Electronic devices seem to have an uncanny ability to make noise at the worst possible times. It's always during an important meeting, a quiet study session at the library, or a biology final that your laptop or smartphone decides to play some obnoxious or embarrassing sound.

Pringles are just as well known for their cylindrical packaging as for their suspiciously addictive fried crisps. Yes, that's crisps—not chips.

There are some things that are just plain difficult to do for those of us with small hands. I started playing the piano when I was a little kid, and I learned the hard way that there were some chords that were just out of my reach.

Lock screen exploits are becoming increasingly common in the mobile world. Four weeks ago there was the iPhone 5 passcode bug (which just got fixed yesterday...kinda). Then there were a couple lock screen bugs on the Samsung Galaxy S3 two weeks ago.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

There are some pretty incredible camera techniques out there, but the biggest problem that amateur photographers run into is that they don't have the equipment to try them. You can still get some great shots, but there are some things that are really hard to do if you don't have the money to drop on expensive lenses and accessories.

This is one of my personal favorite designs from last year, that I wanted to share with you all for this year's valentines day !

I actually have a lot of shoes, and putting them on the floor in my closet just makes for a very large mess, and makes it harder to find a matching pair. So, this simple yet cool DIY shoe storage is actually something I could benefit from doing. This project shouldn't be too difficult to complete. You can get PVC pipe from your local hardware store and either have them cut it, or you can do it at home if you have a table saw. You can also opt to buy concrete forming tubes, which may be a litt...

While the heyday of the Slinky may have been a few decades ago, I still think it's one of the coolest toys to ever go to market. Not to mention it probably has the best commercial ever created.

You've seen security cameras everywhere in the public space. How many are there? Where are they? This is information that can be difficult to come by. It's not just criminals that are interested in information on this. It's your fundamental human right to be able to go about your daily life without being monitored and watched at every step. You might think that these cameras are for safety, and they can certainly help make people feel secure. Then it automatically follows that these people sh...

At night, it can be pretty difficult to see what's inside drawers and cabinets, unless you have night vision or something.

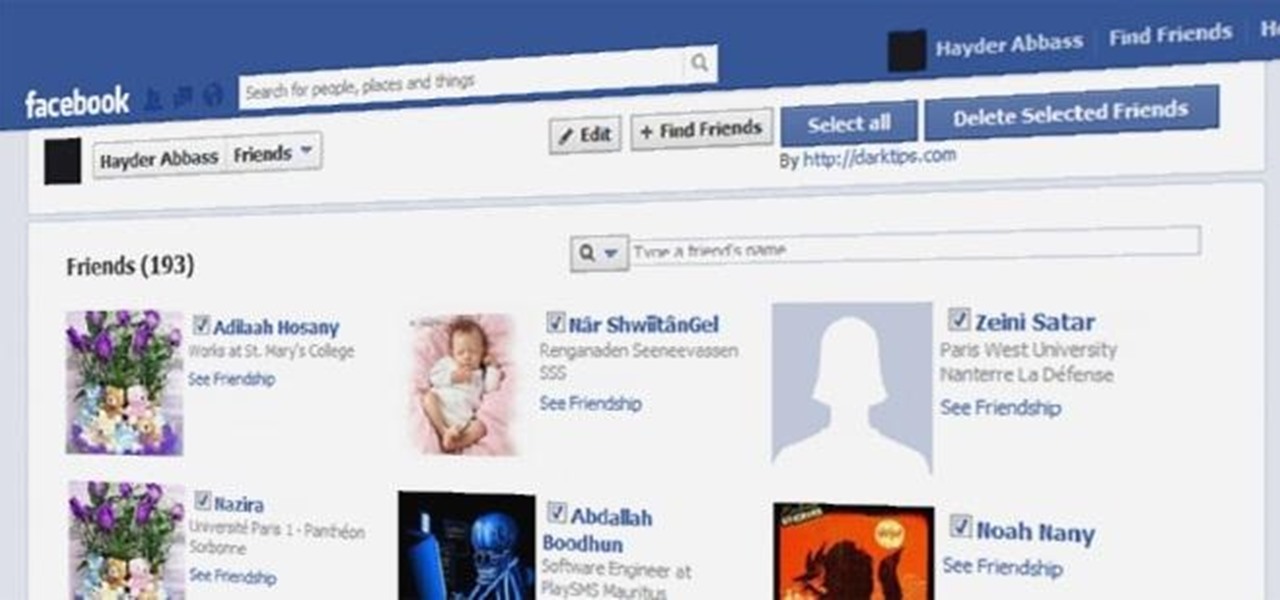
Facebook makes it extremely easy to keep in touch with family and friends, while maintaining those relationships with little to no face-to-face contact. It's the perfect tool for recluses.

