
News: First Look at the iPhone 6's Unbreakable Sapphire Crystal Display
It's increasingly difficult to keep any secrets at bay, and that has become especially true for Apple's upcoming iPhone 6.


It's increasingly difficult to keep any secrets at bay, and that has become especially true for Apple's upcoming iPhone 6.

How to use a tape measure so that you can write on it clearly. Tape measures are one of the most useful tools in your tool kit. Unfortunately it's difficult to write on them clearly because of its glossy surface. In this video l show you how to modify your tape measure to turn it into a really handy note pad.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Are you always afraid to apply lashes by yourself, or that you never get it right? Do you find that your false lashes fall off in the middle of the day? Watch to find out how to apply fake eyelashes or falsies! This is a live step by step tutorial, perfect for beginners!

A lot of people rely on the date on the packaging to tell them when food has gone bad, even with eggs, but the sell-by dates are often somewhat arbitrary and are not expiration dates. If you've been tossing your eggs based on the dates on your carton—you could be wasting perfectly good food.

Yesterday, I was halfway through a recipe when I realized it called for puréed tomatoes, and all I had was diced. I definitely wasn't going to abandon ship and start over on something else, but I didn't want my sauce to have the wrong texture, either. So, I did a quick search and found that I could use my metal sieve to purée the tomatoes.

Removing the thin aluminum foil wrapping from a Hershey Kiss isn't necessarily a difficult thing, but even the easiest of things can be annoying sometimes. For instance, getting chocolate under your fingernail when you're trying to peel the wrapper off, or making a wrapper mess. To make this first-world problem go away, simply grab a Hershey Kiss in-between your index finger and thumb, then pull on the paper plume to yank the chocolate straight out of the wrapper. The plume was originally des...

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....
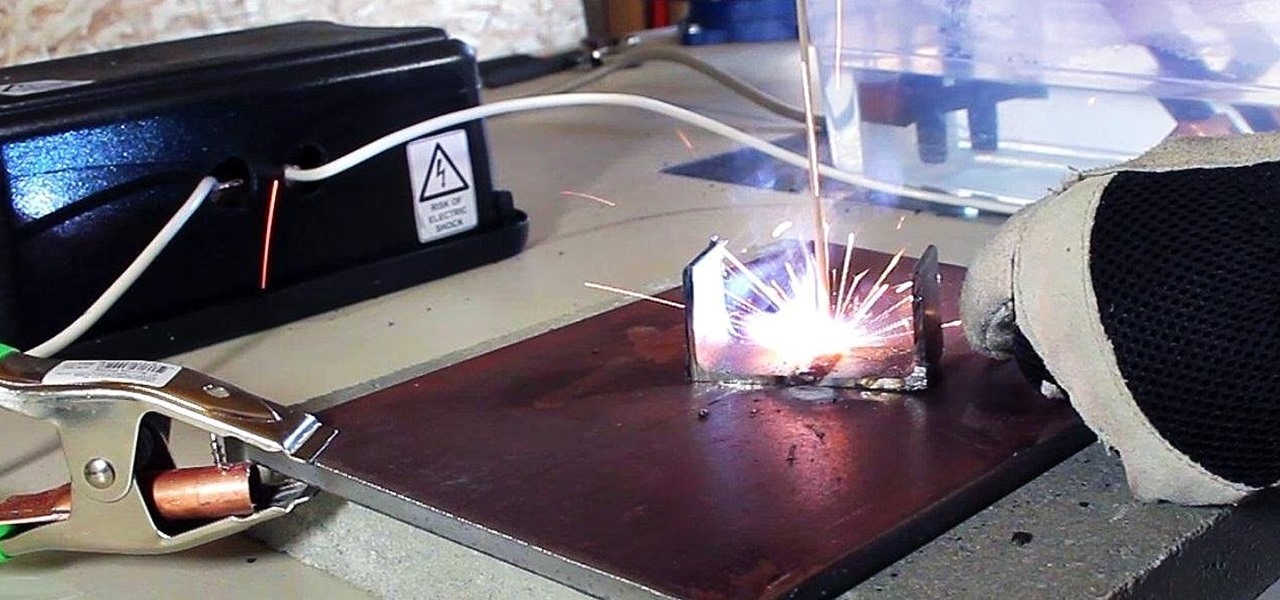
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .
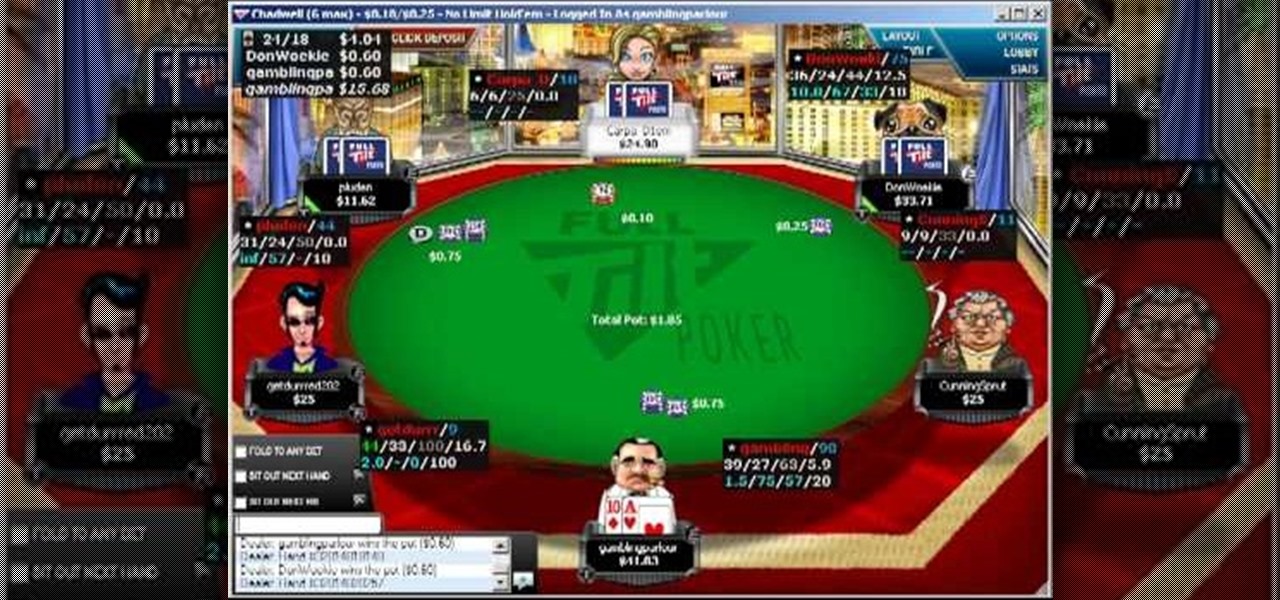
There are plenty of times when very aggressive poker players will make life difficult for you because they're always looking to put max pressure on their opponents to try and get them to fold out their medium strength hands. Knowing how to play against loose aggressive opponents is an important part of beating the games you play, especially the more aggressive online 6-max games. It’s important to know some fundamental strategies outlined in the video below. The common strategy used for each ...

