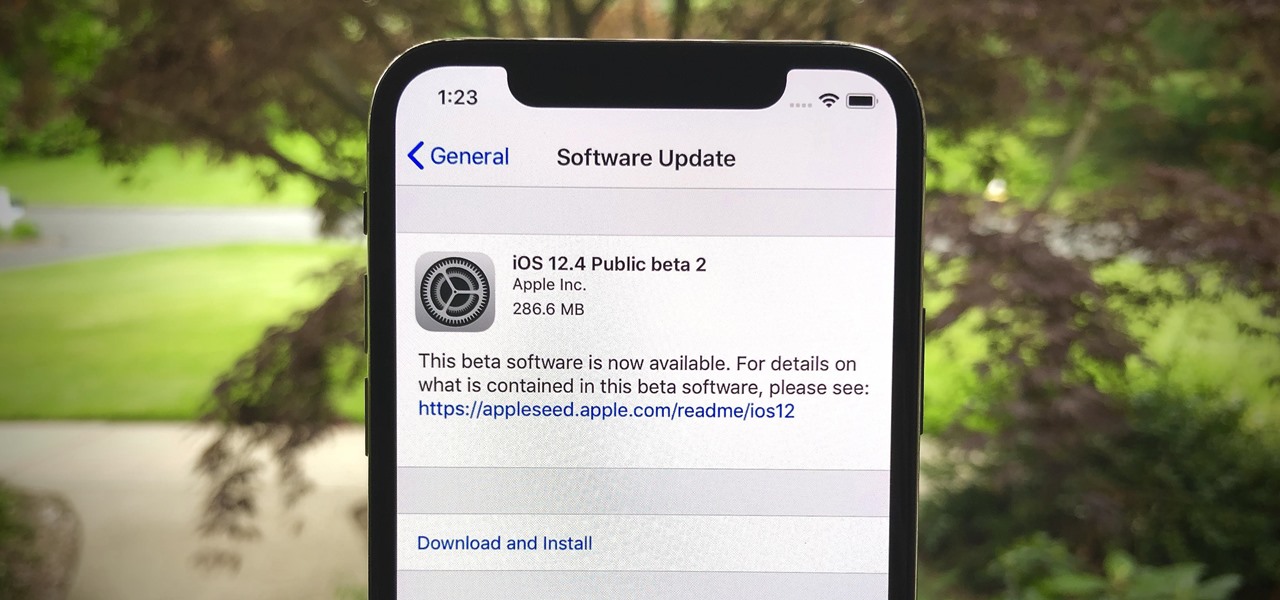
Public beta testers, you're in luck. Apple just released the second iOS 12.4 public beta today, May 20. The update comes five days after the release of the first developer beta for iOS 12.4 and seven days after the release of iOS 12.3. Public beta 2 and dev beta 2 were both released at the same time, something that doesn't happen often.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.

It may sound like deja vu, but neural interface startup CTRL-labs has closed a $28 million funding round led by GV, Google's funding arm, for technology that reads user's nerve signals to interpret hand gestures.

With Apple releasing the iPhone XR, it appears Samsung is looking to challenge this "budget flagship" option head-on. They brought their usual two phone releases this year, but also threw in another three for a total of five phones, including the Samsung Galaxy S10e. And for many, this might be the option to look at.

Earlier this year, Samsung released the Galaxy J3 and J7 to select markets. These two devices are the latest in the J series, Samsung's super-budget series that tries to rewrite what it means to be a budget phone. Now, starting September 14th, you will be able to get them GSM unlocked.

Last week, iOS 12 developer beta 7 was quickly pulled upon release, due to complaints of poor performance and instability issues. While Apple tackled these bugs with the release of developer beta 8 two days later, testers are seeing beta 7 again in their Software Update settings. Why is beta 7 back, and, more importantly, is it safe to download?

The rite of passage for every tech product, formally known as Federal Communications Commission (FCC) certification, has come for the Magic Leap One: Creator Edition.