Last month, Google changed the placement of search options from the left side of the page to the top, right above the first result. In theory, this shouldn't be such a bad thing—it's just looks, right? Well, not quite. Turns out, it actually got rid of a few of the options as well, and a lot of people were not too happy about it. The problem is that the change gives you less functionality, and makes the options that are still there harder to get to. One of the most frustrating changes was how...

Eavesdropping from a distance can be tricky because it usually requires some sort of bug or transmitter. It's easy to transmit audio through lasers, but you can also use lasers to build a microphone that picks up audio from a distance. LucidScience built the Laser Spy System for about $20. To make your own, you'll need a cheap laser pointer, an NPN phototransistor, a headphone amp, and a few other small pieces listed below. A light-to-sound circuit is installed in a small plastic box with the...

On average, it takes three seconds to move your hand from the keyboard to the mouse, then click once and move your hand back to the keyboard. While the time wasted my sound trivial, it can add up quickly throughout the day.

Facebook has always been notoriously difficult to customize. Personally, I think this is an improvement over MySpace's totally open platform (some people should not use code), but users should still have the option to change a few things if they want. While you'll never be able to choose your own background image or add an obnoxious number of aWeSoMe quiz results to your profile, there are a few browser plugins that let you at least change the color scheme.

Rooting your device gives you all-powerful administrative access to your phone and its system settings. Of course, with such power comes great responsibility, and sometimes that responsibility becomes to burdensome or just plain unnecessary.

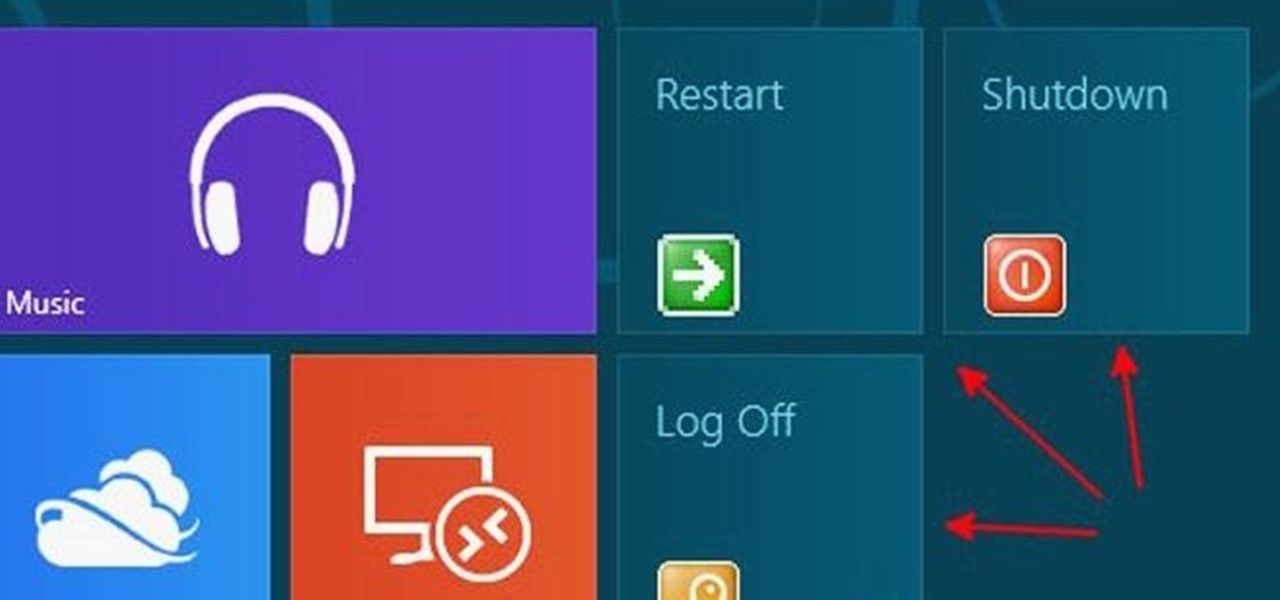
Windows 8 the biggest update to Windows yet. The new gesture-friendly version replaces the aging start menu with a dynamic new Start Screen, complete with live tiles that give you a glimpse into your apps before you launch them, not unlike the new Windows phones. With such a radical departure from the past, some familiar features have been moved around, which will take some getting used to. It's worth noting that the new Windows 8 does not abandon the old desktop model completely; it still ha...