Like in the original Black Ops, there are a bunch of funny and cool Easter eggs built into Call of Duty: Black Ops 2. Most have been discovered, like the Atari arcade invincibility on Nuketown 2025, but perhaps you didn't know about Thor's hammer?

There isn't as much use for old-school four-function calculators anymore since we all have them on our cell phones now. If you've still got one lying around, you can hack it to play recorded sounds, use it to make a metal detector, or turn it into a custom name plate that says anything you want...

Keeping your computer organized and your desktop clutter-free can be pretty difficult. And with last week's official release of Windows 8, users have another screen they need to get used to organizing—the new Metro-style Start Screen. It uses large rectangular or square tiles in place of the standard icons you've seen on older Windows operating systems. For better organization and grouping, you can group similar items onto a page (similar to many smartphones), you increase or decrease the siz...

This tutorial video is all about how to move off and stop and use your mirrors when taking driving lessons in Nottingham and the surrounding area.

Yesterday, the entire Internet was talking about how the new Kindle Fire HD was supposed to be incredibly difficult to hack. Turns out, the folks over at XDA Developers are smarter than they thought—one day later, the mystery has already been solved. The exploit is the same one found by sparkym3 in Ice Cream Sandwich, but Amazon must have forgotten to patch it. As with any root, you can cause some serious damage, or brick your device completely if it's not done properly, so proceed at your ow...

Love taking photos with your smartphone, but don't have a zoom? This tutorial by Unitips will show you how to DIY one with a few simple parts. All you'll need is 1/4" bolts, washers, and wingnuts (two each), some sheet metal, and a pair of binoculars.

Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

Who would have thought that dryer sheets can be a quick remedy for super-staticky flyaway hair? But it's true. It's all about the positive charges in the sheets and their ability to neutralize electron buildup. And that's not the only surprising quick fix for hair problems that you can easily find in your home.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.
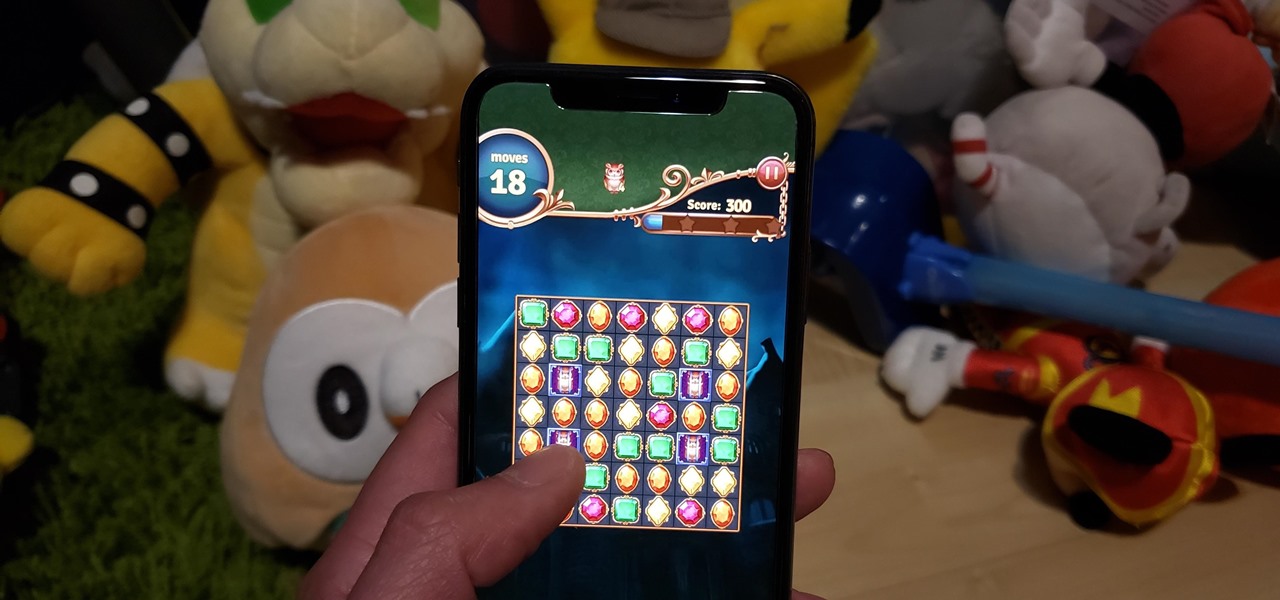
Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.
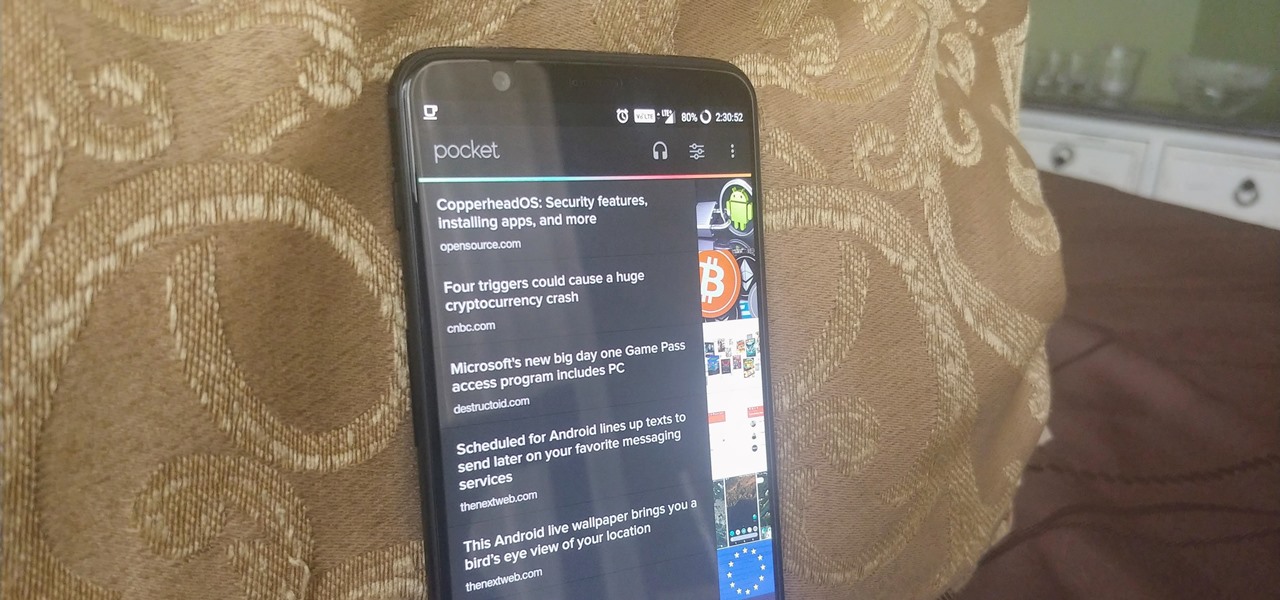
Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Greetings my fellow aspiring hackers,

Your freezer is no one-trick pony. While it does excel at keeping your food fresh for as long as possible, it has a few secret talents it doesn't want you to know about. Like making soda slushies and pyro-friendly smoke mix, as well as reviving dead hard drives. Even better—it can help you do laundry.

Only three things in life are certain: death, taxes, and getting a dent in your car or truck. Even if you're as careful as possible, you can't always account for runaway shopping carts, wrongly thrown footballs, out-of-nowhere light posts, and other real-life annoyances.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...
The experience of actually using the HoloLens 2 can be difficult to describe to anyone who hasn't had a chance to directly interact with the device in person and be blown away by its immersive capabilities.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.