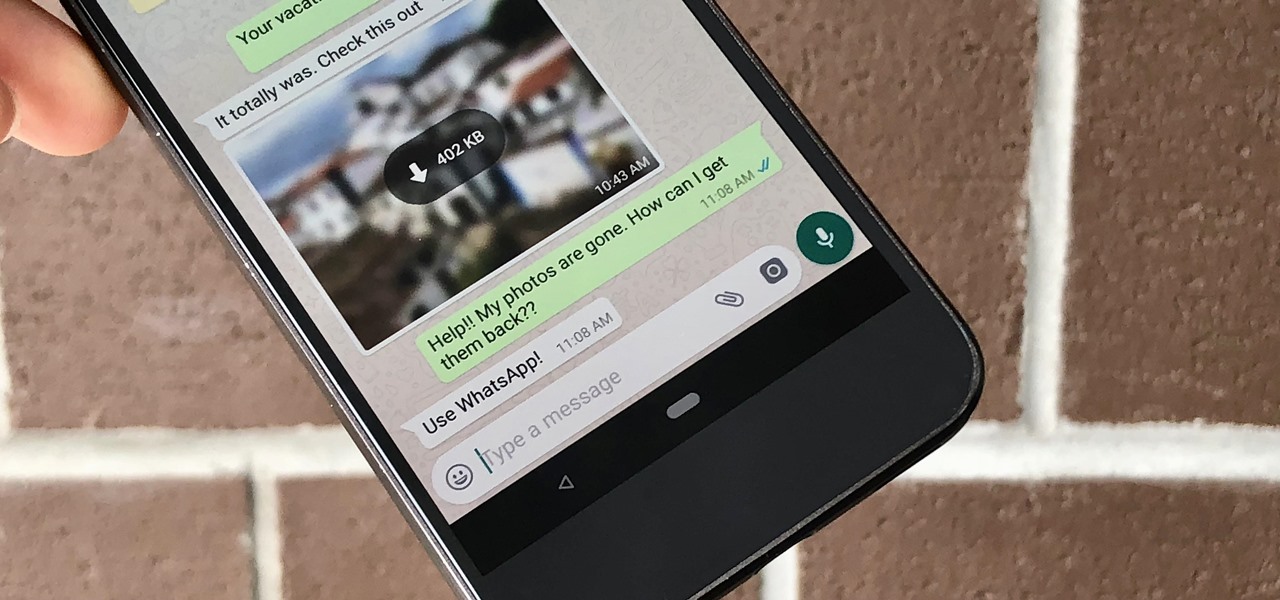
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

On Tuesday, at the Unite Berlin developers conference, Unity unveiled new tools designed specifically for augmented reality that could literally raise the technology to the next level.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

Augmented reality startup 6D.ai is now accepting applicants for the closed beta of its 6D SDK. While operating in the background on a smartphone, the computer vision platform captures a dense 3D mesh in real time using just the device's camera (such a feat typically requires a depth sensor).

We already showed you the dark side of augmented reality in the form of a virtual girlfriend from Japan, but now the same country has given us something a lot less creepy that could be the future of virtual pop stars everywhere.

The S9 and S9+ are both fantastic phones. However, there's no getting around the fact that the S9+ has its advantages. In fact, it's an objectively better smartphone than its smaller counterpart — Samsung has given the S9+ features not found in the S9, meaning you'll be missing out if you choose the 5.8" Galaxy over the 6.2".

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

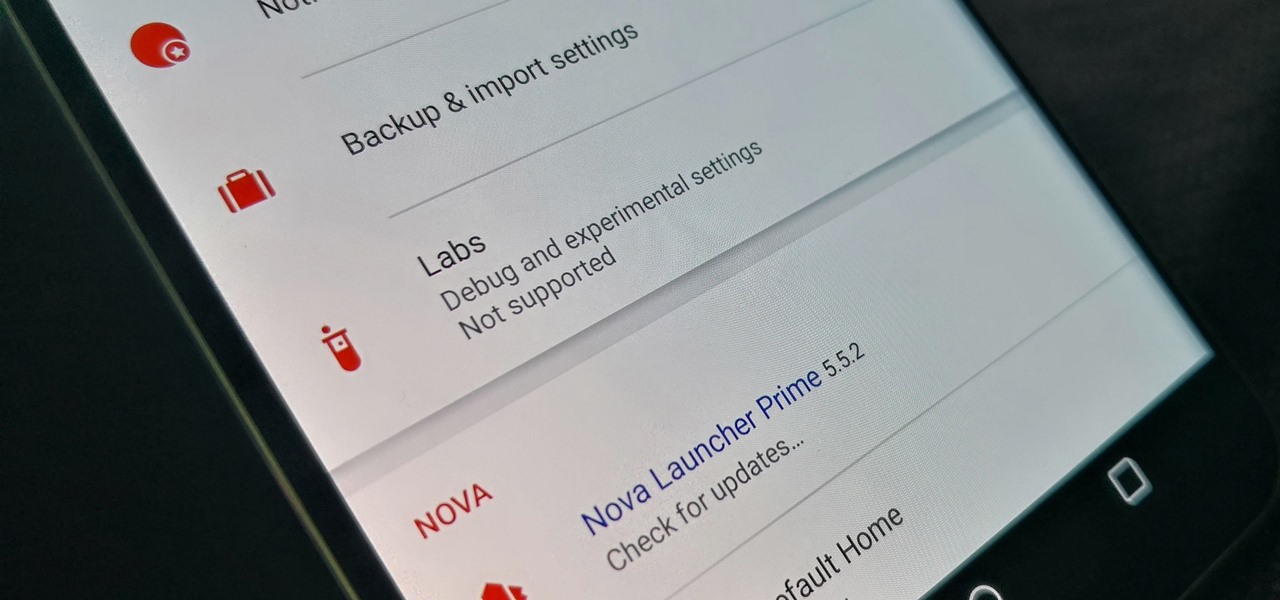
TeslaCoil's Nova Launcher is one of the best home screen apps on the Play Store. It's about as fast as it gets, and it's always among the first to add the latest Android features. However, it looks like Nova Launcher isn't showing users all of the customization options available — apparently, there's a secret menu, and it's pretty simple to unlock.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Huawei has been on a roll recently. They just became the second largest smartphone manufacturer in September, passing Apple and trailing only Samsung. Shortly after, they announced their new Kirin 970 flagship SoC to rival the Snapdragon 835, then followed that up by announcing the Mate 10 and 10 Pro. Well apparently, Huawei isn't done with announcements just yet.