Did you know that the average cost to make a penny is about 2.4 cents?!? That's why the Obama administration asked Congress earlier this year for permission to change the metals in the penny, hoping to get the cost back down where it makes sense.

The original NES controller has become one of the most recognizable symbols of the Nintendo gaming culture, thanks to its perfectly rectangular shape and simple button design. But despite its popular appeal, people just don't game with them anymore. So, what do they do with them? They savor the memories and turn it into something more useful, like a light switch.

Combination locks in Minecraft can be really simple or frustratingly difficult, but no matter how complicated they are, some of them fall victim to the same simple exploits.

Shooting a photo or video in a car can be rather difficult without a proper mount, and if you want to secure your camera outside the car, it can be just plain expensive. Luckily, there are tons of DIY camera mounts for both inside and outside your vehicle, and most of them are pretty cheap to make. Here are some of the best.

We've all played with bubbles as kids, but I think most would agree that they're not exactly the most functional of objects. An international team of researchers made up of Yoichi Ochiai, Alexis Oyama and Keisuke Toyoshima wants to change that. They've figured out how to project both 2D and 3D images onto a micro membrane (soap bubble) using ultrasonic sound waves and a standard projector. The bubble is made of a solution of sugar, glycerin, soap, surfactant, water and milk. The glycerin and ...

You can take some absolutely gorgeous photos using the natural reflection that appears in people's and animals' eyes. With the right angle and lighting, you can even see a detailed picture of what the subject was looking at when the photo was taken. Photo by Martin Cathrae

Making cookies is one of the best things in life, especially around the holidays. There is nothing better than getting together with friends and family and bonding by baking cookies.

This is a pretty simple how-to, because a doorbell is a pretty simple mechanism! The difficult part is in understanding music note blocks.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Look, tests are no fun, and doing poorly on them is rarely an option. Whether you're studious or a slacker, everyone needs a little boost now and again. While students have found ways to cheat as long as tests have existed, the invention of smartphones has greatly enhanced the potential to get ... creative.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Since its debut, retro thriller Stranger Things and its characters have become ingrained in our popular culture — especially the telekinetic Eleven. For cosplayers, it didn't take long before they grabbed their boxes of frozen Eggo waffles, blonde wigs (or bald caps), and pink smocked dresses to transform into El herself.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

With Zoom and Google Meet, you can zoom in using your rear camera on a video call to focus on something far away or to get a closeup view. But in Messenger, Snapchat, WhatsApp, Skype, Instagram, and most other video chat apps, zoom functionality is disabled. And it may appear to be blocked in FaceTime too, but that's not the case — the feature is just hiding in plain sight.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.