We've had a lot of fun digging into the Oreo update for the Galaxy S8. Thus far, we compiled a full list of the biggest changes and ran down some of our favorites. One of the most user-facing components on a smartphone is the camera. Samsung made sure to add some nice tweaks to the camera UI in Oreo too, bringing it more in-line with the camera on the Galaxy Note 8.

With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.

The iPhone X is almost within reach. In fact, you can preorder right now. We know you've been itching to get your hands on Apple's newest iPhone, but before you give up over $1,000 of your hard-earned money, make sure your iPhone X knowledge is up-to-snuff.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Using the Mail app to log in and sync to email services such as Gmail and Outlook is incredibly easy to accomplish on the iPhone thanks to the intuitive nature of its operating system. This is still evident with iOS 11, and though the process differs slightly from its predecessors, it can still be accomplished with relative ease.

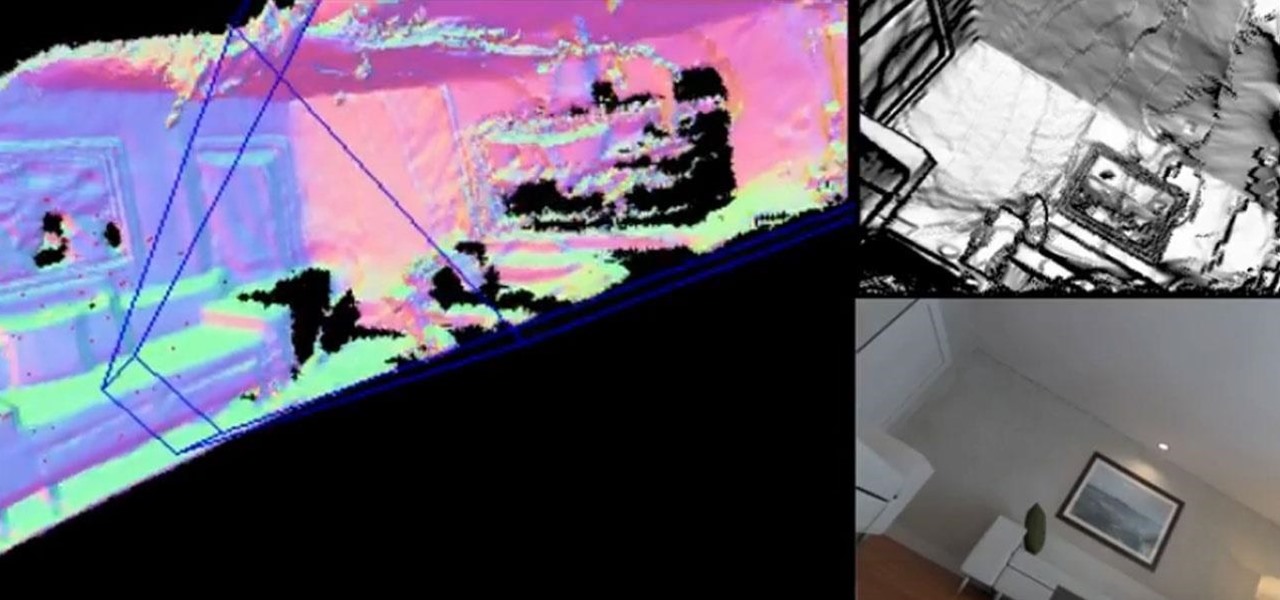
In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your phone.

3D Touch is only available on the 6s and 7 series iPhones right now, and likely future models, so those with older devices are missing out on all the cool "Quick Actions" available for app and settings icons. But the new iOS 11 is finally bringing some of those helpful shortcuts to iPhones without 3D Touch built in.

A new leak by frequent tipster Roland Quandt appears to reveal the renders of Motorola's next budget smartphones, the Moto E4 and E4 Plus.

Waymo's transfer of its driverless car know-how to commercial trucks will likely pose few challenges for the self-driving unit of Alphabet, which owns Google.

If OnePlus co-founder Carl Pei was trying to be slick about using the new OnePlus 5 phone — especially before its speculated summer release — well, he didn't do that great a job of hiding it from us.